k8s 安装 kubernetes-dashboard-2.X
Posted 笨小孩@GF 知行合一
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了k8s 安装 kubernetes-dashboard-2.X相关的知识,希望对你有一定的参考价值。
- 安装使用 k8s 原生的 web 图形化界面来对资源进行查看与管理
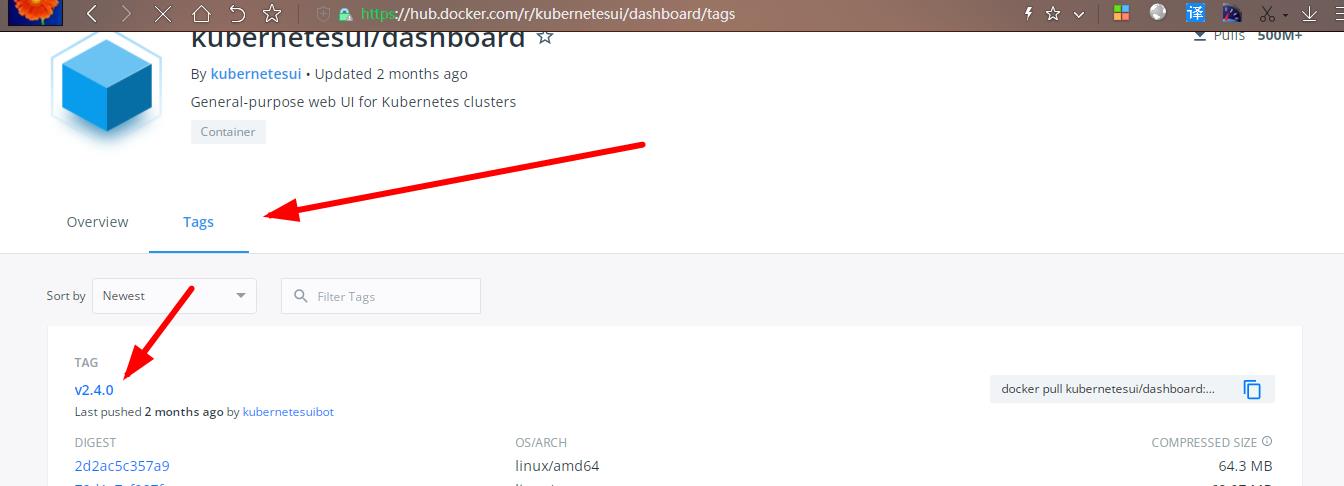
- 在官网查看镜像版本
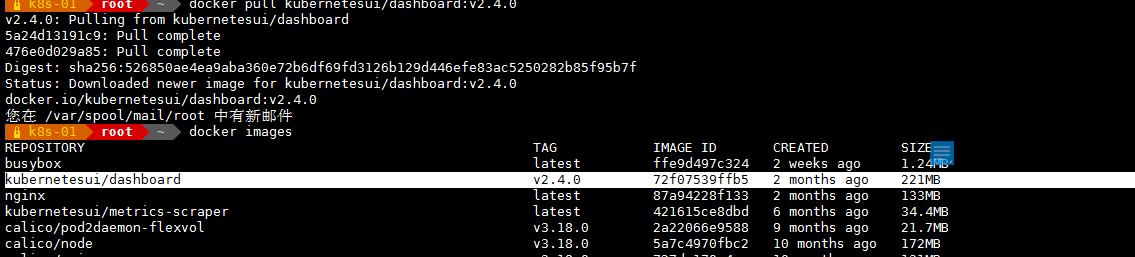
Docker Hub- 所有工作节点拉取镜像
docker pull kubernetesui/dashboard:v2.4.0
docker pull kubernetesui/metrics-scraper:latest
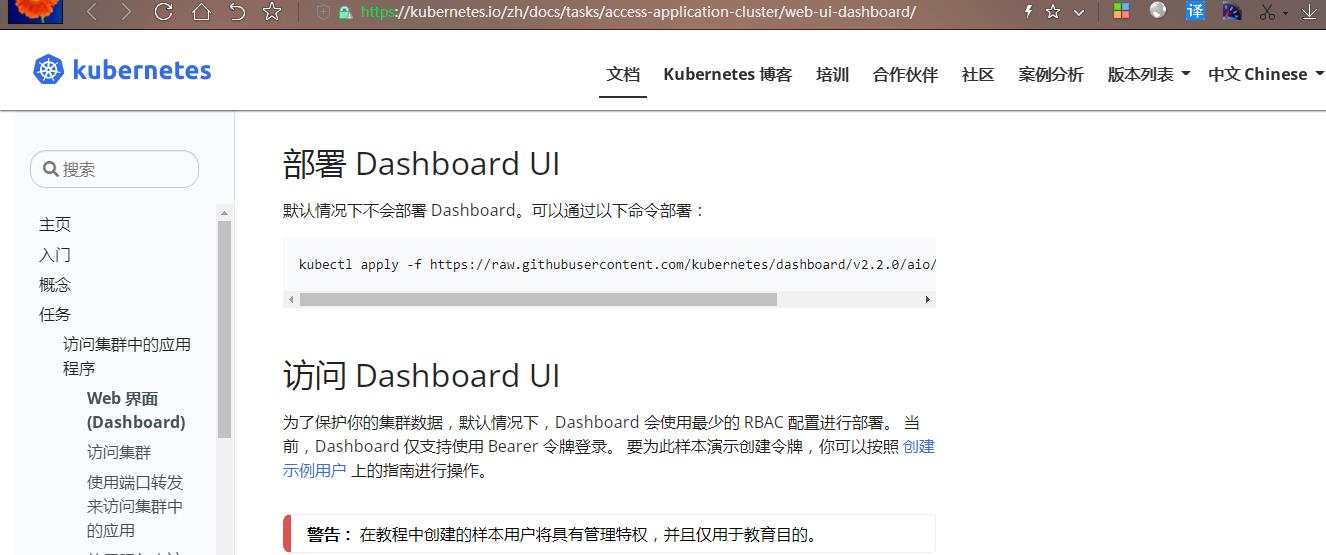
- 获取官方yaml
Web 界面 (Dashboard) | Kubernetes- 编辑 yaml
mv recommended.yaml kubernetes-dashboard.yaml
vim kubernetes-dashboard.yaml# Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: kubernetes-dashboard --- apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard type: NodePort --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboard type: Opaque data: csrf: "" --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboard type: Opaque --- kind: ConfigMap apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard rules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard rules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.4.0 imagePullPolicy: IfNotPresent ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper annotations: seccomp.security.alpha.kubernetes.io/pod: 'runtime/default' spec: containers: - name: dashboard-metrics-scraper image: kubernetesui/metrics-scraper:latest imagePullPolicy: IfNotPresent ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir:
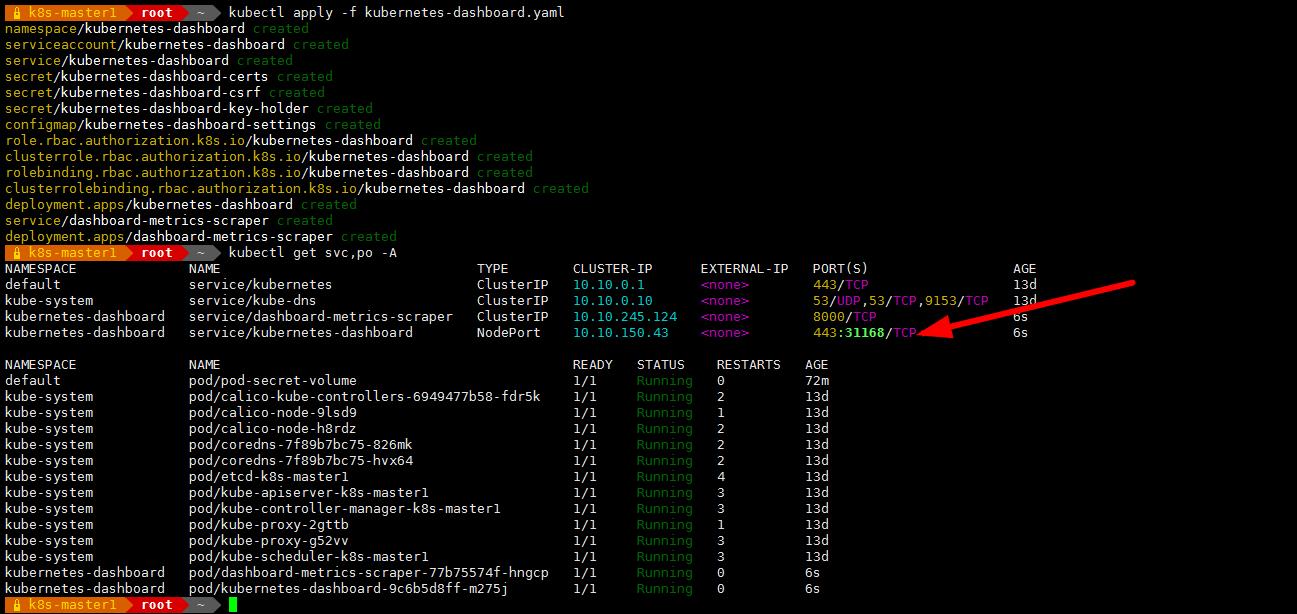
- kubectl apply -f kubernetes-dashboard.yaml
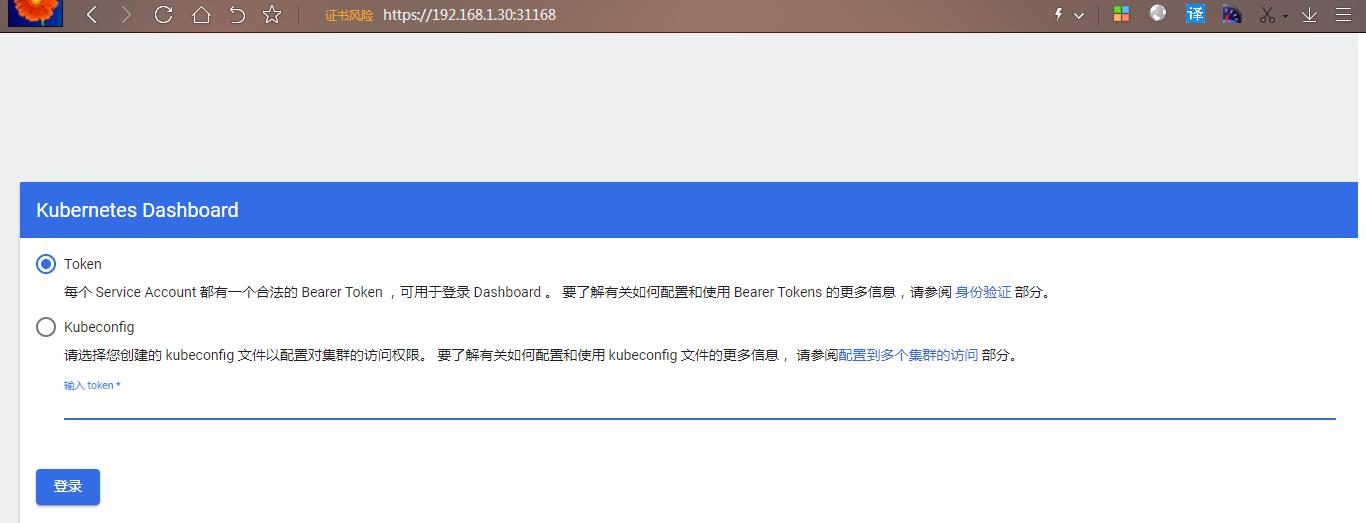
打开浏览器访问:https://192.168.1.30:31168/
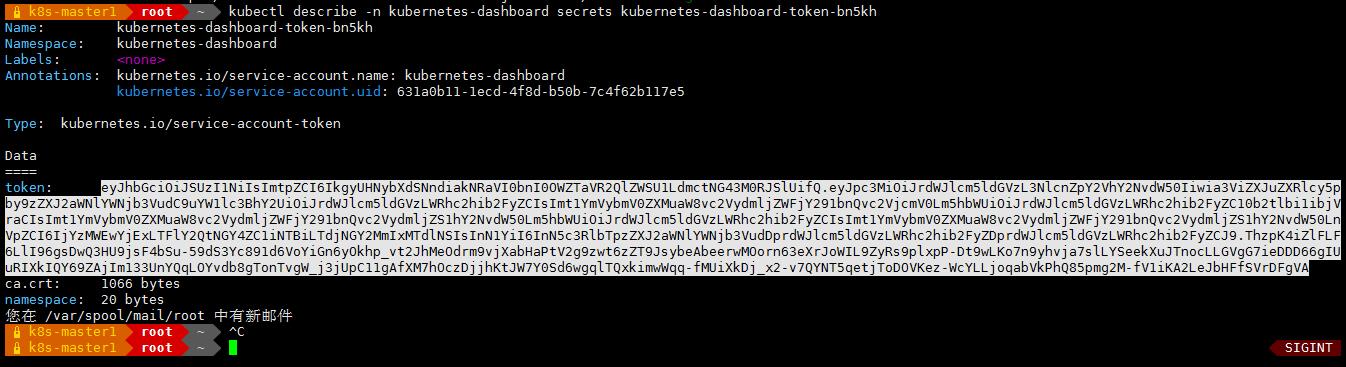
- 通过管理员 Token 登陆 dashboard
kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:kubernetes-dashboard
获取 token复制到 输入 token 处: 点登陆
- 通过普通权限 token 令牌登录 dashboard
- 1.创建一个只能管理指定名称空间的 token
以下步骤在 k8s 的控制节点操作
(1)在 lucky 命名空间创建一个 lucky 的 serviceaccount 账户
kubectl create namespace lucky
kubectl create serviceaccount lucky-admin -n lucky
(2)把 lucky 用户做 rolebingding 绑定
kubectl create rolebinding lucky-admin -n lucky --clusterrole=cluster-admin --serviceaccount=lucky:lucky-admin
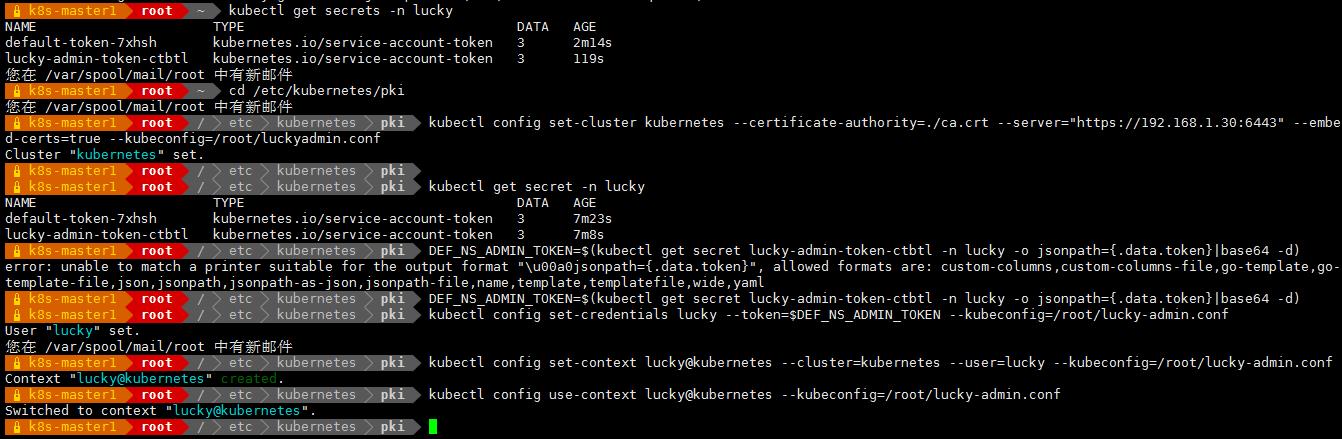
(3)查看 secret
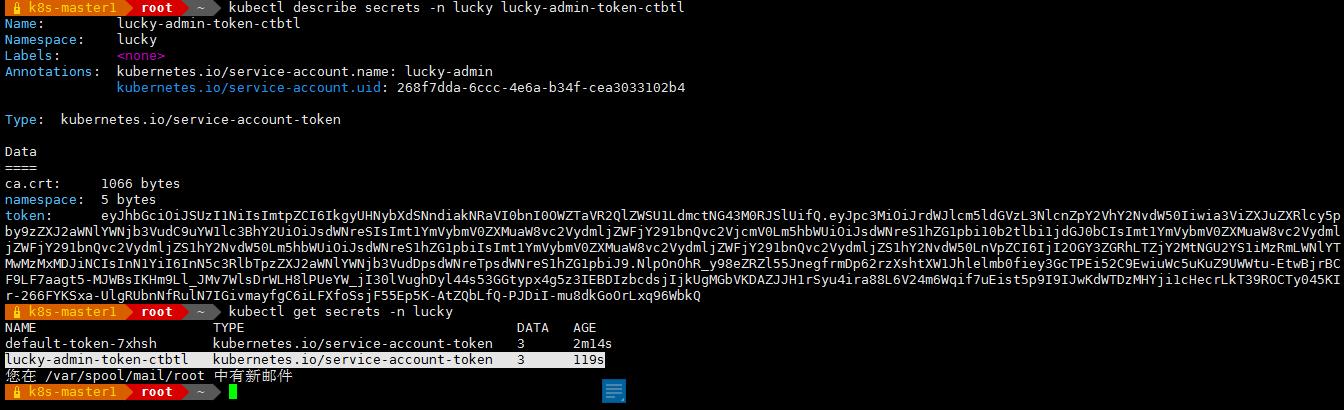
kubectl get secrets -n lucky 显示如下:
kubectl describe secrets -n lucky lucky-admin-token-ctbtl 显示如下:
上面的 token 输入到 web 界面的令牌认证处,登陆之后只能看到 lucky 的命名空间
- 通过 kubeconfig 登录 dashboard
- 把 token 令牌封装成 kubeconfig,通过 kubeconfig 登陆 dashboard
- 1.创建一个只能管理指定名称空间的 kubeconfig 文件
以下步骤在 k8s 的 master 节点操作
cd /etc/kubernetes/pki
(1)创建 cluster
kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://192.168.1.30:6443" --embed-certs=true --kubeconfig=/root/luckyadmin.conf
(2)创建 credentials 时需要使用上面我门创建的 token 信息
kubectl get secret -n lucky
DEF_NS_ADMIN_TOKEN=$(kubectl get secret lucky-admin-token-ctbtl -n lucky -o jsonpath=.data.token|base64 -d)
(3)开始创建 credentials
kubectl config set-credentials lucky --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/lucky-admin.conf
(4)创建 context
kubectl config set-context lucky@kubernetes --cluster=kubernetes --user=lucky --kubeconfig=/root/lucky-admin.conf
(5)切换 context 的 current-context 是 lucky@kubernetes
kubectl config use-context lucky@kubernetes --kubeconfig=/root/lucky-admin.conf
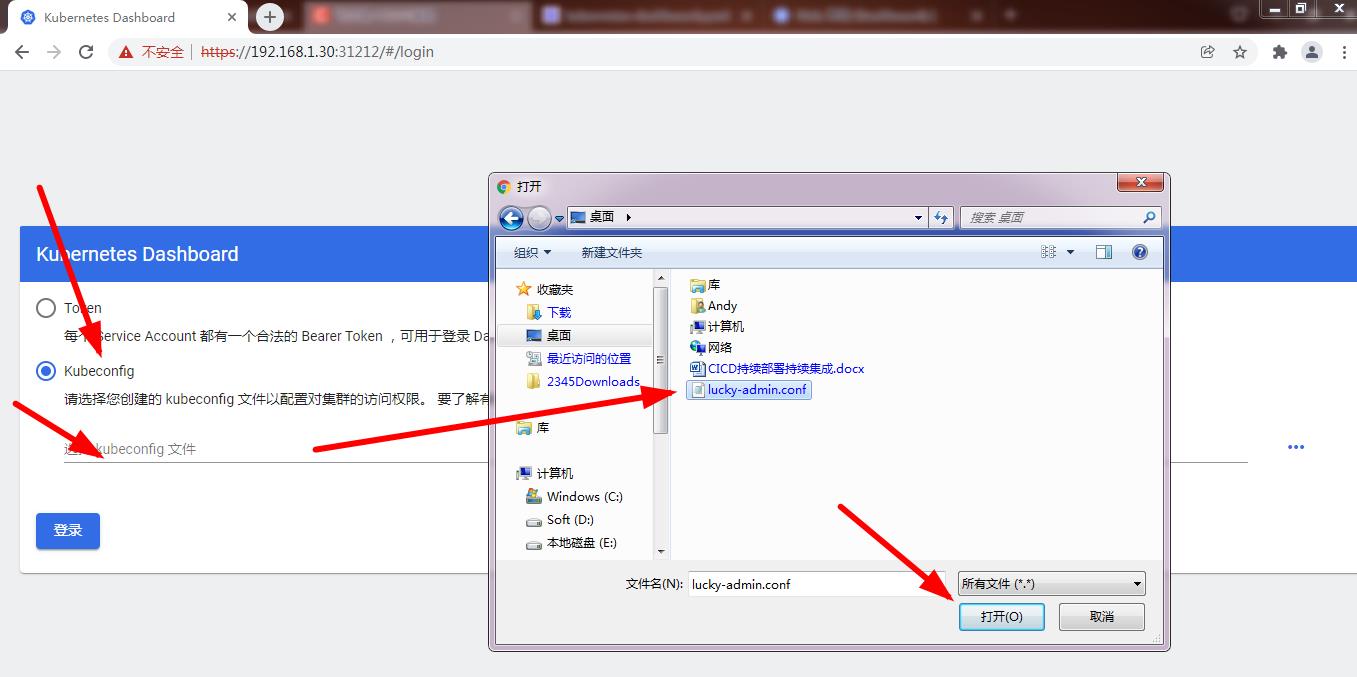
(6)把刚才的 kubeconfig 文件 lucky-admin.conf 复制到桌面
浏览器访问时使用 kubeconfig 认证,把刚才的 lucky-admin.conf 导入到 web 界面,那么就可以登陆了
- 限制用户操作 k8s 资源
- ssl 认证
生成一个证书
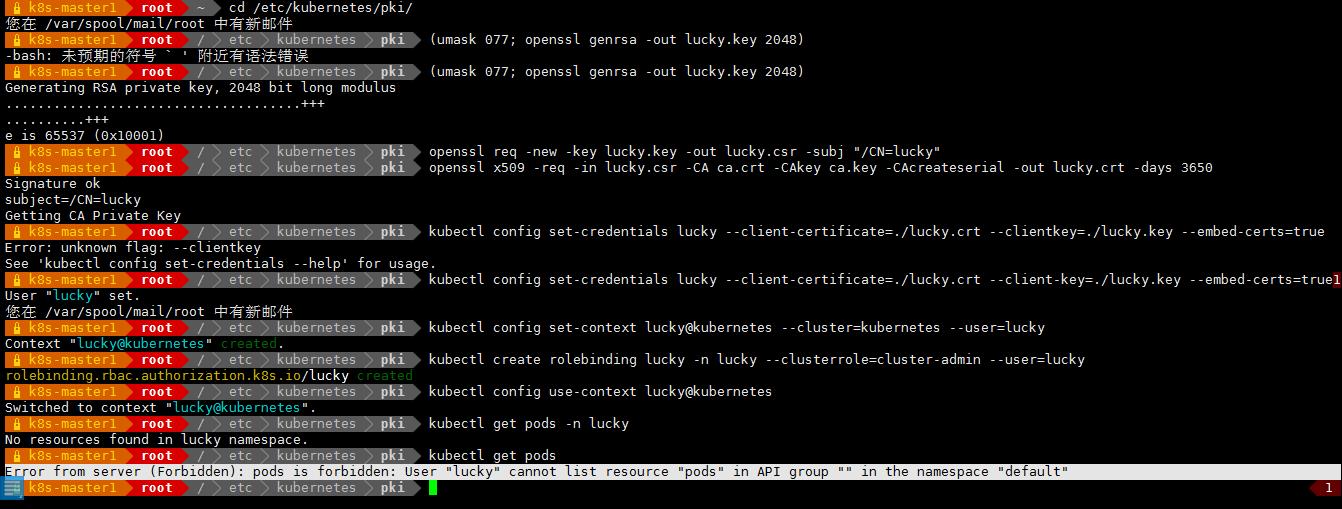
(1)生成一个私钥
cd /etc/kubernetes/pki/
(umask 077; openssl genrsa -out lucky.key 2048)
(2)生成一个证书请求
openssl req -new -key lucky.key -out lucky.csr -subj "/CN=lucky"
(3)生成一个证书
openssl x509 -req -in lucky.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out lucky.crt -days 3650
在 kubeconfig 下新增加一个 lucky 这个用户
(1)把 lucky 这个用户添加到 kubernetes 集群中,可以用来认证 apiserver 的连接
kubectl config set-credentials lucky --client-certificate=./lucky.crt --client-key=./lucky.key --embed-certs=true
(2)在 kubeconfig 下新增加一个 lucky 这个账号
kubectl config set-context lucky@kubernetes --cluster=kubernetes --user=lucky
(3)切换账号到 lucky,默认没有任何权限
kubectl config use-context lucky@kubernetes
kubectl config use-context kubernetes-admin@kubernetes 这个是集群用户,有任何权限
把 user 这个用户通过 rolebinding 绑定到 clusterrole 上,授予权限,权限只是在 lucky 这个名称
空间有效
(1)把 lucky 这个用户通过 rolebinding 绑定到 clusterrole 上
kubectl create rolebinding lucky -n lucky --clusterrole=cluster-admin --user=lucky
(2)切换到 lucky 这个用户
kubectl config use-context lucky@kubernetes
(3)测试是否有权限
kubectl get pods -n lucky
有权限操作这个名称空间
kubectl get pods
没有权限操作其他名称空间
添加一个 lucky 的普通用户
useradd lucky
cp -ar /root/.kube/ /home/lucky/
chown -R lucky.lucky /home/lucky/
su - lucky
kubectl get pods -n lucky
#可以操作 lucky 名称空间
exit
#切换到 kubernetes-admin@kubernetes
kubectl config use-context kubernetes-admin@kubernetes
以上是关于k8s 安装 kubernetes-dashboard-2.X的主要内容,如果未能解决你的问题,请参考以下文章