搭建harbor仓库LDAP认证
Posted xiaoyou2018
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了搭建harbor仓库LDAP认证相关的知识,希望对你有一定的参考价值。
ldap: 192.168.199.177
c5game.com
宿主机:192.168.199.224
测试客户机:192.168.199.223
安装docker、docker-compose
访问查看最新版本https://github.com/goharbor/harbor/releases并下载harbor-offline-installer-vxxx.tgz
[[email protected] ~]# cd /opt/ [[email protected]-registry opt]# wget https://storage.googleapis.com/harbor-releases/release-1.6.0/harbor-offline-installer-v1.6.2.tgz [[email protected] opt]tar zxvf harbor-offline-installer-v1.6.2.tgz && cd !$
修改 harbor.cfg
[[email protected] harbor]# cat harbor.cfg |grep -Ev ‘^$|^#‘ _version = 1.6.0 hostname = 192.168.199.224 ui_url_protocol = http max_job_workers = 10 customize_crt = on ssl_cert = /data/cert/server.crt ssl_cert_key = /data/cert/server.key secretkey_path = /data admiral_url = NA log_rotate_count = 50 log_rotate_size = 200M http_proxy = https_proxy = no_proxy = 127.0.0.1,localhost,ui,registry email_identity = email_server = smtp.mydomain.com email_server_port = 25 email_username = [email protected] email_password = abc email_from = admin <[email protected]> email_ssl = false email_insecure = false harbor_admin_password = TTdjy911.500 auth_mode = ldap_auth ldap_url = ldap://192.168.199.177:389 ldap_searchdn = cn=admin,dc=c5game,dc=com ldap_search_pwd = TTdjy911.500 ldap_basedn = ou=people,dc=c5game,dc=com ldap_uid = uid ldap_scope = 3 ldap_timeout = 5 ldap_verify_cert = true ldap_group_basedn = ou=group,dc=c5game,dc=com ldap_group_filter = objectclass=group ldap_group_gid = cn ldap_group_scope = 2 self_registration = on token_expiration = 30 project_creation_restriction = everyone db_host = postgresql db_password = root123 db_port = 5432 db_user = postgres redis_host = redis redis_port = 6379 redis_password = redis_db_index = 1,2,3 clair_db_host = postgresql clair_db_password = root123 clair_db_port = 5432 clair_db_username = postgres clair_db = postgres clair_updaters_interval = 12 uaa_endpoint = uaa.mydomain.org uaa_clientid = id uaa_clientsecret = secret uaa_verify_cert = true uaa_ca_cert = /path/to/ca.pem registry_storage_provider_name = filesystem registry_storage_provider_config = registry_custom_ca_bundle =
强调:harbor默认链接的是db_auth,如果想使用ldap_auth,
1,在默认情况下第一次登陆的时候在页面的设置里将认证方式改为ldap_auth,一定要将各个配置设置正确;
2,想使用ldap_auth的话,也可以在最初设置认证模式的时候设置为ldap模式,选项设置不正确可以在UI页面设置。
提醒:不管你设置为哪一种模式,只要用户中添加了除管理员的其他用户之后,认证模式就不能再更改;
执行 install.sh 安装
[[email protected] harbor]# ./install.sh
访问 http://192.168.199.224/harbor/sign-in (如果页面是空白,请更改浏览器模式为‘极速模式’)
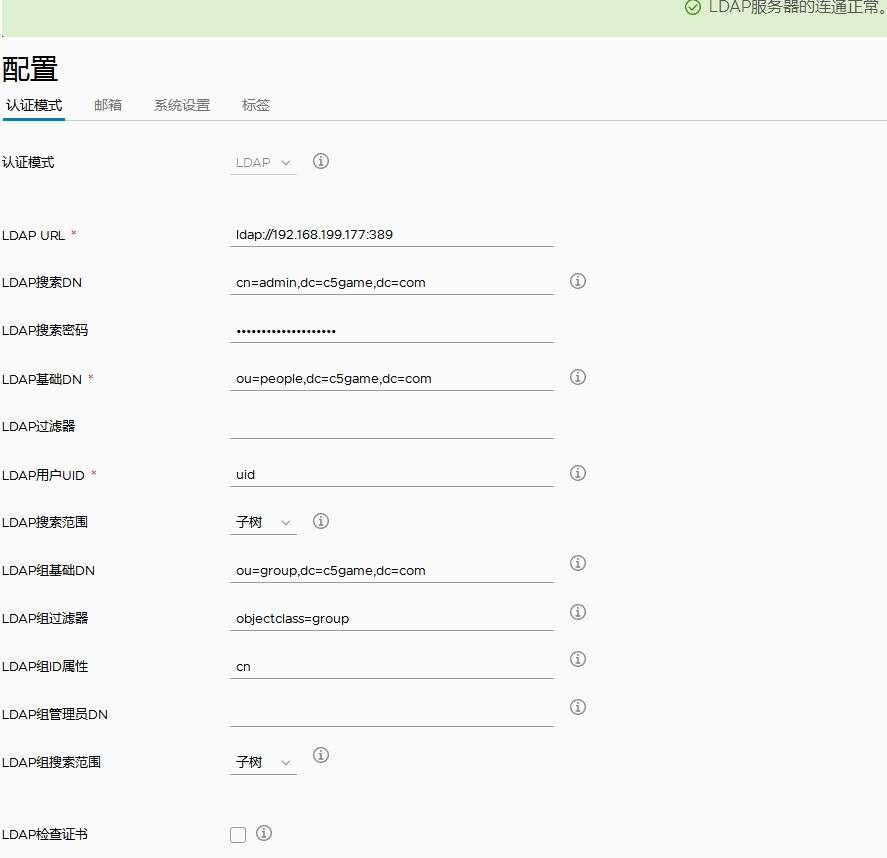
LDAP认证
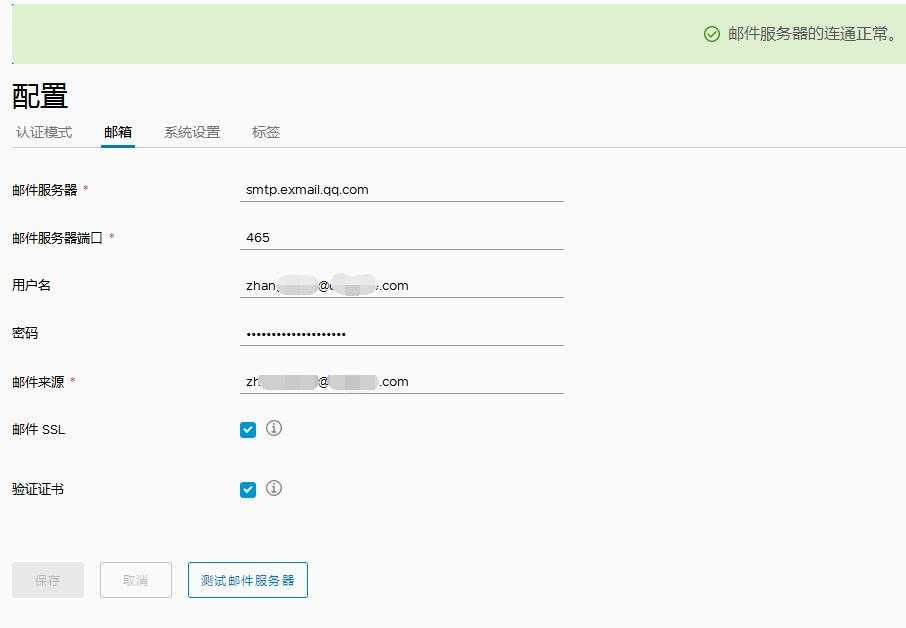
邮件设置
宿主机和客户机都需要更改/etc/sysconfig/docker 不然连接时候报错
docker login 192.168.199.224 Username: admin Password: Error response from daemon: Get https://192.168.199.224/v1/users/: dial tcp 10.236.63.76:443: getsockopt: connection refused
这是因为docker1.3.2版本开始默认docker registry使用的是https,我们设置Harbor默认http方式,所以当执行用docker login、pull、push等命令操作非https的docker regsitry的时就会报错。解决办法:
如果系统是MacOS,则可以点击“Preference”里面的“Advanced”在“Insecure Registry”里加上10.236.63.76,重启Docker客户端就可以了。
如果系统是Ubuntu,则修改配置文件/lib/systemd/system/docker.service,修改[Service]下ExecStart参数,增加 --insecure-registry 192.168.199.224
如果系统是Centos,可以修改配置/etc/sysconfig/docker,将OPTIONS增加 --insecure-registry 192.168.199.224
# Modify these options if you want to change the way the docker daemon runs OPTIONS=‘--selinux-enabled --log-driver=journald --signature-verification=false --insecure-registry 192.168.199.224‘ if [ -z "${DOCKER_CERT_PATH}" ]; then DOCKER_CERT_PATH=/etc/docker fi
然后重启docker服务或者重启宿主机
上传下载镜像
新建一个项目“test” ,访问级别私有,客户机安装docker
客户机下载测试镜像nginx
[[email protected] sysconfig]# docker pull nginx 给nginx镜像重做标签 [[email protected] sysconfig]# docker tag nginx:latest 192.168.199.224/test/nginx:latest 登录服务器 [[email protected] sysconfig]# docker login 192.168.199.224 Username (admin): admin Password: Login Succeeded 上传镜像 [[email protected] sysconfig]# docker push 192.168.199.224/test/nginx
使用LDAP账户拉取私库 test 镜像失败
docker pull 192.168.199.224/test/nginx:latest Error response from daemon: repository 192.168.199.224/test/nginx:latest not found: does not exist or no pull access
这是原因可能有,一是Harbor仓库上test/nginx确实不存在,二是项目未设置公开的时候,该账户未执行docker login 192.168.199.224登录操作,三是该账户对192.168.199.224/test项目没有权限,需要在该项目下增加该成员,并选择角色
如果需要修改Harbor的配置文件harbor.cfg,因为Harbor是基于docker-compose服务编排的,我们可以使用docker-compose命令重启Harbor。不修改配置文件,重启Harbor命令:docker-compose start | stop | restart
1、停止Harbor $ docker-compose down -v Stopping nginx ... done Stopping harbor-jobservice ... done ...... Removing harbor-log ... done Removing network harbor_harbor 2、启动Harbor $ docker-compose up -d Creating network "harbor_harbor" with the default driver Creating harbor-log ... ...... Creating nginx Creating harbor-jobservice ... done
参考: https://www.ilanni.com/?p=13492
https://blog.csdn.net/aixiaoyang168/article/details/73549898
https://ivanzz1001.github.io/records/post/docker/2018/04/11/docker-harbor-uage#2-%E7%94%A8%E6%88%B7%E8%B4%A6%E6%88%B7user-account 使用文档
https://github.com/goharbor/harbor/blob/master/docs/installation_guide.md#configuring-harbor-listening-on-a-customized-port 官网
以上是关于搭建harbor仓库LDAP认证的主要内容,如果未能解决你的问题,请参考以下文章