160个crackme 009 Andrénalin.2
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了160个crackme 009 Andrénalin.2相关的知识,希望对你有一定的参考价值。
说实话,这个crackme做的我十分恼火...
好吧,开始:
伪码检验: 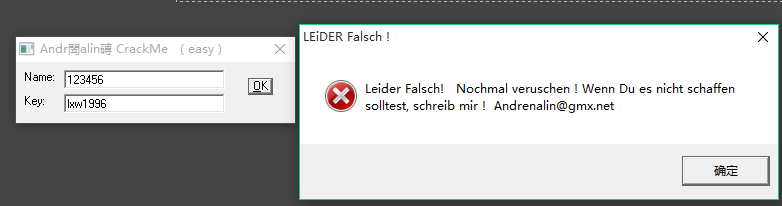
出来的对话框是什么鬼.
OD查找参考文本字符串,后我查了一下这几个奇怪的字符串的翻译: 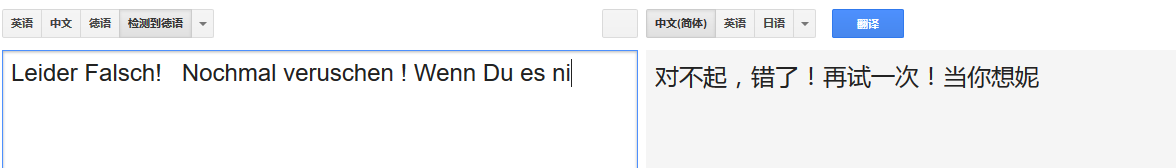
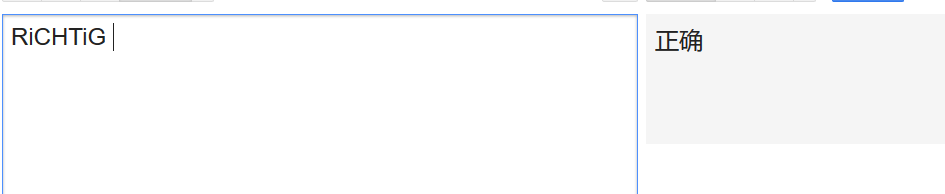
德文..作者像是个德国人...
我们定位到字符串的关键位置,向上发现 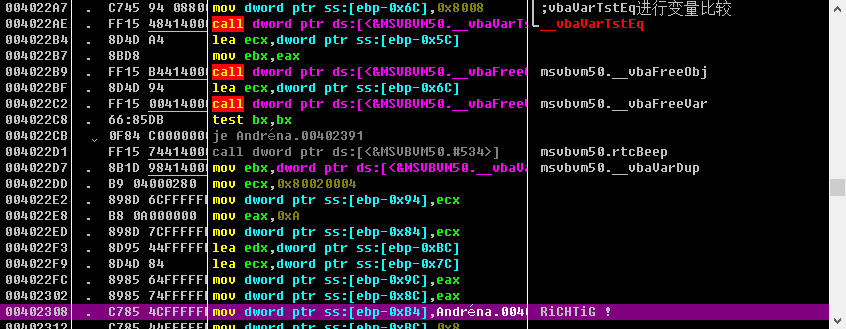
VbaVarTstEq 变量比较函数
于是看到跳转位置,搞清楚关系后,全部nop掉,把程序改名后dump出来,无脑爆破掉了: 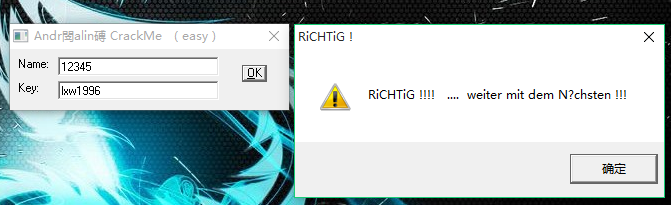
OK,找算法,首先,不熟悉VB API函数的去自行百度博客,照着博客上的一边查,一边做:
004020EC . 8D55 BC lea edx,dword ptr ss:[ebp-0x44] 004020EF . 51 push ecx ; /Step8 = 0019F228 004020F0 . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] ; | 004020F3 . BB 02000000 mov ebx,0x2 ; | 004020F8 . 52 push edx ; |/var18 = 00000058 004020F9 . 50 push eax ; ||retBuffer8 = 0019F228 004020FA . 899D 54FFFFFF mov dword ptr ss:[ebp-0xAC],ebx ; || 00402100 . 899D 44FFFFFF mov dword ptr ss:[ebp-0xBC],ebx ; || 00402106 . FF15 18414000 call dword ptr ds:[<&MSVBVM50.__vbaLenVa>; |\__vbaLenVar 0040210C . 8D8D 44FFFFFF lea ecx,dword ptr ss:[ebp-0xBC] ; | 00402112 . 50 push eax ; |End8 = 0019F228 00402113 . 8D95 E8FEFFFF lea edx,dword ptr ss:[ebp-0x118] ; | 00402119 . 51 push ecx ; |Start8 = 0019F228 0040211A . 8D85 F8FEFFFF lea eax,dword ptr ss:[ebp-0x108] ; | 00402120 . 52 push edx ; |TMPend8 = 00000058 00402121 . 8D4D DC lea ecx,dword ptr ss:[ebp-0x24] ; | 00402124 . 50 push eax ; |TMPstep8 = 0019F228 00402125 . 51 push ecx ; |Counter8 = 0019F228 00402126 . FF15 20414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>; \__vbaVarForInit 0040212C . 8B3D 04414000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaFr>; msvbvm50.__vbaFreeVarList 00402132 > 85C0 test eax,eax 00402134 . 0F84 9C000000 je Andréna.004021D6 0040213A . 8D55 94 lea edx,dword ptr ss:[ebp-0x6C] 0040213D . 8D45 DC lea eax,dword ptr ss:[ebp-0x24] 00402140 . 52 push edx 00402141 . 50 push eax 00402142 . C745 9C 01000>mov dword ptr ss:[ebp-0x64],0x1 00402149 . 895D 94 mov dword ptr ss:[ebp-0x6C],ebx 0040214C . FF15 90414000 call dword ptr ds:[<&MSVBVM50.__vbaI4Var>; msvbvm50.__vbaI4Var 00402152 . 8D4D BC lea ecx,dword ptr ss:[ebp-0x44] ; |;字符串转化成长整型,EAX在此处莫名自加 00402155 . 50 push eax ; |Start = 0x19F228 00402156 . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] ; | 00402159 . 51 push ecx ; |dString8 = 0019F228 0040215A . 52 push edx ; |RetBUFFER = 00000058 0040215B . FF15 38414000 call dword ptr ds:[<&MSVBVM50.#632>] ; \rtcMidCharVar 00402161 . 8D45 84 lea eax,dword ptr ss:[ebp-0x7C] ; ;rtcMidCharVar ->截取字符串,VB中的MID函数,用法MID(“字符串”,”开始的位置”,”取几个字符”) 00402164 . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 00402167 . 50 push eax ; /String8 = 0019F228 00402168 . 51 push ecx ; |ARG2 = 0019F228 00402169 . FF15 70414000 call dword ptr ds:[<&MSVBVM50.__vbaStrVa>; \__vbaStrVarVal 0040216F . 50 push eax ; /String = "" 00402170 . FF15 0C414000 call dword ptr ds:[<&MSVBVM50.#516>] ; \rtcAnsiValueBstr 00402176 . 66:8985 4CFFF>mov word ptr ss:[ebp-0xB4],ax ; ;获取字符串中特定位置的字符转换成Ascii码 0040217D . 8D55 CC lea edx,dword ptr ss:[ebp-0x34] 00402180 . 8D85 44FFFFFF lea eax,dword ptr ss:[ebp-0xBC] 00402186 . 52 push edx ; /var18 = 00000058 00402187 . 8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C] ; | 0040218D . 50 push eax ; |var28 = 0019F228 0040218E . 51 push ecx ; |saveto8 = 0019F228 0040218F . 899D 44FFFFFF mov dword ptr ss:[ebp-0xBC],ebx ; | 00402195 . FF15 94414000 call dword ptr ds:[<&MSVBVM50.__vbaVarAd>; \__vbaVarAdd 0040219B . 8BD0 mov edx,eax 0040219D . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] 004021A0 . FFD6 call esi ; msvbvm50.__vbaVarMove 004021A2 . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 004021A5 . FF15 B8414000 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>; msvbvm50.__vbaFreeStr 004021AB . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] 004021AE . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] 004021B1 . 52 push edx 004021B2 . 50 push eax 004021B3 . 53 push ebx 004021B4 . FFD7 call edi ; msvbvm50.__vbaFreeVarList 004021B6 . 83C4 0C add esp,0xC 004021B9 . 8D8D E8FEFFFF lea ecx,dword ptr ss:[ebp-0x118] 004021BF . 8D95 F8FEFFFF lea edx,dword ptr ss:[ebp-0x108] 004021C5 . 8D45 DC lea eax,dword ptr ss:[ebp-0x24] 004021C8 . 51 push ecx ; /TMPend8 = 0019F228 004021C9 . 52 push edx ; |TMPstep8 = 00000058 004021CA . 50 push eax ; |Counter8 = 0019F228 004021CB . FF15 AC414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>; \__vbaVarForNext 004021D1 .^ E9 5CFFFFFF jmp Andréna.00402132 ; ;重复执行循环结构 004021D6 > 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] 004021D9 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC] 004021DF . 51 push ecx ; /var18 = 0019F228 004021E0 . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] ; | 004021E3 . 52 push edx ; |var28 = 00000058 004021E4 . 50 push eax ; |SaveTo8 = 0019F228 004021E5 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],0x499602D2 ; | 004021EF . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x3 ; | 004021F9 . FF15 5C414000 call dword ptr ds:[<&MSVBVM50.__vbaVarMu>; \__vbaVarMul 004021FF . 8BD0 mov edx,eax ; ;两个变量相乘 00402201 . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] ; ;储存结果的地址 00402204 . FFD6 call esi ; msvbvm50.__vbaVarMove 00402206 . 8B1D A0414000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaMi>; msvbvm50.__vbaMidStmtVar 0040220C . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
实在抱歉,OD分析VB实在不怎么样,而且VB这种奇葩的传参方式,我也是看的云里雾里,于是我只能 VB Decomplier:
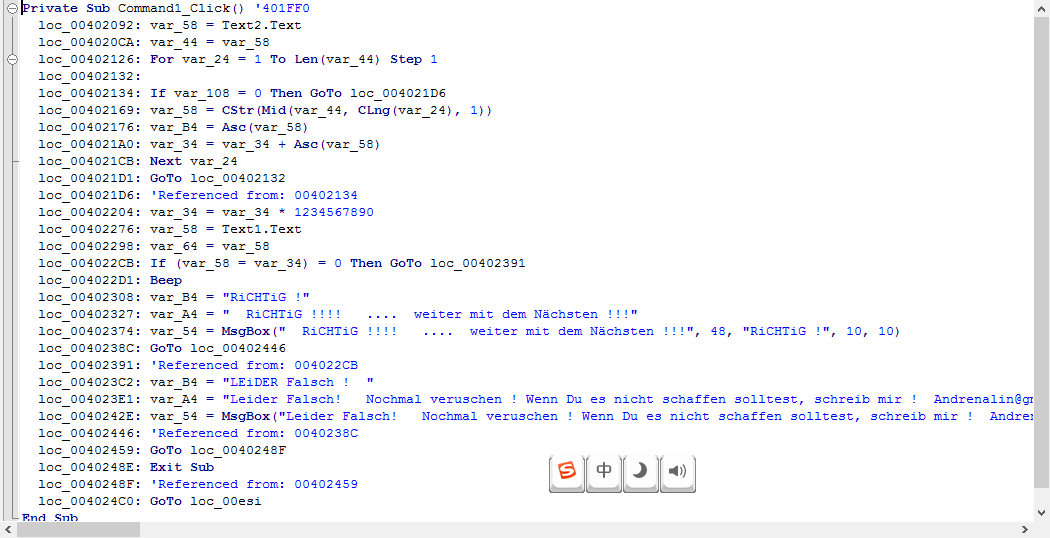
分析代码:
Private Sub Command1_Click() ‘401FF0 loc_00402092: var_58=Text2.Text;输入的name字符串 loc_004020CA: var_44=var_58 loc_00402126: For var_24 =1To Len(var_44) Step 1 ;for(i=1;i<=strlen(var_44);i++) step是循环的步长 loc_00402132: loc_00402134: If var_108 = 0 Then GoTo loc_004021D6 loc_00402169: var_58=CStr(Mid(var_44, CLng(var_24), 1)) loc_00402176: var_B4=Asc(var_58) loc_004021A0: var_34=var_34+Asc(var_58) ;将name的每一个字节转化成Ascii码之后累加放到Var34中 loc_004021CB: Next var_24 loc_004021D1: GoTo loc_00402132 loc_004021D6: ‘Referenced from: 00402134 loc_00402204: var_34=var_34*1234567890 ;VbaVarMul 变量相乘。 loc_00402276: var_58=Text1.Text loc_00402298: var_64=var_58 loc_004022CB: If (var_58=var_34) =0 Then GoTo loc_00402391;如果输入的serial和正确的serial不相等,跳转到错误语句框处 loc_004022D1: Beep loc_00402308: var_B4 = "RiCHTiG !" loc_00402327: var_A4 = " RiCHTiG !!!! .... weiter mit dem N?chsten !!!" loc_00402374: var_54 = MsgBox(" RiCHTiG !!!! .... weiter mit dem N?chsten !!!", 48, "RiCHTiG !", 10, 10) loc_0040238C: GoTo loc_00402446 loc_00402391: ‘Referenced from: 004022CB loc_004023C2: var_B4="LEiDER Falsch ! " loc_004023E1: var_A4="Leider Falsch! Nochmal veruschen ! Wenn Du es nicht schaffen solltest, schreib mir ! [email protected]" loc_0040242E: var_54=MsgBox("Leider Falsch! Nochmal veruschen ! Wenn Du es nicht schaffen solltest, schreib mir ! [email protected]", 16, "LEiDER Falsch ! ", 10, 10) loc_00402446: ‘Referenced from: 0040238C loc_00402459: GoTo loc_0040248F loc_0040248E: Exit Sub loc_0040248F: ‘Referenced from: 00402459 loc_004024C0: GoTo loc_00esi End Sub
大致对流程分析清楚了
0040214C . FF15 90414000 call dword ptr ds:[<&MSVBVM50.__vbaI4Var>; msvbvm50.__vbaI4Var 00402152 . 8D4D BC lea ecx,dword ptr ss:[ebp-0x44] ; |;字符串转化成长整型,EAX在此处莫名自加 00402155 . 50 push eax ; |Start = 0x19F228 00402156 . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] ; | 00402159 . 51 push ecx ; |dString8 = 0019F228 0040215A . 52 push edx ; |RetBUFFER = 00000058 0040215B . FF15 38414000 call dword ptr ds:[<&MSVBVM50.#632>] ; \rtcMidCharVar 00402161 . 8D45 84 lea eax,dword ptr ss:[ebp-0x7C] ; ;rtcMidCharVar ->截取字符串,VB中的MID函数,用法MID(“字符串”,”开始的位置”,”取几个字符”) 00402164 . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 00402167 . 50 push eax ; /String8 = 0019F228 00402168 . 51 push ecx ; |ARG2 = 0019F228 00402169 . FF15 70414000 call dword ptr ds:[<&MSVBVM50.__vbaStrVa>; \__vbaStrVarVal 0040216F . 50 push eax ; /String = "" 00402170 . FF15 0C414000 call dword ptr ds:[<&MSVBVM50.#516>] ; \rtcAnsiValueBstr 00402176 . 66:8985 4CFFF>mov word ptr ss:[ebp-0xB4],ax ; ;获取字符串中特定位置的字符转换成Ascii码 0040217D . 8D55 CC lea edx,dword ptr ss:[ebp-0x34] 00402180 . 8D85 44FFFFFF lea eax,dword ptr ss:[ebp-0xBC] 00402186 . 52 push edx ; /var18 = 00000058 00402187 . 8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C] ; | 0040218D . 50 push eax ; |var28 = 0019F228 0040218E . 51 push ecx ; |saveto8 = 0019F228 0040218F . 899D 44FFFFFF mov dword ptr ss:[ebp-0xBC],ebx ; | 00402195 . FF15 94414000 call dword ptr ds:[<&MSVBVM50.__vbaVarAd>; \__vbaVarAdd 0040219B . 8BD0 mov edx,eax 0040219D . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] 004021A0 . FFD6 call esi ; msvbvm50.__vbaVarMove 004021A2 . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 004021A5 . FF15 B8414000 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>; msvbvm50.__vbaFreeStr 004021AB . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] 004021AE . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] 004021B1 . 52 push edx 004021B2 . 50 push eax 004021B3 . 53 push ebx 004021B4 . FFD7 call edi ; msvbvm50.__vbaFreeVarList 004021B6 . 83C4 0C add esp,0xC 004021B9 . 8D8D E8FEFFFF lea ecx,dword ptr ss:[ebp-0x118] 004021BF . 8D95 F8FEFFFF lea edx,dword ptr ss:[ebp-0x108] 004021C5 . 8D45 DC lea eax,dword ptr ss:[ebp-0x24] 004021C8 . 51 push ecx ; /TMPend8 = 0019F228 004021C9 . 52 push edx ; |TMPstep8 = 00000058 004021CA . 50 push eax ; |Counter8 = 0019F228 004021CB . FF15 AC414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>; \__vbaVarForNext 004021D1 .^ E9 5CFFFFFF jmp Andréna.00402132 ; ;重复执行循环结构这个循环中,将name的每一个字符取出来,转化成Acsii码后相加
004021DF . 51 push ecx ; /var18 = 0019F228 004021E0 . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] ; | 004021E3 . 52 push edx ; |var28 = 00000058 004021E4 . 50 push eax ; |SaveTo8 = 0019F228 ;十进制就是1234567890 004021E5 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],0x499602D2 ; | 004021EF . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x3 ; | 004021F9 . FF15 5C414000 call dword ptr ds:[<&MSVBVM50.__vbaVarMu>; \__vbaVarMul 004021FF . 8BD0 mov edx,eax ; ;两个变量相乘 00402201 . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] ; ;储存结果的地址 00402204 . FFD6 call esi ; msvbvm50.__vbaVarMove 00402206 . 8B1D A0414000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaMi>; msvbvm50.__vbaMidStmtVar
之后的结果与1234567890(Dec)相乘,结果存放在 ss:[ebp-0x34] 中,这是个重点关注的地址,我们Crtl+G过去:
发现地址位置里,什么可看不出来,于是再看看这个vbaVarMul()函数,乘了这么大的数1234567890,应该是存不下去的,应该是转成浮点数了,右键,64bit double
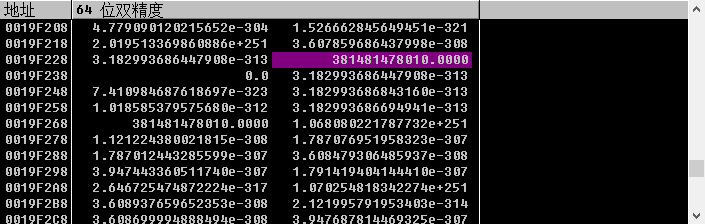
检验一下:
(0x31+0x32+0x33+0x34+0x35+0x36)*1234567890
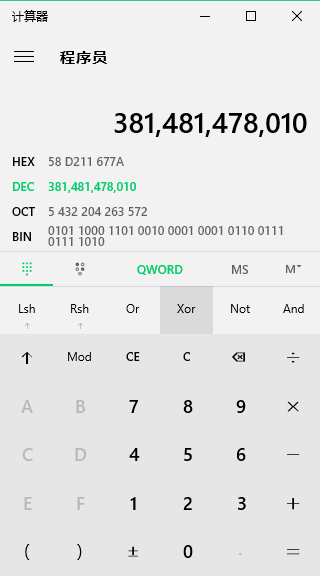
的确是,这个地址需要好好关注。
继续,就有点懵:
0040220C . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] 0040220F . 51 push ecx 00402210 . 6A 04 push 0x4 00402212 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC] 00402218 . 6A 01 push 0x1 0040221A . 52 push edx 0040221B . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>; - 00402225 . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8 0040222F . FFD3 call ebx ; <&MSVBVM50.__vbaMidStmtVar> 00402231 . 8D45 CC lea eax,dword ptr ss:[ebp-0x34] 00402234 . 8D8D 54FFFFFF lea ecx,dword ptr ss:[ebp-0xAC] 0040223A . 50 push eax 0040223B . 6A 09 push 0x9 0040223D . 6A 01 push 0x1 0040223F . 51 push ecx 00402240 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>; - 0040224A . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8 00402254 . FFD3 call ebx 00402256 . 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
vbaMidStmtVar()这个函数,查遍了百度,没什么结果,于是,我就只能借鉴了一下别人的weiteup...好吧,请不要喷我:
原来是插入,其中有一个参数是更改指定位置的字符串的字符
00402210 . 6A 04 push 0x4 00402212 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC] 00402218 . 6A 01 push 0x1 0040221A . 52 push edx 0040221B . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>;
在0x4的字符改成“-”
0040223B . 6A 09 push 0x9 0040223D . 6A 01 push 0x1 0040223F . 51 push ecx 00402240 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>; - 0040224A . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8 00402254 . FFD3 call ebx 00402256 . 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
在0x9的字符改成“-”
最后,就是比较函数:
0040229E . 50 push eax ; /var18 = 0019F260 0040229F . 51 push ecx ; |var28 = 59DE8000 004022A0 . C745 A8 00000>mov dword ptr ss:[ebp-0x58],0x0 ; | 004022A7 . C745 94 08800>mov dword ptr ss:[ebp-0x6C],0x8008 ; |;vbaVarTstEq进行变量比较 004022AE . FF15 48414000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>; \__vbaVarTstEq 004022B4 . 8D4D A4 lea ecx,dword ptr ss:[ebp-0x5C] 004022B7 . 8BD8 mov ebx,eax
两个 参数:
var18 = 0019F260
var28 = 59DE8000
一个是我们输入的name的存储地址lxw1996,另一个是上面提到的很重要的,serial的地址,这个地址,经过一些变化,在我们的伪码中,结果应该是:
381-8147-010
检验一下:
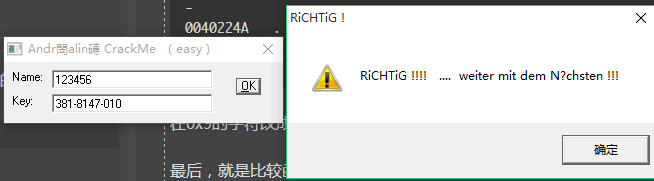
成功了,好吧,姑且算是搞定了吧,注册机:
Python:
names=raw_input("Please input your name:") len1=names.__len__() result=0 i=0 while i<len1: result=result+ord(names[i]) i=i+1 result=result*1234567890 print result serial=str(result) l=list(serial) print l l[3]=‘-‘ l[8]=‘-‘ new= ‘‘.join(l) print new
看到了差距,还要努力,工具是一方面,没有工具就不逆向了吗?
以上是关于160个crackme 009 Andrénalin.2的主要内容,如果未能解决你的问题,请参考以下文章