k8s部署---master节点组件部署
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了k8s部署---master节点组件部署相关的知识,希望对你有一定的参考价值。
kube-APIserver组件介绍- kube-APIserver提供了k8s各类资源对象(pod,RC,Service等)的增删改查及watch等HTTP Rest接口,是整个系统的数据总线和数据中心。
kube-APIserver的功能
- 提供了集群管理的REST API接口(包括认证授权、数据校验以及集群状态变更)
- 提供其他模块之间的数据交互和通信的枢纽(其他模块通过API Server查询或修改数据,只有API Server才直接操作etcd)
- 是资源配额控制的入口
- 拥有完备的集群安全机制
kube-apiserver工作原理图
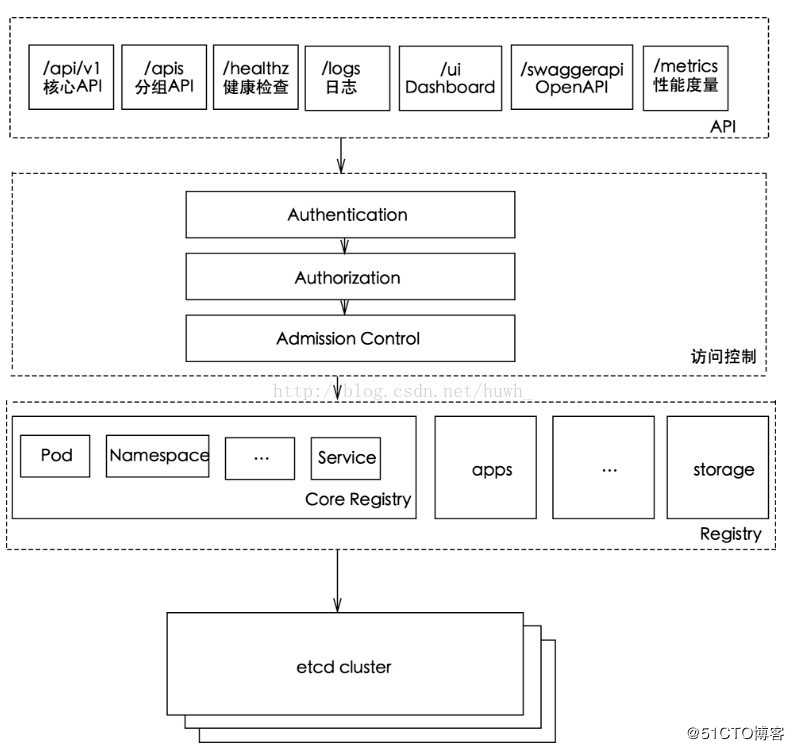
kubernetes API的访问
- k8s通过kube-apiserver这个进程提供服务,该进程运行在单个k8s-master节点上。默认有两个端口
- 本地端口
- 该端口用于接收HTTP请求
- 该端口默认值为8080,可以通过API Server的启动参数“--insecure-port”的值来修改默认值
- 默认的IP地址为“localhost”,可以通过启动参数“--insecure-bind-address”的值来修改该IP地址
- 非认证或授权的HTTP请求通过该端口访问API Server
- 安全端口
- 该端口默认值为6443,可通过启动参数“--secure-port”的值来修改默认值
- 默认IP地址为非本地(Non-Localhost)网络端口,通过启动参数“--bind-address”设置该值
- 该端口用于接收HTTPS请求
- 用于基于Tocken文件或客户端证书及HTTP Base的认证
- 用于基于策略的授权
- 默认不启动HTTPS安全访问控制
kube-controller-manager组件介绍
- kube-Controller Manager作为集群内部的管理控制中心,负责集群内的Node、Pod副本、服务端点(Endpoint)、命名空间(Namespace)、服务账号(ServiceAccount)、资源定额(ResourceQuota)的管理,当某个Node意外宕机时,Controller Manager会及时发现并执行自动化修复流程,确保集群始终处于预期的工作状态。
kube-scheduler组件介绍
- kube-scheduler是以插件形式存在的组件,正因为以插件形式存在,所以其具有可扩展可定制的特性。kube-scheduler相当于整个集群的调度决策者,其通过预选和优选两个过程决定容器的最佳调度位置。
- kube-scheduler(调度器)的指责主要是为新创建的pod在集群中寻找最合适的node,并将pod调度到Node上
- 从集群所有节点中,根据调度算法挑选出所有可以运行该pod的节点
- 再根据调度算法从上述node节点选择最优节点作为最终结果
- Scheduler调度器运行在master节点,它的核心功能是监听apiserver来获取PodSpec.NodeName为空的pod,然后为pod创建一个binding指示pod应该调度到哪个节点上,调度结果写入apiserver
kube-scheduler主要职责
- 集群高可用:如果 kube-scheduler 设置了 leader-elect 选举启动参数,那么会通过 etcd 进行节点选主( kube-scheduler 和 kube-controller-manager 都使用了一主多从的高可用方案)
- 调度资源监听:通过 list-Watch 机制监听 kube-apiserver 上资源的变化,这里的资源主要指的是 Pod 和 Node
- 调度节点分配:通过预选(Predicates)与优选(Priorites)策略,为待调度的 Pod 分配一个 Node 进行绑定并填充nodeName,同时将分配结果通过 kube-apiserver 写入 etcd
实验部署
实验环境
- Master01:192.168.80.12
- Node01:192.168.80.13
- Node02:192.168.80.14
- 本篇实验部署是接上篇文章Flannel部署的,所以实验环境不变,本次部署主要是部署master节点需要的组件
kube-APIserver组件部署
- master01服务器操作,配置apiserver自签证书
[root@master01 k8s]# cd /mnt/ //进入宿主机挂载目录 [root@master01 mnt]# ls etcd-cert etcd-v3.3.10-linux-amd64.tar.gz k8s-cert.sh master.zip etcd-cert.sh flannel.sh kubeconfig.sh node.zip etcd.sh flannel-v0.10.0-linux-amd64.tar.gz kubernetes-server-linux-amd64.tar.gz [root@master01 mnt]# cp master.zip /root/k8s/ //复制压缩包到k8s工作目录 [root@master01 mnt]# cd /root/k8s/ //进入k8s工作目录 [root@master01 k8s]# ls cfssl.sh etcd-v3.3.10-linux-amd64 kubernetes-server-linux-amd64.tar.gz etcd-cert etcd-v3.3.10-linux-amd64.tar.gz master.zip etcd.sh flannel-v0.10.0-linux-amd64.tar.gz [root@master01 k8s]# unzip master.zip //解压压缩包 Archive: master.zip inflating: apiserver.sh inflating: controller-manager.sh inflating: scheduler.sh [root@master01 k8s]# mkdir /opt/kubernetes/{cfg,bin,ssl} -p //在master01中创建工作目录,之前在node节点中同样也创建过工作目录 [root@master01 k8s]# mkdir k8s-cert //创建自签证书目录 [root@master01 k8s]# cp /mnt/k8s-cert.sh /root/k8s/k8s-cert //将挂载的自签证书脚本移动到k8s工作目录中的自签证书目录 [root@master01 k8s]# cd k8s-cert //进入目录 [root@master01 k8s-cert]# vim k8s-cert.sh //编辑拷贝过来的脚本文件 ... cat > server-csr.json <<EOF { "CN": "kubernetes", "hosts": [ "10.0.0.1", "127.0.0.1", "192.168.80.12", //更改地址为master01IP地址 "192.168.80.11", //添加地址为master02IP地址,为之后我们要做的多节点做准备 "192.168.80.100", //添加vrrp地址,为之后要做的负载均衡做准备 "192.168.80.13", //更改地址为node01节点IP地址 "192.168.80.14", //更改地址为node02节点IP地址 "kubernetes", "kubernetes.default", "kubernetes.default.svc", "kubernetes.default.svc.cluster", "kubernetes.default.svc.cluster.local" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "BeiJing", "ST": "BeiJing", "O": "k8s", "OU": "System" } ] } EOF ... :wq [root@master01 k8s-cert]# bash k8s-cert.sh //执行脚本,生成证书 2020/02/10 10:59:17 [INFO] generating a new CA key and certificate from CSR 2020/02/10 10:59:17 [INFO] generate received request 2020/02/10 10:59:17 [INFO] received CSR 2020/02/10 10:59:17 [INFO] generating key: rsa-2048 2020/02/10 10:59:17 [INFO] encoded CSR 2020/02/10 10:59:17 [INFO] signed certificate with serial number 10087572098424151492431444614087300651068639826 2020/02/10 10:59:17 [INFO] generate received request 2020/02/10 10:59:17 [INFO] received CSR 2020/02/10 10:59:17 [INFO] generating key: rsa-2048 2020/02/10 10:59:17 [INFO] encoded CSR 2020/02/10 10:59:17 [INFO] signed certificate with serial number 125779224158375570229792859734449149781670193528 2020/02/10 10:59:17 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). 2020/02/10 10:59:17 [INFO] generate received request 2020/02/10 10:59:17 [INFO] received CSR 2020/02/10 10:59:17 [INFO] generating key: rsa-2048 2020/02/10 10:59:17 [INFO] encoded CSR 2020/02/10 10:59:17 [INFO] signed certificate with serial number 328087687681727386760831073265687413205940136472 2020/02/10 10:59:17 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). 2020/02/10 10:59:17 [INFO] generate received request 2020/02/10 10:59:17 [INFO] received CSR 2020/02/10 10:59:17 [INFO] generating key: rsa-2048 2020/02/10 10:59:18 [INFO] encoded CSR 2020/02/10 10:59:18 [INFO] signed certificate with serial number 525069068228188747147886102005817997066385735072 2020/02/10 10:59:18 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). [root@master01 k8s-cert]# ls *pem //查看 会生成8个证书 admin-key.pem admin.pem ca-key.pem ca.pem kube-proxy-key.pem kube-proxy.pem server-key.pem server.pem [root@master01 k8s-cert]# cp ca*pem server*pem /opt/kubernetes/ssl/ //将证书移动到k8s工作目录下ssl目录中 -
配置apiserver
[root@master01 k8s-cert]# cd .. //回到k8s工作目录 [root@master01 k8s]# tar zxvf kubernetes-server-linux-amd64.tar.gz //解压软件包 kubernetes/ kubernetes/server/ kubernetes/server/bin/ ... [root@master01 k8s]# cd kubernetes/server/bin/ //进入加压后软件命令存放目录 [root@master01 bin]# ls apiextensions-apiserver kube-apiserver.docker_tag kube-proxy cloud-controller-manager kube-apiserver.tar kube-proxy.docker_tag cloud-controller-manager.docker_tag kube-controller-manager kube-proxy.tar cloud-controller-manager.tar kube-controller-manager.docker_tag kube-scheduler hyperkube kube-controller-manager.tar kube-scheduler.docker_tag kubeadm kubectl kube-scheduler.tar kube-apiserver kubelet mounter [root@master01 bin]# cp kube-apiserver kubectl kube-controller-manager kube-scheduler /opt/kubernetes/bin/ //复制关键命令文件到k8s工作目录的bin目录中 [root@master01 bin]# cd /root/k8s/ [root@master01 k8s]# head -c 16 /dev/urandom | od -An -t x | tr -d ‘ ‘ //生成一个序列号 c37758077defd4033bfe95a071689272 [root@master01 k8s]# vim /opt/kubernetes/cfg/token.csv //创建token.csv文件,可以理解为创建一个管理性的角色 c37758077defd4033bfe95a071689272,kubelet-bootstrap,10001,"system:kubelet-bootstrap" //指定用户角色身份,前面的序列号使用生成的序列号 :wq [root@master01 k8s]# bash apiserver.sh 192.168.80.12 https://192.168.80.12:2379,https://192.168.80.13:2379,https://192.168.80.14:2379 //二进制文件,token,证书都准备好,执行apiserver脚本,同时生成配置文件 Created symlink from /etc/systemd/system/multi-user.target.wants/kube-apiserver.service to /usr/lib/systemd/system/kube-apiserver.service. [root@master01 k8s]# ps aux | grep kube //检查进程是否启动成功 root 17088 8.7 16.7 402260 312192 ? Ssl 11:17 0:08 /opt/kubernetes/bin/kube-apiserver --logtostderr=true --v=4 --etcd-servers=https://192.168.80.12:2379,https://192.168.80.13:2379,https://192.168.80.14:2379 --bind-address=192.168.80.12 --secure-port=6443 --advertise-address=192.168.80.12 --allow-privileged=true --service-cluster-ip-range=10.0.0.0/24 --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction --authorization-mode=RBAC,Node --kubelet-https=true --enable-bootstrap-token-auth --token-auth-file=/opt/kubernetes/cfg/token.csv --service-node-port-range=30000-50000 --tls-cert-file=/opt/kubernetes/ssl/server.pem --tls-private-key-file=/opt/kubernetes/ssl/server-key.pem --client-ca-file=/opt/kubernetes/ssl/ca.pem --service-account-key-file=/opt/kubernetes/ssl/ca-key.pem --etcd-cafile=/opt/etcd/ssl/ca.pem --etcd-certfile=/opt/etcd/ssl/server.pem --etcd-keyfile=/opt/etcd/ssl/server-key.pem root 17101 0.0 0.0 112676 980 pts/0 S+ 11:19 0:00 grep --color=auto kube [root@master01 k8s]# cat /opt/kubernetes/cfg/kube-apiserver //查看生成的配置文件 KUBE_APISERVER_OPTS="--logtostderr=true --v=4 --etcd-servers=https://192.168.80.12:2379,https://192.168.80.13:2379,https://192.168.80.14:2379 --bind-address=192.168.80.12 --secure-port=6443 --advertise-address=192.168.80.12 --allow-privileged=true --service-cluster-ip-range=10.0.0.0/24 --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction --authorization-mode=RBAC,Node --kubelet-https=true --enable-bootstrap-token-auth --token-auth-file=/opt/kubernetes/cfg/token.csv --service-node-port-range=30000-50000 --tls-cert-file=/opt/kubernetes/ssl/server.pem --tls-private-key-file=/opt/kubernetes/ssl/server-key.pem --client-ca-file=/opt/kubernetes/ssl/ca.pem --service-account-key-file=/opt/kubernetes/ssl/ca-key.pem --etcd-cafile=/opt/etcd/ssl/ca.pem --etcd-certfile=/opt/etcd/ssl/server.pem --etcd-keyfile=/opt/etcd/ssl/server-key.pem" [root@master01 k8s]# netstat -ntap | grep 6443 //查看监听的端口是否开启 tcp 0 0 192.168.80.12:6443 0.0.0.0:* LISTEN 17088/kube-apiserve tcp 0 0 192.168.80.12:48320 192.168.80.12:6443 ESTABLISHED 17088/kube-apiserve tcp 0 0 192.168.80.12:6443 192.168.80.12:48320 ESTABLISHED 17088/kube-apiserve [root@master01 k8s]# netstat -ntap | grep 8080 //查看监听的端口是否开启 tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 17088/kube-apiserve - 配置scheduler服务
[root@master01 k8s]# ./scheduler.sh 127.0.0.1 //直接执行脚本,启动服务,并生成配置文件即可 Created symlink from /etc/systemd/system/multi-user.target.wants/kube-scheduler.service to /usr/lib/systemd/system/kube-scheduler.service. [root@master01 k8s]# systemctl status kube-scheduler.service //查看服务运行状态 ● kube-scheduler.service - Kubernetes Scheduler Loaded: loaded (/usr/lib/systemd/system/kube-scheduler.service; enabled; vendor preset: disabled) Active: active (running) since 一 2020-02-10 11:22:13 CST; 2min 46s ago //成功运行 Docs: https://github.com/kubernetes/kubernetes ... - 配置controller-manager服务
[root@master01 k8s]# chmod +x controller-manager.sh //添加脚本执行权限 [root@master01 k8s]# ./controller-manager.sh 127.0.0.1 //执行脚本,启动服务,并生成配置文件 Created symlink from /etc/systemd/system/multi-user.target.wants/kube-controller-manager.service to /usr/lib/systemd/system/kube-controller-manager.service. [root@master01 k8s]# systemctl status kube-controller-manager.service //查看运行状态 ● kube-controller-manager.service - Kubernetes Controller Manager Loaded: loaded (/usr/lib/systemd/system/kube-controller-manager.service; enabled; vendor preset: disabled) Active: active (running) since 一 2020-02-10 11:28:21 CST; 7min ago //成功运行 ... [root@master01 k8s]# /opt/kubernetes/bin/kubectl get cs //查看节点运行状态 NAME STATUS MESSAGE ERROR scheduler Healthy ok controller-manager Healthy ok etcd-2 Healthy {"health":"true"} etcd-0 Healthy {"health":"true"} etcd-1 Healthy {"health":"true"}master节点组件部署完成
以上是关于k8s部署---master节点组件部署的主要内容,如果未能解决你的问题,请参考以下文章