linux如何设置一般用户密码必须达到一定强度?还有3月强制更改一次密码?
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了linux如何设置一般用户密码必须达到一定强度?还有3月强制更改一次密码?相关的知识,希望对你有一定的参考价值。
如题
比如密码必须有一定位,有字母还必须有数字之类
3个月强制一般用户更改一次密码3个月到期后,更改密码时,一般用户自己操作,不需要管理员更改
另外,以下这种方法,在密码到期之后是一般用户自己修改密码,还是管理员修改密码?
[root@localhost ~]# vim /etc/login.defs
PASS_MAX_DAYS 99999 (最大什么时候过期)
PASS_MIN_DAYS 0 (最小什么事后过期)
PASS_MIN_LEN 5 (密码最小长度)
PASS_WARN_AGE 7 (警告天数)
1、首先使用的命令为:passwd。
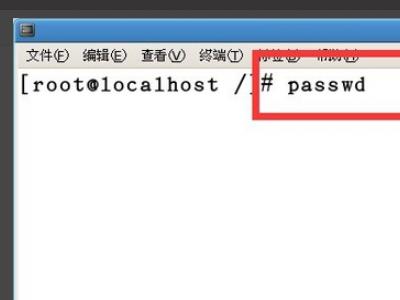
2、在终端输入passwd,然后回车,会让输入新的密码,在输入密码时,终端并不会显示出输入的密码,所以不要以为自己没有输入进去。
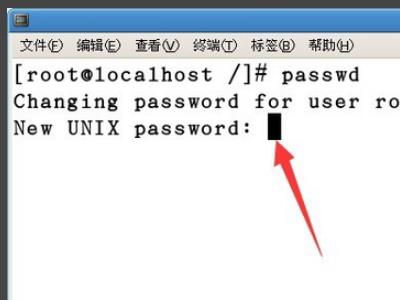
3、然后再次输入密码,进行密码确认。
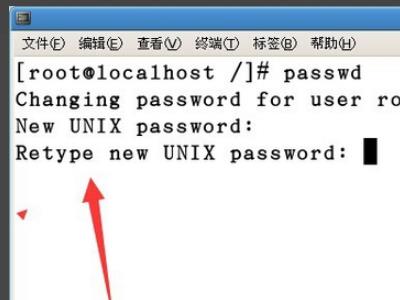
4、确认之后,就会提示更改密码成功。
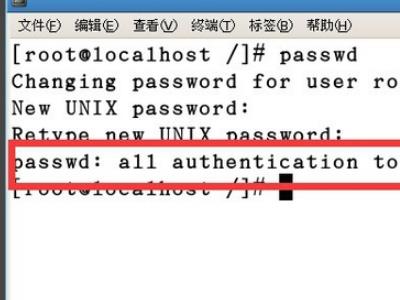
5、为了验证是否更改密码成功,没必要对系统进行重启,只需要更换用户就可以了。
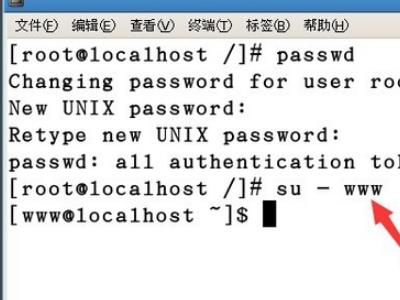
[root@localhost ~]# vim /etc/pam.d/system-auth里
找到password requisite pam_cracklib.so在后面可以加 difok=x(要x个不同字符) minlen=x(最小密码长度) ucredit=-x(最少x个大写字母) lcredit=-x(最少x个小写字母) dcredit=-x (最少x个数字)dictpath=/usr/share/cracklib/pw_dict
时间在
[root@localhost ~]# vim /etc/login.defs
PASS_MAX_DAYS 99999 (最大什么时候过期)
PASS_MIN_DAYS 0 (最小什么事后过期)
PASS_MIN_LEN 5 (密码最小长度)
PASS_WARN_AGE 7 (警告天数)
我们在使用linux系统设置密码的时候,经常遇到这样的问题,系统提示:您的密码太简单,或者您的密码是字典的一部分。那么系统是如何实现对用户的密码的复杂度的检查的呢?
系统对密码的控制是有两部分(我知道的)组成:
1 cracklib
2 login.defs
声明:login.defs主要是控制密码的有效期。对密码进行时间管理。此处不细谈
login.defs --shadow password suite configuration
pam_cracklib.so 才是控制密码复杂度的关键文件
redhat公司专门开发了cracklib这个安装包来判断密码的复杂度
可以rpm -ql cracklib查看
密码的复杂度的判断是通过pam模块控制来实现的,具体的模块是pam_cracklibpam_cracklib 的参数介绍:
debug
This option makes the module write information to syslog(3) indicating the behavior of the module (this option does not write password information to the log file).
type=XXX
The default action is for the module to use the following prompts when requesting passwords: "New UNIX password: " and "Retype UNIX password: ". The default word UNIX can be replaced with this option.
retry=N
Prompt user at most N times before returning with error. The default is 1
difok=N
This argument will change the default of 5 for the number of characters in the new password that must not be present in the old password. In addition, if 1/2 of the characters in the new password are different then the new password will be accepted anyway.
difignore=N
How many characters should the password have before difok will be ignored. The default is 23.
minlen=N
The minimum acceptable size for the new password (plus one if credits are not disabled which is the default). In addition to the number of characters in the new password, credit (of +1 in length) is given for each different kind of character (other, upper, lower and digit). The default for this parameter is 9 which is good for a old style UNIX password all of the same type of character but may be too low to exploit the added security of a md5 system. Note that there is a pair of length limits in Cracklib itself, a "way too short" limit of 4 which is hard coded in and a defined limit (6) that will be checked without reference to minlen. If you want to allow passwords as short as 5 characters you should not use this module.
dcredit=N
(N >= 0) This is the maximum credit for having digits in the new password. If you have less than or N digits, each digit will count +1 towards meeting the current minlen value. The default for dcredit is 1 which is the recommended value for minlen less than 10.
(N < 0) This is the minimum number of digits that must be met for a new password.
ucredit=N
(N >= 0) This is the maximum credit for having upper case letters in the new password. If you have less than or N upper case letters each letter will count +1 towards meeting the current minlen value. The default for ucredit is 1 which is the recommended value for minlen less than 10.
(N > 0) This is the minimum number of upper case letters that must be met for a new password.
lcredit=N
(N >= 0) This is the maximum credit for having lower case letters in the new password. If you have less than or N lower case letters, each letter will count +1 towards meeting the current minlen value. The default for lcredit is 1 which is the recommended value for minlen less than 10.
(N < 0) This is the minimum number of lower case letters that must be met for a new password.
ocredit=N
(N >= 0) This is the maximum credit for having other characters in the new password. If you have less than or N other characters, each character will count +1 towards meeting the current minlen value. The default for ocredit is 1 which is the recommended value for minlen less than 10.
(N < 0) This is the minimum number of other characters that must be met for a new password.
use_authtok
This argument is used to force the module to not prompt the user for a new password but use the one provided by the previously stacked password module.
dictpath=/path/to/dict
Path to the cracklib dictionaries.
dictpath=/path/to/dict //注:密码字典,这个是验证用户的密码是否是字典一部分的关键。
Path to the cracklib dictionaries.
cracklib密码强度检测过程
首先检查密码是否是字典的一部分,如果不是,则进行下面的检查
密码强度检测过程
These checks are:
Palindrome
Is the new password a palindrome of the old one?
新密码是否旧密码的回文
Case Change Only
Is the new password the the old one with only a change of case?
新密码是否只是就密码改变了大小写
Similar
Is the new password too much like the old one?
新密码是否和旧密码很相似
This is primarily controlled by one argument, difok which is a number of characters that if different between the old and new are enough to accept the new password, this defaults to 10 or 1/2 the size of the new password whichever is smaller.
To avoid the lockup associated with trying to change a long and complicated password, difignore is available. This argument can be used to specify the minimum length a new password needs to be before the difok value is ignored. The default value for difignore is 23.
Simple
Is the new password too small?
新密码是否太短
This is controlled by 5 arguments minlen, dcredit, ucredit, lcredit, and ocredit. See the section on the arguments for the details of how these work and there defaults.
Rotated
Is the new password a rotated version of the old password?
新密码的字符是否是旧密码字符的一个循环
例如旧密码:123
新密码:231
Already used
Was the password used in the past?
这个密码以前是否使用过
Previously used passwords are to be found in /etc/security/opasswd.
那么系统是如何实现这个控制的呢?
在系统的配置文件/etc/pam.d/system-auth 中有这样一行
password requisite pam_cracklib.so try_first_pass retry=3
我们可以根据pam_cracklib的参数这样配置这个pam模块来达到我们想要的目的
password required /lib/security/pam_cracklib.so retry=3 type= minlen=8 difok=3 dictpath=/path/to/dict本回答被提问者和网友采纳
如何在 Ruby on Rails 中使用 Devise 验证密码强度?
【中文标题】如何在 Ruby on Rails 中使用 Devise 验证密码强度?【英文标题】:How to validate password strength with Devise in Ruby on Rails? 【发布时间】:2013-01-04 00:51:53 【问题描述】:我想强制用户在注册时选择强密码。
我知道,那里有很多 jquery 密码强度计,我很可能也会使用其中之一。但这并不能真正强制任何人选择强密码。注册表单也必须在不启用 js 的情况下可用,因此仍然可能使用弱密码进行注册。
帐户必须是最安全的,因为如果您已登录,您可以看到其他帐户的数据,我不想在任何情况下暴露这些数据。所以我想在这里寻求最大的安全性,因此我认为,只允许使用强密码是最重要的。
所以,
如何设置和自定义验证最低密码强度的要求?我只能在设计配置文件中找到密码长度。我应该使用其他 gem 来完成这项任务吗?
【问题讨论】:
【参考方案1】:在撰写本文时(2018 年),我建议其他人在使用之前推荐的 Devise Security extension gem 之前考虑较新的 Devise Security 分支(截至 2016 年 3 月 v0.10.0 已过时,但 仍然 OG AF mang!)
编辑:This one 看起来更新,但 idk。
【讨论】:
【参考方案2】:我最近发布了一个设计 gem,它使用 zxcvbn 库来拒绝弱密码:
https://github.com/bitzesty/devise_zxcvbn
【讨论】:
请注意,这最终会使用 ExecJS - 这是一个令人惊讶的依赖关系。 @jamesmoore 这是必需的,因为 zxcvbn 算法的纯 Ruby 版本没有返回与 JS 版本相同的结果,我们切换以便我们可以在前端和后端获得相同的结果. 有趣 - 这里绝对是一个设计权衡。我宁愿没有 js 依赖并获得稍微不同的结果(并且只在服务器上完成所有操作,因此客户端结果将无关紧要),但有些人需要相反的结果是有道理的。【参考方案3】:您可以使用Devise Security extension,您可以在其中定义密码正则表达式验证(除其他外)并强制执行您想要的密码强度。
【讨论】:
听起来不错。我会试一试。不过,我之前没见过regex syntax used in the config file。(?=...) 我明白它的作用,但我希望能稍微解释一下,? 的含义。
恕我直言,这些测试太天真了;它只需要一个数字和大写字母。一个没有数字的很长的密码仍然是安全的,但是Passw0rd(例如)是一个糟糕的密码(但仍然满足这些要求)
@Carpetsmoker 是对的;尝试通过匹配正则表达式来提高密码强度是一个糟糕的主意。以上是关于linux如何设置一般用户密码必须达到一定强度?还有3月强制更改一次密码?的主要内容,如果未能解决你的问题,请参考以下文章