cas客户端流程详解(源码解析)--单点登录
Posted guoxiaoyu
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了cas客户端流程详解(源码解析)--单点登录相关的知识,希望对你有一定的参考价值。
博主之前一直使用了cas客户端进行用户的单点登录操作,决定进行源码分析来看cas的整个流程,以便以后出现了问题还不知道是什么原因导致的
cas主要的形式就是通过过滤器的形式来实现的,来,贴上示例配置:

1 <listener> 2 <listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class> 3 </listener> 4 5 <filter> 6 <filter-name>SSO Logout Filter</filter-name> 7 <filter-class>org.jasig.cas.client.session.SingleSignOutFilter</filter-class> 8 </filter> 9 10 <filter-mapping> 11 <filter-name>SSO Logout Filter</filter-name> 12 <url-pattern>/*</url-pattern> 13 </filter-mapping> 14 15 <!-- SSO单点登录认证filter --> 16 <filter> 17 <filter-name>SSO Authentication Filter</filter-name> 18 <filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class> 19 <init-param> 20 <!-- SSO服务器地址 --> 21 <param-name>SSOServerUrl</param-name> 22 <param-value>http://sso.jxeduyun.com/sso</param-value> 23 </init-param> 24 <init-param> 25 <!-- 统一登录地址 --> 26 <param-name>SSOLoginUrl</param-name> 27 <param-value>http://www.jxeduyun.com/App.ResourceCloud/Src/index.php</param-value> 28 </init-param> 29 <init-param> 30 <!-- 应用服务器地址, 域名或者[http://|https://]{ip}:{port} --> 31 <param-name>serverName</param-name> 32 <param-value>http://127.0.0.1:9000</param-value> 33 </init-param> 34 <init-param> 35 <!-- 除了openId,是否需要返回loginName以及userId等更多信息 --> 36 <param-name>needAttribute</param-name> 37 <param-value>true</param-value> 38 </init-param> 39 <init-param> 40 <!-- 可选,不需要单点登录的页面,多个页面以英文逗号分隔,支持正则表达式形式 --> 41 <!-- 例如:/abc/.*.jsp,/.*/index.jsp --> 42 <param-name>excludedURLs</param-name> 43 <param-value>/site2.jsp</param-value> 44 </init-param> 45 </filter> 46 47 <filter-mapping> 48 <filter-name>SSO Authentication Filter</filter-name> 49 <url-pattern>/TyrzLogin/*</url-pattern> 50 </filter-mapping> 51 52 <!-- SSO ticket验证filter --> 53 <filter> 54 <filter-name>SSO Ticket Validation Filter</filter-name> 55 <filter-class>org.jasig.cas.client.validation.Cas20ProxyReceivingTicketValidationFilter</filter-class> 56 <init-param> 57 <!-- 应用服务器地址, 域名或者[http://|https://]{ip}:{port} --> 58 <param-name>serverName</param-name> 59 <param-value>http://127.0.0.1:9000</param-value> 60 </init-param> 61 <init-param> 62 <!-- 除了openId,是否需要返回loginName以及userId等更多信息 --> 63 <param-name>needAttribute</param-name> 64 <param-value>true</param-value> 65 </init-param> 66 <init-param> 67 <!-- SSO服务器地址前缀,用于生成验证地址,和SSOServerUrl保持一致 --> 68 <param-name>SSOServerUrlPrefix</param-name> 69 <param-value>http://sso.jxeduyun.com/sso</param-value> 70 </init-param> 71 </filter> 72 73 <filter-mapping> 74 <filter-name>SSO Ticket Validation Filter</filter-name> 75 <url-pattern>/*</url-pattern> 76 </filter-mapping>
博主用的不是官方的cas的jar包,是第三方要求的又再次封装的jar包,不过就是属性,获取用户信息的逻辑多了点,其他的还是官方的源码,博主懒 的下载官方的jar在进行一步一步的debug看源码了。
基本配置是添加4个过滤器,请求的时候可以进行拦截进行查看,最后一个是jfinal的开发框架,类似spring,不用管,
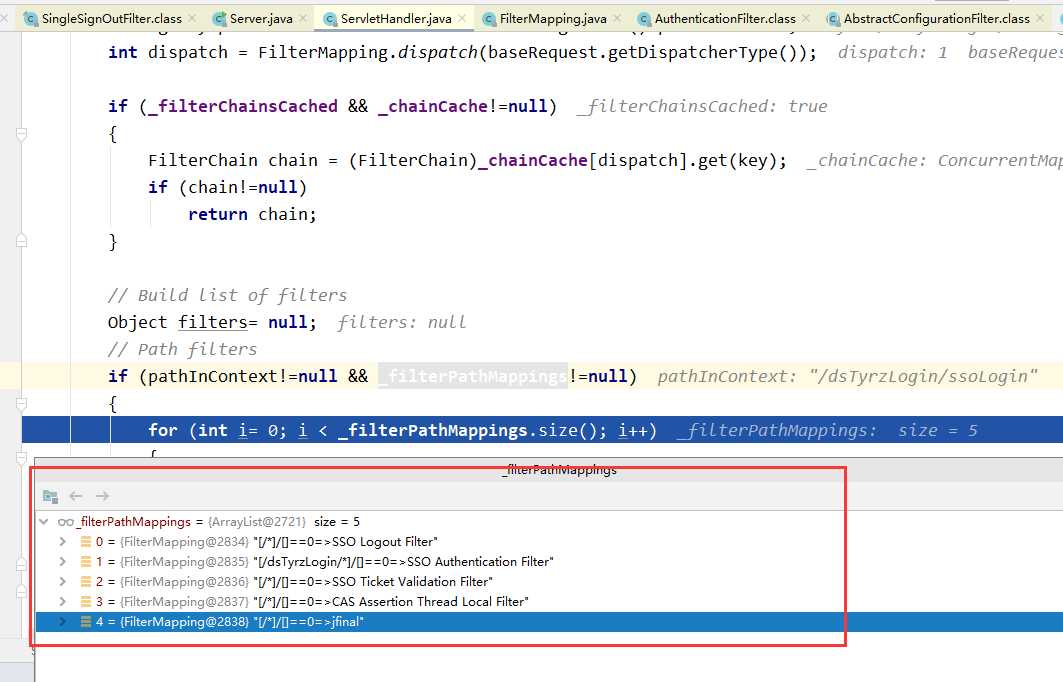
以上是jetty抓到请求时,进行获取过滤的流程,只关注cas的这四个,里面涉及到了缓存过滤器(节点类型存储)
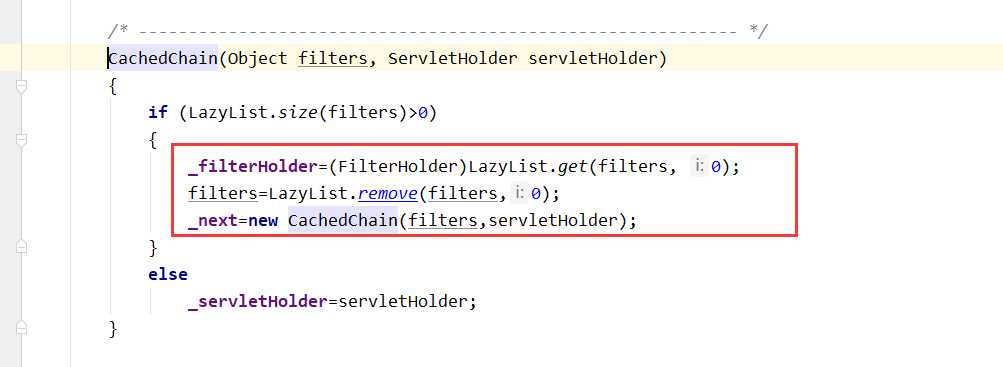
全部进行路径URL匹配完之后,会获取到需要进行执行的过滤器,SSO Logout Filter->SSO Authentication Filter->SSO Ticket Validation Filter->CAS Assertion Thread Local Filter->jfinal->default
那我们就来一个一个看看,每个过滤器都做了哪些事。
SSO Logout Filter,从名字上看,应该是个退出的流程操作。来源吗附上:
1 public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException { 2 HttpServletRequest request = (HttpServletRequest)servletRequest; 3 HttpServletResponse response = (HttpServletResponse)servletResponse; 4 //查看请求中是否带有ticket参数 5 if (!handler.isTokenRequest(request) && !CommonUtils.isNotBlank(request.getParameter("ticket"))) { 6 //如果没有的ticket参数,查看是否是退出请求 7 if (handler.isLogoutRequest(request)) { 8 if (this.sessionMappingStorage != null && !this.sessionMappingStorage.getClass().equals(HashMapBackedSessionMappingStorage.class)) { 9 //是退出请求,直接销毁session,直接return,不会在执行其他过滤器 10 handler.destroySession(request, response); 11 return; 12 } 13 this.log.trace("Ignoring URI " + request.getRequestURI()); 14 } else { 15 handler.recordSession(request); 16 } 17 ///继续执行下一个执行器 18 filterChain.doFilter(servletRequest, servletResponse); 19 }
AuthenticationFilter,该过滤器主要做法:
1 public final void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException { 2 String requestedUrl = ((HttpServletRequest)servletRequest).getServletPath(); 3 boolean isExcludedUrl = false; 4 //这里会获取到xml中的排除需要过滤的URL配置 5 if (this.excludedRequestUrlPatterns != null && this.excludedRequestUrlPatterns.length > 0) { 6 Pattern[] arr$ = this.excludedRequestUrlPatterns; 7 int len$ = arr$.length; 8 9 for(int i$ = 0; i$ < len$; ++i$) { 10 Pattern p = arr$[i$]; 11 if (isExcludedUrl = p.matcher(requestedUrl).matches()) { 12 break; 13 } 14 } 15 } 16 17 HttpServletRequest request = (HttpServletRequest)servletRequest; 18 HttpServletResponse response = (HttpServletResponse)servletResponse; 19 //如果当前URL是被排除,不需要校验cas单点登录的话,直接跳过当前过滤器,进行下一步 20 if (this.isIgnoreSSO() && isExcludedUrl) { 21 filterChain.doFilter(request, response); 22 } else { 23 //如果当前不被排除在外,查看白名单URL,也可以直接跳过该过滤器 24 boolean isWhiteUrl = false; 25 if (this.whiteRequestUrlPatterns != null && this.whiteRequestUrlPatterns.length > 0) { 26 Pattern[] arr$ = this.whiteRequestUrlPatterns; 27 int len$ = arr$.length; 28 29 for(int i$ = 0; i$ < len$; ++i$) { 30 Pattern p = arr$[i$]; 31 if (isWhiteUrl = p.matcher(requestedUrl).matches()) { 32 break; 33 } 34 } 35 } 36 37 if (isWhiteUrl) { 38 filterChain.doFilter(request, response); 39 } else { 40 //如果都没匹配上,说明该URL是需要进行校验查看的 41 HttpSession session = request.getSession(false); 42 //从session中取出改属性值,查看当前session是否已经认证过了。如果认证过了了,可以跳过该过滤器 43 Assertion assertion = session != null ? (Assertion)session.getAttribute("_const_cas_assertion_") : null; 44 //第一次请求的时候,改对象一定为null,因为没人登录过 45 if (assertion != null) { 46 filterChain.doFilter(request, response); 47 } else { 48 String serviceUrl = this.constructServiceUrl(request, response); 49 String ticket = CommonUtils.safeGetParameter(request, this.getArtifactParameterName()); 50 //查看是否session中有_const_cas_gateway_该属性值,第一次登录也没有 51 boolean wasGatewayed = this.gatewayStorage.hasGatewayedAlready(request, serviceUrl); 52 //如果都没有 53 if (!CommonUtils.isNotBlank(ticket) && !wasGatewayed) { 54 String encodedService; 55 //查看是否是cas服务器return回调我们的这个接口请求,该属性值在下面,也就是第一次登录的时候,设置的 56 if (request.getSession().getAttribute("casreturn") != null) { 57 request.getSession().removeAttribute("casreturn"); 58 if (isExcludedUrl) { 59 filterChain.doFilter(request, response); 60 } else { 61 encodedService = Base64.encodeBase64String(serviceUrl.getBytes()); 62 encodedService = encodedService.replaceAll("[\\s* ]", ""); 63 if (!this.SSOLoginUrl.startsWith("https://") && !this.SSOLoginUrl.startsWith("http://")) { 64 this.SSOLoginUrl = this.getServerName() + (this.getServerName().endsWith("/") ? "" : "/") + this.SSOLoginUrl; 65 } 66 //-------------@这里---------------------- 67 //一直以为是所有校验都没有参数后,在下面才是跳转到登录页,,没想到,直接回调了,并没有让用户去登陆,而是在这里才去调用登录页 68 //让用户去登陆。大坑 69 response.sendRedirect(CommonUtils.joinUrl(this.SSOLoginUrl, "nextpage=" + encodedService)); 70 } 71 } else { 72 //第一次登录的时候是这里,他会将你xml中的cas服务器地址拼接成login登录地址,我们当前请求的URL编码之后,会被cas登录成功后回调使用 73 encodedService = this.SSOServerUrl + "/login?service=" + URLEncoder.encode(serviceUrl, "UTF-8") + "&redirect=true"; 74 //并且设置cas服务器回调标识 75 request.getSession().setAttribute("casreturn", true); 76 //第一次登录的时候,只能到这里了,因为ticket参数,或则session中_const_cas_assertion_属性都没有,只能去cas服务器请求登录, 77 //这里有个坑,,没想到在这里没有直接出现登录页,而是调用cas服务器地址后,直接返回来了,而且会在@那里再去调用登录地址 78 response.sendRedirect(encodedService); 79 //其他的事情后续就不要再debug了,已经跟我们cas没有啥关系了,博主,debug了半天越看越懵,才发现是服务在做其他的事情, 80 // 我们的登录页面早就已经出现了 81 } 82 } else { 83 filterChain.doFilter(request, response); 84 } 85 } 86 } 87 } 88 }
上面的还有一个坑,就是,在用户登录成功后,回调我们的地址,第一次并不会带给我们ticket参数,而且还会走
ncodedService = this.SSOServerUrl + "/login?service=" + URLEncoder.encode(serviceUrl, "UTF-8") + "&redirect=true";
这个逻辑,并且附上casreturn属性,然后,cas服务器这回才会把ticket参数返回给我们的接口,剩下的就是下一个过滤器的事情了,慢慢来:
好了,这次有ticket了,我们来看下一个过滤器SSO Ticket Validation Filter
1 public final void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException { 2 //这里做了点事,是否为代理,博主没用这个,默认代理为null,返回true 3 if (this.preFilter(servletRequest, servletResponse, filterChain)) { 4 HttpServletRequest request = (HttpServletRequest)servletRequest; 5 HttpServletResponse response = (HttpServletResponse)servletResponse; 6 //获取ticket请求参数 7 String ticket = CommonUtils.safeGetParameter(request, this.getArtifactParameterName()); 8 //到这里了,分为三种情况, 9 //有ticket,因为你已经登录了,cas服务器登录成功返回给你了,接下来进行校验 10 //无ticket,可能你没有配置第一个过滤器,溜进来了 11 //无ticket,ticket已经校验成功后跳转回来了,用户属性已经设置到session中了,所以这次请求没有ticket了,不用去校验 12 if (CommonUtils.isNotBlank(ticket)) { 13 if (this.log.isDebugEnabled()) { 14 this.log.debug("Attempting to validate ticket: " + ticket); 15 } 16 17 try { 18 //开始ticket票据校验,这才是这个ticket过滤器真正要做的 19 //constructServiceUrl这个方法不用管,就是拼接一下URL路径,把我的APPID啥的拼接上去 20 //validate做了挺多事,请看下一个类注释,这里先过去(大概逻辑就是去cas服务器验证ticket) 21 Assertion assertion = this.ticketValidator.validate(ticket, this.constructServiceUrl(request, response)); 22 if (this.log.isDebugEnabled()) { 23 this.log.debug("Successfully authenticated user: " + assertion.getPrincipal().getName()); 24 } 25 //看到这里没有,就是在第一个过滤器进行校验的参数,如果ticket验证成功,就会往request,及session设置属性,该属性就是_const_cas_assertion_ 26 //该属性值则是一个用户信息map 27 request.setAttribute("_const_cas_assertion_", assertion); 28 if (this.useSession) { 29 request.getSession().setAttribute("_const_cas_assertion_", assertion); 30 } 31 //空方法,不用管 32 this.onSuccessfulValidation(request, response, assertion); 33 //ticket验证成功后,在进行跳转,这次是跳到我们自己的请求地址 34 if (this.redirectAfterValidation) { 35 this.log.debug("Redirecting after successful ticket validation."); 36 response.sendRedirect(this.constructServiceUrl(request, response)); 37 return; 38 } 39 } catch (TicketValidationException var8) { 40 response.setStatus(403); 41 this.log.warn(var8, var8); 42 this.onFailedValidation(request, response); 43 if (this.exceptionOnValidationFailure) { 44 throw new ServletException(var8); 45 } 46 47 return; 48 } 49 } 50 51 filterChain.doFilter(request, response); 52 } 53 }
里面的ticket验证逻辑在此:
1 public Assertion validate(String ticket, String service) throws TicketValidationException { 2 //此处是拼接好要调用的URL 3 //http://sso.jxeduyun.com/sso/,该路径是在web.xml中改ticket过滤器进行配置的SSOServerUrlPrefix 4 //http://sso.jxeduyun.com/sso/serviceValidate?needAttribute=true&ticket=ST-28699-qdyblKpRwc5LpLk57dRM-sso.jxeduyun.com&service=http%3A%2F%2F127.0.0.1%3A9000%2Fdsideal_yy%2FdsTyrzLogin%2FssoLogin%3FloginType%3Dweb%26from%3Dew%26appId%3D00000&appKey=00000 5 String validationUrl = this.constructValidationUrl(ticket, service); 6 if (this.log.isDebugEnabled()) { 7 this.log.debug("Constructing validation url: " + validationUrl); 8 } 9 10 try { 11 this.log.debug("Retrieving response from server."); 12 //这里不用看,就是发起请求调用上面的接口,查看ticket有效性 13 String serverResponse = this.retrieveResponseFromServer(new URL(validationUrl), ticket); 14 if (serverResponse == null) { 15 throw new TicketValidationException("The CAS server returned no response."); 16 } else { 17 if (this.log.isDebugEnabled()) { 18 this.log.debug("Server response: " + serverResponse); 19 } 20 //这个不用看了,就是解析返回的cas数据,然后获取里面的用户信息,并封装成map 21 return this.parseResponseFromServer(serverResponse); 22 } 23 } catch (MalformedURLException var5) { 24 throw new TicketValidationException(var5); 25 } 26 }
因为ticket验证成功后并没有直接到下一个过滤器,而是从新请求了一次,这次不会有ticket参数了,因为session中已经有属性了,就在前几个过滤器中进行判断,在都走一次,然后才会到下面这个过滤器
1 public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException { 2 HttpServletRequest request = (HttpServletRequest)servletRequest; 3 HttpSession session = request.getSession(false); 4 Assertion assertion = (Assertion)((Assertion)(session == null ? request.getAttribute("_const_cas_assertion_") : session.getAttribute("_const_cas_assertion_"))); 5 6 try { 7 //该过滤器的作用就是,把用户对象从session中拿出来,放到AssertionHolder里面,从而在代码中获取对象信息的时候, 8 //直接调用该对象即可 9 AssertionHolder.setAssertion(assertion); 10 filterChain.doFilter(servletRequest, servletResponse); 11 } finally { 12 AssertionHolder.clear(); 13 } 14 15 }
至此,cas的登录流程全部走完,不知道大家看懂多少,花了博主大概一天的时间才把源码理解通,ticket返回示例给大家一下,还有代码调用:
1 失败示例: 2 <cas:serviceResponse xmlns:cas=‘http://www.yale.edu/tp/cas‘> 3 <cas:authenticationFailure code=‘INVALID_TICKET‘> 4 ticket 'ST-28699-qdyblKpRwc5LpLk57dRM-sso.jxeduyun.com' not recognized 5 </cas:authenticationFailure> 6 </cas:serviceResponse> 7 成功示例: 8 <cas:serviceResponse xmlns:cas=‘http://www.yale.edu/tp/cas‘> 9 <cas:authenticationSuccess> 10 <cas:user>test</cas:user> 11 <cas:attributes> 12 <cas:multipleId>test-test-test-test-test</cas:multipleId> 13 14 <cas:userId>test</cas:userId> 15 16 <cas:loginName>test</cas:loginName> 17 18 </cas:attributes> 19 </cas:authenticationSuccess> 20 </cas:serviceResponse>
代码调用示例:
1 Assertion assertion = AssertionHolder.getAssertion(); 2 String openId = assertion.getPrincipal().getName(); 3 Map<String, Object> attributes = assertion.getPrincipal().getAttributes(); 4 String userId = attributes.get("userId").toString(); 5 String loginName = attributes.get("loginName").toString(); 6 System.out.println("openId:"+openId); 7 System.out.println("userId:"+userId); 8 System.out.println("loginName:"+loginName);
原创不易,转载请说明出处!谢谢
--------------------------------------------------------------------------------

以上是关于cas客户端流程详解(源码解析)--单点登录的主要内容,如果未能解决你的问题,请参考以下文章
