wireshark 指令模式 => tshark
Windows 及Linux 可至安裝目錄執行>tshark
tshark.exe -i 7(利用-D找要的介面代號)
輸出json版本需要2.2以上,Centos需要原碼安裝
ubuntu===============================================================
sudo apt-add-repository ppa:wireshark-dev/stable
sudo apt-get update
sudo apt-get install wireshark
sudo dpkg-reconfigure wireshark-common
Centos7===============================================================
SUDO YUM INSTALL BISON FLEX GTK3-DEVEL QT-DEVEL GCC-C++ LIBPCAP-DEVEL C-ARES-DEVEL LIBSMI-DEVEL GNUTLS-DEVEL LIBGCRYPT-DEVEL KRB5-DEVEL GEOIP-DEVEL ORTP-DEVEL PORTAUDIO-DEVEL AUTOMAKE AUTOCONF LIBTOOL
TAR XF WIRESHARK*
CD /WIRESHARK*
./AUTOGEN.SH
./CONFIGURE –ENABLE-SETCAP-INSTALL
MAKE
SUDO MAKE INSTALL
===============================================================
tshark command
TShark (Wireshark) 2.2.4 (v2.2.4-0-gcc3dc1b)
Dump and analyze network traffic.
See https://www.wireshark.org for more information.
Usage: tshark [options] …
Capture interface:
-i name or idx of interface (def: first non-loopback) #擷取介面 ex. -i ens160
-f packet filter in libpcap filter syntax #wireshark的capture 相同,可直接參考string指令
-s packet snapshot length (def: 65535)
-p don’t capture in promiscuous mode
-I capture in monitor mode, if available
-B size of kernel buffer (def: 2MB)
-y link layer type (def: first appropriate)
-D print list of interfaces and exit
-L print list of link-layer types of iface and exit
Capture stop conditions:
-c stop after n packets (def: infinite) #ex.-c 10 抓十個包
-a … duration:NUM – stop after NUM seconds
filesize:NUM – stop this file after NUM KB
files:NUM – stop after NUM files
Capture output:
-b … duration:NUM – switch to next file after NUM secs
filesize:NUM – switch to next file after NUM KB
files:NUM – ringbuffer: replace after NUM files
RPCAP options:
-A : use RPCAP password authentication
Input file:
-r set the filename to read from (- to read from stdin) #讀pcap檔
Processing:
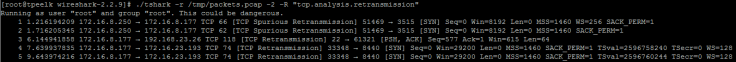
-2 perform a two-pass analysis #參考下面例子
-R packet Read filter in Wireshark display filter syntax#與wireshark Filter功能相同,與其他分析結合需要加-2
EX:查RTO的封包: ./tshark -r /tmp/packets.pcap -2 -R “tcp.analysis.retransmission"
-Y packet displaY filter in Wireshark display filter
syntax #與-R相同功能更強大?
-n disable all name resolutions (def: all enabled)
-N enable specific name resolution(s): “mnNtCd"
-d ==, …
“Decode As", see the man page for details
Example: tcp.port==8888,http
-H read a list of entries from a hosts file, which will
then be written to a capture file. (Implies -W n)
–disable-protocol disable dissection of proto_name
–enable-heuristic
enable dissection of heuristic protocol
–disable-heuristic
disable dissection of heuristic protocol
Output:
-w <outfile|-> write packets to a pcap-format file named “outfile" #存檔成pcap,相關-T
(or to the standard output for “-“)
-C start with specified configuration profile
-F set the output file type, default is pcapng
an empty “-F" option will list the file types
-V add output of packet tree (Packet Details) #顯示封包樹狀詳細內容
-O Only show packet details of these protocols, comma
separated
-P print packet summary even when writing to a file
-S the line separator to print between packets
-x add output of hex and ASCII dump (Packet Bytes)
-T pdml|ps|psml|json|ek|text|fields #存檔成其他格式,相關-w
format of text output (def: text)
-j protocols layers filter if -T ek|pdml|json selected,
(e.g. “http tcp ip",
-e field to print if -Tfields selected (e.g. tcp.port,
_ws.col.Info)
this option can be repeated to print multiple fields
-E= set options for output when -Tfields selected:
bom=y|n print a UTF-8 BOM
header=y|n switch headers on and off
separator=/t|/s| select tab, space, printable character as separator
occurrence=f|l|a print first, last or all occurrences of each field
aggregator=,|/s| select comma, space, printable character as
aggregator
quote=d|s|n select double, single, no quotes for values
-t a|ad|d|dd|e|r|u|ud output format of time stamps (def: r: rel. to first) #轉時間格式 EX: ad是 2017-09-05 14:28:08
-u s|hms output format of seconds (def: s: seconds)
-l flush standard output after each packet
-q be more quiet on stdout (e.g. when using statistics) #配合-z 可只顯示分析結果
-Q only log true errors to stderr (quieter than -q)
-g enable group read access on the output file(s)
-W n Save extra information in the file, if supported.
n = write network address resolution information
-X : eXtension options, see the man page for details
-U tap_name PDUs export mode, see the man page for details
-z various statistics, see the man page for details #使用內建的統計分析
EX統計IP: -z conv,ip
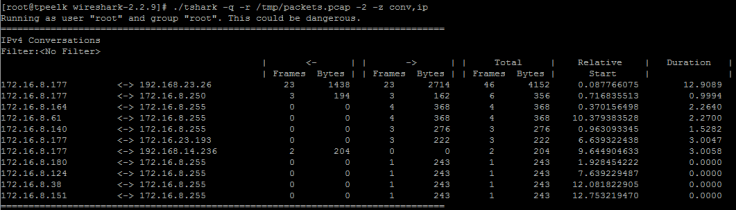
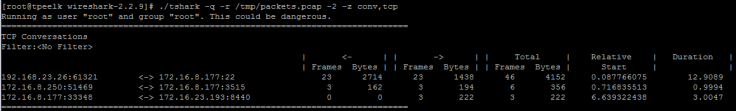
EX2統計tcp Conversations status: -z conv,tcp
–capture-comment
add a capture comment to the newly created
output file (only for pcapng)
Miscellaneous:
-h display this help and exit
-v display version info and exit
-o : … override preference setting
-K keytab file to use for kerberos decryption
-G [report] dump one of several available reports and exit
default report="fields"
use “-G ?" for more help