BUGKU (Take the maze)
Posted sweetbaby
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了BUGKU (Take the maze)相关的知识,希望对你有一定的参考价值。
首先进行查壳,没有壳。
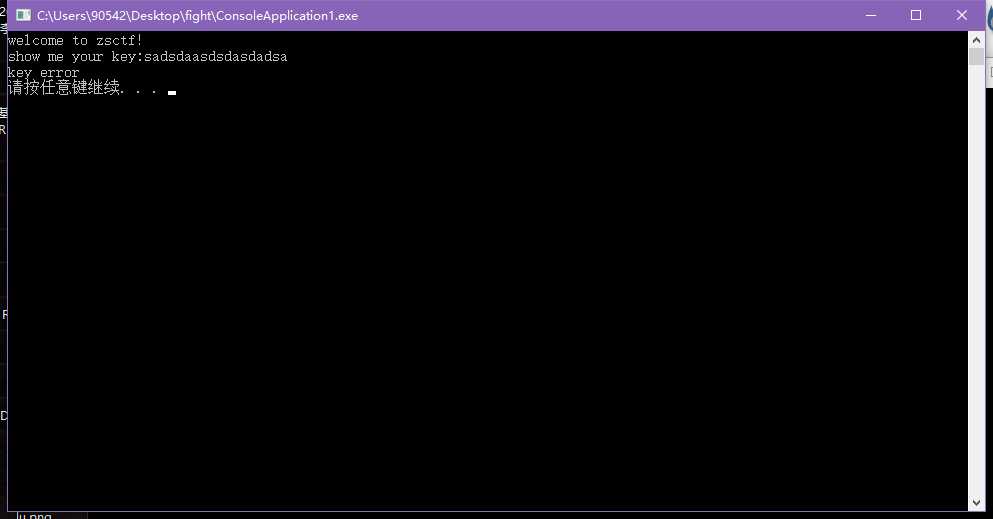
随便输入,看程序执行信息。随意输入字符串,提示key error
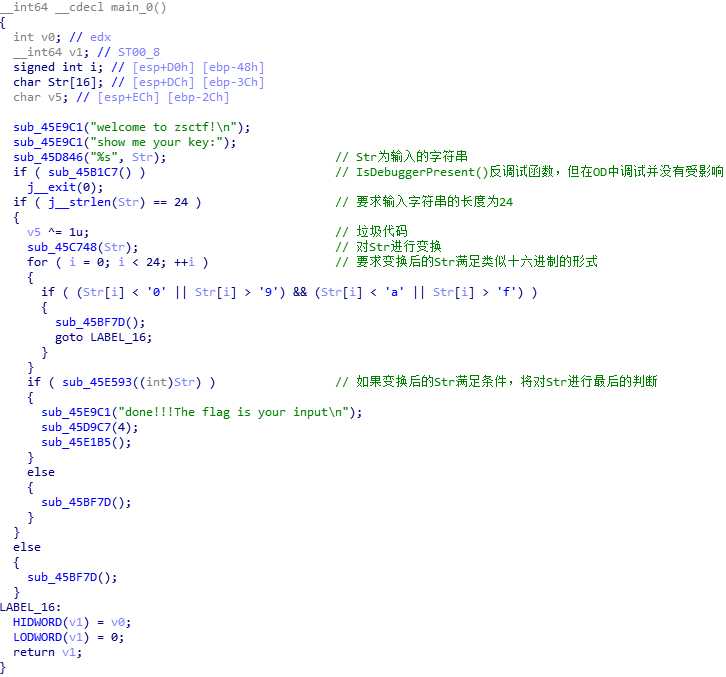
放到IDA中打开,在左侧函数窗口中找到main0,F5反编译,进行分析。具体已在分析在图中标识。
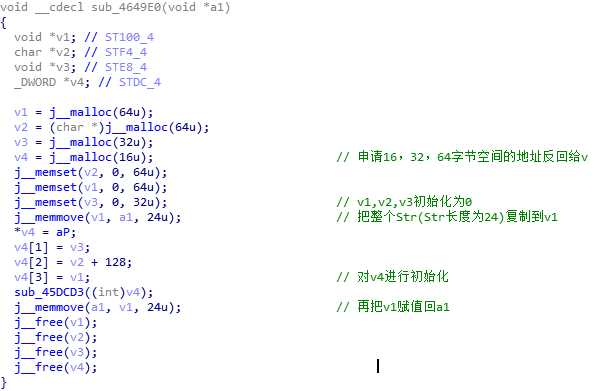
关于main函数的逻辑是很容易理解的,但是接下来可就犯难了。我首先是打开45C748(对Str进行变换的函数)。如下图,看起来应该是在进行对Str变换之前,做一些初始化工作。
整个过程不难理解,但当我打开45DCD3函数时,就一头雾水了。
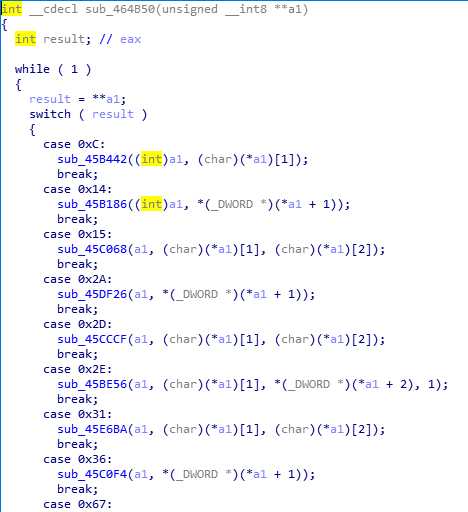
这没得分析(后来才知道是VM处理过的),于是打开OD输入012345678901234567891234,试试看(之前做过一个逆向题,印象深刻,那也是对字符串进行变换的函数,再IDA中查看,根本看不明白,拿到OD里面一跑,才知道,原来就是个base64编码啊。╮(╯▽╰)╭)经过变换,如下图所示。
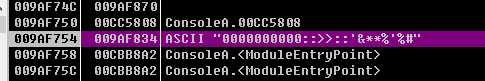
我做过的逆向题不多,根据以往的经验,在IDA中看不懂,或者是不是很理解的情况下,在OD中跟进调试一下,往往会有所收获。所以就跟进了这个函数。结果,不会就是不会,一点办法都没有。╮(╯_╰)╭。之后,也是在调试的时候偶然把上图的字符串(即0000000000::>>::‘&**%‘%#)当作输入,进行调试,结果发现返回的竟是012345678901234567891234。当时没有细想,没感觉有什么大不了的。后来才猛然间醒悟,如果知道了正确的输入,先输入进去,得到加密后的字符串,这不就是flag了吗?于是有了往下做下去的动力。
接着分析。
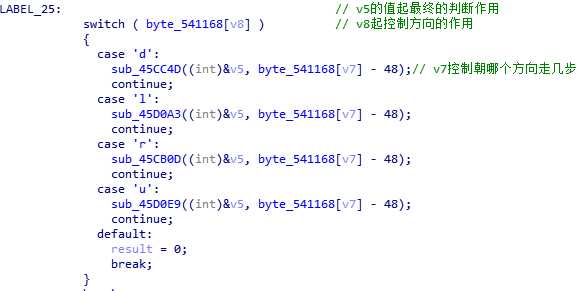
再来打开其中的45CC4D函数。(其中的注释是后来看了别人的WP加的)。

之前做过类似的迷宫逆向题,知道得有一张“地图”,可找了半天也没发现。再者这个函数里面套函数,这种return,实在绕的头疼,最后还是看了别人的WP,找了找思路。原来得在if语句这里,写一个IDC内置脚本(第一次接触)。
这个脚本很容易理解。然后的话,四个函数里面的数组都是不一样的,然后一个个把Dword中的地址改掉,dump出“地图”来就行了。
1 auto i; 2 for(i=0;i<26*12;i++){ 3 if(Dword(0x540548+4*i)^Dword(0x540068+4*i)) 4 Message("0,"); 5 else Message("1,"); 6 }
我用的python,它处理字符串不能够直接修改某个位置上的值,所以用C写会舒服一些。
1 up=‘0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0‘.replace(‘,‘,‘‘) 2 down=‘1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0‘.replace(‘,‘,‘‘) 3 left=‘0,1,0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1‘.replace(‘,‘,‘‘) 4 right=‘0,0,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,0,1,0,0,0,1,0,0,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,1,1,1,0,0,0,1,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,1,1,0,0,0,0,0,1,1,1,1,1,0,0,0,0,0,1,1,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,1,0,0,0,1,1,1,1,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,1,1,1,1,1,0‘.replace(‘,‘,‘‘) 5 tmp=‘~`-.‘ 6 for i in range(len(up)): 7 if i%26==0: 8 print ‘\\n‘ 9 if up[i]==‘1‘: 10 tmp=tmp.replace(‘~‘,‘U‘) 11 if down[i]==‘1‘: 12 tmp=tmp.replace(‘`‘,‘D‘) 13 if left[i]==‘1‘: 14 tmp=tmp.replace(‘-‘,‘L‘) 15 if right[i]==‘1‘: 16 tmp=tmp.replace(‘.‘,‘R‘) 17 print tmp+‘ ‘, 18 tmp=‘~`-.‘
最后在画图里面打开对应着地图,把路线画出来。
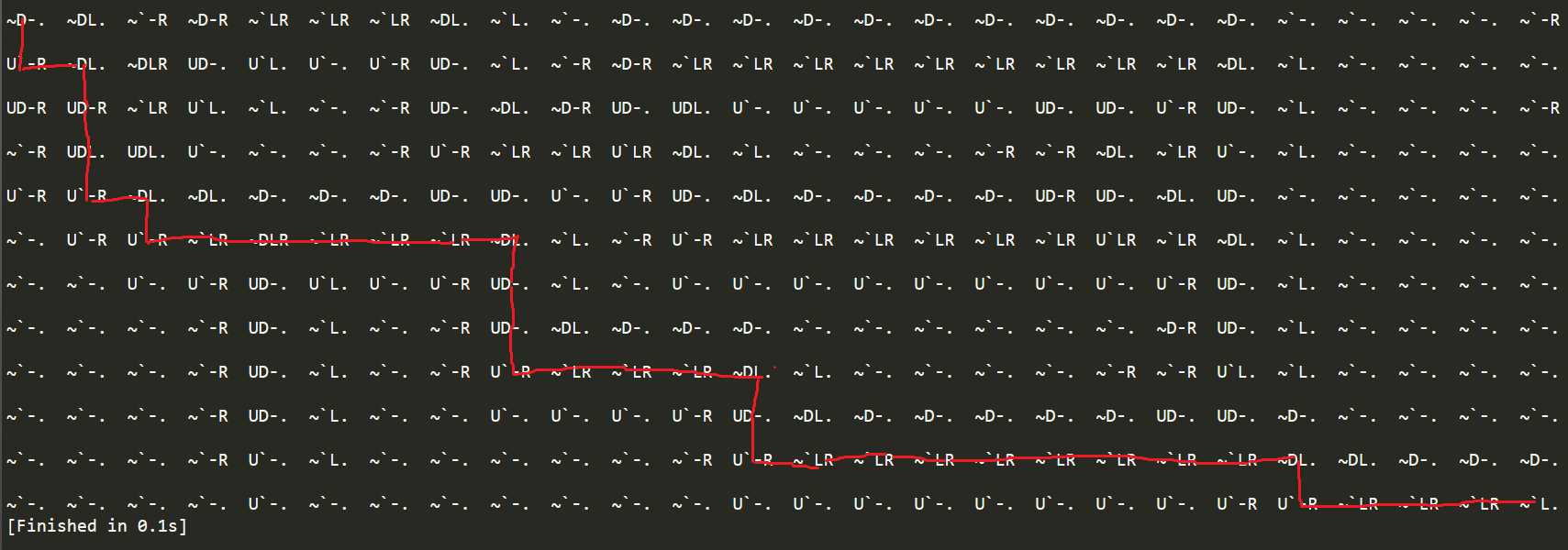
0-d
2-l
3-r
4-u
06260826062b0829072e0629
然后按照之前的想法,把06260826062b0829072e0629输进去,得到加密后的字符串,这个字符串再重新输入回去,成功,如下图。
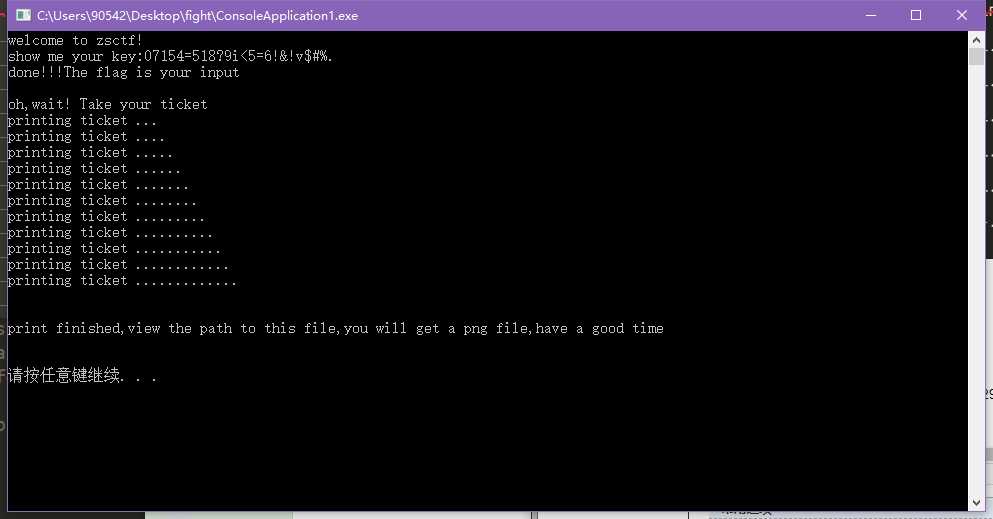
给了张二维码,说是最终flag要加作者的名字。到此结束。
最后感觉这个题,自己感觉还是挺有趣的,其实我如果之前接触过IDC的话,不看别人的WP也会自己做出来的。
以上是关于BUGKU (Take the maze)的主要内容,如果未能解决你的问题,请参考以下文章