用shell脚本批量进行xss跨站攻击请求
Posted gufengchen
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了用shell脚本批量进行xss跨站攻击请求相关的知识,希望对你有一定的参考价值。
由于执行的xss攻击请求他多了,初步估计要执行83次,而且还要执行3篇,如果手工一个一个去执行,说出去,我还配叫自动化大师吗;
有鉴于此,边打算自己编写一个脚本进行批量执行;
而短脚本的编写,非shell莫属,想到做到;
首先附上xss跨站攻击的请求报文:
POST /web/show.asp?id=1327 HTTP/1.1 Host: 192.168.26.xxx Connection: close Accept: image/gif, image/jpeg, image/pjpeg, image/pjpeg, application/x-shockwave-flash, */* User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727) Content-Type: application/json Content-Length: 25 "11111": " onabort =" 将onabort换成如下攻击特征: onactivate onafterprint onbeforeactivate onbeforeprint onbeforeunload onblur oncancel oncanplaythrough oncanplay onchange onclick oncontextmenu oncopy oncuechange oncut ondblclick ondragdrop ondragend ondragenter ondragleave ondragover ondragstart ondrag ondrop ondurationchange onemptied onended onerror onfocus onformchange onforminput onhashchange oninput oninvalid onkeydown onkeypress onkeyup onloadeddata onloadedmetadata onloadstart onload onmessage onmousedown onmouseenter onmouseleave onmousemove onmouseout onmouseover onmouseup onmousewheel onmove onoffline ononline onpagehide onpageshow onpaste onpause onplaying onplay onpopstate onprogress onpropertychange onratechange onreadystatechange onreset onresize onscroll onsearch onseeked onseeking onselect onshow onstalled onstart onstorage onsubmit onsuspend ontimeupdate ontoggle onunload onvolumechange onwaiting onwheel
看到没有如果一个一个执行,我的天,这要猴年马月才能搞完!
话不多说,附上shlle脚本代码:
#!/bin/bash echo "循环开始开始执行" for j in $(cat rules3.txt) do echo " 注意的是,json数据里变量要用 ‘‘ 括起" # curl complete post json post 请求 # curl -i -X POST -H "‘Content-type‘:‘application/x-www-form-urlencoded‘, ‘charset‘:‘utf-8‘, ‘Accept‘: ‘text/plain‘" -d ‘json_data=...‘ url curl -i -X POST -H "‘Content-type‘:‘application/json‘" -d $j http://192.168.26.213/ done echo "循环结束"
其中rules3.txt文件内容为:
‘json_data="11111":"onactivate"‘/ ‘json_data="11111":"onafterprint="‘/ ‘json_data="11111":"onbeforeactivate ="‘/ ‘json_data="11111":"onbeforeunload="‘/ ‘json_data="11111":"onblur="‘/ ‘json_data="11111":"oncancel="‘/ ‘json_data="11111":"oncanplaythrough="‘/ ‘json_data="11111":"oncanplay="‘/ ‘json_data="11111":"onchange="‘/ ‘json_data="11111":"onclick="‘/ ‘json_data="11111":"oncontextmenu="‘/ ‘json_data="11111":"oncopy="‘/ ‘json_data="11111":"oncuechange="‘/ ‘json_data="11111":"oncut="‘/ ‘json_data="11111":"ondblclick="‘/ ‘json_data="11111":"ondragdrop="‘/ ‘json_data="11111":"ondragend="‘/ ‘json_data="11111":"onondragenter="‘/ ‘json_data="11111":"ondragleave="‘/ ‘json_data="11111":"ondragstart="‘/ ‘json_data="11111":"ondrag="‘/ ‘json_data="11111":"ondrop="‘/ ‘json_data="11111":"ondurationchange="‘/ ‘json_data="11111":"onemptied="‘/ ‘json_data="11111":"onerror="‘/ ‘json_data="11111":"onfocus="‘/ ‘json_data="11111":"onformchange="‘/ ‘json_data="11111":"onforminput="‘/ ‘json_data="11111":"onhashchange="‘/ ‘json_data="11111":"oninput="‘/ ‘json_data="11111":"onkeydown="‘/ ‘json_data="11111":"onkeypress="‘/ ‘json_data="11111":"onkeyup="‘/ ‘json_data="11111":"onloadeddata="‘/ ‘json_data="11111":"onloadedmetadata="‘/ ‘json_data="11111":"onloadstart="‘/ ‘json_data="11111":"onload="‘/ ‘json_data="11111":"onmessage="‘/ ‘json_data="11111":"onmousedown="‘/ ‘json_data="11111":"onmouseenter="‘/ ‘json_data="11111":"onmouseleave="‘/ ‘json_data="11111":"onmousemove="‘/ ‘json_data="11111":"onmouseout="‘/ ‘json_data="11111":"onmouseover="‘/ ‘json_data="11111":"onmousewheel="‘/ ‘json_data="11111":"onmove="‘/ ‘json_data="11111":"onoffline="‘/ ‘json_data="11111":"ononline="‘/ ‘json_data="11111":"onpagehide="‘/ ‘json_data="11111":"onpageshow="‘/ ‘json_data="11111":"onpaste="‘/ ‘json_data="11111":"onpause="‘/ ‘json_data="11111":"onplaying="‘/ ‘json_data="11111":"onplay="‘/ ‘json_data="11111":"onpopstate="‘/ ‘json_data="11111":"onprogress="‘/ ‘json_data="11111":"onpropertychange="‘/ ‘json_data="11111":"onreset="‘/ ‘json_data="11111":"onresize="‘/ ‘json_data="11111":"onscroll="‘/ ‘json_data="11111":"onsearch="‘/ ‘json_data="11111":"onseeked="‘/ ‘json_data="11111":"onseeking="‘/ ‘json_data="11111":"onselect="‘/ ‘json_data="11111":"onshow="‘/ ‘json_data="11111":"onstalled="‘/ ‘json_data="11111":"onstart="‘/ ‘json_data="11111":"onstorage="‘/ ‘json_data="11111":"onsubmit="‘/ ‘json_data="11111":"onsuspend="‘/ ‘json_data="11111":"ontimeupdate="‘/ ‘json_data="11111":"ontoggle="‘/ ‘json_data="11111":"onunload="‘/ ‘json_data="11111":"onvolumechange="‘/ ‘json_data="11111":"onwaiting="‘/ ‘json_data="11111":"onwheel="‘/ ‘json_data="11111":"onbeforeprint"‘/ ‘json_data="11111":"onbeforeactivate ="‘/ ‘json_data="11111":"onended"‘/ ‘json_data="11111":"oninvalid"‘/ ‘json_data="11111":"onmouseup"‘/ ‘json_data="11111":"ondratechange"‘/ ‘json_data="11111":"onreadystatechange"‘/
注意
curl -i -X POST -H "‘Content-type:‘application/json‘" -d " ‘xxx‘:‘sss‘" url
结果为:
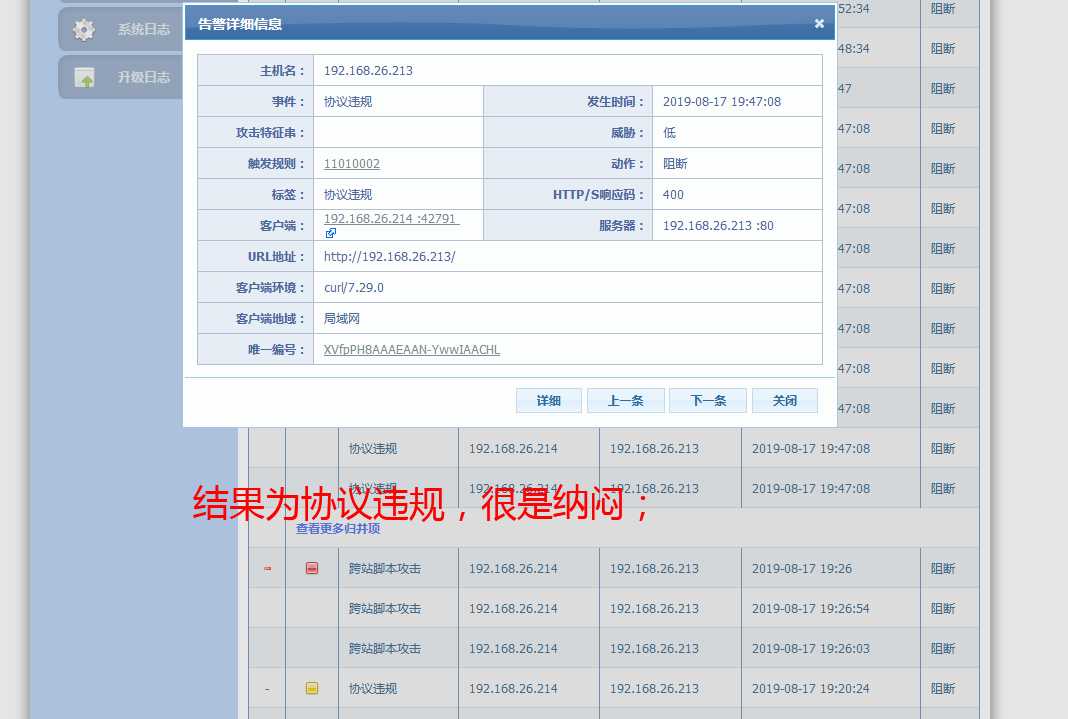
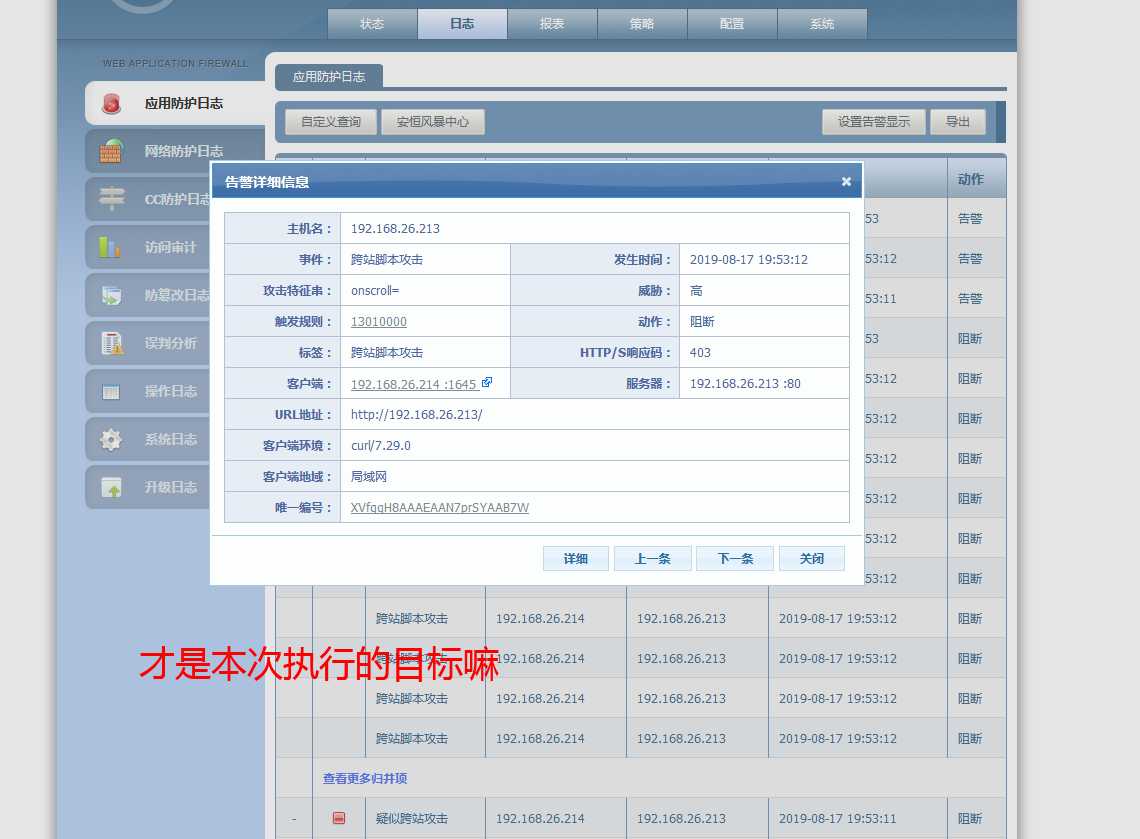
改成这个格式后:
curl -i -X POST -H "‘Content-type‘:‘application/x-www-form-urlencoded‘, ‘charset‘:‘utf-8‘, ‘Accept‘: ‘text/plain‘" -d ‘json_data=...‘ url
想拥有阿里云服务器的可以登陆此网站哦:https://promotion.aliyun.com/ntms/yunparter/invite.html?userCode=qqwovx6h
以上是关于用shell脚本批量进行xss跨站攻击请求的主要内容,如果未能解决你的问题,请参考以下文章