QKD网络的中继方案
Posted limer98
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了QKD网络的中继方案相关的知识,希望对你有一定的参考价值。
源自:ITU-T标准中的密钥管理相关(Key management)
Alternative scheme of key relay
A key relay scheme to share a key between the originating node and destinating node is illustrated in Figure 3. The KeyAB is generated between KMA-A and KMA-B. The KeyAB is relayed from KMA-B to KMA-C by OTP encryption with the KeyBC. It is relayed from KMA-C to KMA-D by OTP encryption with KeyCD and finally supplied to KSA-D.
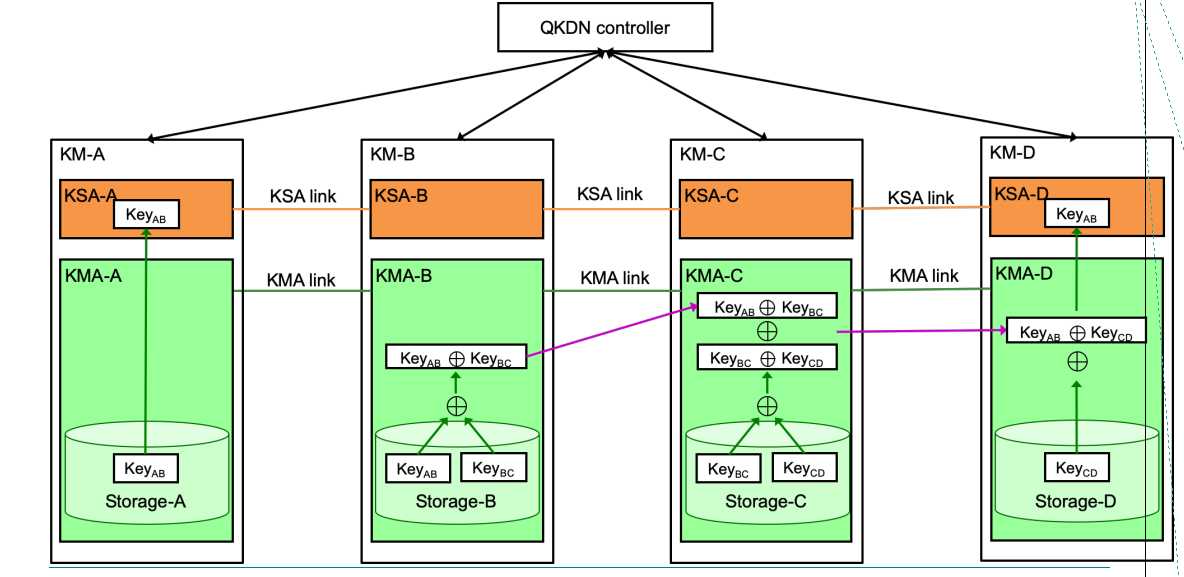
Figure 3 - Scheme of key relaying from point to point in Recommendation draft ITU-T Y.3800 (case 1)
In case 2 which is illustrated in Figure 4, a random bit string KeyRN which is generated locally at KMA-A is used for key relay from KMA-A to KMA-D.
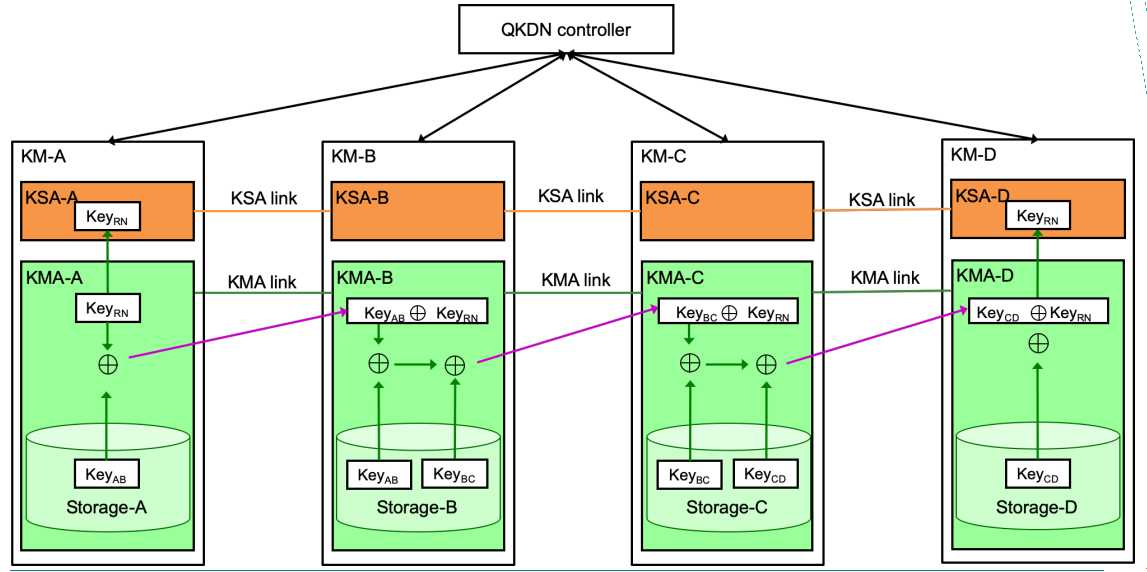
Figure 4 - Scheme of key relaying from point to point in Recommendation draft ITU-T Y.3800 (case 2)
There are two problems for the schemes case 1 and case 2 of key relaying from point to point in real application. One is that the XOR ciphertext key and the corresponding decryption key may coexist on one relay node, which has a security risk. The other is that the network has complex KMA links between nodes, which results in implementation difficulty. To help alleviate the above problems, two modified schemes of key relaying will be described in the following.
以上是关于QKD网络的中继方案的主要内容,如果未能解决你的问题,请参考以下文章