华为防火墙综合实验
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了华为防火墙综合实验相关的知识,希望对你有一定的参考价值。
华为防火墙综合实验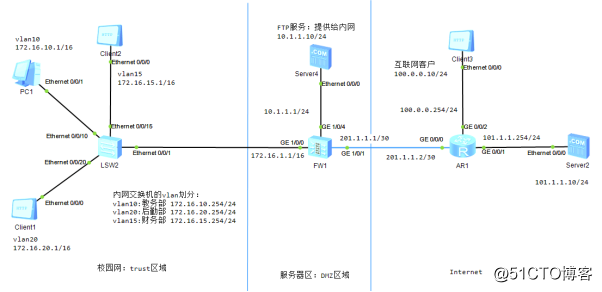
设计需求:
1:局域网需求
(1)vlan的设计
vlan10,教务部,网络地址为172.16.10.0/24
vlan20,后勤部,网络地址为172.16.20.0/24
vlan15,财务部,网络地址为172.16.15.0/24
(2)资源访问
要求教务部和后勤部可以上网,并且可以访问DMZ区域的FTP和WEB服务
财务部不能和其他vlan通信,也不能上网,但是能够访问DMZ区域的FTP和WEB服务
2:防火墙安全区域的设计
防火墙接口G1/0/0加入到trust区域
防火墙接口G1/0/4和G1/0/5加入DMZ区域
G1/0/1加入untrust区域
3:互联网用户访问内网服务器的设计
要求在互联网上能够访问DMZ区域中的WEB服务,但不能访问它的FTP服务
配置步骤:
1:内网二层交换机配置
<Huawei>undo terminal monitor
<Huawei>sys
[Huawei]sysname S2
[S2]
[S2]vlan batch 10 15 20
[S2]
[S2]int e0/0/10
[S2-Ethernet0/0/10]port link-type hybrid
[S2-Ethernet0/0/10]port hybrid pvid vlan 10
[S2-Ethernet0/0/10]port hybrid untagged vlan 10 20
[S2-Ethernet0/0/10]quit
[S2]
[S2]int g0/0/20
[S2-Ethernet0/0/20]port link-type hybrid
[S2-Ethernet0/0/20]port hybrid pvid vlan 20
[S2-Ethernet0/0/20]port hybrid untagged vlan 10 20
[S2-Ethernet0/0/20]quit
[S2]
[S2]int g0/0/15
[S2-Ethernet0/0/15]port link-type hybrid
[S2-Ethernet0/0/15]port hybrid pvid vlan 15
[S2-Ethernet0/0/15]port hybrid untagged vlan 1 15
[S2-Ethernet0/0/15]quit
[S2]
[S2]int g0/0/1
[S2-Ethernet0/0/1]port link-type hybrid
[S2-Ethernet0/0/1]port hybrid pvid vlan 1
[S2-Ethernet0/0/1]port hybrid untagged vlan 1 10 15 20
[S2-Ethernet0/0/1]quit
[S2]
2:运营商路由器的IP地址的设置
<Huawei>undo terminal monitor
<Huawei>sys
[Huawei]sysname R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 201.1.1.2 30
[R1-GigabitEthernet0/0/0]quit
[R1]
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 101.1.1.254 24
[R1-GigabitEthernet0/0/1]quit
[R1]
[R1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip add 100.0.0.254 24
[R1-GigabitEthernet0/0/2]quit
[R1]
2:防火墙设置
(1)Ip地址的设置
<USG6000V1>undo terminal monitor
<USG6000V1>sys
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 172.16.1.1 16
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 201.1.1.1 30
[USG6000V1-GigabitEthernet1/0/1]quit
[USG6000V1]
[USG6000V1]int g1/0/4
[USG6000V1-GigabitEthernet1/0/4]ip add 10.1.1.1 24
[USG6000V1-GigabitEthernet1/0/4]quit
[USG6000V1]
(2)安全区域的设置
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g1/0/0
[USG6000V1-zone-trust]quit
[USG6000V1]
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]add int g1/0/4
[USG6000V1-zone-dmz]quit
[USG6000V1]
[USG6000V1]firewall zone name untrust
[USG6000V1-zone-jiaoyu]add int g1/0/1
[USG6000V1-zone-jiaoyu]quit
[USG6000V1]
(3)设置安全策略,使内网用户可以访问dmz区域的FTP服务和WEB服务
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_1
[USG6000V1-policy-security-rule-sec_1]source-zone trust
[USG6000V1-policy-security-rule-sec_1]destination-zone dmz
[USG6000V1-policy-security-rule-sec_1]service ftp
[USG6000V1-policy-security-rule-sec_1]service http
[USG6000V1-policy-security-rule-sec_1]action permit
[USG6000V1-policy-security-rule-sec_1]quit
[USG6000V1-policy-security]quit
[USG6000V1]
(4)设置安全策略,使内网用户可以访问互联网,并且阻止财务部上网
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_2
[USG6000V1-policy-security-rule-sec_3]source-zone trust
[USG6000V1-policy-security-rule-sec_2]source-address 172.16.20.0 24
[USG6000V1-policy-security-rule-sec_2]source-address 172.16.10.0 24
[USG6000V1-policy-security-rule-sec_3]destination-zone untrust
[USG6000V1-policy-security-rule-sec_3]action permit
[USG6000V1-policy-security-rule-sec_3]quit
[USG6000V1-policy-security]quit
[USG6000V1]
(5)设置安全策略,使互联网用户能够访问DMZ区域的WEB服务
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_3
[USG6000V1-policy-security-rule-sec_3]source-zone untrust
[USG6000V1-policy-security-rule-sec_3]destination-zone dmz
[USG6000V1-policy-security-rule-sec_3]destination-address 10.1.1.0 24
[USG6000V1-policy-security-rule-sec_3]service http
[USG6000V1-policy-security-rule-sec_3]action permit
[USG6000V1-policy-security-rule-sec_3]quit
[USG6000V1-policy-security]quit
[USG6000V1]
(6)配置防火墙默认路由
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 201.1.1.2
(7)配置nat
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name nat_policy
[USG6000V1-policy-nat-rule-nat_policy]source-address 172.16.0.0 16
[USG6000V1-policy-nat-rule-nat_policy]source-zone trust
[USG6000V1-policy-nat-rule-nat_policy]destination-zone untrust
[USG6000V1-policy-nat-rule-nat_policy]action nat easy-ip
[USG6000V1-policy-nat-rule-nat_policy]quit
[USG6000V1-policy-nat]quit
[USG6000V1]
[USG6000V1]nat server natserver_web protocol tcp global 200.0.0.1 80 inside 10.1.1.10 80 no-reverse
[USG6000V1]ip route-static 200.0.0.1 32 NULL 0
在运营商的路由器上配置前往200.0.0.1的;路由
ip route-static 200.0.0.0 24 201.1.1.1
3:验证访问
略
以上是关于华为防火墙综合实验的主要内容,如果未能解决你的问题,请参考以下文章