24-思科防火墙:ASA透明防火墙实验
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了24-思科防火墙:ASA透明防火墙实验相关的知识,希望对你有一定的参考价值。
一、实验拓扑: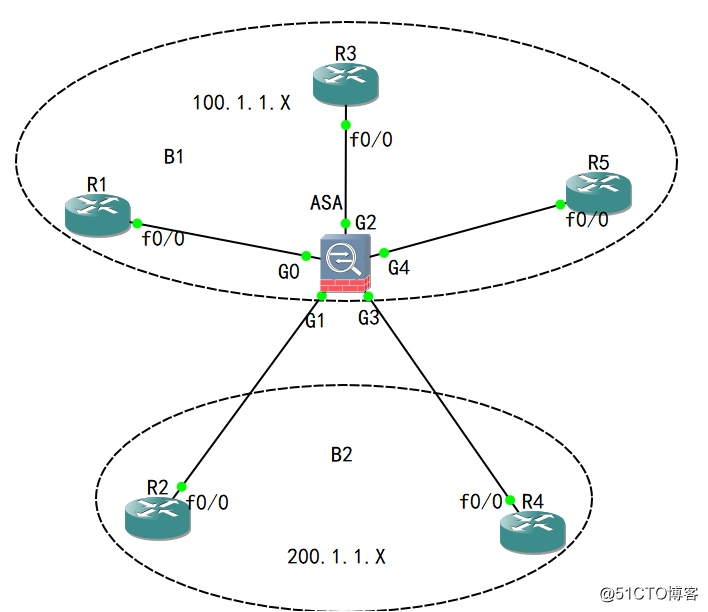
二、实验要求:
1、show mode:单模式;show firewall:路由模式——>firewall transparent;ASA清除所有配置;
切换透明模式是不需要重启的;透明模式的ASA是二层设备,所以这里的接口不能在配IP地址了,按Tab键也没有效果的;
2、要配置一个管理IP地址,其实所谓的管理IP地址就是桥的主IP;配置:interface bvi 1,并配置IP地址:100.1.1.100,组是可以配IP地址的;
3、因为有2个组,所以网管IP必须是有2个,增加B2组管理组bvi 2,IP地址:200.1.1.200;show int ip bri只能看到组的IP地址,那么其它接口怎么才能和组绑定在一起呢?
4、进入接口G0,定义名字:nameif B1.outside(定义为B1组里的Outside),定义安全级别:security-level 0,定义所属哪个组:bridge group 1;no shutdown;
G2:dmz,50,bridge group 1,no shutdown;G4:inside,100,bridge group 100,no shutdown;
绑定好以后再去show int ip bri,就会有相应的接口地址显示;
5、同理:G1、G3对应B2的outside、inside;show ip int bri验证
6、测试:ASA分别去Ping 各个路由器应该可以通了。R5 Telnt R1也可以做到;R1 Telnet R5因为是Inbound流量,所以不通;ARP默认是可以穿越ASA的,所以R1可以获得R5接口的地址,但是不通,原因是三层流量不通的;
7、采用ACL抓取并放行R1到R5的Telnet流量;测试R1登录R5?
8、如遇到ASA只显示4个接口,建议重启ASA、GNS3;或者添加6个VM网卡,再重启。
三、命令部署:
1、R1、R2、R3、R4、R5基本配置:
R1(config)#int f0/0
R1(config-if)#no shutdown
R1(config-if)#ip add 100.1.1.1 255.255.255.0
R1(config)#username aa password aa
R1(config)#line vty 0 4
R1(config-line)#login local
R2(config)#int f0/0
R2(config-if)#no shutdown
R2(config-if)#ip add 200.1.1.2 255.255.255.0
R3(config)#int f0/0
R3(config-if)#no shutdown
R3(config-if)#ip add 100.1.1.3 255.255.255.0
R3(config)#username aa password aa
R3(config)#line vty 0 4
R3(config-line)#login local
R4(config)#int f0/0
R4(config-if)#no shutdown
R4(config-if)#ip add 200.1.1.4 255.255.255.0
R5(config)#int f0/0
R5(config-if)#no shutdown
R5(config-if)#ip add 100.1.1.5 255.255.255.0
R5(config)#username aa password aa
R5(config)#line vty 0 4
R5(config-line)#login local
2、ASA查看模式、防火墙、清除所有配置,修改防火墙模式:
ASA# show mode
Security context mode: single
ASA# show firewall
Firewall mode: Router
ASA(config)# clear configure all
ciscoasa(config)# firewall transparent
验证:
ciscoasa(config)# show firewall
Firewall mode: Transparent
ciscoasa(config)# show int ip bri
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 unassigned YES unset administratively down up
GigabitEthernet1 unassigned YES unset administratively down up
GigabitEthernet2 unassigned YES unset administratively down up
GigabitEthernet3 unassigned YES unset administratively down up
3、配置2个管理组,2个管理IP地址:
ciscoasa(config)# interface bvi 1 //bvi:Bridge Virtual Interface 网桥虚拟接口
ciscoasa(config-if)# ip add 100.1.1.100 255.255.255.0
ciscoasa(config)# interface bvi 2
ciscoasa(config-if)# ip add 200.1.1.200 255.255.255.0
4、将G0、G2、G4接口分别定义为Outside、DMZ、Inside,绑定管理组,定义安全级别:
ciscoasa(config)# int g0
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# nameif B1.outside
ciscoasa(config-if)# security-level 0
ciscoasa(config-if)# bridge-group 1
ciscoasa(config)# int g2
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# nameif B1.dmz
ciscoasa(config-if)# security-level 50
ciscoasa(config-if)# bridge-group 1
ciscoasa(config)# int g4
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# nameif B1.inside
ciscoasa(config-if)# security-level 100
ciscoasa(config-if)# bridge-group 1
ciscoasa(config)# int g1
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# nameif B2.outside
ciscoasa(config-if)# security-level 0
ciscoasa(config-if)# bridge-group 2
ciscoasa(config)# int g3
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# nameif B2.inside
ciscoasa(config-if)# security-level 100
ciscoasa(config-if)# bridge-group 2
验证:
ciscoasa(config)# show int ip bri
Interface IP-Address OK? Method Status Protocol
BVI1 100.1.1.100 YES unset up up
BVI2 200.1.1.200 YES unset up up
GigabitEthernet0 100.1.1.100 YES unset up up
GigabitEthernet1 200.1.1.200 YES unset up up
GigabitEthernet2 100.1.1.100 YES unset up up
GigabitEthernet3 200.1.1.200 YES unset up up
GigabitEthernet4 100.1.1.100 YES unset up up
5、ASA PingR1~R5路由器都可以通:
ciscoasa# ping 100.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.1.1.1, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
ciscoasa# ping 100.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.1.1.3, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
ciscoasa# ping 100.1.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.1.1.5, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/8/10 ms
ciscoasa# ping 200.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.1.1.2, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
ciscoasa# ping 200.1.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.1.1.4, timeout is 2 seconds:!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
6、R3远程Telnet登录R1,反过来登录,查看ARP,部署ACL:
R5#telnet 100.1.1.1
Trying 100.1.1.1 ... Open
User Access Verification
Username: aa
Password:
R1>
R1#show arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 100.1.1.5 0 cc05.0750.0000 ARPA FastEthernet0/0
Internet 100.1.1.1 - cc01.16d4.0000 ARPA FastEthernet0/0
ciscoasa(config)# access-list tel permit tcp host 100.1.1.1 host 100.1.1.5 eq 23
ciscoasa(config)# access-group tel in interface B1.outside
验证:
R1#telnet 100.1.1.5
Trying 100.1.1.5 ... Open
User Access Verification
Username: aa
Password:
R5>
以上是关于24-思科防火墙:ASA透明防火墙实验的主要内容,如果未能解决你的问题,请参考以下文章