交换安全三宝(DHCP Snooping+IPSG+DAI)简单实验
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了交换安全三宝(DHCP Snooping+IPSG+DAI)简单实验相关的知识,希望对你有一定的参考价值。
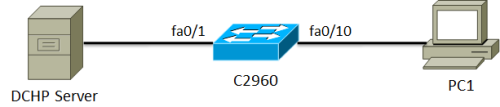
1 实验拓扑图
2 DHCP Snooping
2.1 基本DHCP Snooping配置:
C2960#show running-config
Building configuration...
!
ipdhcp snooping vlan 10
ipdhcp snooping
!
interface FastEthernet0/1
description ---Connected to DHCP_Server ---
switchportaccess vlan 10
switchport modeaccess
spanning-treeportfast
spanning-treebpduguard enable
ip dhcp snoopingtrust
!
interface FastEthernet0/10
description ---Connected to PC1 ---
switchportaccess vlan 10
switchport modeaccess
spanning-treeportfast
spanning-treebpduguard enable
!
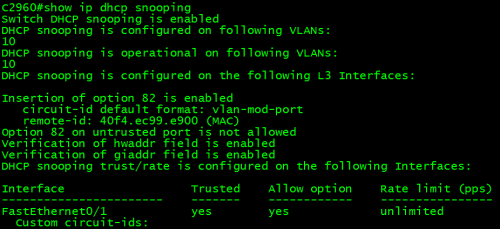
2.2 验证DHCP Snooping效果:
一、首先,PC能够正常通过DHCP获取到IP地址:
二、C2960上验证DHCP Snooping效果:
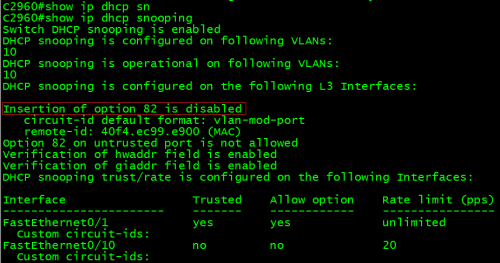
C2960#showip dhcp snooping
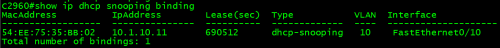
C2960#showip dhcp snooping binding
注:此绑定表非常关键,是后续IPSG和DAI的基础。
2.3 扩展DHCP Snooping配置:
(一)指定DHCP Snooping绑定数据库的位置
注:如果想写到外部数据库,必须先写到本地,否则不成功。
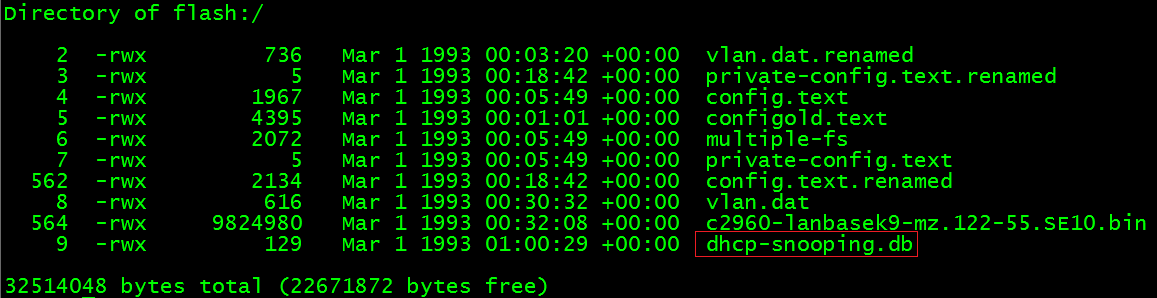
C2960(config)#ip dhcp snooping databaseflash:/dhcp-snooping.db
01:00:28: %DHCP_SNOOPING-4-DHCP_SNOOPING_DATABASE_FLASH_WARNING:Saving DHCP snooping bindings to flash can fill up your device causing thewrites of bindings to device, to fail.
01:00:29: %DHCP_SNOOPING-4-NTP_NOT_RUNNING: NTP is notrunning; reloaded binding lease expiration times are incorrect.
01:00:29: %DHCP_SNOOPING-6-AGENT_OPERATION_SUCCEEDED:DHCP snooping database Write succeeded.
(二)限制端口接收DHCP包的速率
C2960(config)#interface f0/10
C2960(config-if)#ip dhcp snooping limit rate 20
(三)DHCP 选项82的处理
1、关闭82选项
C2960(config)#no ip dhcp snooping information option
C2960#showip dhcp snooping
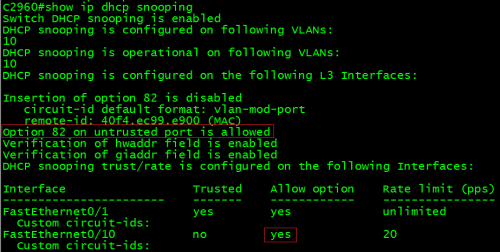
2、允许从untrust接口接收插入了82选项的DHCP报文
C2960(config)#ip dhcp snooping information optionallow-untrusted
C2960#showip dhcp snooping
3 IP Source Guard
2.1 基本IPSG配置:
C2960#show running-config interface f0/10
Building configuration...
Current configuration : 423 bytes
!
interface FastEthernet0/10
description ---Connected to PC1 ---
switchportaccess vlan 10
switchport modeaccess
switchportport-security maximum 10
switchportport-security
switchportport-security mac-address sticky
switchportport-security mac-address sticky 54ee.7535.bb02 vlan access
spanning-treeportfast
spanning-treebpduguard enable
ip verify sourceport-security
ip dhcpsnooping limit rate 20
end
2.2 验证IPSG效果:
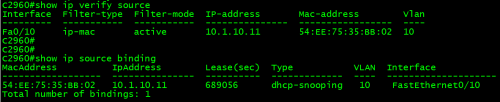
一、交换机上形成了IPSG绑定表
C2960#showip verify source
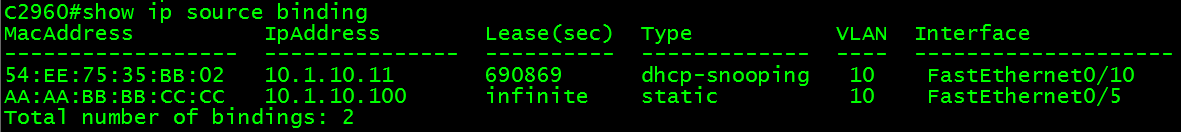
C2960#showip source binding
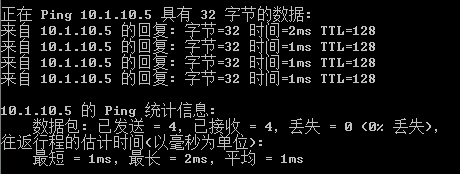
二、此时PC能够和外界正常通信
注:经过实验,此时如果将PC1改为手动设置IP(仍为10.1.10.11),则2960的DHCP Snooping绑定表马上消失,IPSG绑定表也随之消失,导致此时PC1无法和外界通信。
2.3 扩展IPSG配置:
(一)手工配置IPSG绑定表
C2960(config)#ip source bindingAAAA.BBBB.CCCC vlan 10 10.1.10.100 interface Fa0/5
C2960#showip source binding
3 Dynamic ARP Inspection
2.1 基本DAI配置:
C2960#show running-config
Building configuration...
!
interface FastEthernet0/1
description ---Connected to DHCP_Server ---
switchportaccess vlan 10
switchport modeaccess
ip arp inspectiontrust
spanning-treeportfast
spanning-treebpduguard enable
ip dhcpsnooping trust
!
iparp inspection vlan 10
iparp inspection validate src-mac dst-mac ip
!
2.2 验证DAI效果:
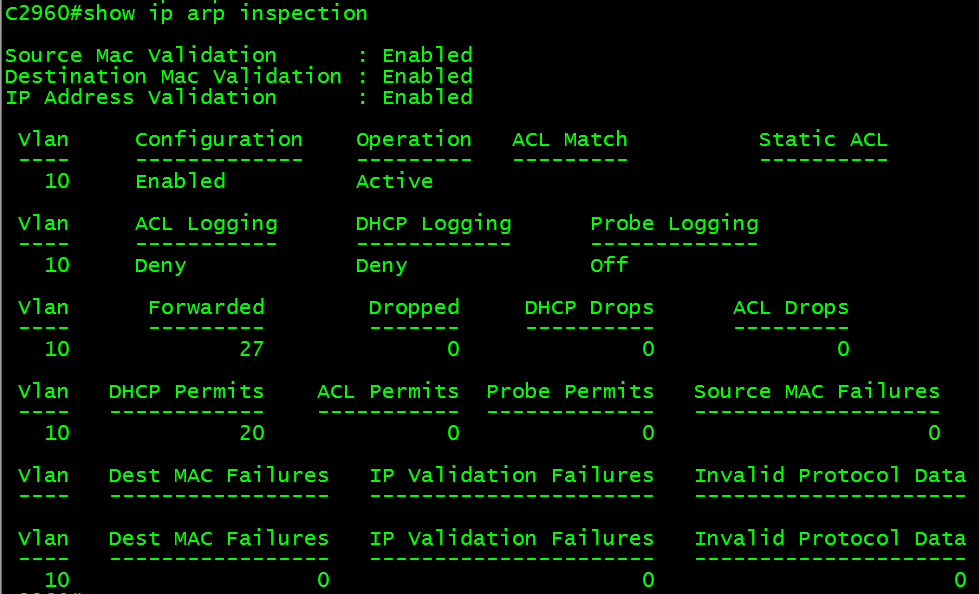
C2960#show ip arp inspection
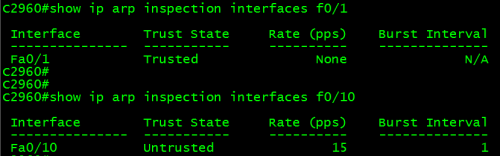
C2960#showip arp inspection interface f0/1
2.3 扩展DAI配置:
(一)限制端口接收ARP报文的速率
C2960(config)#interface fastEthernet 0/10
C2960(config-if)#ip arp inspection limit rate 20
(二)配置ARP访问控制列表,主要是为了静态配置IP地址的主机,相当于做了手动的映射
C2960(config)#arp access-list TEST
C2960(config-arp-nacl)#permit ip host 10.1.10.20 machost aaaa.bbbb.cccc
C2960(config)#ip arp inspection filter TEST vlan 10
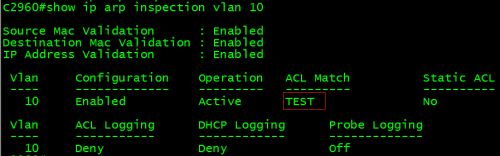
C2960#showip arp inspection vlan 10
(三)配置由于DAI导致err-disable的端口自动恢复
C2960(config)#errdisable recovery cause arp-inspection
C2960(config)#errdisable recovery interval 60
C2960#showerrdisable recovery
C2960最终配置:
C2960#show running-config
Building configuration...
Current configuration : 3001 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname C2960
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
system mtu routing 1500
!
!
ip dhcp snooping vlan 10
ip dhcp snooping
ip arp inspection vlan 10
ip arp inspection validate src-mac dst-mac ip
ip arp inspection filter TEST vlan 10
!
!
errdisable recovery cause arp-inspection
errdisable recovery interval 60
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
interface FastEthernet0/1
description ---Connected to DHCP_Server ---
switchportaccess vlan 10
switchport modeaccess
ip arpinspection trust
spanning-treeportfast
spanning-treebpduguard enable
ip dhcp snoopingtrust
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
description ---Connected to PC1 ---
switchportaccess vlan 10
switchport modeaccess
switchportport-security maximum 10
switchportport-security
switchportport-security mac-address sticky
switchportport-security mac-address sticky 54ee.7535.bb02 vlan access
ip arpinspection limit rate 20
spanning-treeportfast
spanning-treebpduguard enable
ip verifysource port-security
ip dhcpsnooping limit rate 20
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
!
interface FastEthernet0/24
!
interface FastEthernet0/25
!
interface FastEthernet0/26
!
interface FastEthernet0/27
!
interface FastEthernet0/28
!
interface FastEthernet0/29
!
interface FastEthernet0/30
!
interface FastEthernet0/31
!
interface FastEthernet0/32
!
interface FastEthernet0/33
!
interface FastEthernet0/34
!
interface FastEthernet0/35
!
interface FastEthernet0/36
!
interface FastEthernet0/37
!
interface FastEthernet0/38
!
interface FastEthernet0/39
!
interface FastEthernet0/40
!
interface FastEthernet0/41
!
interface FastEthernet0/42
!
interface FastEthernet0/43
!
interface FastEthernet0/44
!
interface FastEthernet0/45
!
interface FastEthernet0/46
!
interface FastEthernet0/47
!
interface FastEthernet0/48
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
no ip address
no iproute-cache
!
interface Vlan10
ip address10.1.10.254 255.255.255.0
!
ip http server
ip http secure-server
ip source binding AAAA.BBBB.CCCC vlan 10 10.1.10.100interface Fa0/5
!
arp access-list TEST
permit ip host10.1.10.20 mac host aaaa.bbbb.cccc
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
C2960#
本文出自 “点滴技术积累” 博客,转载请与作者联系!
以上是关于交换安全三宝(DHCP Snooping+IPSG+DAI)简单实验的主要内容,如果未能解决你的问题,请参考以下文章
h3c交换机如何配置DHCP服务器、DHCP中继、DAI和IPSG?