Log Parser Lizard 日志分析
Posted didiaoxiaofei
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Log Parser Lizard 日志分析相关的知识,希望对你有一定的参考价值。
1. Log Parser Lizard 介绍
Log Parser Lizard是一款强大好用的日志分析工具,使用这款软件可以方便用户对服务器日志、网站日志等进行直观用户的分析,支持基于文本的日志文件、XML 文件、CSV(逗号分隔符)文件以及注册表、文件系统等内容。
2. Windows日志分析
1.统计登陆成功的
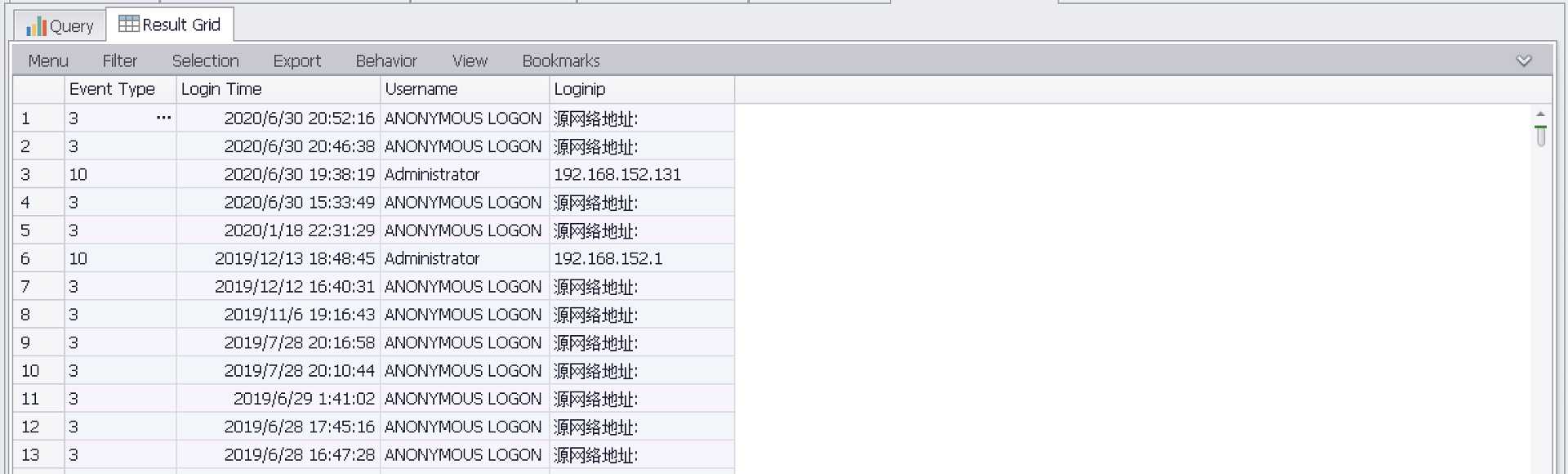
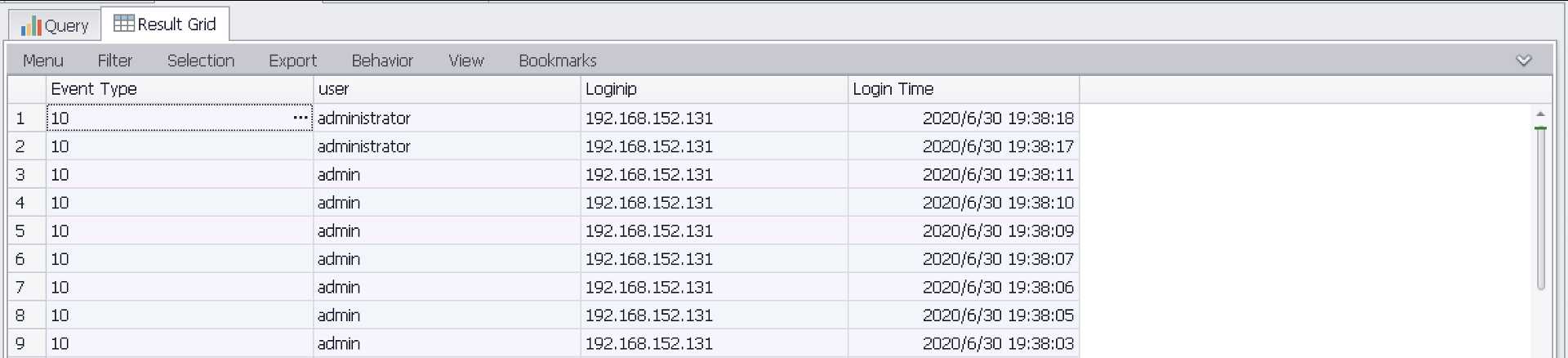
统计登陆成功状态为(3/10)用户
SELECT EXTRACT_TOKEN(Message,13,‘ ‘) as EventType,TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,‘|‘) as Username,EXTRACT_TOKEN(Message,38,‘ ‘) as Loginip FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=4624 and (EXTRACT_TOKEN(Message,13,‘ ‘) = ‘3‘ or EXTRACT_TOKEN(Message,13,‘ ‘) = ‘10‘)
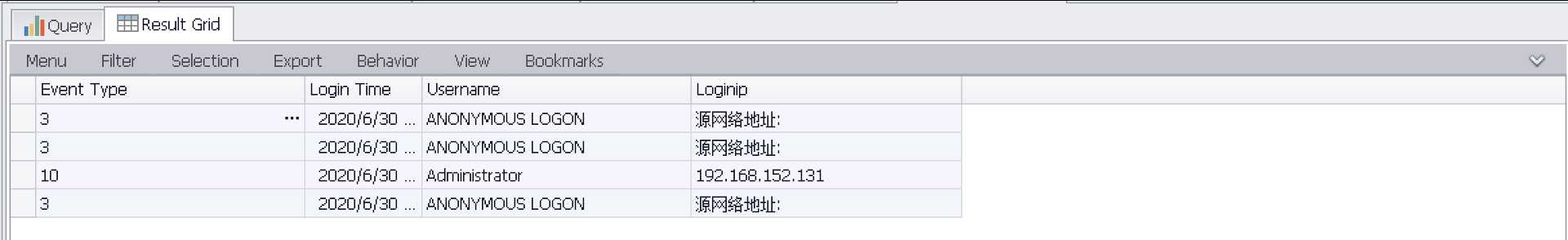
统计时间在06-20到06-30登陆成功状态为(3/10)用户
SELECT EXTRACT_TOKEN(Message,13,‘ ‘) as EventType,TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,‘|‘) as Username,EXTRACT_TOKEN(Message,38,‘ ‘) as Loginip FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where TimeGenerated>‘2020-06-20 23:32:11‘ and TimeGenerated<‘2020-06-30 23:34:00‘ and EventID=4624 and (EXTRACT_TOKEN(Message,13,‘ ‘) = ‘3‘ or EXTRACT_TOKEN(Message,13,‘ ‘) = ‘10‘)
- 统计登陆失败的
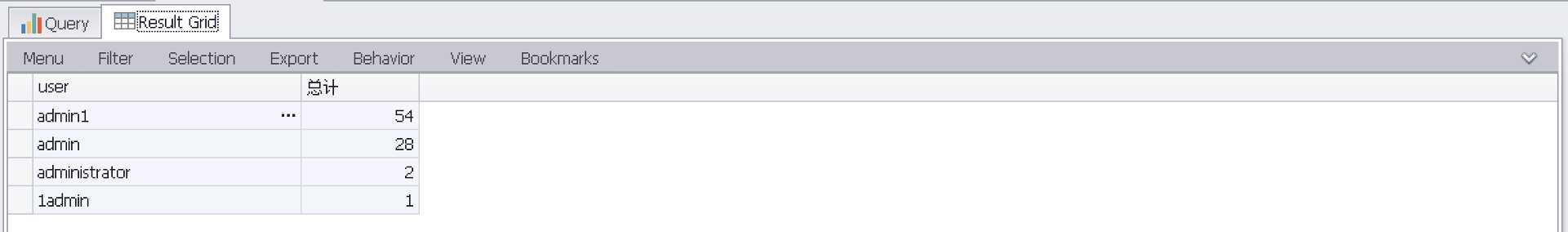
按用户名统计爆破次数(聚合)
select EXTRACT_TOKEN(Message,19,‘ ‘) as user,count(EXTRACT_TOKEN(Message,19,‘ ‘)) AS 总计 FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=4625 GROUP by EXTRACT_TOKEN(Message,19,‘ ‘) ORDER by 总计 desc
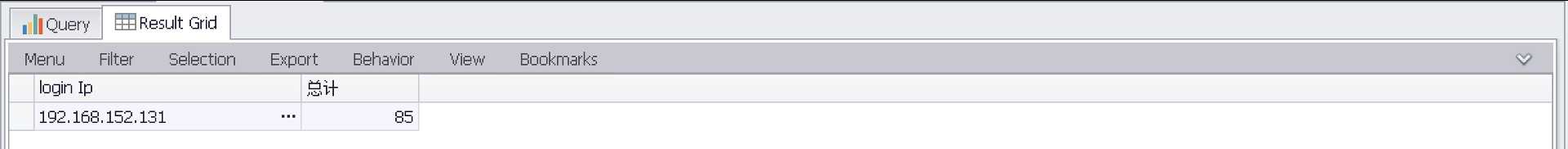
按IP地址统计爆破次数(聚合)
select EXTRACT_TOKEN(Message,39,‘ ‘) as loginIp,count(EXTRACT_TOKEN(Message,39,‘ ‘)) AS 总计 FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=4625 GROUP by EXTRACT_TOKEN(Message,39,‘ ‘) ORDER by 总计 desc
提取登录失败用户名并显示登陆失败时间
SELECT EXTRACT_TOKEN(Message,13,‘ ‘) as EventType,EXTRACT_TOKEN(Message,19,‘ ‘) as user,EXTRACT_TOKEN(Message,39,‘ ‘) as Loginip,TimeGenerated as LoginTime FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=4625
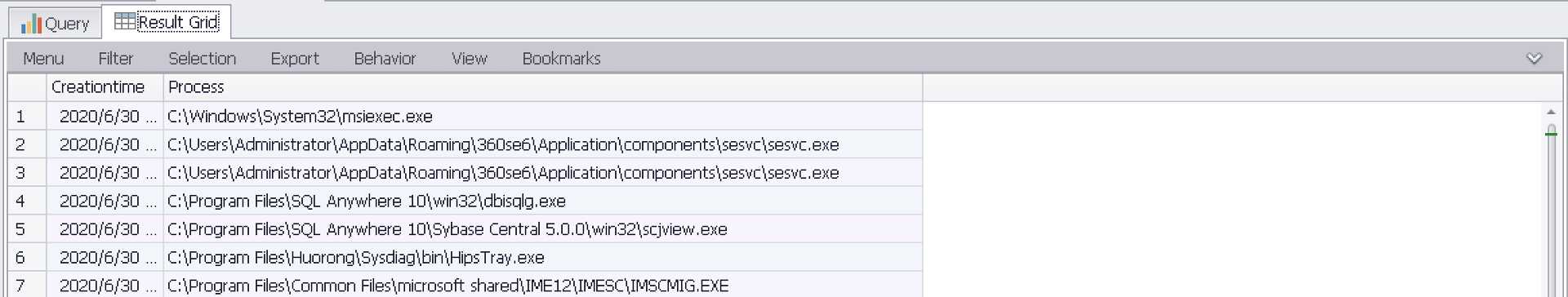
- 查询 [Administrator] 创建的进程
SELECT TimeGenerated as Creationtime,EXTRACT_TOKEN(Strings,5,‘|‘) as Process FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=4688 and Message LIKE ‘%Administrator%‘
- 查询创建的服务
SELECT TimeGenerated as Creationtime,Message FROM ‘C:Program FilesLog Parser 2.2Security-01.evtx‘ where EventID=7045
- 查询重置密码
SELECT TimeGenerated as Creationtime,Message FROM Security.evtx where EventID=4724
- 查询重置密码
SELECT TimeGenerated as Creationtime,Message FROM Security.evtx where EventID=4724
- 查询用户已添加到特权本地组
SELECT TimeGenerated as Creationtime,Message FROM Security.evtx where EventID=4732
- 终端会话日志
终端会话日志-RDP断开连接:
SELECT TimeGenerated as LoginTime,Strings FROM Operational.evtx where EventID=24
终端会话日志-RDP重连:
SELECT TimeGenerated as LoginTime,Strings FROM Operational.evtx where EventID=25
终端会话日志-RDP登陆:
SELECT TimeGenerated as LoginTime,Strings FROM Operational.evtx where EventID=21
以上是关于Log Parser Lizard 日志分析的主要内容,如果未能解决你的问题,请参考以下文章