centos部署ipsec *** nat穿越
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了centos部署ipsec *** nat穿越相关的知识,希望对你有一定的参考价值。
***(virtual private network,虚拟专用网)就是在两个网络实体之间建立的一种受保护的连接,这两个实体可以通过点到点的链路直接相连,但通常情况下他们会相隔较远的距离。***方式有三种:
Site-to-Site(站点到站点或者网关到网关):如3个机构分布在互联网的3个不同的地方,各使用一个ipsec ***网关相互建立***隧道,企业内网(若干PC)之间的数据通过这些网关建立的IPSec隧道实现安全互联。
End-to-End(端到端或者PC到PC): 两个PC之间的通信由两个PC之间的IPSec会话保护,而不是网关。
End-to-Site(端到站点或者PC到网关):两个PC之间的通信由网关和异地PC之间的IPSec进行保护。
本次讲述第一种方式Site-to-Site(站点到站点或者网关到网关)
1、需求分析
PC1部署Ipsec ***,配置私网地址,在无线路由器做NAT;
华为USG做总部的***服务器;
因考虑PC1访问互联网需要通过无线路由器做nat,所ipsec ***要考虑到nat穿越,后面openswan会有相关配置;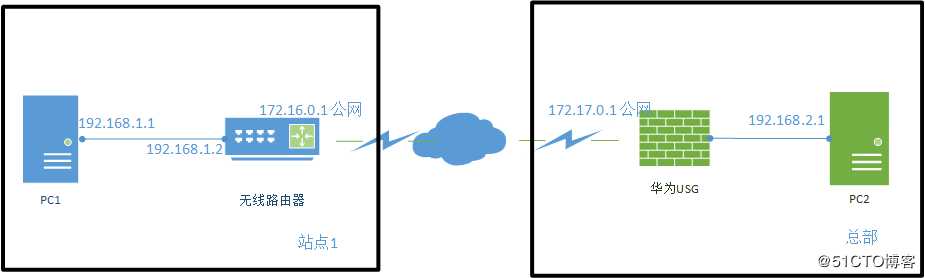
2、安装openswan
pc1部署centos7操作系统,在linux上部署openswan
yum install -y openswan lsof
我们改动内核参数,允许IP转发、永久性禁止重定向。
sed -i ‘s#net.ipv4.ip_forward = 0#net.ipv4.ip_forward = 1#g‘ /etc/sysctl.conf
sed -i ‘s#net.ipv4.conf.default.rp_filter = 1#net.ipv4.conf.default.rp_filter = 0#g‘ /etc/sysctl.conf查看内核参数,确保禁止重定向sysctl -a | egrep "ipv4.*(accept|send)_redirects"
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.lo.accept_redirects = 0
net.ipv4.conf.lo.send_redirects = 0
net.ipv4.conf.eth0.accept_redirects = 0
net.ipv4.conf.eth0.send_redirects = 0重新装入/etc/sysctl.confsysctl -p
3、修改ipsec配置文件
vi /etc/ipsec.conf
config setup
plutodebug=all
plutostderrlog=/var/log/ipsec.log
# Debug-logging controls: "none" for (almost) none, "all" for lots.
# klipsdebug=none
# plutodebug="control parsing"
# For Red Hat Enterprise Linux and Fedora, leave protostack=netkey
protostack=netkey
nat_traversal=yes
#实现nat穿越
virtual_private=
oe=off
# Enable this if you see "failed to find any available worker"
# nhelpers=04、修改lan-to-lan的配置文件
[root@localhost ~]# cat /etc/ipsec.d/site1-tosite2.conf
conn site1-tosite2
type=tunnel
#隧道模式
authby=secret
#共享秘钥方式
auto=start
ike=3des-sha1;modp1024
keyexchange=ike
phase2=esp
phase2alg=3des-sha1
pfs=no
left=%defaultroute
leftid=alice
leftnexthop=%defaultroute
leftsubnet=192.168.1.0/24
right=172.17.0.1
rightsubnet=192.168.2.0/24 5、配置ipsec ***共享秘钥
vi /etc/ipsec.d/idcsubnet1-to-awsvpc1.secrets本端公网地址 对端公网地址: PSK "123456"
6、检查命令
设置开机启动 ,命令#chkconfig ipsec on
命令 #ipsec verify ,没有fail项即可
[root@localhost ~]# ipsec verify
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 3.25 (netkey) on 3.10.0-1062.9.1.el7.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Two or more interfaces found, checking IP forwarding [OK]
Checking rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/all/rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/ens33/rp_filter [ENABLED]
rp_filter is not fully aware of IPsec and should be disabled
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking ‘ip‘ command [OK]
Checking ‘iptables‘ command [OK]
Checking ‘prelink‘ command does not interfere with FIPS [OK]
Checking for obsolete ipsec.conf options [OBSOLETE KEYWORD]
Warning: ignored obsolete keyword ‘nat_traversal‘
ipsec verify: encountered 5 errors - see ‘man ipsec_verify‘ for help命令 #service ipsec status ,检查进程状态,tunnel up数量
命令 #ip xfrm policy ,检查tunnel的详细信息,源/目的subnet、下一跳等
以上是关于centos部署ipsec *** nat穿越的主要内容,如果未能解决你的问题,请参考以下文章