关于 AWS IAM Role 的最佳实践
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了关于 AWS IAM Role 的最佳实践相关的知识,希望对你有一定的参考价值。
一、EC2针对 EC2 上面的应用程序,不要分配 User Credentials,使用 IAM Role Attachment。
可以访问 EC2 的 meatdata 查看赋予的 Role 权限
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/二、Software on local laptop
针对在自己电脑上面开发测试的用户,用户需要 S3 的访问权限,不给用户分配权限,这样可以避免 AK/SK 丢失造成的损失,我们可以给 User 分配一个 Cross accunt role,让用户使用接口 assume-role 获取临时的 AK/SK,然后去访问AWS 资源。
2.1、创建用户 alice
不给用户分配任何权限。
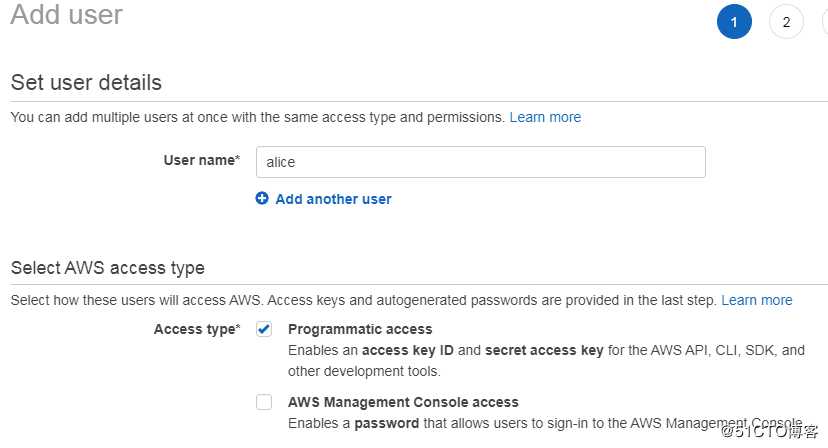
最后得到用户的 AK/SK
Access key ID :AKIA5NAGHF6N2WFTQZP6
Secret access key:TqJ/9Hg450x204r1lai+C3w0+3kvVOeTckPZhvau2.2、创建一个跨账户 Role
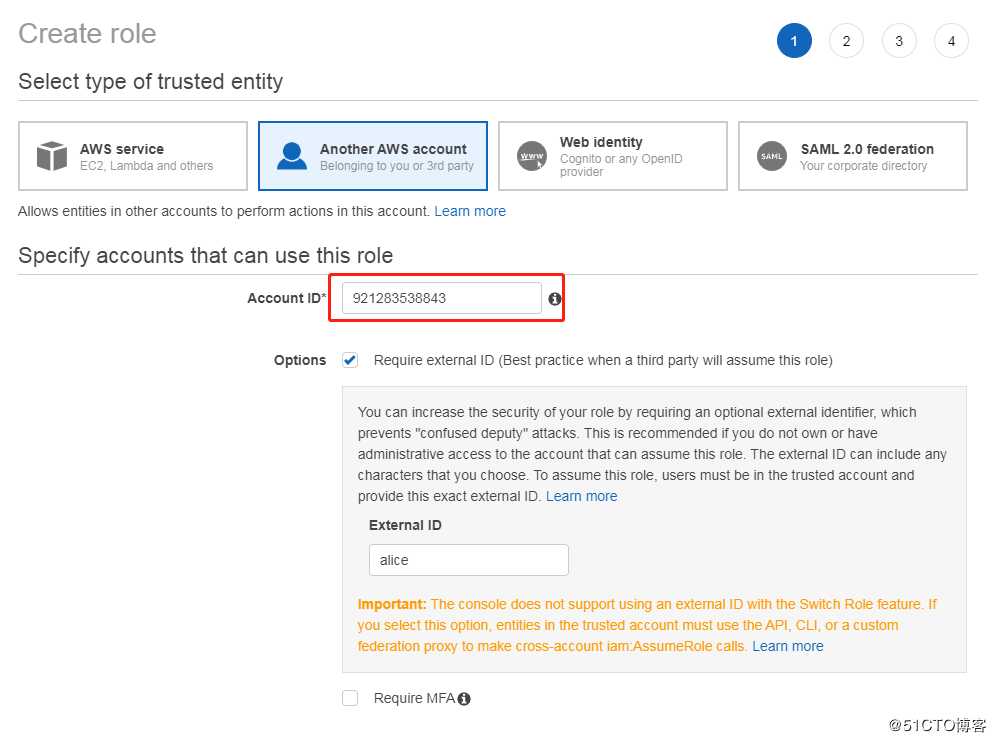
给角色增加权限。
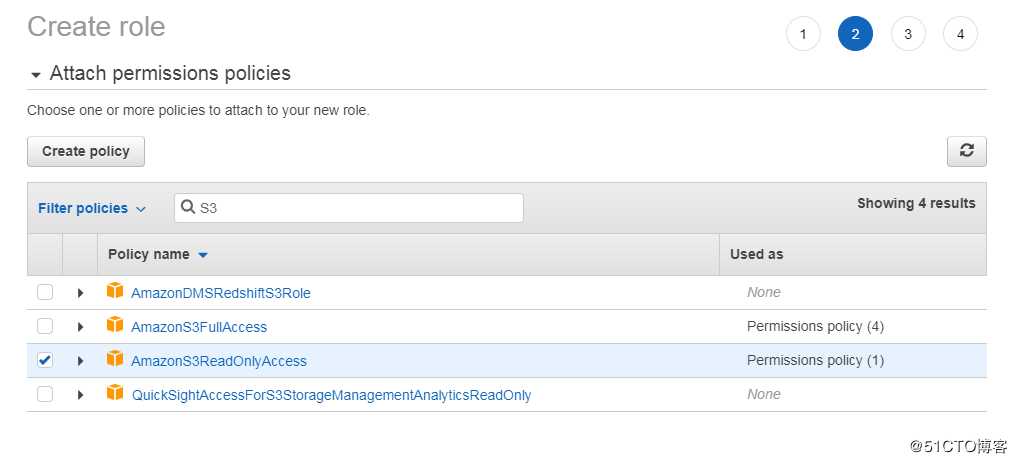
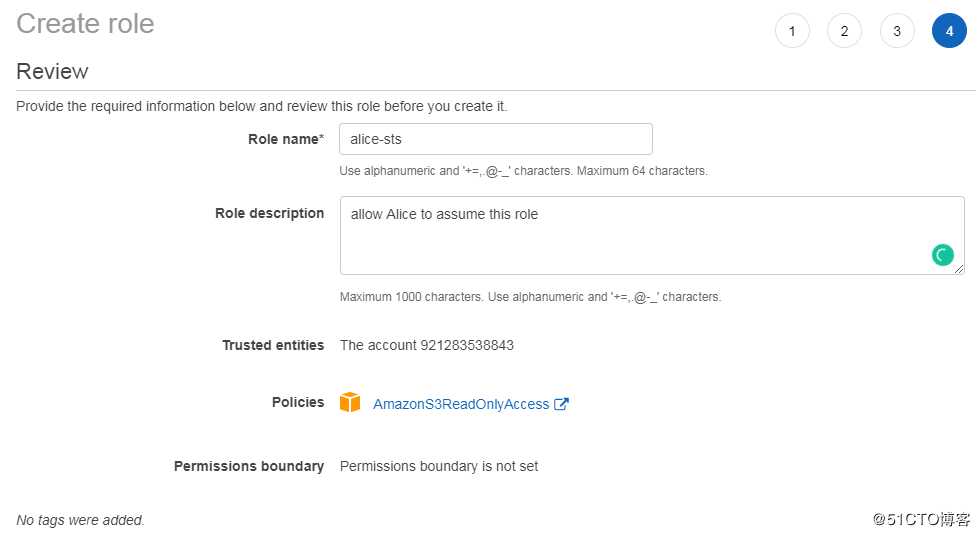
生成的 Role ARN:arn:aws:iam::921283538843:role/alice-sts给 alice 赋予 assume role 的权限。
Policy 格式如下:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::921283538843:role/alice-sts"
}
]
}2.3、测试用户权限
直接使用 AK/SK,查看用户是否有相应的权限。
使用 aws configure 配置。
wangzan:~/.aws $ aws configure
AWS Access Key ID [****************H6YU]: AKIA5NAGHF6N2WFTQZP6
AWS Secret Access Key [****************bVA/]: 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
Default region name [us-east-1]:
Default output format [json]:
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AIDA5NAGHF6NZASTSA7Y6",
"Arn": "arn:aws:iam::921283538843:user/alice"
}
wangzan:~/.aws $ aws s3 ls
An error occurred (AccessDenied) when calling the ListBuckets operation: Access Denied直接使用是获取不到权限的,那我们使用 assume-role。
wangzan:~/.aws $ aws sts assume-role --role-arn arn:aws:iam::921283538843:role/alice-sts --role-session-name s3-access --external-id alice
{
"AssumedRoleUser": {
"AssumedRoleId": "AROA5NAGHF6NSZZVCDMHE:s3-access",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/s3-access"
},
"Credentials": {
"SecretAccessKey": "sJuL4gzx6ScdloJyyO6J4mCnFdtMcFm/uAPVjOz7",
"SessionToken": "IQoJb3JpZ2luX2VjECMaCXVzLWVhc3QtMSJHMEUCIGkmsQ250D6CqAQfsWxfMog5SYovpefP5jMS2+cOUexGAiEAnlNtMrdhtz60YEjEoCCHce3YVQOMTCXf2gAJf7RSv+Aq2QEIi///////////ARAAGgw5MjEyODM1Mzg4NDMiDE3ySalHbx1Bf97NjiqtAcmjLjLW8FsTQMkO1xBUFbREur7ZqtO/AGR2oG6AnZIUUXNr2RRcmE6+IQgArlMBzppC/Q2uAnPkbz1GIdMKohUbL+9d2eZIOBwr9Vs/43iFSuAsdiLa9C5HI3++keG+5IkjS/Yj9rP30p1Bj2JK6TlTUQnZtINf1im4PmoIrxotWXkJH6BU8kG7PJ3bOgFCRWeG8w3h/d3sCx4GqUmnKISKosHSBUidm6PJ41GNMMSul/AFOuMBB0LfECQaR+C8+uxpil5KRE0a5DDq+IPDWaPQIpQ+s5q4ewLpSfGKTwKTrDPk7Hi1R/vhuNKNNUcgSjzz5Wh4NwjkbGmddcFDvlZCv2rXIRMPbcM6i/bXTz3HbCX/f5K3bcubiIShpezfDm/00Iy+qGPzaqDLZ5XNkMZ9msXBVYYd0YS++wprPGpX5GQBKh/vqS4HPWCeqRRrHbKGQO3/ycMXjjeHKpY07WcXhM3lbDR583JDcLTsfItldFeC8y4aXMGugTLUwmQm9pihC/TxP13zjWl1rh/cgR4FGDFbosb1Bq0=",
"Expiration": "2019-12-27T11:04:52Z",
"AccessKeyId": "ASIA5NAGHF6NZJHS6VVN"
}
}然后去编辑 ~/.aws/credentials,把生成的Credentials放到里面,如下:
[default]
aws_access_key_id = ASIA5NAGHF6NZJHS6VVN
aws_secret_access_key = sJuL4gzx6ScdloJyyO6J4mCnFdtMcFm/uAPVjOz7
aws_session_token = IQoJb3JpZ2luX2VjECMaCXVzLWVhc3QtMSJHMEUCIGkmsQ250D6CqAQfsWxfMog5SYovpefP5jMS2+cOUexGAiEAnlNtMrdhtz60YEjEoCCHce3YVQOMTCXf2gAJf7RSv+Aq2QEIi///////////ARAAGgw5MjEyODM1Mzg4NDMiDE3ySalHbx1Bf97NjiqtAcmjLjLW8FsTQMkO1xBUFbREur7ZqtO/AGR2oG6AnZIUUXNr2RRcmE6+IQgArlMBzppC/Q2uAnPkbz1GIdMKohUbL+9d2eZIOBwr9Vs/43iFSuAsdiLa9C5HI3++keG+5IkjS/Yj9rP30p1Bj2JK6TlTUQnZtINf1im4PmoIrxotWXkJH6BU8kG7PJ3bOgFCRWeG8w3h/d3sCx4GqUmnKISKosHSBUidm6PJ41GNMMSul/AFOuMBB0LfECQaR+C8+uxpil5KRE0a5DDq+IPDWaPQIpQ+s5q4ewLpSfGKTwKTrDPk7Hi1R/vhuNKNNUcgSjzz5Wh4NwjkbGmddcFDvlZCv2rXIRMPbcM6i/bXTz3HbCX/f5K3bcubiIShpezfDm/00Iy+qGPzaqDLZ5XNkMZ9msXBVYYd0YS++wprPGpX5GQBKh/vqS4HPWCeqRRrHbKGQO3/ycMXjjeHKpY07WcXhM3lbDR583JDcLTsfItldFeC8y4aXMGugTLUwmQm9pihC/TxP13zjWl1rh/cgR4FGDFbosb1Bq0=然后再去请求 S3。
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AROA5NAGHF6NSZZVCDMHE:s3-access",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/s3-access"
}
2.4、自动更换临时权限
修改 ~/.aws/credentials,出现了一点问题,我就把那个Role 里面的限制取消了,也就是那个 external-id。
[alice]
aws_access_key_id = AKIA5NAGHF6N2WFTQZP6
aws_secret_access_key = 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
aws_session_token =
[default]
role_arn = arn:aws:iam::921283538843:role/alice-sts
source_profile = alice可以看下目前的 Role。
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AROA5NAGHF6NSZZVCDMHE:botocore-session-1577441862",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/botocore-session-1577441862"
}以上是关于关于 AWS IAM Role 的最佳实践的主要内容,如果未能解决你的问题,请参考以下文章
Terraform aws_iam_role_policy 中的 JSON 语法错误
服务角色 arn:aws:iam::20011470201:role/deploy 无权执行以下操作:autoscaling:DescribeLifecycleHooks
Terraform AWS 提供商数据源 aws_iam_role 所需的参数“名称”是不是需要角色的路径?
带有 iam_role 的 AWS Redshift COPY