华为防火墙基础自学系列 | Hub Spoke IPsec VdPdNd
Posted COCOgsta
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了华为防火墙基础自学系列 | Hub Spoke IPsec VdPdNd相关的知识,希望对你有一定的参考价值。
视频来源:B站《乾颐堂HCIP-HCIE-security安全 2019年录制》
一边学习一边整理老师的课程内容及试验笔记,并与大家分享,侵权即删,谢谢支持!
附上汇总贴:华为防火墙基础自学系列 | 汇总_COCOgsta的博客-CSDN博客
Hub Spke IPSec VPN组网
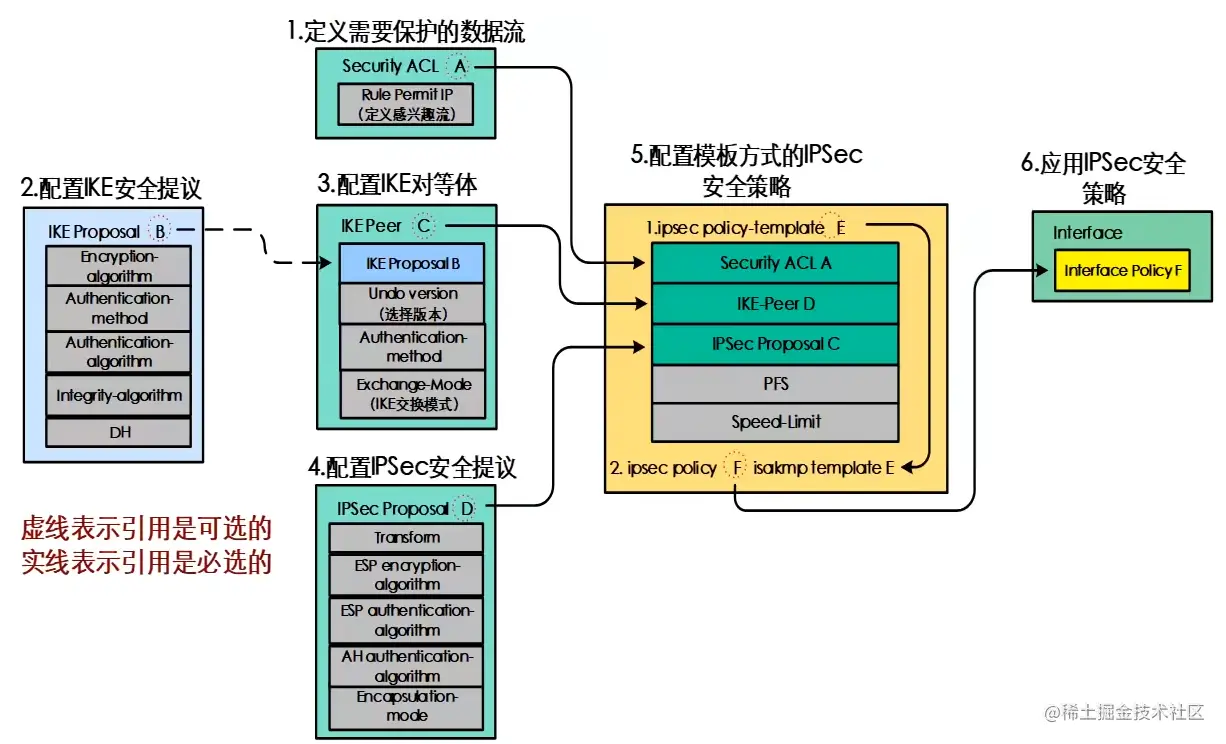
本组网尝试使用IKE安全策略模板来建立IPSec VPN,策略模板适用于中心站点固定地址,分支站点较多并且使用动态地址的工程环境。
删除S2SVPN环境
FW1和FW2删除IPsec策略。
FW1和FW2删除安全策略。
配置流程图
交换机底层桥接
Hub(FW1)网络配置
修改g0/0/2接口地址

修改默认网关

Spoke1(FW2)网络配置
修改g0/0/2接口地址

修改默认网关

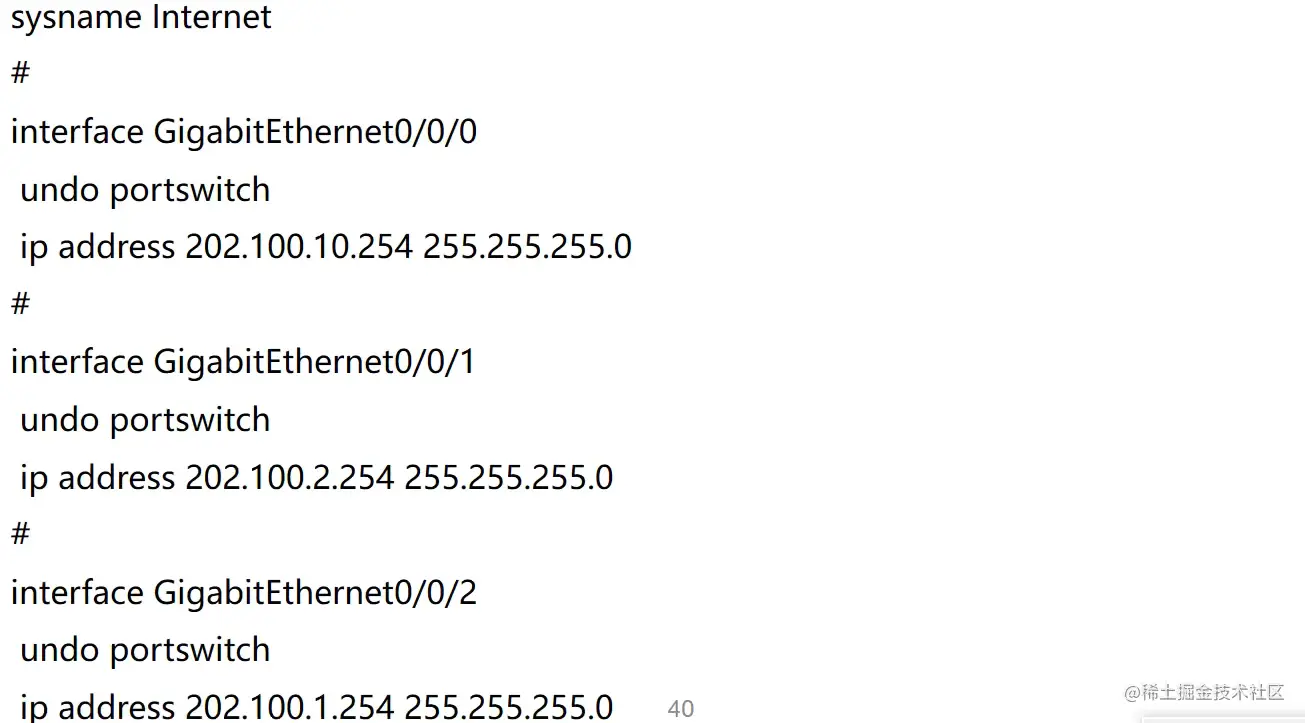
Internet(AR1)网络配置
配置Internet底层网络
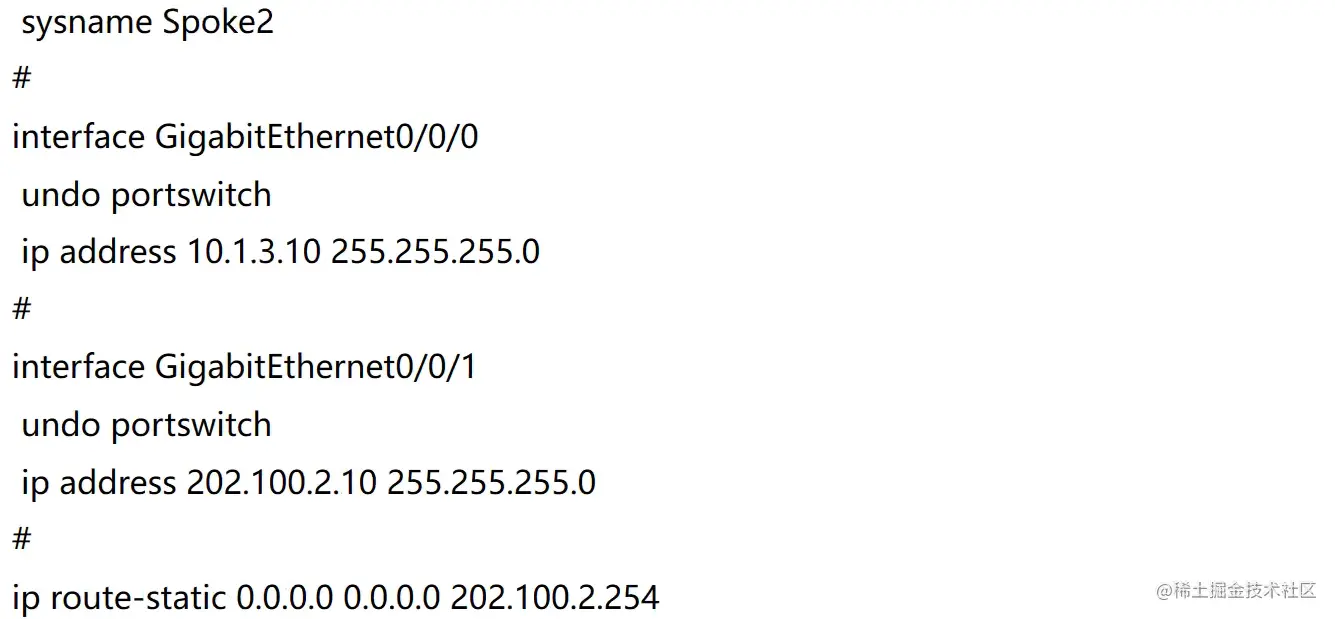
Spoke(AR2)网络配置
配置Spoke2底层网络
Hub配置IPsec(Web)
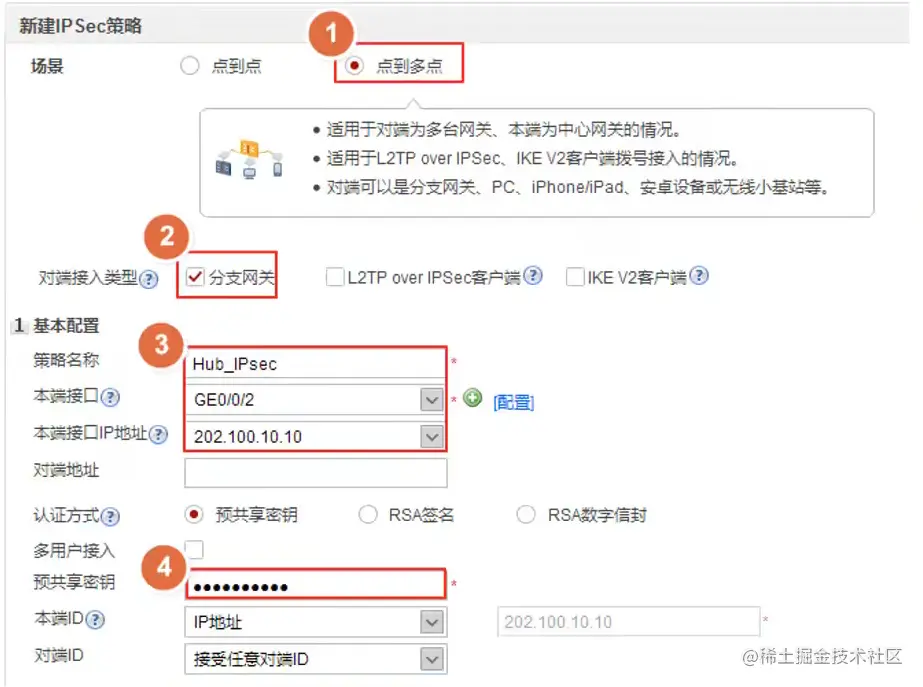
Hub新建IPsec策略
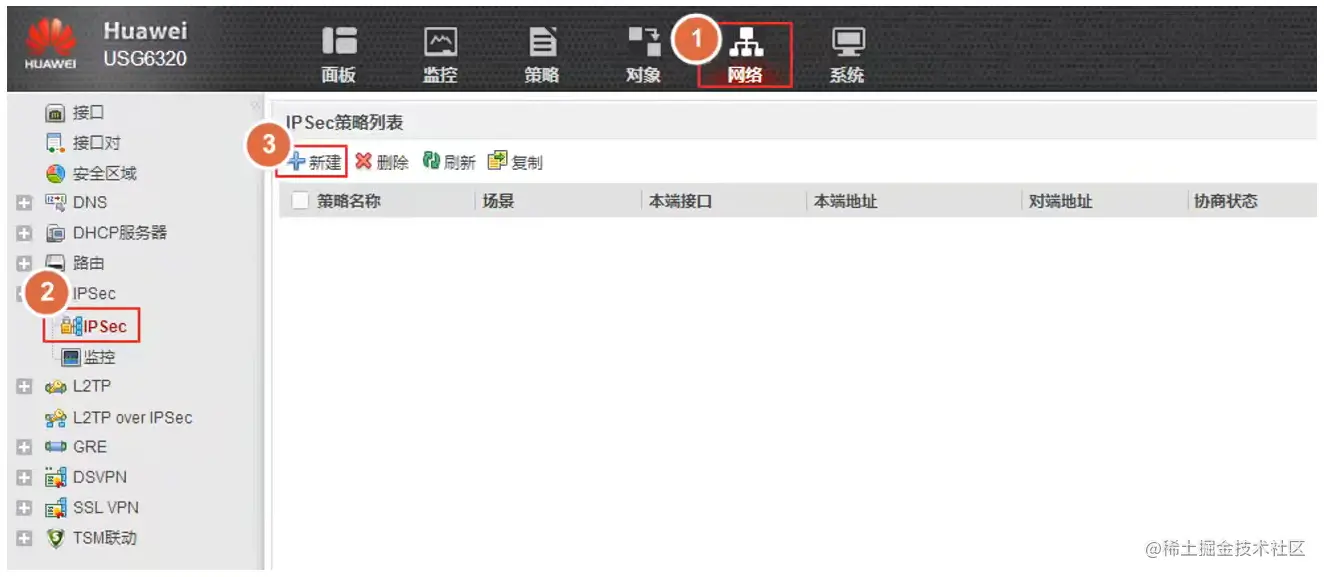
场景为【点到多点】,对端接入类型为【分支网关】,不填写对端IP地址。
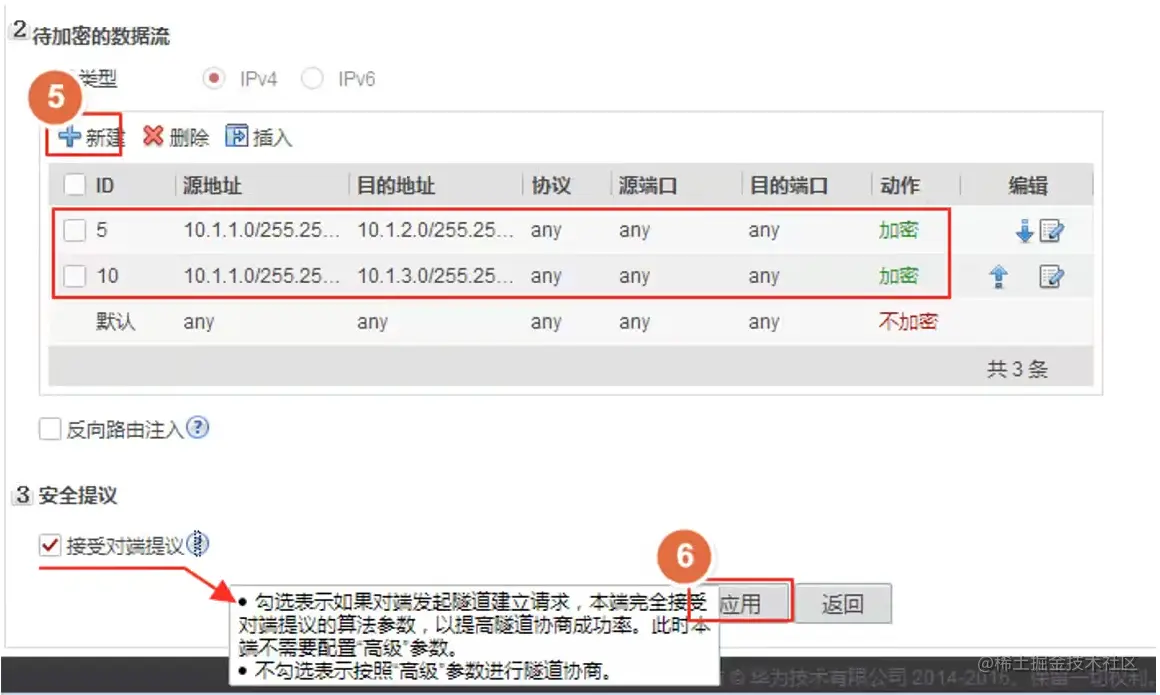
配置感兴趣流,接受对方的安全提议。
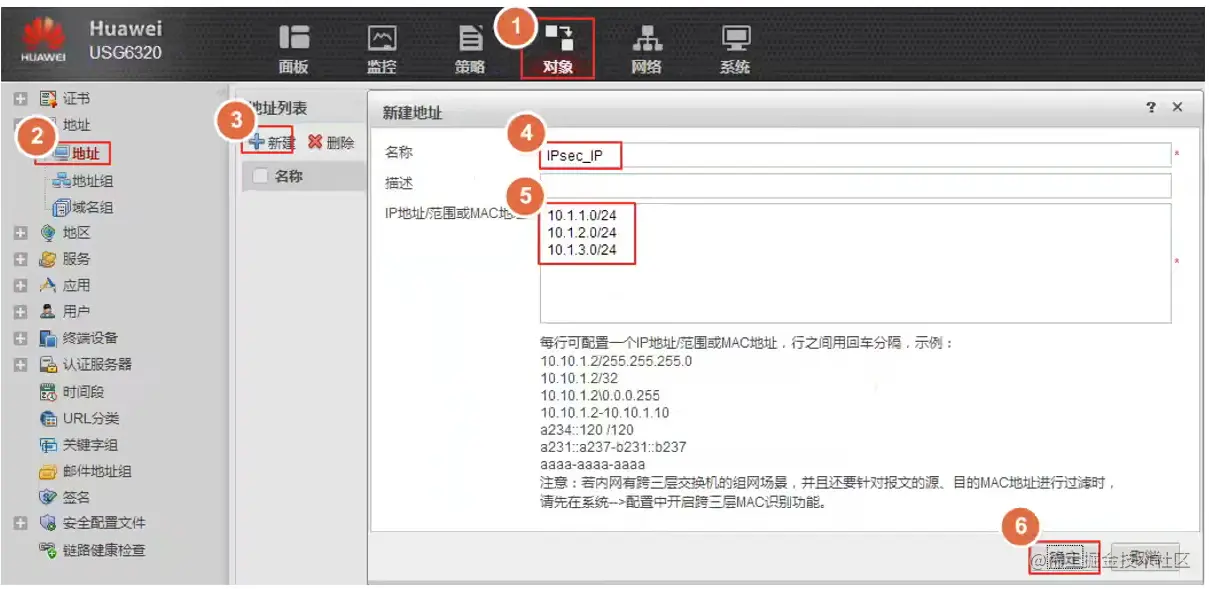
Hub配置安全策略(Web)
配置地址组,匹配感兴趣的IP地址。
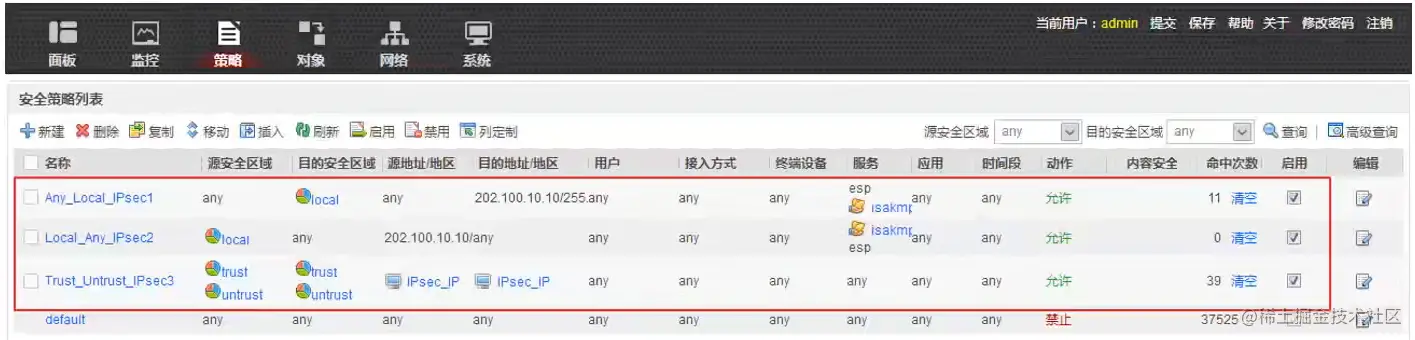
放行安全策略
Hub配置IPsec(CLI)
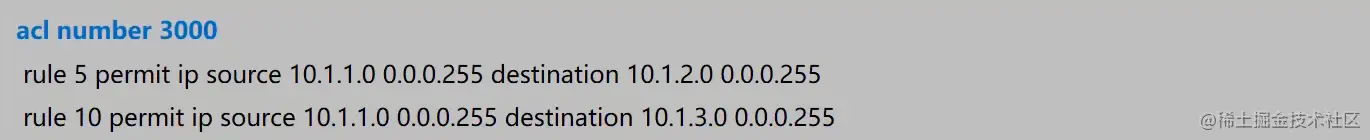
Hub配置ACL
Hub配置IKE Proposal

Hub配置IKE Peer

Hub配置IPsec proposal

Hub配置IPsec模板

Hub配置IPsec policy

Hub调用IPsec policy

Hub配置地址组

Hub配置安全策略(CLI)
Hub配置安全策略
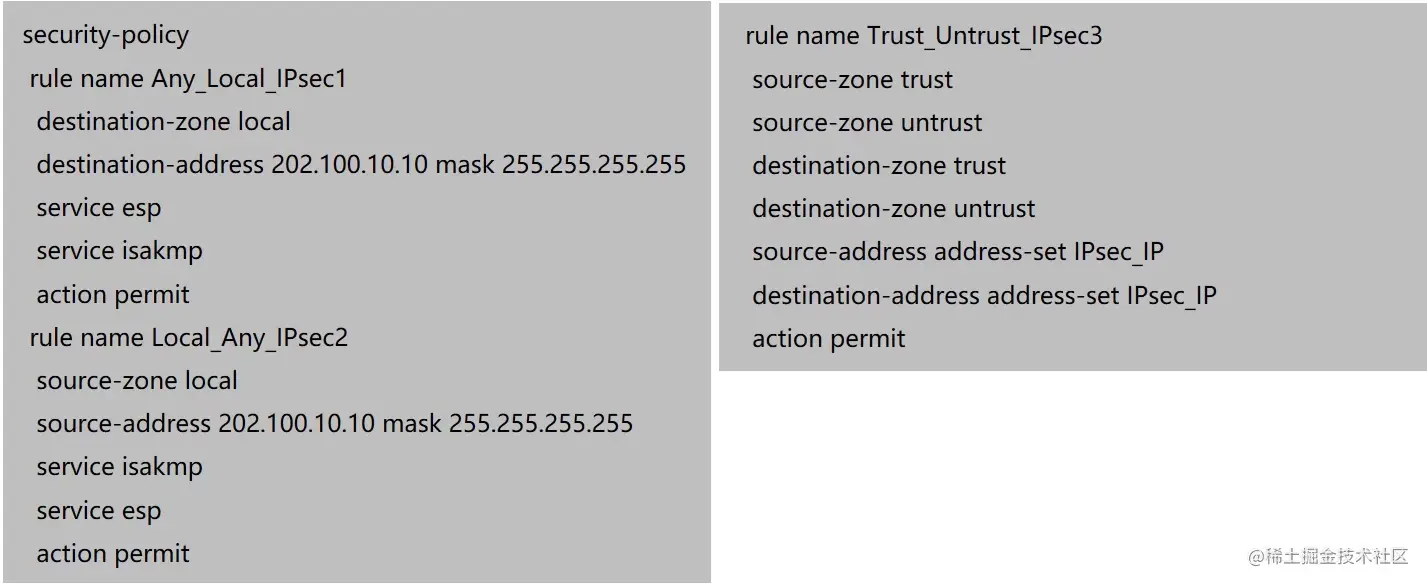
Spoke1配置IPsec(Web)
Spoke配置IPsec策略方式,和配置点到点场景没有区别。
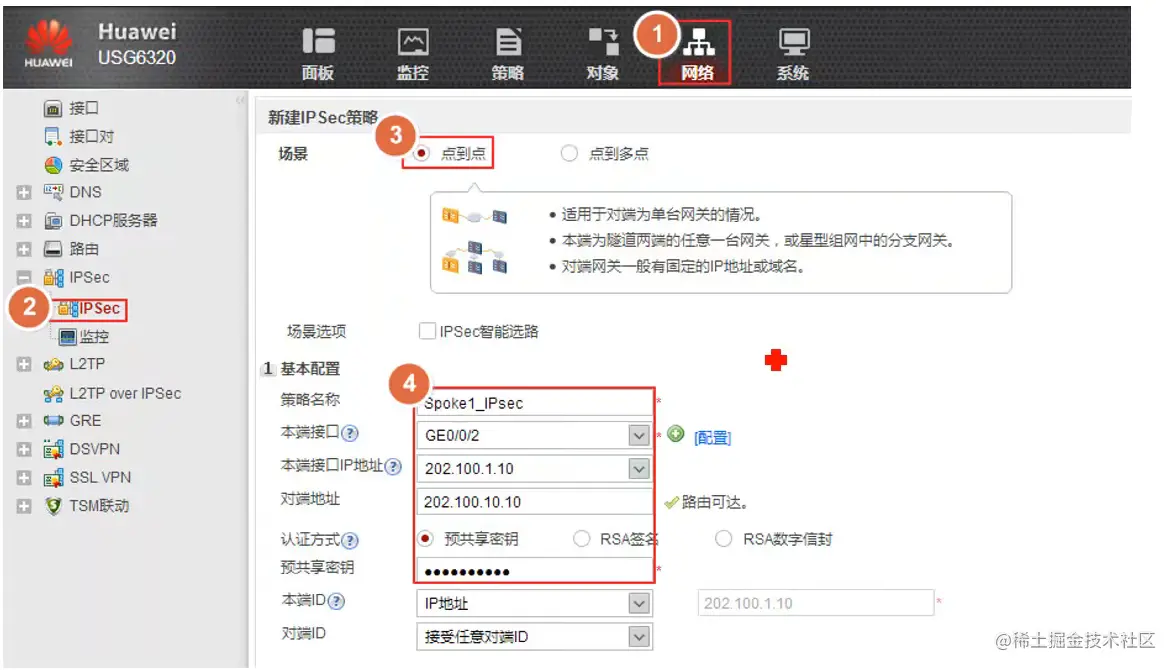
配置感兴趣流
Spoke1配置安全策略(Web)
放行安全策略
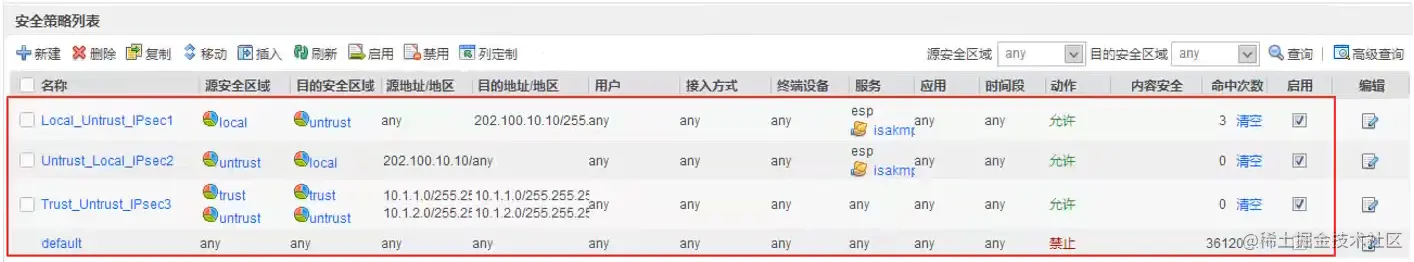
Spoke2配置IPsec
配置ACL

配置IKE proposal
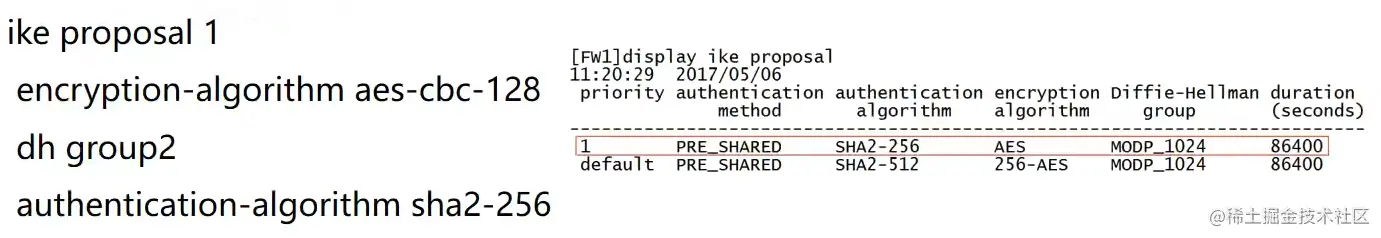
配置IKE peer

配置IPsec proposal

配置IPsec policy

接口下调用ipsec policy

Hub查看IPse状态
在Hub上查看IPsec的状态,和两个Spoke协商成功。
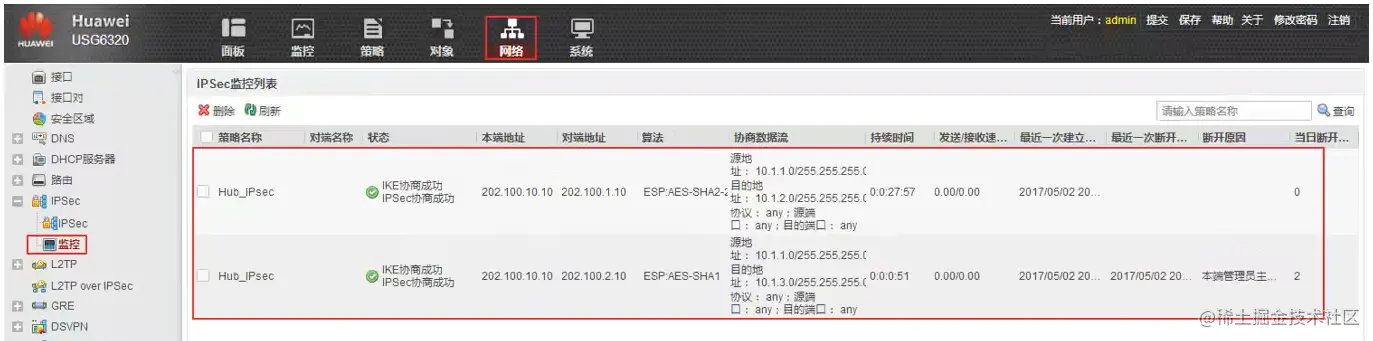
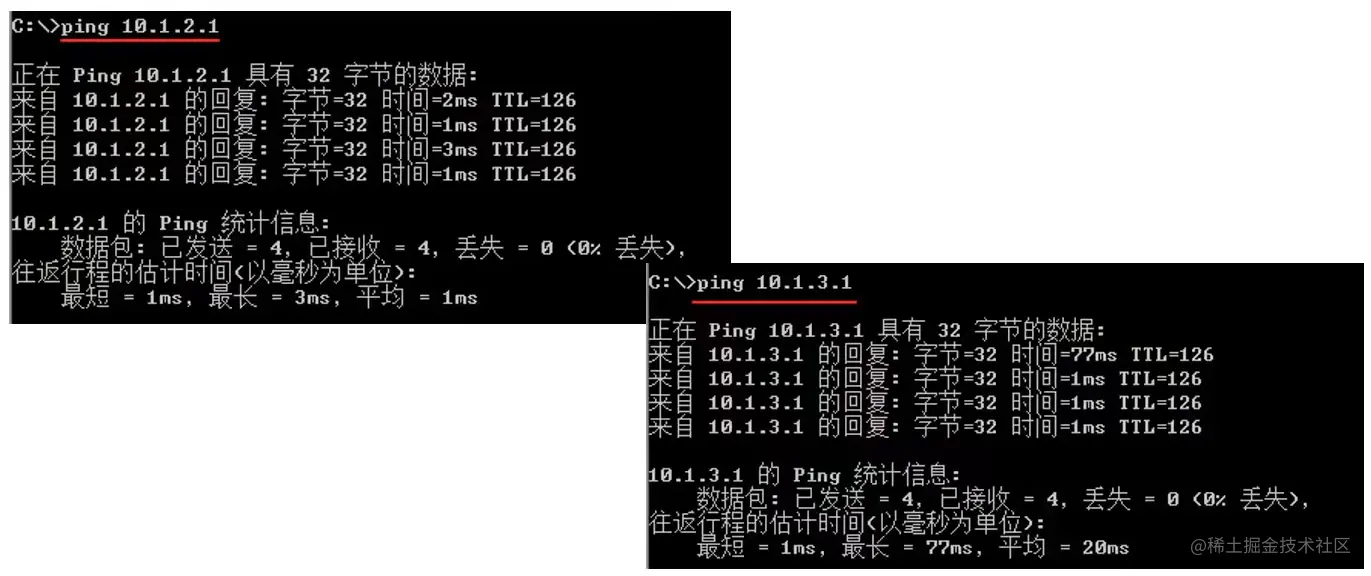
IPsec连通性测试
使用PC1测试到PC2和PC3的连通性。
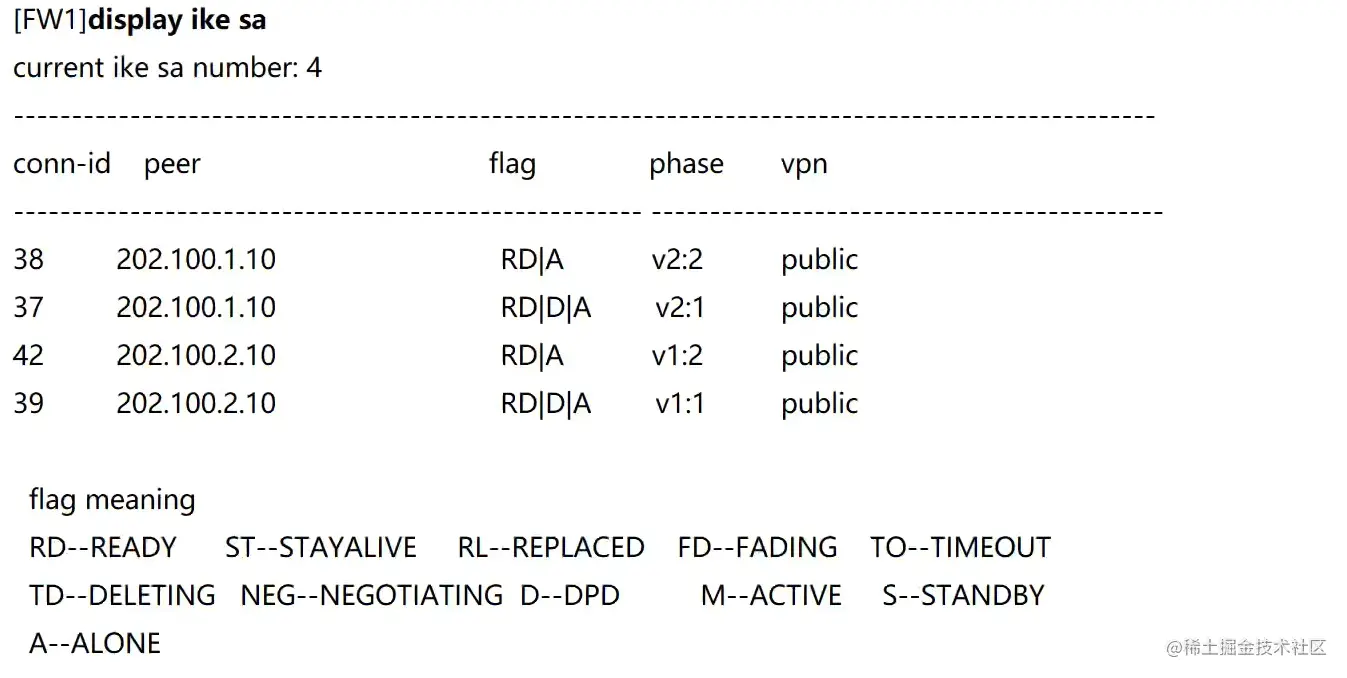
Hub查看IKE SA
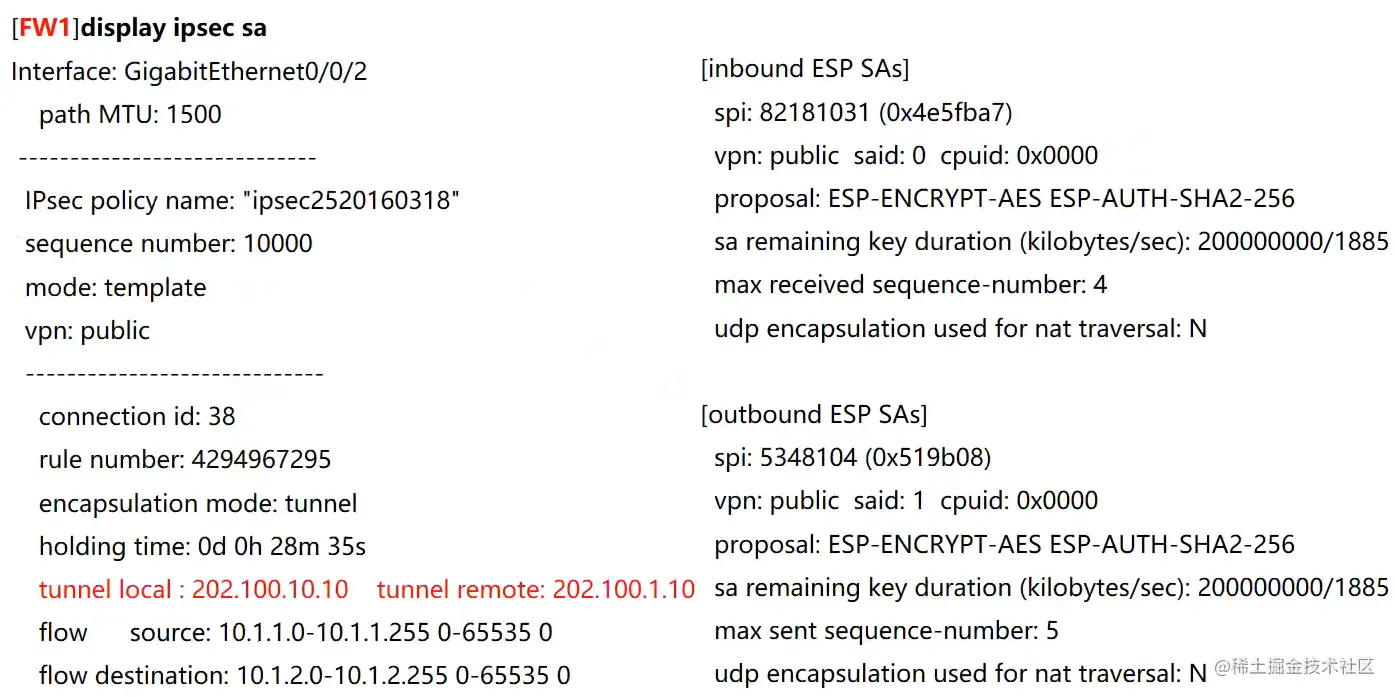
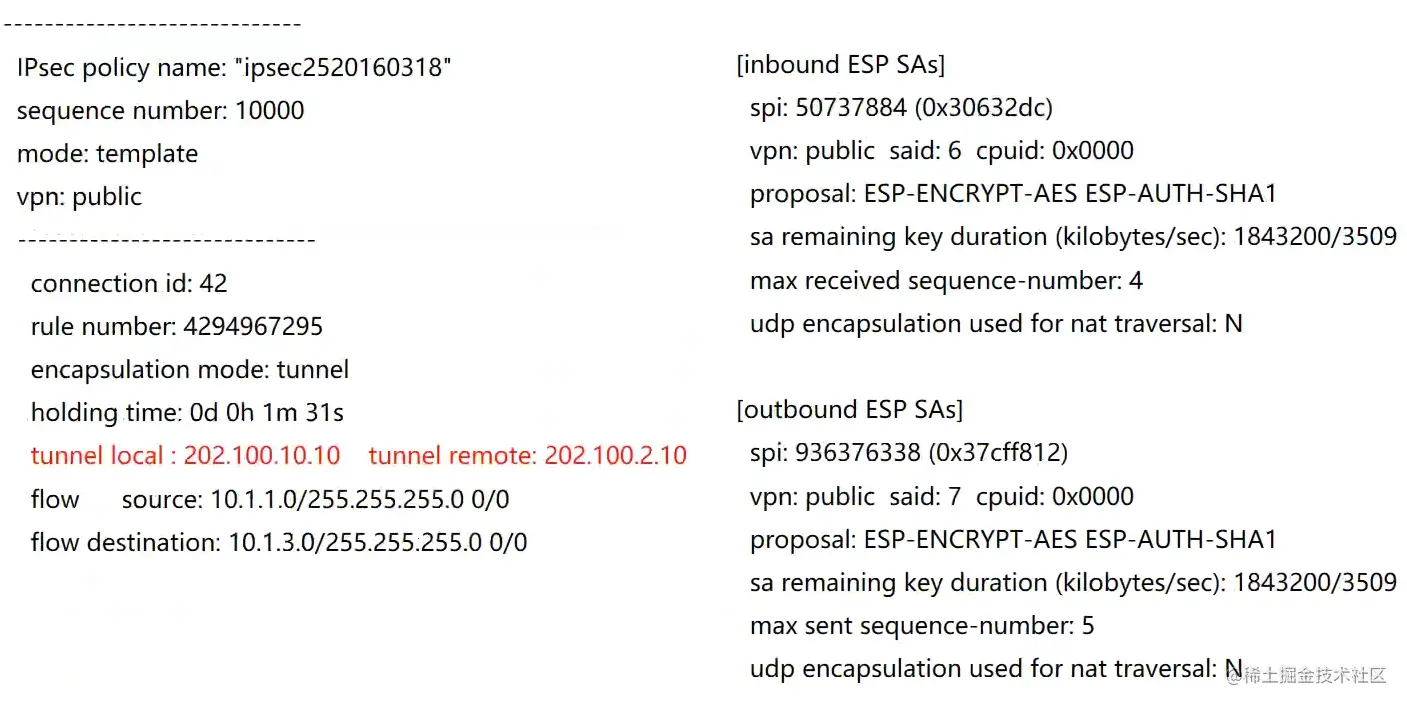
Hub查看IPsec SA
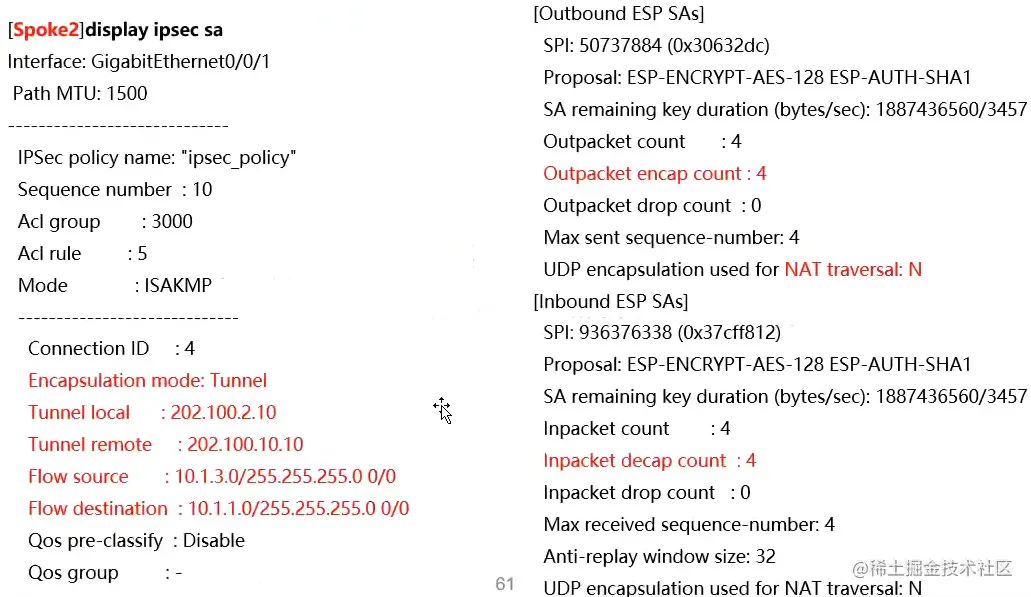
Spoke2查看IPsec SA
实验
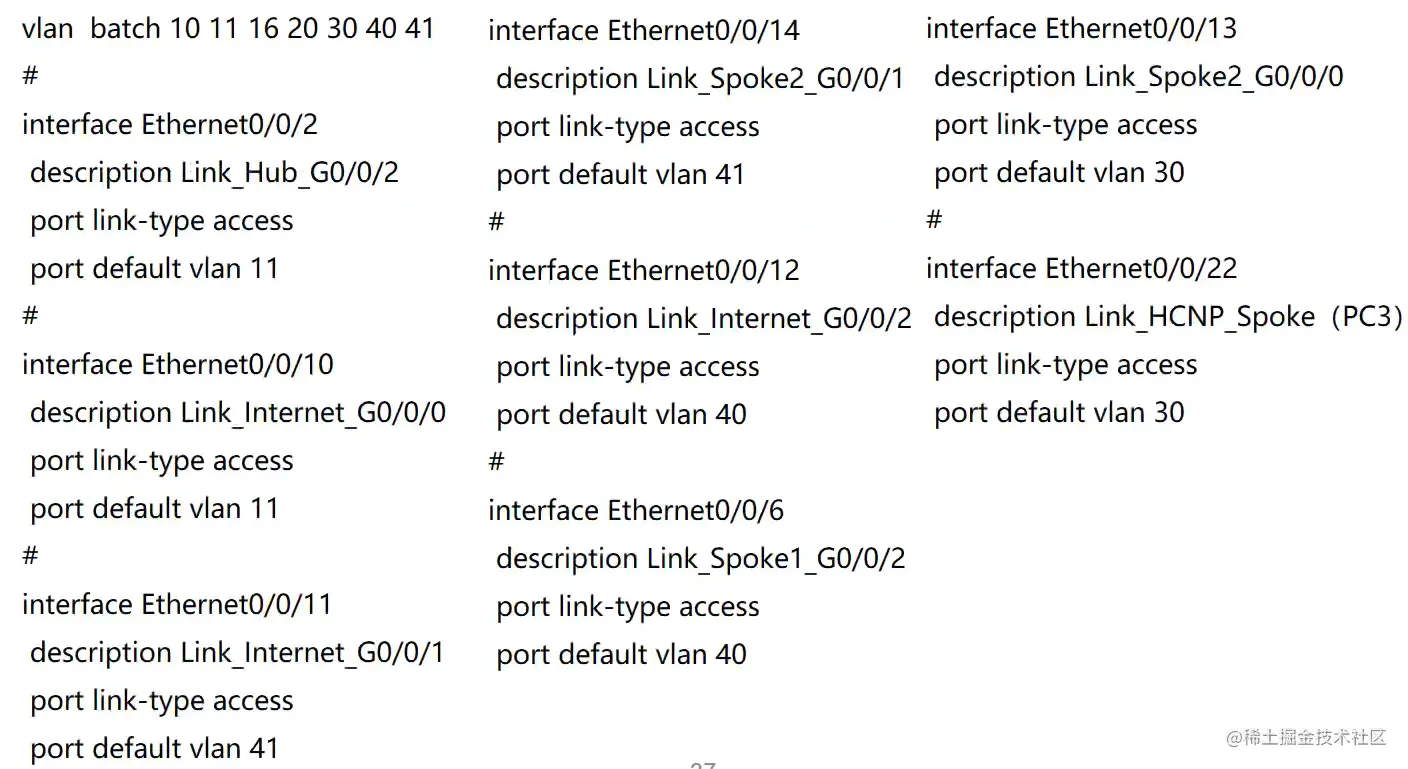
SW1
vlan batch 10 11 16 20 30 40 41
interface Ethernet0/0/2
description Link_Hub_G0/0/2
port link-type access
port default vlan 11
interface Ethernet0/0/10
description Link_Internet_G0/0/0
port link-type access
port default vlan 11
interface Ethernet0/0/11
description Link_Internet_G0/0/1
port link-type access
port default vlan 41
interface Ethernet0/0/14
description Link_Spoke2_G0/0/1
port link-type access
port default vlan 41
interface Ethernet0/0/12
description Link_Internet_G0/0/2
port link-type access
port default vlan 40
interface Ethernet0/0/6
description Link_Spoke1_G0/0/2
port link-type access
port default vlan 40
interface Ethernet0/0/13
description Link_Spoke2_G0/0/0
port link-type access
port default vlan 30
interface Ethernet0/0/22
description Link_HCNP_Spoke(PC3)
port link-type access
port default vlan 30
复制代码FW1(Hub)
interface g0/0/1
ip address 10.1.1.10 24
interface g0/0/2
ip address 202.100.10.10 24
undo ip route-static 0.0.0.0 0.0.0.0 202.100.1.11
ip route-static 0.0.0.0 0.0.0.0 202.100.10.254
// 用图形化界面配置后的结果
acl number 3000
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
ike proposal 1
authentication-algorithm sha2-256
integrity-algorithm aes-xcbc-96 hmac-sha2-256
ike peer ike48143238157
exchange-mode auto
pre-shared-key Huawei@123
ike negotiate compatible
ike-proposal 1
remote-id-type none
ipsec proposal prop48143238157
encapsulation-mode auto
esp authentication-algorithm sha2-256
ipsec policy-template tpl48143238157 1
security acl 3000
ike-peer ike48143238157
alias hub_ipsec
proposal prop48143238157
local-address applied-interface
sa duration traffic-based 200000000
sa duration time-based 3600
ipsec policy ipsec4814323820 10000 isakmp template tpl48143238157
interface GigabitEthernet0/0/2
ipsec policy ipsec4814323820 auto-neg
ip service-set ISAKMP type object
service 0 protocol udp source-port 0 to 65535 destination-port 5000
security-policy
rule name ipsec1
source-zone local
destination-zone untrust
source-address 202.100.10.10 mask 255.255.255.255
service ISAKMP
service esp
action permit
rule name ipsec2
source-zone untrust
destination-zone local
destination-address 202.100.10.10 mask 255.255.255.255
service ISAKMP
service esp
action permit
rule name ipsec3
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address address-set ipsec
destination-address address-set ipsec
action permit
复制代码FW2(Spoke1)
interface g0/0/1
ip address 10.1.2.10 24
interface g0/0/2
ip address 202.100.1.10 24
undo ip route-static 0.0.0.0 0.0.0.0 202.100.1.10
ip route-static 0.0.0.0 0.0.0.0 202.100.1.254
复制代码AR1(Internet)
interface g0/0/0
undo portswitch
ip address 202.100.10.254 24
interface g0/0/1
undo portswitch
ip address 202.100.2.254 24
interface g0/0/2
undo portswitch
ip address 202.100.1.254 24
复制代码AR2(Spoke2)
interface g0/0/1
undo portswitch
ip address 202.100.2.10 24
interface g0/0/0
undo portswitch
ip address 10.1.3.10 24
ip route-static 0.0.0.0 0.0.0.0 202.100.2.254
ike proposal 10
encryption-algorithm aes-cbc-128
authentication-algorithm sha2-256
ike peer hub v1
exchange-mode main
pre-shared-key simple Huawei@123
ike-proposal 10
remote-address 202.100.10.10
acl 3000
rule permit ip source 10.1.3.0 0.0.0.255 destination 10.1.1.0 0.00.255
ipsec proposal 10
esp encryption-algorithm aes-128
esp authentication-algorithm sha1
ipsec policy ipsec_policy 10 isakmp
security acl 3000
ike-peer hub
proposal 10
interface g0/0/1
ipsec policy ipsec_policy
以上是关于华为防火墙基础自学系列 | Hub Spoke IPsec VdPdNd的主要内容,如果未能解决你的问题,请参考以下文章
100集华为HCIE安全培训视频教材整理 | Hub Spoke IPSec VdPdN
100集华为HCIE安全培训视频教材整理 | Hub Spoke IPSec VPN