cp4 Docker 网络1
Posted wenyule
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了cp4 Docker 网络1相关的知识,希望对你有一定的参考价值。
网络基础
Docker Network
单机网络
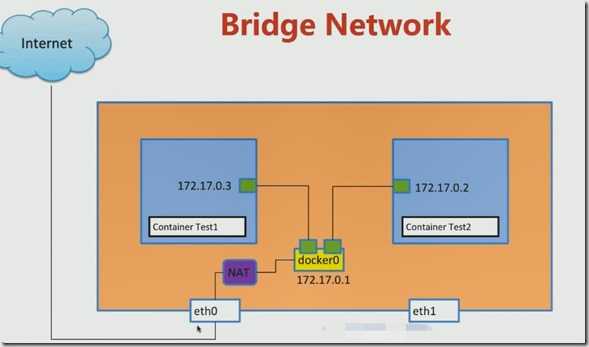
Bridge Network
Host Network
None Network
多机网络:overlay Network
网络的分层
公有IP和私有IP
Public IP:互联网上的唯一标识,可以访问internet
Private IP:不可在互联网上使用,仅供机构内部使用
A类10.0.0.0--10.255.255.255(10.0.0.0/8)
B类172.16.0.0--172.31.255.255(172.16.0.0/12)
C类192.168.0.0--192.168.255.255(192.168.0.0/16)
网络地址转换NAT
Ping和telnet
Ping(ICMP):验证IP的可达性
Linux网络命名空间
Linux Network Namespace

查看当前网络命名空间 [[email protected] vagrant]# ip netns list 添加网络命名空间 [[email protected] vagrant]# ip netns add test1 [[email protected] vagrant]# ip netns add test2 [[email protected] vagrant]# ip netns list test2 test1 [[email protected] vagrant]# sudo ip netns exec test1 ip link 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 [[email protected] vagrant]# sudo ip netns exec test1 ip link set dev lo up [[email protected] vagrant]# sudo ip netns exec test1 ip link 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 [[email protected] vagrant]# ip netns exec test1 ip link 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 [[email protected] vagrant]# sudo ip link set veth-test1 netns test1 [[email protected] vagrant]# ip netns exec test1 ip link 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 6: veth-test1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT qlen 1000 link/ether 36:2d:2a:23:8e:af brd ff:ff:ff:ff:ff:ff
添加了一个test2的网络命名空间 [[email protected] vagrant]# ip netns add test2 绑定到veth-test2的设备 [[email protected] vagrant]# sudo ip link set veth-test2 netns test2 查看命名空间的ip link [[email protected] vagrant]# ip netns exec test2 ip link 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 5: veth-test2: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT qlen 1000 link/ether 2e:00:77:8a:33:57 brd ff:ff:ff:ff:ff:ff 给网络命名空间添加ip并绑定 sudo ip netns exec test1 ip addr add 192.168.1.1/24 dev veth-testl sudo ip netns exec test2 ip addr add 192.168.1.2/24 dev veth-test2 将两个网络命名空间绑定的ip设备启动 sudo ip netns exec test1 ip link set dev veth-testl up sudo ip netns exec test2 ip link set dev veth-test2 up 查看完整的命名空间ip信息 [[email protected] vagrant]# ip netns exec test1 ip a 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 6: veth-testl: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 36:2d:2a:23:8e:af brd ff:ff:ff:ff:ff:ff inet 192.168.1.1/24 scope global veth-testl valid_lft forever preferred_lft forever inet6 fe80::342d:2aff:fe23:8eaf/64 scope link valid_lft forever preferred_lft forever [[email protected] vagrant]# ip netns exec test2 ip a 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 5: veth-test2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 2e:00:77:8a:33:57 brd ff:ff:ff:ff:ff:ff inet 192.168.1.2/24 scope global veth-test2 valid_lft forever preferred_lft forever inet6 fe80::2c00:77ff:fe8a:3357/64 scope link valid_lft forever preferred_lft forever 测试命名空间的 互通性 ping [[email protected] vagrant]# ip netns exec test2 ping 192.168.1.1 PING 192.168.1.1 (192.168.1.1) 56(84) bytes of data. 64 bytes from 192.168.1.1: icmp_seq=1 ttl=64 time=0.050 ms 64 bytes from 192.168.1.1: icmp_seq=2 ttl=64 time=0.110 ms 64 bytes from 192.168.1.1: icmp_seq=3 ttl=64 time=0.202 ms 64 bytes from 192.168.1.1: icmp_seq=4 ttl=64 time=0.052 ms 64 bytes from 192.168.1.1: icmp_seq=5 ttl=64 time=0.040 ms
Docker Bridge0详解
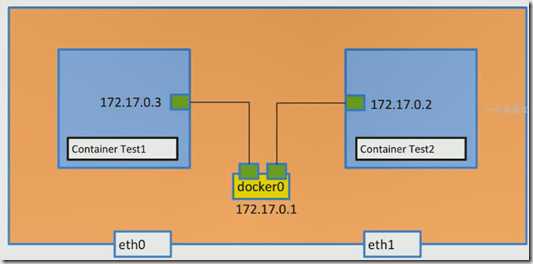
每个容器之间有独立的命名空间(ip),相互之间可以ping 通,
Docker Bridge0 在宿主机上桥接出来的一块命名空间,通常为 172.17.0.2, 里面容器的ip一般在该网段随机分布。除非容器暴露了外面的,否则外面宿主机不能访问
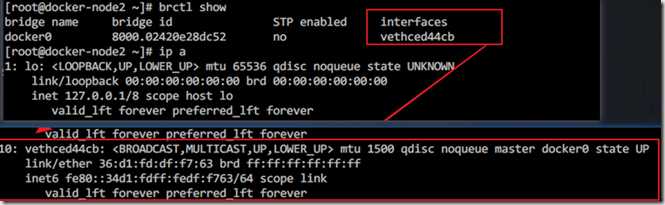
[[email protected] ~]# sudo docker run -d --name test1 busybox /bin/sh -c "while true;do sleep 3600;done" 8f7cbad560db6d4c604395f3ee16c15d6fc4073e3010134e2520aed780b6198d ? [[email protected] ~]# docker exec test1 ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 9: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever ? 查看网桥 brctl show
新创建一个容器,新增了一个命名空间
Bridge Network 网桥
查看网桥
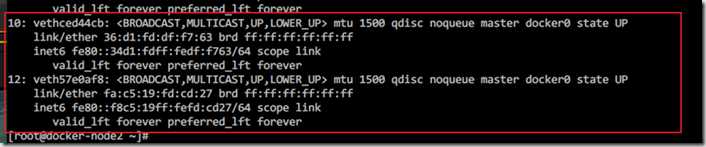
新创建一个容器后,会在网桥上有一个新的接口
通信
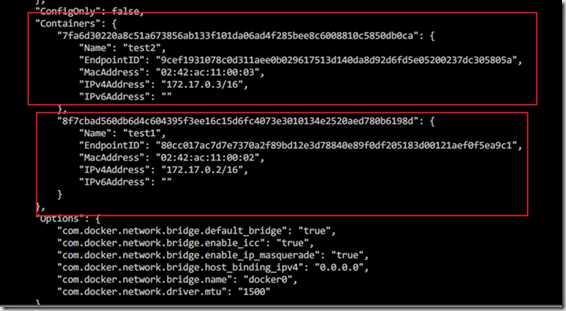
在docker0网桥上面创建的容器关联 ? [vagrantedocker-node1~]# sudo docker run -d --name test2 --link test1 busybox /bin/sh -c "while true;do sleep 3600;done" test2 link test1 容器test2 link 容器test1 2 --> 1 ping 通 1 --> 2 ping 不通 创建网桥 [[email protected] ~]# docker network create -d bridge my-bridge d7b1a39ddd6cd0fff8a7f2ff57a3391e9ac68f8bf09b05460f7d1200c712bc78 [[email protected] ~]# brctl show bridge name bridge id STP enabled interfaces br-d7b1a39ddd6c 8000.0242ed73f4fa no docker0 8000.02420e28dc52 no veth8bb0084 vethced44cb ? ? [[email protected] ~]# docker network ls NETWORK ID NAME DRIVER SCOPE 0e7556320fdd bridge bridge local 0b32df326904 host host local d7b1a39ddd6c my-bridge bridge local e2db49527111 none null local ? ? [[email protected] ~]# sudo docker run -d --name test3 --network my-bridge busybox /bin/sh -c "while true;do sleep 3600;done" 7eb76c6ca9f6123811fc75cae03e571f669b308c2b6bad0cfbdd598508629f0d [[email protected] ~]# brctl show bridge name bridge id STP enabled interfaces br-d7b1a39ddd6c 8000.0242ed73f4fa no vethee72a47 docker0 8000.02420e28dc52 no veth8bb0084 vethced44cb
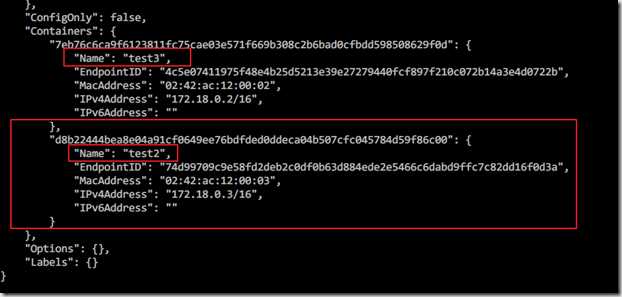
docker network inspect my-bridge
sudo docker run -d --name test3 --network my-bridge busybox /bin/sh -c "while true;do sleep 3600;done"
test2 和 test 3 在同一个网桥my-bridge (自己创建的),可以通过名称ping
docker inspect my-bridge
总结
docker network connect my-bridge test1
tes2和test 1在docker 默认的bridge上
但是互相只能通过ip来ping通
不能通过名字
自己创建的bridge 能够解决互相ip,名字都ping通
以上是关于cp4 Docker 网络1的主要内容,如果未能解决你的问题,请参考以下文章
![346925984[4] 技术分享图片](https://image.cha138.com/20210725/02f3d1e385094c3595f6f9ee25238c0a.jpg)
![347080937[4] 技术分享图片](https://image.cha138.com/20210725/384ee2dbfeba4cd1b2d42cb4438ed282.jpg)
![347249562[4] 技术分享图片](https://image.cha138.com/20210725/4151d8973e8d4a9ca308e372d2f6790c.jpg)
![140035421[4] 技术分享图片](https://image.cha138.com/20210725/4237649faf0d4b618ae258752ce4aeb7.jpg)

![142110968[4] 技术分享图片](https://image.cha138.com/20210725/e483ac578f7c434a93dd7b17b24e10df.jpg)
![5423040e-3b36-473a-9ef5-d7f23716f852[4] 技术分享图片](https://image.cha138.com/20210725/329d2a8a8030451d83b2a999109d6bfe.jpg)
![0e034502-7711-42fa-b4ce-7152314cf51e[4] 技术分享图片](https://image.cha138.com/20210725/baa8c625f28947d7a62bab3779e83793.jpg)
![2dc08891-99ee-4017-b575-32c3cfd26222[4] 技术分享图片](https://image.cha138.com/20210725/df7be3a915cd4bb9862512f19126c382.jpg)