Rancher 部署Grafana+项目监控并集成LDAP
Posted weavepub
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Rancher 部署Grafana+项目监控并集成LDAP相关的知识,希望对你有一定的参考价值。
业务服务暴露了prometheus的指标,现需要获取该指标值,并用grafana进行展示,并集成ldap验证登入grafana
1、启动监控
在rancher对应的业务的项目下启用监控,工具 -> 监控。在服务列表中能够找到两个服务,这两个服务都可以访问prometheus数据。
http://access-prometheus
http://expose-prometheus:8080
2、部署Grafana
镜像
grafana/grafana:6.5.1密文:grafana
GF_SECURITY_ADMIN_PASSWORD=admin123环境变量
添加变量,声明ldap配置文件
GF_AUTH_LDAP_CONFIG_FILE=/opt/ldap.toml
GF_AUTH_LDAP_ENABLED=true添加附加资源
类型:Secret,源:grafana,键:All数据卷
添加PVC
pvc-grafana-data //pvc
/var/lib/grafana //容器路径
添加配置映射 /opt/ldap.toml
# To troubleshoot and get more log info enable ldap debug logging in grafana.ini
# [log]
# filters = ldap:debug
[[servers]]
# Ldap server host (specify multiple hosts space separated)
host = "172.16.5.123"
# Default port is 389 or 636 if use_ssl = true
port = 389
# Set to true if ldap server supports TLS
use_ssl = false
# Set to true if connect ldap server with STARTTLS pattern (create connection in insecure, then upgrade to secure connection with TLS)
start_tls = false
# set to true if you want to skip ssl cert validation
ssl_skip_verify = false
# set to the path to your root CA certificate or leave unset to use system defaults
# root_ca_cert = "/path/to/certificate.crt"
# Authentication against LDAP servers requiring client certificates
# client_cert = "/path/to/client.crt"
# client_key = "/path/to/client.key"
# Search user bind dn
bind_dn = "cn=manager,dc=tencent,dc=cn"
# Search user bind password
# If the password contains # or ; you have to wrap it with triple quotes. Ex """#password;"""
bind_password = 'admin123'
# User search filter, for example "(cn=%s)" or "(sAMAccountName=%s)" or "(uid=%s)"
search_filter = "(uid=%s)"
# An array of base dns to search through
search_base_dns = ["ou=员工,dc=tencent,dc=cn"]
## For Posix or LDAP setups that does not support member_of attribute you can define the below settings
## Please check grafana LDAP docs for examples
group_search_filter = "(&(objectClass=posixGroup)(memberUid=%s))"
group_search_base_dns = ["ou=部门,dc=tencent,dc=cn"]
group_search_filter_user_attribute = "uid"
# Specify names of the ldap attributes your ldap uses
[servers.attributes]
name = "givenName"
surname = "sn"
username = "cn"
member_of = "cn"
email = "email"
# Map ldap groups to grafana org roles
[[servers.group_mappings]]
group_dn = "cn=admins,ou=groups,dc=grafana,dc=org"
org_role = "Admin"
# To make user an instance admin (Grafana Admin) uncomment line below
# grafana_admin = true
# The Grafana organization database id, optional, if left out the default org (id 1) will be used
# org_id = 1
[[servers.group_mappings]]
group_dn = "cn=users,ou=groups,dc=grafana,dc=org"
org_role = "Editor"
[[servers.group_mappings]]
# If you want to match all (or no ldap groups) then you can use wildcard
group_dn = "*"
org_role = "Viewer"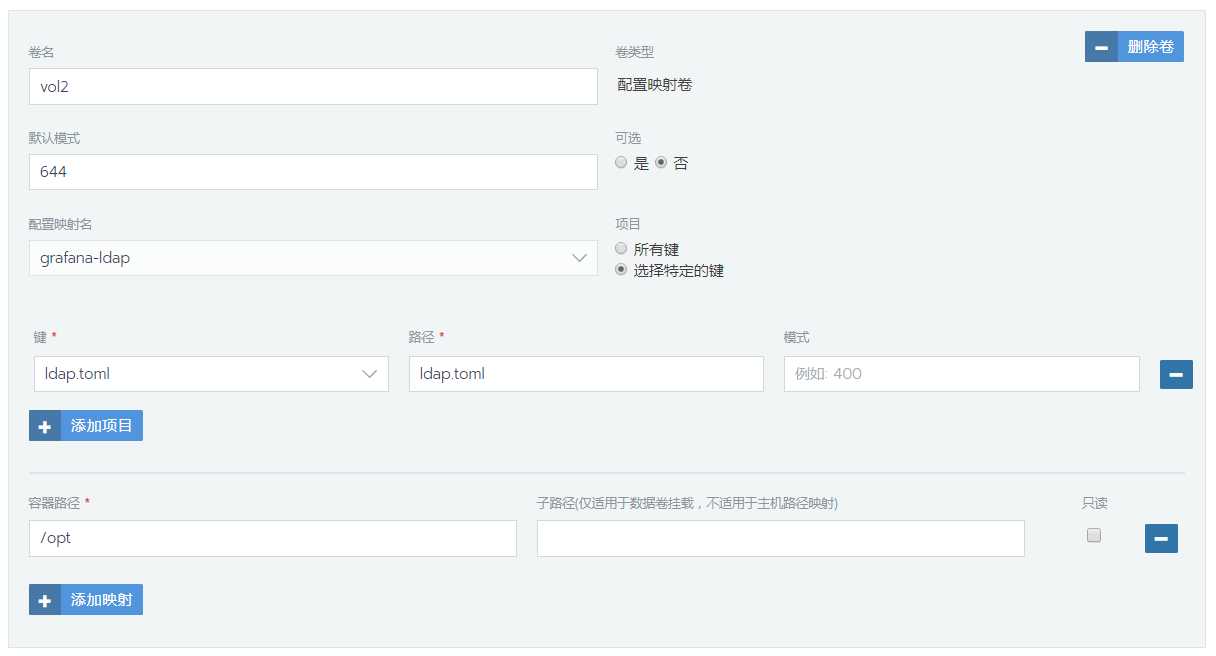
grafana集成LDAP参考:https://grafana.com/docs/grafana/latest/auth/ldap/
3、配置Grafana
添加数据源,因为grafana服务和该启用监控的项目不在用一个namespace,使用如下两个地址都可以访问。
http://access-prometheus.cattle-prometheus-p-jtkrp
http://expose-prometheus.metrics-prometheus-p-jtkrp:8080如果grafana和该项目不在同一个集群,则需要对access-prometheus再配置ingress暴露到集群外访问。
4、说明
1、如果收集整个集群的POD占用资源等数据,需要访问Rancher的 System 项目中cattle-prometheus命名空间下的access-prometheus 或 expose-prometheus-metrics 服务。
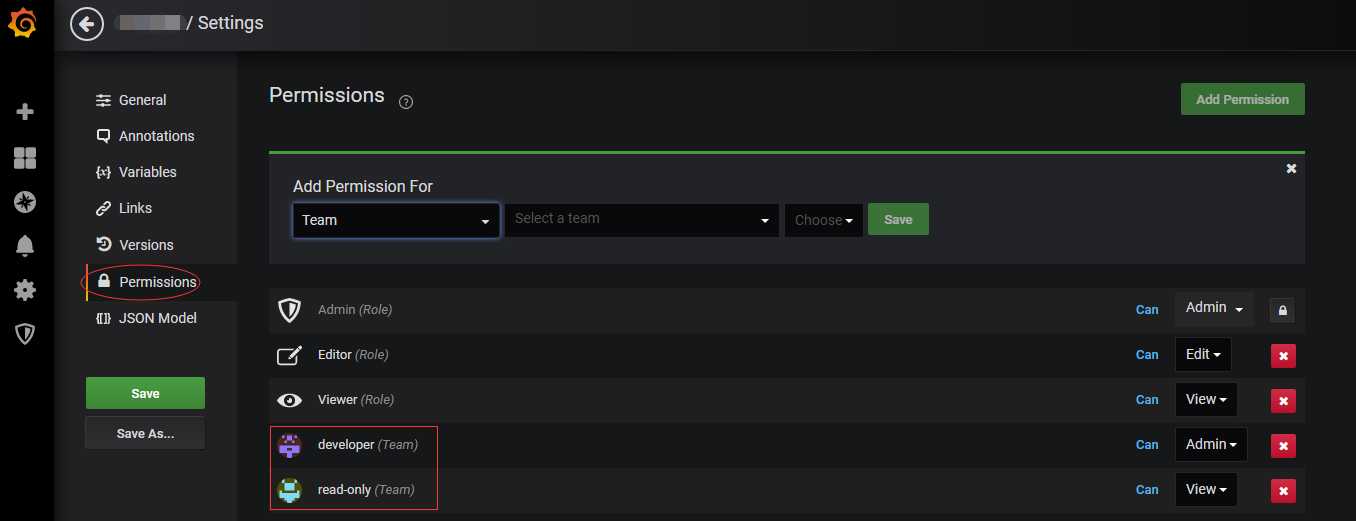
2、集成LDAP后,账号设置admin角色后,每次登入都会被重置权限。可以创建 Team,并赋予相关权限。
以上是关于Rancher 部署Grafana+项目监控并集成LDAP的主要内容,如果未能解决你的问题,请参考以下文章