实验吧CTF练习题---WEB---Forms解析
Posted redhskb
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了实验吧CTF练习题---WEB---Forms解析相关的知识,希望对你有一定的参考价值。
实验吧web之Forms
flag值:ctfforms_are_easy
解题步骤:
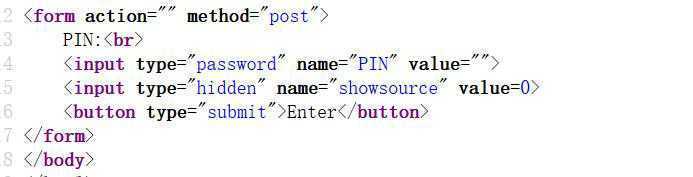
1、查看页面源代码,从中发现"value=0",并且在框内输入任何东西都没有反应

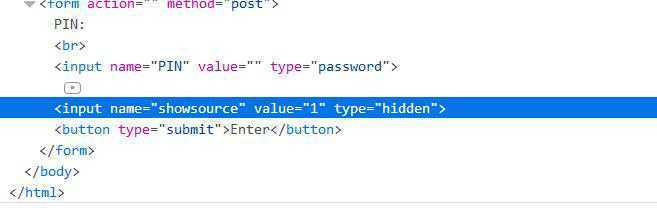
2、打开调试器,找到"value=0"这个位置,把"value=0"改成"value=1"

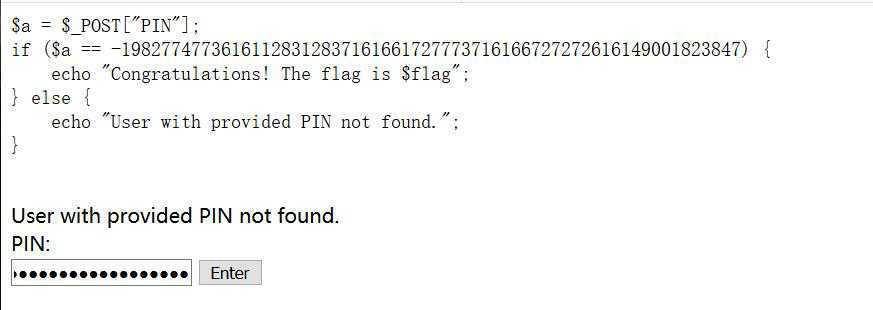
3、在框内随意输出任意字符,反弹出php源码,把a=·····的数字填到框内

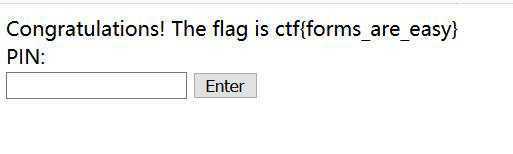
4、提交反弹flag值,结束

以上是关于实验吧CTF练习题---WEB---Forms解析的主要内容,如果未能解决你的问题,请参考以下文章