GRE over IPSEC
Posted 害怕网络暴力
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了GRE over IPSEC相关的知识,希望对你有一定的参考价值。
华三配置(gre over ipsec) vpn 主模式
拓扑
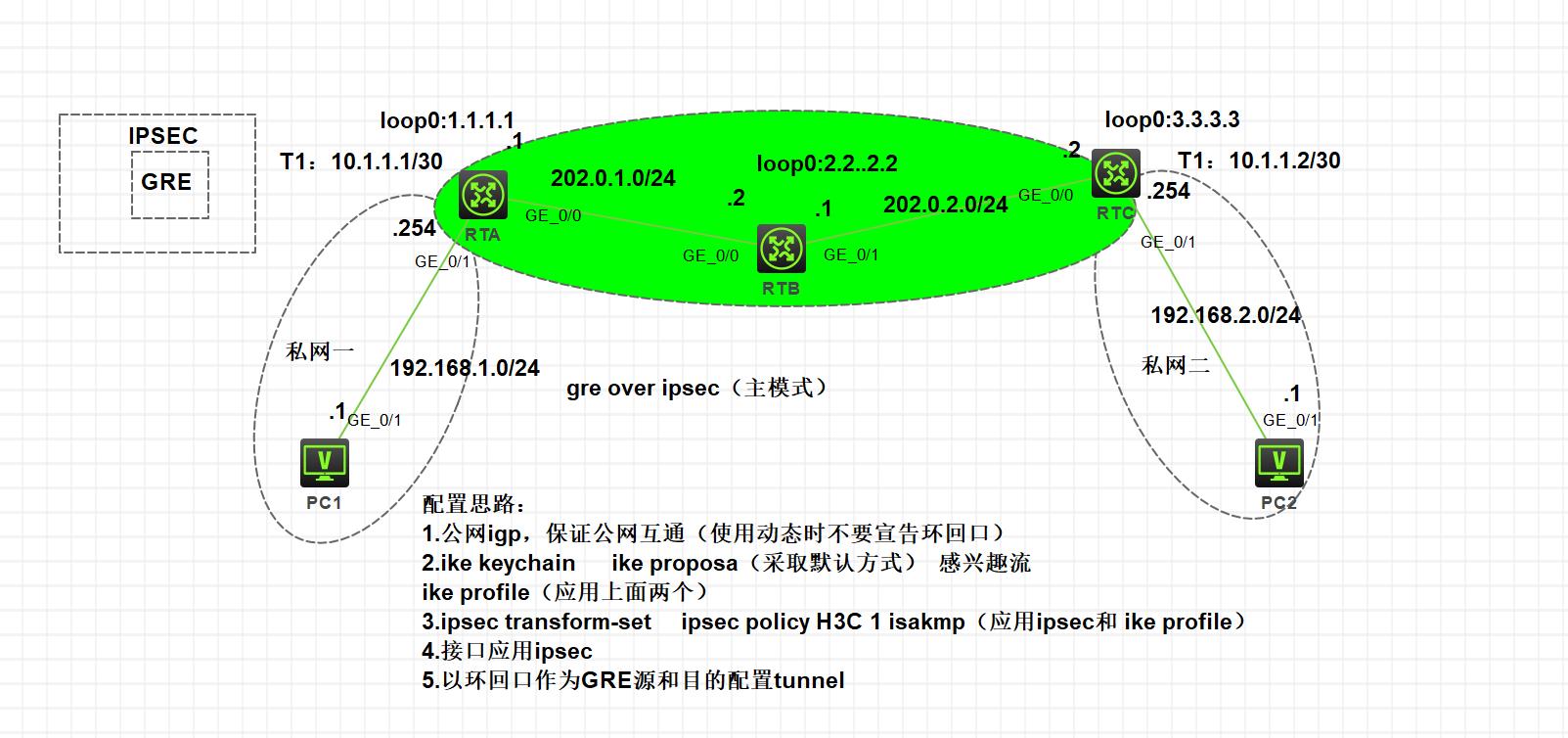
注意点:
GRE over IPSEC:ipsec中acl匹配的是tunnle流,源和目的是隧道的源和目的
IPSEC over GRE:acl匹配的就是业务流
GRE over IPSEC:ike对等体中remote-address地址是对方公网口的物理地址
IPSEC over GRE:ike对等体中remote-address地址是对方tunnel接口地址
GRE over IPSEC:ipsec policy应用在本地物理接口上
IPSEC over GRE:ipsec policy应用在本地tunnel接口上
一、配地址


RTA
<H3C>sys
System View: return to User View with Ctrl+Z.
[H3C]
[H3C]in
[H3C]interface g0/1
[H3C-GigabitEthernet0/1]ip address 192.168.1.254 24
[H3C-GigabitEthernet0/1]in g0/0
[H3C-GigabitEthernet0/0]ip address 202.0.1.1 24
[H3C-GigabitEthernet0/0]qu
[H3C]interface LoopBack 0
[H3C-LoopBack0]ip address 1.1.1.1 32
RTB
<H3C>sys
System View: return to User View with Ctrl+Z.
[H3C]sysname RTB
[RTB]in g0/0
[RTB-GigabitEthernet0/0]ip address 202.0.1.2 24
[RTB-GigabitEthernet0/0]in g0/1
[RTB-GigabitEthernet0/1]ip address 202.0.2.1 24
[RTB-GigabitEthernet0/1]qu
[RTB]interface LoopBack 0
[RTB-LoopBack0]ip address 2.2.2.2 32
RTC
<H3C>sys
System View: return to User View with Ctrl+Z.
[H3C]in g0/0
[H3C-GigabitEthernet0/0]ip address 202.0.2.2 24
[H3C-GigabitEthernet0/0]in g0/1
[H3C-GigabitEthernet0/1]ip address 192.168.2.254 24
[H3C-GigabitEthernet0/1]qu
[H3C]interface LoopBack 0
[H3C-LoopBack0]ip address 3.3.3.3 24
[H3C-LoopBack0]qu
[H3C]sysname RTC
二、公网IGP
[RTA]ospf 1
[RTA-ospf-1]area 0
[RTA-ospf-1-area-0.0.0.0]network 202.0.1.1 0.0.0.0
[RTB]ospf 1
[RTB-ospf-1]area 0
[RTB-ospf-1-area-0.0.0.0]network 202.0.1.2 0.0.0.0
[RTB-ospf-1-area-0.0.0.0]network 202.0.2.1 0.0.0.0
[RTC]ospf 1
[RTC-ospf-1]area 0
[RTC-ospf-1-area-0.0.0.0]network 202.0.2.2 0.0.0.0
三、配置ike
[RTA]ike keychain k1 #密钥名称随便起
[RTA-ike-keychain-k1]pre-shared-key address 202.0.2.2 key simple 123456
#这里地址要是对面的公网地址,密码两端密钥必须一致
[RTA]ike proposal 1 #创建ike 安全提议,然后直接退出,采用默认配置
[RTA]ike profile p1 #创建ike模板,调用上面的ike密钥,ike安全提议
[RTA-ike-profile-p1]keychain k1
[RTA-ike-profile-p1]proposal 1
[RTA-ike-profile-p1]local-identity address 202.0.1.1 #设置对端地址
[RTA-ike-profile-p1]match remote identity address 202.0.2.2 255.255.255.255
#设置本端地址
[RTC]ike keychain k1
[RTC-ike-keychain-k1]pre-shared-key address 202.0.1.1 key simple 123456
[RTC-ike-keychain-k1]qu
[RTC]ike proposal 1
[RTC-ike-proposal-1]qu
[RTC]ike profile p1
[RTC-ike-profile-p1]keychain k1
[RTC-ike-profile-p1]proposal 1
[RTC-ike-profile-p1]local-identity address 202.0.2.2
[RTC-ike-profile-p1]match remote identity address 202.0.1.1 255.255.255.255
四、配置ipsec
[RTA]ipsec transform-set t1 #创建ipsec安全提议
[RTA-ipsec-transform-set-t1]encapsulation-mode tunnel #封装模式为隧道
[RTA-ipsec-transform-set-t1]esp authentication-algorithm sha1
#esp协议的验证方式为sha1
[RTA-ipsec-transform-set-t1]esp encryption-algorithm des-cbc
#esp的加密方式为des-cbc
[RTA]ipsec policy h3c 1 isakmp #创建ipsec策略还h3c,进程号为1
[RTA-ipsec-policy-isakmp-h3c-1]ike-profile p1 #调用ike模板
[RTA-ipsec-policy-isakmp-h3c-1]transform-set t1 #调用ipsec安全提议
[RTA-ipsec-policy-isakmp-h3c-1]security acl 3000 #调用acl3000
[RTA-ipsec-policy-isakmp-h3c-1]local-address 202.0.1.1
[RTA-ipsec-policy-isakmp-h3c-1]remote-address 202.0.2.2
[RTC]ipsec transform-set t1
[RTC-ipsec-transform-set-t1]encapsulation-mode tunnel
[RTC-ipsec-transform-set-t1]esp authentication-algorithm sha1
[RTC-ipsec-transform-set-t1]esp encryption-algorithm des-cbc
[RTC-ipsec-transform-set-t1]qu
[RTC]ipsec policy h3c 1 isakmp
[RTC-ipsec-policy-isakmp-h3c-1]ike-profile p1
[RTC-ipsec-policy-isakmp-h3c-1]transform-set t1
[RTC-ipsec-policy-isakmp-h3c-1]security acl 3000
[RTC-ipsec-policy-isakmp-h3c-1] local-address 202.0.2.2
[RTC-ipsec-policy-isakmp-h3c-1]remote-address 202.0.1.1
**配置感兴趣流**
[RTA]acl advanced 3000
[RTA-acl-ipv4-adv-3000]rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
[RTC]acl advanced 3000
[RTC-acl-ipv4-adv-3000]rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
**在接口应用**
[RTA]interface g0/0
[RTA-GigabitEthernet0/0]ipsec apply policy h3c
[RTC]in g0/0
[RTC-GigabitEthernet0/0]ipsec apply policy h3c
引流
[RTA]ip route-static 0.0.0.0 0 202.0.1.2 #这个一定要配置,不然出口设备收到数据包不知道向哪里转发,必须从出接口转发,才能触发ipsec
[RTC]ip route-static 0.0.0.0 0 202.0.2.1
测试两端环回口

五、配置GRE
[RTA]interface Tunnel 1 mode gre #创建GRE隧道
[RTA-Tunnel1]ip address 10.1.1.1 30 #配置IP
[RTA-Tunnel1]source 1.1.1.1 #这里的源和目的是ipsec的感兴趣流,
[RTA-Tunnel1]destination 3.3.3.3
[RTC]interface Tunnel 1 mode gre
[RTC-Tunnel1]ip address 10.1.1.2 30
[RTC-Tunnel1]source 3.3.3.3
[RTC-Tunnel1]destination 1.1.1.1
引流
[RTA]ip route-static 192.168.2.0 24 Tunnel 1 #告诉设备,去往2.0网段把数据丢给GRE隧道
[RTC]ip route-static 192.168.1.0 24 Tunnel 1
测试

以上是关于GRE over IPSEC的主要内容,如果未能解决你的问题,请参考以下文章