Kubernetes(k8s)访问控制:身份认证
Posted 人生的哲理
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Kubernetes(k8s)访问控制:身份认证相关的知识,希望对你有一定的参考价值。
一.系统环境
本文主要基于Kubernetes1.21.9和Linux操作系统CentOS7.4。
| 服务器版本 | docker软件版本 | Kubernetes(k8s)集群版本 | CPU架构 |
|---|---|---|---|
| CentOS Linux release 7.4.1708 (Core) | Docker version 20.10.12 | v1.21.9 | x86_64 |
Kubernetes集群架构:k8scloude1作为master节点,k8scloude2,k8scloude3作为worker节点。
| 服务器 | 操作系统版本 | CPU架构 | 进程 | 功能描述 |
|---|---|---|---|---|
| k8scloude1/192.168.110.130 | CentOS Linux release 7.4.1708 (Core) | x86_64 | docker,kube-apiserver,etcd,kube-scheduler,kube-controller-manager,kubelet,kube-proxy,coredns,calico | k8s master节点 |
| k8scloude2/192.168.110.129 | CentOS Linux release 7.4.1708 (Core) | x86_64 | docker,kubelet,kube-proxy,calico | k8s worker节点 |
| k8scloude3/192.168.110.128 | CentOS Linux release 7.4.1708 (Core) | x86_64 | docker,kubelet,kube-proxy,calico | k8s worker节点 |
二.前言
作为目前最流行的容器编排平台之一,Kubernetes提供了强大的安全性能。在Kubernetes集群中,访问控制是保障集群安全的重要组成部分。其中,身份认证是访问控制的核心。本篇博客将介绍Kubernetes中的身份认证机制。
使用身份认证的前提是已经有一套可以正常运行的Kubernetes集群,关于Kubernetes(k8s)集群的安装部署,可以查看博客《Centos7 安装部署Kubernetes(k8s)集群》https://www.cnblogs.com/renshengdezheli/p/16686769.html。
三.Kubernetes访问控制
用户使用 kubectl、客户端库或构造 REST 请求来访问 Kubernetes API。 用户账户和 Kubernetes 服务账号都可以被鉴权访问 API。 当请求到达 API 时,它会经历多个阶段,如下图所示:
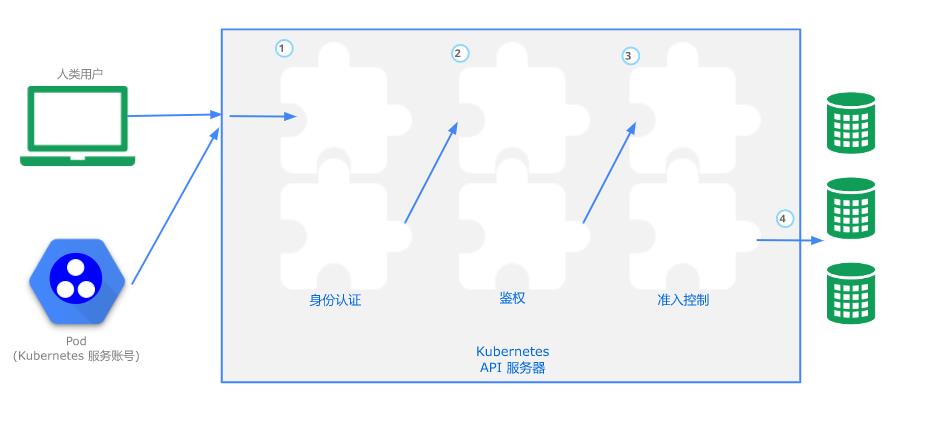
整体过程简述:请求发起方进行K8s API请求,建立 TLS 后,经过Authentication(认证)、Authorization(鉴权)、AdmissionControl(准入控制)三个阶段的校验,最后把请求转化为对K8s对象的变更操作持久化至etcd中。
四.身份认证简介
Kubernetes的身份认证机制用于识别发送请求的用户是否经过身份验证。通常情况下,这个过程包括以下步骤:
- 认证代理服务器接收到用户的请求。
- 认证代理服务器执行对用户的身份验证。
- 身份验证通过后,代理服务器会发出一个持有有效期的令牌,并在请求的标头中添加该令牌。
- 进入Kubernetes API server的请求会首先检查其标头中的令牌是否存在和有效。
- 如果令牌有效,则该请求将被允许进入API server进行处理。
用户账户:在Kubernetes中,每个用户都有一个账户,该账户用于表示用户的身份信息。账户由用户名、UID和组列表组成。其中,UID是唯一标识符,而组列表则表示用户所属的所有组。
Kubernetes支持多种身份认证方式,包括:
- 客户端证书认证
- HTTP基本认证
- Token认证
- OpenID Connect认证
五.身份认证
5.1 配置客户端机器
如下是我们的kubernetes集群。
[root@k8scloude1 ~]# kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
k8scloude1 Ready control-plane,master 67d v1.21.0 192.168.110.130 <none> CentOS Linux 7 (Core) 3.10.0-693.el7.x86_64 docker://20.10.12
k8scloude2 Ready <none> 67d v1.21.0 192.168.110.129 <none> CentOS Linux 7 (Core) 3.10.0-693.el7.x86_64 docker://20.10.12
k8scloude3 Ready <none> 67d v1.21.0 192.168.110.128 <none> CentOS Linux 7 (Core) 3.10.0-693.el7.x86_64 docker://20.10.12
先准备一台机器作为访问k8s集群的客户端,机器etcd1作为客户端,不是k8s集群的一部分。
访问k8s集群需要客户端工具kubectl,下面安装kubectl,--disableexcludes=kubernetes 表示禁掉除了这个之外的别的仓库。
[root@etcd1 ~]# yum -y install kubectl-1.21.0-0 --disableexcludes=kubernetes
配置kubectl命令自动补全。
[root@etcd1 ~]# vim /etc/profile
[root@etcd1 ~]# grep source /etc/profile
source <(kubectl completion bash)
使配置生效。
[root@etcd1 ~]# source /etc/profile
[root@etcd1 ~]# kubectl get node
The connection to the server localhost:8080 was refused - did you specify the right host or port?
5.2 使用base auth的方式进行认证
base-auth的验证方式,在kubernetes 1.19版本之后被遗弃了,所以知道有这么一种验证方式即可。
base auth验证的语法如下:kubectl -s="Kubernetes control plane地址" --username="用户名" --password="密码" get pods -n kube-system。
kubectl cluster-info可以查看集群信息,Kubernetes control plane,CoreDNS,Metrics-server地址如下。
[root@k8scloude1 ~]# kubectl cluster-info
Kubernetes control plane is running at https://192.168.110.130:6443
CoreDNS is running at https://192.168.110.130:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy
Metrics-server is running at https://192.168.110.130:6443/api/v1/namespaces/kube-system/services/https:metrics-server:/proxy
To further debug and diagnose cluster problems, use \'kubectl cluster-info dump\'.
kubectl options命令可以列出全局使用的命令参数。
[root@k8scloude1 ~]# kubectl options
The following options can be passed to any command:
--add-dir-header=false: If true, adds the file directory to the header of the log messages
......
--password=\'\': Password for basic authentication to the API server
--profile=\'none\': Name of profile to capture. One of (none|cpu|heap|goroutine|threadcreate|block|mutex)
--profile-output=\'profile.pprof\': Name of the file to write the profile to
--request-timeout=\'0\': The length of time to wait before giving up on a single server request. Non-zero values
should contain a corresponding time unit (e.g. 1s, 2m, 3h). A value of zero means don\'t timeout requests.
-s, --server=\'\': The address and port of the Kubernetes API server
--skip-headers=false: If true, avoid header prefixes in the log messages
--skip-log-headers=false: If true, avoid headers when opening log files
--stderrthreshold=2: logs at or above this threshold go to stderr
--tls-server-name=\'\': Server name to use for server certificate validation. If it is not provided, the hostname
used to contact the server is used
--token=\'\': Bearer token for authentication to the API server
--user=\'\': The name of the kubeconfig user to use
--username=\'\': Username for basic authentication to the API server
-v, --v=0: number for the log level verbosity
--vmodule=: comma-separated list of pattern=N settings for file-filtered logging
--warnings-as-errors=false: Treat warnings received from the server as errors and exit with a non-zero exit code
使用base auth的方式连接我们集群,kubernetes集群的Kubernetes control plane地址是https://192.168.110.130:6443,连接失败,因为用户qwe不存在。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --username="qwe" --password="ajkqk" get nodes
Unable to connect to the server: x509: certificate signed by unknown authority
5.3 使用token的方式进行认证
使用openssl生成一串token值。
[root@k8scloude1 ~]# openssl rand -hex 10
1b3aa30ed8b896146f0f
k8s默认不支持token认证,需要修改/etc/kubernetes/manifests/kube-apiserver.yaml 文件,启动token认证。
[root@k8scloude1 ~]# ls /etc/kubernetes/manifests/kube-apiserver.yaml
/etc/kubernetes/manifests/kube-apiserver.yaml
启动token认证方式,添加参数 - --token-auth-file=/etc/kubernetes/pki/mytok.csv - --enable-bootstrap-token-auth=true。
[root@k8scloude1 ~]# vim /etc/kubernetes/manifests/kube-apiserver.yaml
[root@k8scloude1 ~]# grep token-auth /etc/kubernetes/manifests/kube-apiserver.yaml
- --token-auth-file=/etc/kubernetes/pki/mytok.csv
- --enable-bootstrap-token-auth=true
/etc/kubernetes/pki/mytok.csv文件记录的是token,用户信息。/etc/kubernetes/pki/mytok.csv文件格式:token,用户名,id。
1b3aa30ed8b896146f0f,test,3表示test用户的id为3,token值为1b3aa30ed8b896146f0f。
[root@k8scloude1 ~]# vim /etc/kubernetes/pki/mytok.csv
[root@k8scloude1 ~]# cat /etc/kubernetes/pki/mytok.csv
1b3aa30ed8b896146f0f,test,3
重启kubelet使kube-apiserver.yaml 配置生效。
[root@k8scloude1 ~]# systemctl restart kubelet
[root@k8scloude1 ~]# systemctl status kubelet
● kubelet.service - kubelet: The Kubernetes Node Agent
Loaded: loaded (/usr/lib/systemd/system/kubelet.service; enabled; vendor preset: disabled)
Drop-In: /usr/lib/systemd/system/kubelet.service.d
└─10-kubeadm.conf
Active: active (running) since 五 2022-03-18 01:52:33 CST; 1s ago
Docs: https://kubernetes.io/docs/
Main PID: 91790 (kubelet)
Memory: 50.2M
CGroup: /system.slice/kubelet.service
└─91790 /usr/bin/kubelet --bootstrap-kubeconfig=/etc/kubernetes/bootstrap-kubelet.conf --kubeconfig=/etc/kubernetes/kubelet.conf --config=/var/lib/kubelet/config.yaml --network-plugin=cni --pod-in...
下面在客户端使用token进行认证,token值为/etc/kubernetes/pki/mytok.csv里的token值。报证书问题的错误。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --token=\'1b3aa30ed8b896146f0f\' get nodes
Unable to connect to the server: x509: certificate signed by unknown authority
--insecure-skip-tls-verify=true 忽略证书认证。可以看到认证成功,get nodes查看集群节点,但是没有权限查看集群节点,关于授权下一篇博客会讲。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --token=\'1b3aa30ed8b896146f0f\' --insecure-skip-tls-verify=true get nodes
Error from server (Forbidden): nodes is forbidden: User "test" cannot list resource "nodes" in API group "" at the cluster scope
查看pod。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --token=\'1b3aa30ed8b896146f0f\' --insecure-skip-tls-verify=true get pod
Error from server (Forbidden): pods is forbidden: User "test" cannot list resource "pods" in API group "" in the namespace "default"
查看kube-system命名空间下的pod,可以发现用户test使用token认证通过了,但是没有资源的访问权限,进行资源的授权即可 。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --token=\'1b3aa30ed8b896146f0f\' --insecure-skip-tls-verify=true get pod -n kube-system
Error from server (Forbidden): pods is forbidden: User "test" cannot list resource "pods" in API group "" in the namespace "kube-system"
使用错误的token就认证失败Unauthorized。
[root@etcd1 ~]# kubectl -s="https://192.168.110.130:6443" --token=\'1b3aa30ed8b896146f0g\' --insecure-skip-tls-verify=true get pod -n kube-system
error: You must be logged in to the server (Unauthorized)
5.4 使用管理员的kubeconfig文件进行认证
kubeconfig文件不是一个名字叫做kubeconfig的文件,而是用于做认证的文件我们就叫做kubeconfig文件,如果qwe.txt里有认证信息,则qwe.txt也就是kubeconfig文件。
安装好kubernetes集群之后,系统会生成一个管理员权限的kubeconfig文件:/etc/kubernetes/admin.conf。
[root@k8scloude1 ~]# ls /etc/kubernetes/
admin.conf controller-manager.conf kubelet.conf manifests pki scheduler.conf
[root@k8scloude1 ~]# ls /etc/kubernetes/admin.conf
/etc/kubernetes/admin.conf
切换到tom用户。
[root@k8scloude1 ~]# su - tom
因为Tom用户没有kubeconfig文件,所以连接不上k8s。
[tom@k8scloude1 ~]$ kubectl get nodes
The connection to the server localhost:8080 was refused - did you specify the right host or port?
[tom@k8scloude1 ~]$ exit
登出
root用户的家目录下有kubeconfig文件,所以可以连接k8s。
[root@k8scloude1 ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 67d v1.21.0
k8scloude2 Ready <none> 67d v1.21.0
k8scloude3 Ready <none> 67d v1.21.0
tom用户不能查看k8s节点状态,原因为没有kubeconfig文件。用户默认使用的kubeconfig文件是 ~/.kube/config ,比如:/root/.kube/config。
把具有管理员权限的kubeconfig文件:admin.conf复制到tom用户家目录下面。
[root@k8scloude1 ~]# cp /etc/kubernetes/admin.conf /home/tom/
修改属主。
[root@k8scloude1 ~]# chown tom:tom /home/tom/admin.conf
切换到tom用户。
[root@k8scloude1 ~]# su - tom
上一次登录:五 3月 18 11:48:02 CST 2022pts/0 上
[tom@k8scloude1 ~]$ ls
admin.conf
[tom@k8scloude1 ~]$ ll -h
总用量 8.0K
-rw------- 1 tom tom 5.5K 3月 18 11:55 admin.conf
查看k8s节点状态,--kubeconfig 指定所使用的kubeconfig文件。
[tom@k8scloude1 ~]$ kubectl --kubeconfig=admin.conf get nodes
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 67d v1.21.0
k8scloude2 Ready <none> 67d v1.21.0
k8scloude3 Ready <none> 67d v1.21.0
也可以设置环境变量。
[tom@k8scloude1 ~]$ export KUBECONFIG=admin.conf
[tom@k8scloude1 ~]$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 67d v1.21.0
k8scloude2 Ready <none> 67d v1.21.0
k8scloude3 Ready <none> 67d v1.21.0
取消环境变量。
[tom@k8scloude1 ~]$ unset KUBECONFIG
[tom@k8scloude1 ~]$ kubectl get nodes
The connection to the server localhost:8080 was refused - did you specify the right host or port?
把admin.conf复制到家目录下的隐藏文件里。
[tom@k8scloude1 ~]$ ls ~/.kube/
cache
[tom@k8scloude1 ~]$ cp admin.conf ~/.kube/config
[tom@k8scloude1 ~]$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 67d v1.21.0
k8scloude2 Ready <none> 67d v1.21.0
k8scloude3 Ready <none> 67d v1.21.0
要让其他客户端可以使用kubectl管理k8s,把kubeconfig文件拷贝到相应客户端机器即可。
[tom@k8scloude1 ~]$ scp admin.conf root@192.168.110.133:
在客户端使用kubeconfig文件连接k8s。
[root@etcd1 ~]# ls
admin.conf
[root@etcd1 ~]# kubectl --kubeconfig=admin.conf get node
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 67d v1.21.0
k8scloude2 Ready <none> 67d v1.21.0
k8scloude3 Ready <none> 67d v1.21.0
5.5 使用自定义的kubeconfig文件进行认证
/etc/kubernetes/admin.conf这个认证文件具有管理员权限,不适合普通用户使用,具有安全风险,接下来我们给普通用户创建一个自定义的kubeconfig文件。
kubectl config view获取kubeconfig文件结构,关于kubeconfig文件的详细介绍,请查看博客《k8s多集群切换:使用kubeconfig文件管理多套kubernetes(k8s)集群》。
[tom@k8scloude1 ~]$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.110.130:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences:
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
创建目录存放相关文件。
[root@k8scloude1 ~]# mkdir safe
[root@k8scloude1 ~]# cd safe/
创建命名空间。
[root@k8scloude1 safe]# kubectl create ns safe
namespace/safe created
切换namespace。
[root@k8scloude1 safe]# kubens safe
Context "kubernetes-admin@kubernetes" modified.
Active namespace is "safe".
[root@k8scloude1 safe]# kubectl get pod
No resources found in safe namespace.
5.5.1 申请证书
下面开始申请证书。
创建私钥,名字可以自己命名为 test.key。
[root@k8scloude1 safe]# openssl genrsa -out test.key 2048
Generating RSA private key, 2048 bit long modulus
...............................+++
.....................................................................................+++
e is 65537 (0x10001)
利用刚生成的私钥test.key ,生成证书请求文件 test.csr,CN 的值 test,就是我们授权的用户。
[root@k8scloude1 safe]# openssl req -new -key test.key -out test.csr -subj "/CN=test/O=cka2020"
[root@k8scloude1 safe]# ls
test.csr test.key
对证书请求文件test.csr进行 base64 编码。
[root@k8scloude1 safe]# cat test.csr | base64 | tr -d "\\n"
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pqQ0NBVTRDQVFBd0lURU5NQXNHQTFVRUF3d0VkR1Z6ZERFUU1BNEdBMVVFQ2d3SFkydGhNakF5TURDQwpBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQQURDQ0FRb0NnZ0VCQUxJTWtZTGN5NklWM3FSMmRJSm8vUnRRCnZ1amYrYjRMUWp2YjlSeGhaTjZTdEcyUFlMWHhvSi9FRUlVYkJMb1dpUFg0NVhvdDNNamNLRmtaaUoyWmY1L3EKeHhPRkF2dFliM3NCNVI0UCt0V2xMeExialBibS9NNE56QXl0eUJvOWl4cFh0ODNFRFJZaElac2VDR2NVTlVuMQpkMUl4NW0rRkdTU3RTZmU0MDdPM3IrTTRsMVF1U3JWNCtIYmFST0l3cW4rTmpzbGVEdmVzV2FPVWx2ZkJqR0tmCjVxejk1bVZGMGp4NUxYNzVwWHFvTWljWnU3c0dLMFFWV0ZFOUR4ZXFCMlgrb2pPc2dYYVRVNUtzSHJESlcxb3gKRlJIVm10NEx5Q0dUd3dDZzNGWFVJWnNCM1FRb3lNLytKbTNkWVg1bGhxaE9sekYxdU4vOGdzTG1Rci9LeXRFQwpBd0VBQWFBQU1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQm9HWlE5cWo2QlluTmtKM3lubG8xdjR0MStTa0U4CmUxOXdiL3IyNnlRRHhpWWoreHU4V042TUZBY3hldmtYTWQzUTA3NmpBa2ZnRTRrV2xYV09YQVd3SmNIdGI2RzgKaVZMMmxKRVd0WWhDcVVBRmlwZzREN29YSHBPTEUwNElwOHVyMVFheHdQODFhQ2RLRDNFSVVNbGJuR3BpcXpmLwp3cFJZbklBeWpoVzhraldmSUNEeHZrM2VIWUFhQUdGM0JxcXEyaEQyQ2lQVkVwS2dXa3FrVUF0bzF6K2JDdjZzCk0zVDgyR2IrbGFrelVYNjRUSU9pUHNNbXpQTWJJbUxlN3pkZTM3Ry9ZVXh6MTY1dGJQUXRkTFFmQzhGS3lnY1UKOW5kR3k2Q3piUFNFanp0cjMvcXdpdWpEK09IYVpocE9jdjBkSmdRc3NpUlQxQVU0S3NvUFBkSkUKLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==[root@k8scloude1 safe]#
编写申请证书请求文件的 yaml 文件,注意:这里 apiVersion 要带 beta1,否则 signerName 那行就不能注释掉,但这样的话后面的 操作就不能获取到证书。这里 request 里的是 base64 编码之后的证书请求文件。
[root@k8scloude1 safe]# vim csr.yaml
[root@k8scloude1 safe]# cat csr.yaml
apiVersion: certificates.k8s.io/v1beta1
kind: CertificateSigningRequest
metadata:
name: test
spec:
groups:
- system:authenticated
#signerName: kubernetes.io/legacy-aa #注意这行是被注释掉的
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pqQ0NBVTRDQVFBd0lURU5NQXNHQTFVRUF3d0VkR1Z6ZERFUU1BNEdBMVVFQ2d3SFkydGhNakF5TURDQwpBU0l3RFFZSktvWklodmNOQVFFQkJRQURnZ0VQQURDQ0FRb0NnZ0VCQUxJTWtZTGN5NklWM3FSMmRJSm8vUnRRCnZ1amYrYjRMUWp2YjlSeGhaTjZTdEcyUFlMWHhvSi9FRUlVYkJMb1dpUFg0NVhvdDNNamNLRmtaaUoyWmY1L3EKeHhPRkF2dFliM3NCNVI0UCt0V2xMeExialBibS9NNE56QXl0eUJvOWl4cFh0ODNFRFJZaElac2VDR2NVTlVuMQpkMUl4NW0rRkdTU3RTZmU0MDdPM3IrTTRsMVF1U3JWNCtIYmFST0l3cW4rTmpzbGVEdmVzV2FPVWx2ZkJqR0tmCjVxejk1bVZGMGp4NUxYNzVwWHFvTWljWnU3c0dLMFFWV0ZFOUR4ZXFCMlgrb2pPc2dYYVRVNUtzSHJESlcxb3gKRlJIVm10NEx5Q0dUd3dDZzNGWFVJWnNCM1FRb3lNLytKbTNkWVg1bGhxaE9sekYxdU4vOGdzTG1Rci9LeXRFQwpBd0VBQWFBQU1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQm9HWlE5cWo2QlluTmtKM3lubG8xdjR0MStTa0U4CmUxOXdiL3IyNnlRRHhpWWoreHU4V042TUZBY3hldmtYTWQzUTA3NmpBa2ZnRTRrV2xYV09YQVd3SmNIdGI2RzgKaVZMMmxKRVd0WWhDcVVBRmlwZzREN29YSHBPTEUwNElwOHVyMVFheHdQODFhQ2RLRDNFSVVNbGJuR3BpcXpmLwp3cFJZbklBeWpoVzhraldmSUNEeHZrM2VIWUFhQUdGM0JxcXEyaEQyQ2lQVkVwS2dXa3FrVUF0bzF6K2JDdjZzCk0zVDgyR2IrbGFrelVYNjRUSU9pUHNNbXpQTWJJbUxlN3pkZTM3Ry9ZVXh6MTY1dGJQUXRkTFFmQzhGS3lnY1UKOW5kR3k2Q3piUFNFanp0cjMvcXdpdWpEK09IYVpocE9jdjBkSmdRc3NpUlQxQVU0S3NvUFBkSkUKLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==
usages:
- client auth
申请证书。
[root@k8scloude1 safe]# kubectl apply -f csr.yaml
Warning: certificates.k8s.io/v1beta1 CertificateSigningRequest is deprecated in v1.19+, unavailable in v1.22+; use certificates.k8s.io/v1 CertificateSigningRequest
certificatesigningrequest.certificates.k8s.io/test created
查看已经发出证书申请的请求。
[root@k8scloude1 safe]# kubectl get csr -o wide
NAME AGE SIGNERNAME REQUESTOR CONDITION
test 95s kubernetes.io/legacy-unknown kubernetes-admin Pending
批准证书。
[root@k8scloude1 safe]# kubectl certificate approve test
certificatesigningrequest.certificates.k8s.io/test approved
查看审批通过的证书。
[root@k8scloude1 safe]# kubectl get csr -o wide
NAME AGE SIGNERNAME REQUESTOR CONDITION
test 3m15s kubernetes.io/legacy-unknown kubernetes-admin Approved,Issued
以yaml文件的格式查看审批通过的证书。
[root@k8scloude1 safe]# kubectl get csr test -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
"apiVersion":"certificates.k8s.io/v1beta1","kind":"CertificateSigningRequest","metadata":"annotations":,"name":"test","spec":"groups":["system:authenticated"],"request":"......","usages":["client auth"]
creationTimestamp: "2022-03-18T07:46:23Z"
name: test
resourceVersion: "2771685"
selfLink: /apis/certificates.k8s.io/v1/certificatesigningrequests/test
uid: b04adc21-54c9-4fc7-b2bd-5544b74ee647
spec:
groups:
- system:masters
- system:authenticated
request: ......
signerName: kubernetes.io/legacy-unknown
usages:
- client auth
username: kubernetes-admin
status:
certificate: ......
conditions:
- lastTransitionTime: "2022-03-18T07:49:32Z"
lastUpdateTime: "2022-03-18T07:49:32Z"
message: This CSR was approved by kubectl certificate approve.
reason: KubectlApprove
status: "True"
type: Approved
/etc/kubernetes/pki/目录下存放的都是集群的证书。
[root@k8scloude1 safe]# ls /etc/kubernetes/pki/
apiserver.crt apiserver-etcd-client.key apiserver-kubelet-client.crt ca.crt etcd front-proxy-ca.key front-proxy-client.key sa.key
apiserver-etcd-client.crt apiserver.key apiserver-kubelet-client.key ca.key front-proxy-ca.crt front-proxy-client.crt mytok.csv sa.pub
只查看certificate字段,查看证书。
[root@k8scloude1 safe]# kubectl get csr/test -o jsonpath=\'.status.certificate\'
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCekNDQWUrZ0F3SUJBZ0lSQUxnZXduNXBxTzVUc1JELytpTmZua1l3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TWpBek1UZ3dOelEwTXpKYUZ3MHlNekF6TVRndwpOelEwTXpKYU1DRXhFREFPQmdOVkJBb1RCMk5yWVRJd01qQXhEVEFMQmdOVkJBTVRCSFJsYzNRd2dnRWlNQTBHCkNTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDeURKR0MzTXVpRmQ2a2RuU0NhUDBiVUw3bzMvbSsKQzBJNzIvVWNZV1Rla3JSdGoyQzE4YUNmeEJDRkd3UzZGb2oxK09WNkxkekkzQ2haR1lpZG1YK2Y2c2NUaFFMNwpXRzk3QWVVZUQvclZwUzhTMjR6MjV2ek9EY3dNcmNnYVBZc2FWN2ZOeEEwV0lTR2JIZ2huRkRWSjlYZFNNZVp2CmhSa2tyVW4zdU5PenQ2L2pPSmRVTGtxMWVQaDIya1RpTUtwL2pZN0pYZzczckZtamxKYjN3WXhpbithcy9lWmwKUmRJOGVTMSsrYVY2cURJbkdidTdCaXRFRlZoUlBROFhxZ2RsL3FJenJJRjJrMU9TckI2d3lWdGFNUlVSMVpyZQpDOGdoazhNQW9OeFYxQ0diQWQwRUtNalAvaVp0M1dGK1pZYW9UcGN4ZGJqZi9JTEM1a0sveXNyUkFnTUJBQUdqClJqQkVNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdId1lEVlIwakJCZ3cKRm9BVXd5QzNoOGt5RUtRcnJocTVod3Y5UjQ4cjMwOHdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBS1F1SGlIagpXbWdoL29GWkg0S0h5dVRDZmhjK0w3S0JMd0M5c0U5cHQrck1LMzczODdXZU5mVDN5Y0psSE9qMU0zQ2I0M3lPCnB3RmlsZ3g3MlAwVTlzdnZybzBRZjUycUxTSUlBekNORFFvNkFNRWxtVDlYUkJ0bGxHM2ZlT0dZSGxQN3NwTEMKM3BQUWNrZkxsTU9qSVBILzhxQ08zZmNMOUNIcUkzRFVqZ0VxSUV1NTh2cnN0VFIzRjljZGN0aWdzaGlMWHBBbwpuOWpNMmRZSG0xdmh1aU9mS2VIdWllKzZIaVZZZVAyWjdieEtBKzNpVkhac0krc1lpWXhPZENnRTdobmVLcXd6CnhGVjQvZUxSbzgrdHVEanJlbUJhUTJQaDhPUkZ6bkFzc3RaNXdaSkQ1dUFJdUd6L0hudHBQdk1uNjZqLytuTmgKbDcvOVFNaDI0YzRqU1B3PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==[root@k8scloude1 safe]#
对certificate解码并导出证书文件。
[root@k8scloude1 safe]# kubectl get csr/test -o jsonpath=\'.status.certificate\' | base64 -d > test.crt
查看证书文件。
[root@k8scloude1 safe]# ls
csr.yaml test.crt test.csr test.key
[root@k8scloude1 safe]# cat test.crt
-----BEGIN CERTIFICATE-----
MIIDBzCCAe+gAwIBAgIRALgewn5pqO5TsRD/+iNfnkYwDQYJKoZIhvcNAQELBQAw
FTETMBEGA1UEAxMKa3ViZXJuZXRlczAeFw0yMjAzMTgwNzQ0MzJaFw0yMzAzMTgw
NzQ0MzJaMCExEDAOBgNVBAoTB2NrYTIwMjAxDTALBgNVBAMTBHRlc3QwggEiMA0G
CSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCyDJGC3MuiFd6kdnSCaP0bUL7o3/m+
C0I72/UcYWTekrRtj2C18aCfxBCFGwS6Foj1+OV6LdzI3ChZGYidmX+f6scThQL7
WG97AeUeD/rVpS8S24z25vzODcwMrcgaPYsaV7fNxA0WISGbHghnFDVJ9XdSMeZv
hRkkrUn3uNOzt6/jOJdULkq1ePh22kTiMKp/jY7JXg73rFmjlJb3wYxin+as/eZl
RdI8eS1++aV6qDInGbu7BitEFVhRPQ8Xqgdl/qIzrIF2k1OSrB6wyVtaMRUR1Zre
C8ghk8MAoNxV1CGbAd0EKMjP/iZt3WF+ZYaoTpcxdbjf/ILC5kK/ysrRAgMBAAGj
RjBEMBMGA1UdJQQMMAoGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHwYDVR0jBBgw
FoAUwyC3h8kyEKQrrhq5hwv9R48r308wDQYJKoZIhvcNAQELBQADggEBAKQuHiHj
Wmgh/oFZH4KHyuTCfhc+L7KBLwC9sE9pt+rMK37387WeNfT3ycJlHOj1M3Cb43yO
pwFilgx72P0U9svvro0Qf52qLSIIAzCNDQo6AMElmT9XRBtllG3feOGYHlP7spLC
3pPQckfLlMOjIPH/8qCO3fcL9CHqI3DUjgEqIEu58vrstTR3F9cdctigshiLXpAo
n9jM2dYHm1vhuiOfKeHuie+6HiVYeP2Z7bxKA+3iVHZsI+sYiYxOdCgE7hneKqwz
xFV4/eLRo8+tuDjremBaQ2Ph8ORFznAsstZ5wZJD5uAIuGz/HntpPvMn66j/+nNh
l7/9QMh24c4jSPw=
-----END CERTIFICATE-----
[root@k8scloude1 safe]# ls
csr.yaml test.crt test.csr test.key
test用户的证书文件就申请好了。
5.5.2 生成test用户的kubeconfig文件
拷贝 CA 证书。
[root@k8scloude1 safe]# cp /etc/kubernetes/pki/ca.crt .
[root@k8scloude1 safe]# ls
ca.crt csr.yaml test.crt test.csr test.key
kubeconfig文件包含3个字段:cluster,user,context上下文(可以把cluster和user关联在一起),kubeconfig文件里,clusters 字段指定 kubernetes 集群的信息,users 指定用户,contexts 用于 指定上下文,包括用户默认所在的命名空间等信息。
设置集群字段:--kubeconfig指定生成的kubeconfig文件名,set-cluster指定集群名,--server指定连接的那个k8s上,--certificate-authority 指定CA证书,--embed-certs=true 的意思是把CA证书内容写入到此 kubeconfig 文件里。
[root@k8scloude1 safe]# kubectl config --kubeconfig=kctest set-cluster clustertest --server=https://192.168.110.130:6443 --certificate-authority=ca.crt --embed-certs=true
Cluster "clustertest" set.
查看kctest 。
[root@k8scloude1 safe]# ls
ca.crt csr.yaml kctest test.crt test.csr test.key
[root@k8scloude1 safe]# cat kctest
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeU1ERXdPVEE0TVRnd01Wb1hEVE15TURFd056QTRNVGd3TVZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTEZyCkRxb2YyV2twdDJ1a2xSWnljRHQyQ2xmYnNXdTBhb256NW1rTG5IaThlZFdJbkdWR09tMllxV0x2V20yRGFrYWYKSk9oNmtRU0wyYjBXZjBRbnZaMklIQ0hBYm5lTmI0NEpIaHVTL2MxU285d2VNQm5GNk9ZRjU2Qkk4dnlSamJhZgoyVXBQSUhNZTlYcitmZTYvRHRmTGFwOERkSFlCWGFPWlpZcDZIaGEyU1JWSjg4cmJRbzJuWnV6Ykl5bWdMUnpSCnpwdE9TRVpBa1JUMzRkZmF4bm0yM3hVNG9vSnRDRWhjZVNjZ3QvZ0szOFRXMmJkRmIzU1c2UWdNc0FFOG4yVXQKaDR4c203TDVla29kTHU1N2VmWHhNZTVKTU5yTXBIL0h5M3BHSlpab0NYbG5rbm9ML2EzdTBHKzgzak8zcXRzWgp0M004TDdDcTc5Qm5BQW41aS8wQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNTWd0NGZKTWhDa0s2NGF1WWNML1VlUEs5OVBNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDcFVtSittNk9nNFZuQjBSNWpxd05EakJxZ0pQVWtONHB1MFFURlg1WWs4NGFOMnQvYgpKWTFTQ3hnR2h5Q1JERVA1U0NUMXZrdHRqaFpVVnArZjdZUnE3V1BXK0JQcWE3Nm5TUlEydUkxRHoxVDhZSGNnCi9CRkNadWIwQVZ4Y0Z1RTdSb1NkbjFDOTlqaERjUCtIRW9zRFl6dUYzZmo4QzlCMkl6d3ZIaHpaUDAvVlZSRDcKay9wWk5ub3hRdHNoWHdvVnhYS1BacHNGMHhvL1ppcUVoa2ZIYURMVC9MZE5qYXhyTjNOcFRhbTNTV2tyelZ6VQpKWGpyL0xKbGs3THVBcVBVT1VBdHBRTDZSbTArTXVQTGw0YkxQNFhOOTZOZit0NDlHdS9LeXBabXpIQkFOMWl0CkYrN0szeXVoamQ4VVNtUE14SVdPR2JEc05sTHMzTmJ5S3RpNgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.110.130:6443
name: clustertest
contexts: null
current-context: ""
kind: Config
preferences:
users: null
这里--embed-certs=true 的意思是把CA证书内容写入到此 kubeconfig 文件里,如果--embed-certs=false,使用kctest文件还要把ca.crt也要拷贝到相应地方。
[root@k8scloude1 safe]# kubectl config --kubeconfig=kctest set-cluster clustertest --server=https://192.168.110.130:6443 --certificate-authority=ca.crt --embed-certs=false
Cluster "clustertest" set.
[root@k8scloude1 safe]# cat kctest
apiVersion: v1
clusters:
- cluster:
certificate-authority: ca.crt
server: https://192.168.110.130:6443
name: clustertest
contexts: null
current-context: ""
kind: Config
preferences:
users: null
设置集群字段。
[root@k8scloude1 safe]# kubectl config --kubeconfig=kctest set-cluster clustertest --server=https://192.168.110.130:6443 --certificate-authority=ca.crt --embed-certs=true
Cluster "clustertest" set.
设置用户字段。
[root@k8scloude1 safe]# kubectl config --kubeconfig=kctest set-credentials test --client-certificate=test.crt --client-key=test.key --embed-certs=true
User "test" set.
查看kctest 。
[root@k8scloude1 safe]# cat kctest
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeU1ERXdPVEE0TVRnd01Wb1hEVE15TURFd056QTRNVGd3TVZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTEZyCkRxb2YyV2twdDJ1a2xSWnljRHQyQ2xmYnNXdTBhb256NW1rTG5IaThlZFdJbkdWR09tMllxV0x2V20yRGFrYWYKSk9oNmtRU0wyYjBXZjBRbnZaMklIQ0hBYm5lTmI0NEpIaHVTL2MxU285d2VNQm5GNk9ZRjU2Qkk4dnlSamJhZgoyVXBQSUhNZTlYcitmZTYvRHRmTGFwOERkSFlCWGFPWlpZcDZIaGEyU1JWSjg4cmJRbzJuWnV6Ykl5bWdMUnpSCnpwdE9TRVpBa1JUMzRkZmF4bm0yM3hVNG9vSnRDRWhjZVNjZ3QvZ0szOFRXMmJkRmIzU1c2UWdNc0FFOG4yVXQKaDR4c203TDVla29kTHU1N2VmWHhNZTVKTU5yTXBIL0h5M3BHSlpab0NYbG5rbm9ML2EzdTBHKzgzak8zcXRzWgp0M004TDdDcTc5Qm5BQW41aS8wQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNTWd0NGZKTWhDa0s2NGF1WWNML1VlUEs5OVBNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDcFVtSittNk9nNFZuQjBSNWpxd05EakJxZ0pQVWtONHB1MFFURlg1WWs4NGFOMnQvYgpKWTFTQ3hnR2h5Q1JERVA1U0NUMXZrdHRqaFpVVnArZjdZUnE3V1BXK0JQcWE3Nm5TUlEydUkxRHoxVDhZSGNnCi9CRkNadWIwQVZ4Y0Z1RTdSb1NkbjFDOTlqaERjUCtIRW9zRFl6dUYzZmo4QzlCMkl6d3ZIaHpaUDAvVlZSRDcKay9wWk5ub3hRdHNoWHdvVnhYS1BacHNGMHhvL1ppcUVoa2ZIYURMVC9MZE5qYXhyTjNOcFRhbTNTV2tyelZ6VQpKWGpyL0xKbGs3THVBcVBVT1VBdHBRTDZSbTArTXVQTGw0YkxQNFhOOTZOZit0NDlHdS9LeXBabXpIQkFOMWl0CkYrN0szeXVoamQ4VVNtUE14SVdPR2JEc05sTHMzTmJ5S3RpNgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.110.130:6443
name: clustertest
contexts: null
current-context: ""
kind: Config
preferences:
users:
- name: test
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCekNDQWUrZ0F3SUJBZ0lSQUxnZXduNXBxTzVUc1JELytpTmZua1l3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TWpBek1UZ3dOelEwTXpKYUZ3MHlNekF6TVRndwpOelEwTXpKYU1DRXhFREFPQmdOVkJBb1RCMk5yWVRJd01qQXhEVEFMQmdOVkJBTVRCSFJsYzNRd2dnRWlNQTBHCkNTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDeURKR0MzTXVpRmQ2a2RuU0NhUDBiVUw3bzMvbSsKQzBJNzIvVWNZV1Rla3JSdGoyQzE4YUNmeEJDRkd3UzZGb2oxK09WNkxkekkzQ2haR1lpZG1YK2Y2c2NUaFFMNwpXRzk3QWVVZUQvclZwUzhTMjR6MjV2ek9EY3dNcmNnYVBZc2FWN2ZOeEEwV0lTR2JIZ2huRkRWSjlYZFNNZVp2CmhSa2tyVW4zdU5PenQ2L2pPSmRVTGtxMWVQaDIya1RpTUtwL2pZN0pYZzczckZtamxKYjN3WXhpbithcy9lWmwKUmRJOGVTMSsrYVY2cURJbkdidTdCaXRFRlZoUlBROFhxZ2RsL3FJenJJRjJrMU9TckI2d3lWdGFNUlVSMVpyZQpDOGdoazhNQW9OeFYxQ0diQWQwRUtNalAvaVp0M1dGK1pZYW9UcGN4ZGJqZi9JTEM1a0sveXNyUkFnTUJBQUdqClJqQkVNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdId1lEVlIwakJCZ3cKRm9BVXd5QzNoOGt5RUtRcnJocTVod3Y5UjQ4cjMwOHdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBS1F1SGlIagpXbWdoL29GWkg0S0h5dVRDZmhjK0w3S0JMd0M5c0U5cHQrck1LMzczODdXZU5mVDN5Y0psSE9qMU0zQ2I0M3lPCnB3RmlsZ3g3MlAwVTlzdnZybzBRZjUycUxTSUlBekNORFFvNkFNRWxtVDlYUkJ0bGxHM2ZlT0dZSGxQN3NwTEMKM3BQUWNrZkxsTU9qSVBILzhxQ08zZmNMOUNIcUkzRFVqZ0VxSUV1NTh2cnN0VFIzRjljZGN0aWdzaGlMWHBBbwpuOWpNMmRZSG0xdmh1aU9mS2VIdWllKzZIaVZZZVAyWjdieEtBKzNpVkhac0krc1lpWXhPZENnRTdobmVLcXd6CnhGVjQvZUxSbzgrdHVEanJlbUJhUTJQaDhPUkZ6bkFzc3RaNXdaSkQ1dUFJdUd6L0hudHBQdk1uNjZqLytuTmgKbDcvOVFNaDI0YzRqU1B3PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb2dJQkFBS0NBUUVBc2d5Umd0ekxvaFhlcEhaMGdtajlHMUMrNk4vNXZndENPOXYxSEdGazNwSzBiWTlnCnRmR2duOFFRaFJzRXVoYUk5ZmpsZWkzY3lOd29XUm1JblpsL24rckhFNFVDKzFodmV3SGxIZy82MWFVdkV0dU0KOXViOHpnM01ESzNJR2oyTEdsZTN6Y1FORmlFaG14NElaeFExU2ZWM1VqSG1iNFVaSksxSjk3alRzN2V2NHppWApWQzVLdFhqNGR0cEU0akNxZjQyT3lWNE85NnhabzVTVzk4R01ZcC9tclAzbVpVWFNQSGt0ZnZtbGVxZ3lKeG03CnV3WXJSQlZZVVQwUEY2b0haZjZpTTZ5QmRwTlRrcXdlc01sYldqRVZFZFdhM2d2SUlaUERBS0RjVmRRaG13SGQKQkNqSXovNG1iZDFoZm1XR3FFNlhNWFc0My95Q3d1WkN2OHJLMFFJREFRQUJBb0lCQUJwK2RFaWN3bEJrSUxVbwpTejM4a1cwM0hyRllZcms4dzZaVW5LeVVjWVlOSG53UEViMEJMMzJXbHo2M1BvVFNSWjhVWWxGRDhjNlJ0QTlPCkZWNGVNVGVDb0F6dmhmb1F0c1gvQ2pEbS85UTZ1RDUrSFFQQWEyM2Q3N2NUUk90aXJRaEdkVHRSS1FGWi9MNHcKUWQvVXlma3ZaWW45a3VTVlVhQjdpTDRyNnBTYlNQNmhmQktraWZqd2FOY3N5TW9xZk5ub0ZJZVJOZ3Fxd2d1cQpEOHVMSTNlY2JFKytnTmUySkNROTNYbmtmdERWa0NoNUVIRHlwU3BPaVM2RXgxVnRqMGRhSXdUaVp4STNxRHh1ClEzTkJialJ5MFhqckkwNWhQUU1SKysrUm83YnlsQlFXQmtuM0Z2ckNFY2w5RVVaUlRqUEhUaFMrcldWYUFlSWYKVzlKZFpnRUNnWUVBNXFVT2U4TmZ1Q1dwL0hRYzA0TXpkazFLZ3d5OFd1bmFJT3MyNHJoNjZVWmprN0Y1cEUvYQpoVDBJSTJBaURPRGpmMWh1MXkwTTZibFVDc1NpcXdLQ28wR0d2WnMrOU55WlBOMFhtQ0EvOTlVUG5HRzI1OE5RCjI4U1lCL05COWZRRjVtbFY3NDNDRzhYcHVITUZhS0ZrVHoxZnlFKzVFUThtMEVnZkJwMWhINGtDZ1lFQXhaOVYKVEdPam5CUU5HYUg5RTRaaWRDSXIvR3BlSkxvQnhRd05MaDFqT1dkcjVKNW91MDRsNVp4NW10S090R1JQc3FZYQpsOWxKRzlJUGkxNTBiNU05aDB0K0lZWUR6NjdORlNIR0Z6aHFST29lS25lQnRteTVYVHdKMDhyY205QlFrUjlZCmZmTExkSCtvSi9RblNGNFhrWlo0VUk5L3NtdWdZQXhJQmgzNGR3a0NnWUFEY3V4b2hWOWxEWXNoTDB0UERtTXkKbmExRGtHa3dvdGFVTDNBK3E2dUsyWGFidXNlcTRWYlBMejV6NlBnWllUT0ZyL2pZVnVBZWpwcm5IbEdnWlFVMwpFNy9FRGhJKzd4MkxmM0xlMzN5VlpDWTduR3B6eE1Qc3hWL1FucDZaNHZCRHBjZVhNWE41bnRnRDNoUnlvQmN6CjZDTUtoOGFvcnFWUjhBSW13eXUwb1FLQmdCTlVORG1XZlVna3hlczk1c3prRmZrWjVvZDN0K0dMdCtTWCt5b0oKZ2N6NWlwbi96R3FWaUN0ZkZKM0ovbDh5ZUlFV3NmOHNKM1JySlU0U1hQMFV2NjNkK21ZNC8ySnV6R3hHczJOTwpCMGJhUnowTUYwbktkSTdqOG1vZXExa3FGTmM4NDZEZUFIeFNpQlh3VVc5SWxMR09zQkhoRnpKU1NJdGNhQ2NCCkEyNVJBb0dBRW5pUDQwVjExNnVibThPTjFua3Z6NmpzRFdGdDdaTllBdDQ1cE9oN2lYNnh6UC9IZ0VtWjJ4b2wKeFVYekJueXpDSHZkVk1IQjI0bXYzYVhLcWtvTlY0elJmbHlyVG9neVhzQlAzQ0hmYzcwM29ONXVQK3BzVDVnVQpzRkN4TDlwQ0V4NVBxWTdYNDVJZ0VHNE9Dc2FUS3JBeDFtZmZOVnkraWhnQ3VFYjU4dkE9Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
设置上下文字段。
[root@k8scloude1 safe]# kubectl config --kubeconfig=kctest set-context contexttest --cluster=clustertest --namespace=default --user=test
Context "contexttest" created.
现在kctest就是一个完整的kubeconfig文件了。
[root@k8scloude1 safe]# cat kctest
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeU1ERXdPVEE0TVRnd01Wb1hEVE15TURFd056QTRNVGd3TVZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTEZyCkRxb2YyV2twdDJ1a2xSWnljRHQyQ2xmYnNXdTBhb256NW1rTG5IaThlZFdJbkdWR09tMllxV0x2V20yRGFrYWYKSk9oNmtRU0wyYjBXZjBRbnZaMklIQ0hBYm5lTmI0NEpIaHVTL2MxU285d2VNQm5GNk9ZRjU2Qkk4dnlSamJhZgoyVXBQSUhNZTlYcitmZTYvRHRmTGFwOERkSFlCWGFPWlpZcDZIaGEyU1JWSjg4cmJRbzJuWnV6Ykl5bWdMUnpSCnpwdE9TRVpBa1JUMzRkZmF4bm0yM3hVNG9vSnRDRWhjZVNjZ3QvZ0szOFRXMmJkRmIzU1c2UWdNc0FFOG4yVXQKaDR4c203TDVla29kTHU1N2VmWHhNZTVKTU5yTXBIL0h5M3BHSlpab0NYbG5rbm9ML2EzdTBHKzgzak8zcXRzWgp0M004TDdDcTc5Qm5BQW41aS8wQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNTWd0NGZKTWhDa0s2NGF1WWNML1VlUEs5OVBNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDcFVtSittNk9nNFZuQjBSNWpxd05EakJxZ0pQVWtONHB1MFFURlg1WWs4NGFOMnQvYgpKWTFTQ3hnR2h5Q1JERVA1U0NUMXZrdHRqaFpVVnArZjdZUnE3V1BXK0JQcWE3Nm5TUlEydUkxRHoxVDhZSGNnCi9CRkNadWIwQVZ4Y0Z1RTdSb1NkbjFDOTlqaERjUCtIRW9zRFl6dUYzZmo4QzlCMkl6d3ZIaHpaUDAvVlZSRDcKay9wWk5ub3hRdHNoWHdvVnhYS1BacHNGMHhvL1ppcUVoa2ZIYURMVC9MZE5qYXhyTjNOcFRhbTNTV2tyelZ6VQpKWGpyL0xKbGs3THVBcVBVT1VBdHBRTDZSbTArTXVQTGw0YkxQNFhOOTZOZit0NDlHdS9LeXBabXpIQkFOMWl0CkYrN0szeXVoamQ4VVNtUE14SVdPR2JEc05sTHMzTmJ5S3RpNgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.110.130:6443
name: clustertest
contexts:
- context:
cluster: clustertest
namespace: default
user: test
name: contexttest
current-context: ""
kind: Config
preferences:
users:
- name: test
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCekNDQWUrZ0F3SUJBZ0lSQUxnZXduNXBxTzVUc1JELytpTmZua1l3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TWpBek1UZ3dOelEwTXpKYUZ3MHlNekF6TVRndwpOelEwTXpKYU1DRXhFREFPQmdOVkJBb1RCMk5yWVRJd01qQXhEVEFMQmdOVkJBTVRCSFJsYzNRd2dnRWlNQTBHCkNTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDeURKR0MzTXVpRmQ2a2RuU0NhUDBiVUw3bzMvbSsKQzBJNzIvVWNZV1Rla3JSdGoyQzE4YUNmeEJDRkd3UzZGb2oxK09WNkxkekkzQ2haR1lpZG1YK2Y2c2NUaFFMNwpXRzk3QWVVZUQvclZwUzhTMjR6MjV2ek9EY3dNcmNnYVBZc2FWN2ZOeEEwV0lTR2JIZ2huRkRWSjlYZFNNZVp2CmhSa2tyVW4zdU5PenQ2L2pPSmRVTGtxMWVQaDIya1RpTUtwL2pZN0pYZzczckZtamxKYjN3WXhpbithcy9lWmwKUmRJOGVTMSsrYVY2cURJbkdidTdCaXRFRlZoUlBROFhxZ2RsL3FJenJJRjJrMU9TckI2d3lWdGFNUlVSMVpyZQpDOGdoazhNQW9OeFYxQ0diQWQwRUtNalAvaVp0M1dGK1pZYW9UcGN4ZGJqZi9JTEM1a0sveXNyUkFnTUJBQUdqClJqQkVNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdId1lEVlIwakJCZ3cKRm9BVXd5QzNoOGt5RUtRcnJocTVod3Y5UjQ4cjMwOHdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBS1F1SGlIagpXbWdoL29GWkg0S0h5dVRDZmhjK0w3S0JMd0M5c0U5cHQrck1LMzczODdXZU5mVDN5Y0psSE9qMU0zQ2I0M3lPCnB3RmlsZ3g3MlAwVTlzdnZybzBRZjUycUxTSUlBekNORFFvNkFNRWxtVDlYUkJ0bGxHM2ZlT0dZSGxQN3NwTEMKM3BQUWNrZkxsTU9qSVBILzhxQ08zZmNMOUNIcUkzRFVqZ0VxSUV1NTh2cnN0VFIzRjljZGN0aWdzaGlMWHBBbwpuOWpNMmRZSG0xdmh1aU9mS2VIdWllKzZIaVZZZVAyWjdieEtBKzNpVkhac0krc1lpWXhPZENnRTdobmVLcXd6CnhGVjQvZUxSbzgrdHVEanJlbUJhUTJQaDhPUkZ6bkFzc3RaNXdaSkQ1dUFJdUd6L0hudHBQdk1uNjZqLytuTmgKbDcvOVFNaDI0YzRqU1B3PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb2dJQkFBS0NBUUVBc2d5Umd0ekxvaFhlcEhaMGdtajlHMUMrNk4vNXZndENPOXYxSEdGazNwSzBiWTlnCnRmR2duOFFRaFJzRXVoYUk5ZmpsZWkzY3lOd29XUm1JblpsL24rckhFNFVDKzFodmV3SGxIZy82MWFVdkV0dU0KOXViOHpnM01ESzNJR2oyTEdsZTN6Y1FORmlFaG14NElaeFExU2ZWM1VqSG1iNFVaSksxSjk3alRzN2V2NHppWApWQzVLdFhqNGR0cEU0akNxZjQyT3lWNE85NnhabzVTVzk4R01ZcC9tclAzbVpVWFNQSGt0ZnZtbGVxZ3lKeG03CnV3WXJSQlZZVVQwUEY2b0haZjZpTTZ5QmRwTlRrcXdlc01sYldqRVZFZFdhM2d2SUlaUERBS0RjVmRRaG13SGQKQkNqSXovNG1iZDFoZm1XR3FFNlhNWFc0My95Q3d1WkN2OHJLMFFJREFRQUJBb0lCQUJwK2RFaWN3bEJrSUxVbwpTejM4a1cwM0hyRllZcms4dzZaVW5LeVVjWVlOSG53UEViMEJMMzJXbHo2M1BvVFNSWjhVWWxGRDhjNlJ0QTlPCkZWNGVNVGVDb0F6dmhmb1F0c1gvQ2pEbS85UTZ1RDUrSFFQQWEyM2Q3N2NUUk90aXJRaEdkVHRSS1FGWi9MNHcKUWQvVXlma3ZaWW45a3VTVlVhQjdpTDRyNnBTYlNQNmhmQktraWZqd2FOY3N5TW9xZk5ub0ZJZVJOZ3Fxd2d1cQpEOHVMSTNlY2JFKytnTmUySkNROTNYbmtmdERWa0NoNUVIRHlwU3BPaVM2RXgxVnRqMGRhSXdUaVp4STNxRHh1ClEzTkJialJ5MFhqckkwNWhQUU1SKysrUm83YnlsQlFXQmtuM0Z2ckNFY2w5RVVaUlRqUEhUaFMrcldWYUFlSWYKVzlKZFpnRUNnWUVBNXFVT2U4TmZ1Q1dwL0hRYzA0TXpkazFLZ3d5OFd1bmFJT3MyNHJoNjZVWmprN0Y1cEUvYQpoVDBJSTJBaURPRGpmMWh1MXkwTTZibFVDc1NpcXdLQ28wR0d2WnMrOU55WlBOMFhtQ0EvOTlVUG5HRzI1OE5RCjI4U1lCL05COWZRRjVtbFY3NDNDRzhYcHVITUZhS0ZrVHoxZnlFKzVFUThtMEVnZkJwMWhINGtDZ1lFQXhaOVYKVEdPam5CUU5HYUg5RTRaaWRDSXIvR3BlSkxvQnhRd05MaDFqT1dkcjVKNW91MDRsNVp4NW10S090R1JQc3FZYQpsOWxKRzlJUGkxNTBiNU05aDB0K0lZWUR6NjdORlNIR0Z6aHFST29lS25lQnRteTVYVHdKMDhyY205QlFrUjlZCmZmTExkSCtvSi9RblNGNFhrWlo0VUk5L3NtdWdZQXhJQmgzNGR3a0NnWUFEY3V4b2hWOWxEWXNoTDB0UERtTXkKbmExRGtHa3dvdGFVTDNBK3E2dUsyWGFidXNlcTRWYlBMejV6NlBnWllUT0ZyL2pZVnVBZWpwcm5IbEdnWlFVMwpFNy9FRGhJKzd4MkxmM0xlMzN5VlpDWTduR3B6eE1Qc3hWL1FucDZaNHZCRHBjZVhNWE41bnRnRDNoUnlvQmN6CjZDTUtoOGFvcnFWUjhBSW13eXUwb1FLQmdCTlVORG1XZlVna3hlczk1c3prRmZrWjVvZDN0K0dMdCtTWCt5b0oKZ2N6NWlwbi96R3FWaUN0ZkZKM0ovbDh5ZUlFV3NmOHNKM1JySlU0U1hQMFV2NjNkK21ZNC8ySnV6R3hHczJOTwpCMGJhUnowTUYwbktkSTdqOG1vZXExa3FGTmM4NDZEZUFIeFNpQlh3VVc5SWxMR09zQkhoRnpKU1NJdGNhQ2NCCkEyNVJBb0dBRW5pUDQwVjExNnVibThPTjFua3Z6NmpzRFdGdDdaTllBdDQ1cE9oN2lYNnh6UC9IZ0VtWjJ4b2wKeFVYekJueXpDSHZkVk1IQjI0bXYzYVhLcWtvTlY0elJmbHlyVG9neVhzQlAzQ0hmYzcwM29ONXVQK3BzVDVnVQpzRkN4TDlwQ0V4NVBxWTdYNDVJZ0VHNE9Dc2FUS3JBeDFtZmZOVnkraWhnQ3VFYjU4dkE9Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
修改kctest,修改当前上下文为contexttest:current-context: "contexttest"。
[root@k8scloude1 safe]# vim kctest
[root@k8scloude1 safe]# cat kctest
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeU1ERXdPVEE0TVRnd01Wb1hEVE15TURFd056QTRNVGd3TVZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTEZyCkRxb2YyV2twdDJ1a2xSWnljRHQyQ2xmYnNXdTBhb256NW1rTG5IaThlZFdJbkdWR09tMllxV0x2V20yRGFrYWYKSk9oNmtRU0wyYjBXZjBRbnZaMklIQ0hBYm5lTmI0NEpIaHVTL2MxU285d2VNQm5GNk9ZRjU2Qkk4dnlSamJhZgoyVXBQSUhNZTlYcitmZTYvRHRmTGFwOERkSFlCWGFPWlpZcDZIaGEyU1JWSjg4cmJRbzJuWnV6Ykl5bWdMUnpSCnpwdE9TRVpBa1JUMzRkZmF4bm0yM3hVNG9vSnRDRWhjZVNjZ3QvZ0szOFRXMmJkRmIzU1c2UWdNc0FFOG4yVXQKaDR4c203TDVla29kTHU1N2VmWHhNZTVKTU5yTXBIL0h5M3BHSlpab0NYbG5rbm9ML2EzdTBHKzgzak8zcXRzWgp0M004TDdDcTc5Qm5BQW41aS8wQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNTWd0NGZKTWhDa0s2NGF1WWNML1VlUEs5OVBNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDcFVtSittNk9nNFZuQjBSNWpxd05EakJxZ0pQVWtONHB1MFFURlg1WWs4NGFOMnQvYgpKWTFTQ3hnR2h5Q1JERVA1U0NUMXZrdHRqaFpVVnArZjdZUnE3V1BXK0JQcWE3Nm5TUlEydUkxRHoxVDhZSGNnCi9CRkNadWIwQVZ4Y0Z1RTdSb1NkbjFDOTlqaERjUCtIRW9zRFl6dUYzZmo4QzlCMkl6d3ZIaHpaUDAvVlZSRDcKay9wWk5ub3hRdHNoWHdvVnhYS1BacHNGMHhvL1ppcUVoa2ZIYURMVC9MZE5qYXhyTjNOcFRhbTNTV2tyelZ6VQpKWGpyL0xKbGs3THVBcVBVT1VBdHBRTDZSbTArTXVQTGw0YkxQNFhOOTZOZit0NDlHdS9LeXBabXpIQkFOMWl0CkYrN0szeXVoamQ4VVNtUE14SVdPR2JEc05sTHMzTmJ5S3RpNgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.110.130:6443
name: clustertest
contexts:
- context:
cluster: clustertest
namespace: default
user: test
name: contexttest
current-context: "contexttest"
kind: Config
preferences:
users:
- name: test
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCekNDQWUrZ0F3SUJBZ0lSQUxnZXduNXBxTzVUc1JELytpTmZua1l3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TWpBek1UZ3dOelEwTXpKYUZ3MHlNekF6TVRndwpOelEwTXpKYU1DRXhFREFPQmdOVkJBb1RCMk5yWVRJd01qQXhEVEFMQmdOVkJBTVRCSFJsYzNRd2dnRWlNQTBHCkNTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDeURKR0MzTXVpRmQ2a2RuU0NhUDBiVUw3bzMvbSsKQzBJNzIvVWNZV1Rla3JSdGoyQzE4YUNmeEJDRkd3UzZGb2oxK09WNkxkekkzQ2haR1lpZG1YK2Y2c2NUaFFMNwpXRzk3QWVVZUQvclZwUzhTMjR6MjV2ek9EY3dNcmNnYVBZc2FWN2ZOeEEwV0lTR2JIZ2huRkRWSjlYZFNNZVp2CmhSa2tyVW4zdU5PenQ2L2pPSmRVTGtxMWVQaDIya1RpTUtwL2pZN0pYZzczckZtamxKYjN3WXhpbithcy9lWmwKUmRJOGVTMSsrYVY2cURJbkdidTdCaXRFRlZoUlBROFhxZ2RsL3FJenJJRjJrMU9TckI2d3lWdGFNUlVSMVpyZQpDOGdoazhNQW9OeFYxQ0diQWQwRUtNalAvaVp0M1dGK1pZYW9UcGN4ZGJqZi9JTEM1a0sveXNyUkFnTUJBQUdqClJqQkVNQk1HQTFVZEpRUU1NQW9HQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdId1lEVlIwakJCZ3cKRm9BVXd5QzNoOGt5RUtRcnJocTVod3Y5UjQ4cjMwOHdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBS1F1SGlIagpXbWdoL29GWkg0S0h5dVRDZmhjK0w3S0JMd0M5c0U5cHQrck1LMzczODdXZU5mVDN5Y0psSE9qMU0zQ2I0M3lPCnB3RmlsZ3g3MlAwVTlzdnZybzBRZjUycUxTSUlBekNORFFvNkFNRWxtVDlYUkJ0bGxHM2ZlT0dZSGxQN3NwTEMKM3BQUWNrZkxsTU9qSVBILzhxQ08zZmNMOUNIcUkzRFVqZ0VxSUV1NTh2cnN0VFIzRjljZGN0aWdzaGlMWHBBbwpuOWpNMmRZSG0xdmh1aU9mS2VIdWllKzZIaVZZZVAyWjdieEtBKzNpVkhac0krc1lpWXhPZENnRTdobmVLcXd6CnhGVjQvZUxSbzgrdHVEanJlbUJhUTJQaDhPUkZ6bkFzc3RaNXdaSkQ1dUFJdUd6L0hudHBQdk1uNjZqLytuTmgKbDcvOVFNaDI0YzRqU1B3PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb2dJQkFBS0NBUUVBc2d5Umd0ekxvaFhlcEhaMGdtajlHMUMrNk4vNXZndENPOXYxSEdGazNwSzBiWTlnCnRmR2duOFFRaFJzRXVoYUk5ZmpsZWkzY3lOd29XUm1JblpsL24rckhFNFVDKzFodmV3SGxIZy82MWFVdkV0dU0KOXViOHpnM01ESzNJR2oyTEdsZTN6Y1FORmlFaG14NElaeFExU2ZWM1VqSG1iNFVaSksxSjk3alRzN2V2NHppWApWQzVLdFhqNGR0cEU0akNxZjQyT3lWNE85NnhabzVTVzk4R01ZcC9tclAzbVpVWFNQSGt0ZnZtbGVxZ3lKeG03CnV3WXJSQlZZVVQwUEY2b0haZjZpTTZ5QmRwTlRrcXdlc01sYldqRVZFZFdhM2d2SUlaUERBS0RjVmRRaG13SGQKQkNqSXovNG1iZDFoZm1XR3FFNlhNWFc0My95Q3d1WkN2OHJLMFFJREFRQUJBb0lCQUJwK2RFaWN3bEJrSUxVbwpTejM4a1cwM0hyRllZcms4dzZaVW5LeVVjWVlOSG53UEViMEJMMzJXbHo2M1BvVFNSWjhVWWxGRDhjNlJ0QTlPCkZWNGVNVGVDb0F6dmhmb1F0c1gvQ2pEbS85UTZ1RDUrSFFQQWEyM2Q3N2NUUk90aXJRaEdkVHRSS1FGWi9MNHcKUWQvVXlma3ZaWW45a3VTVlVhQjdpTDRyNnBTYlNQNmhmQktraWZqd2FOY3N5TW9xZk5ub0ZJZVJOZ3Fxd2d1cQpEOHVMSTNlY2JFKytnTmUySkNROTNYbmtmdERWa0NoNUVIRHlwU3BPaVM2RXgxVnRqMGRhSXdUaVp4STNxRHh1ClEzTkJialJ5MFhqckkwNWhQUU1SKysrUm83YnlsQlFXQmtuM0Z2ckNFY2w5RVVaUlRqUEhUaFMrcldWYUFlSWYKVzlKZFpnRUNnWUVBNXFVT2U4TmZ1Q1dwL0hRYzA0TXpkazFLZ3d5OFd1bmFJT3MyNHJoNjZVWmprN0Y1cEUvYQpoVDBJSTJBaURPRGpmMWh1MXkwTTZibFVDc1NpcXdLQ28wR0d2WnMrOU55WlBOMFhtQ0EvOTlVUG5HRzI1OE5RCjI4U1lCL05COWZRRjVtbFY3NDNDRzhYcHVITUZhS0ZrVHoxZnlFKzVFUThtMEVnZkJwMWhINGtDZ1lFQXhaOVYKVEdPam5CUU5HYUg5RTRaaWRDSXIvR3BlSkxvQnhRd05MaDFqT1dkcjVKNW91MDRsNVp4NW10S090R1JQc3FZYQpsOWxKRzlJUGkxNTBiNU05aDB0K0lZWUR6NjdORlNIR0Z6aHFST29lS25lQnRteTVYVHdKMDhyY205QlFrUjlZCmZmTExkSCtvSi9RblNGNFhrWlo0VUk5L3NtdWdZQXhJQmgzNGR3a0NnWUFEY3V4b2hWOWxEWXNoTDB0UERtTXkKbmExRGtHa3dvdGFVTDNBK3E2dUsyWGFidXNlcTRWYlBMejV6NlBnWllUT0ZyL2pZVnVBZWpwcm5IbEdnWlFVMwpFNy9FRGhJKzd4MkxmM0xlMzN5VlpDWTduR3B6eE1Qc3hWL1FucDZaNHZCRHBjZVhNWE41bnRnRDNoUnlvQmN6CjZDTUtoOGFvcnFWUjhBSW13eXUwb1FLQmdCTlVORG1XZlVna3hlczk1c3prRmZrWjVvZDN0K0dMdCtTWCt5b0oKZ2N6NWlwbi96R3FWaUN0ZkZKM0ovbDh5ZUlFV3NmOHNKM1JySlU0U1hQMFV2NjNkK21ZNC8ySnV6R3hHczJOTwpCMGJhUnowTUYwbktkSTdqOG1vZXExa3FGTmM4NDZEZUFIeFNpQlh3VVc5SWxMR09zQkhoRnpKU1NJdGNhQ2NCCkEyNVJBb0dBRW5pUDQwVjExNnVibThPTjFua3Z6NmpzRFdGdDdaTllBdDQ1cE9oN2lYNnh6UC9IZ0VtWjJ4b2wKeFVYekJueXpDSHZkVk1IQjI0bXYzYVhLcWtvTlY0elJmbHlyVG9neVhzQlAzQ0hmYzcwM29ONXVQK3BzVDVnVQpzRkN4TDlwQ0V4NVBxWTdYNDVJZ0VHNE9Dc2FUS3JBeDFtZmZOVnkraWhnQ3VFYjU4dkE9Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
5.5.3 使用test用户的kubeconfig文件进行认证
只要客户端机器使用kctest文件,用户test就可以连接集群clustertest了。
把kctest文件拷贝到客户端机器。
[root@k8scloude1 safe]# scp kctest 192.168.110.133:~
[root@etcd1 ~]# ls kctest
kctest
--kubeconfig指定使用的kubeconfig文件,发现用户test认证成功了,但是没有权限。
[root@etcd1 ~]# kubectl get nodes --kubeconfig=kctest
Error from server (Forbidden): nodes is forbidden: User "test" cannot list resource "nodes" in API group "" at the cluster scope
对test用户授予cluster-admin的权限,对test用户进行授权,kctest里存储的是test用户的证书和私钥,所以kctest就具备了test的权限。
[root@k8scloude1 safe]# kubectl create clusterrolebinding test --clusterrole=cluster-admin --user=test
clusterrolebinding.rbac.authorization.k8s.io/test created
对test用户授予cluster-admin的权限之后,客户端可以查看节点信息了。
[root@etcd1 ~]# kubectl get nodes --kubeconfig=kctest
NAME STATUS ROLES AGE VERSION
k8scloude1 Ready control-plane,master 68d v1.21.0
k8scloude2 Ready <none> 68d v1.21.0
k8scloude3 Ready <none> 68d v1.21.0
取消用户test的授权。
[root@k8scloude1 safe]# kubectl delete clusterrolebinding test
clusterrolebinding.rbac.authorization.k8s.io "test" deleted
取消用户test的授权之后,用户test只能认证成功,但是没有权限。
[root@etcd1 ~]# kubectl get nodes --kubeconfig=kctest
Error from server (Forbidden): nodes is forbidden: User "test" cannot list resource "nodes" in API group "" at the cluster scope
可以查看所有的集群角色绑定。
[root@k8scloude1 safe]# kubectl get clusterrolebinding
NAME ROLE AGE
calico-kube-controllers ClusterRole/calico-kube-controllers 68d
calico-node ClusterRole/calico-node 68d
cluster-admin ClusterRole/cluster-admin 68d
ingress-nginx ClusterRole/ingress-nginx 31d
ingress-nginx-admission ClusterRole/ingress-nginx-admission 31d
kubeadm:get-nodes ClusterRole/kubeadm:get-nodes 68d
kubeadm:kubelet-bootstrap ClusterRole/system:node-bootstrapper 68d
......
system:controller:endpointslice-controller ClusterRole/system:controller:endpointslice-controller 68d
system:controller:endpointslicemirroring-controller ClusterRole/system:controller:endpointslicemirroring-controller 68d
system:controller:ephemeral-volume-controller ClusterRole/system:controller:ephemeral-volume-controller 68d
system:service-account-issuer-discovery ClusterRole/system:service-account-issuer-discovery 68d
system:volume-scheduler ClusterRole/system:volume-scheduler 68d
验证test用户是否具有list当前命名空间里的 pod 的权限。
[root@k8scloude1 ~]# kubectl auth can-i list pods --as test
yes
验证test用户是否具有list命名空间kube-system里pod的权限。
[root@k8scloude1 ~]# kubectl auth can-i list pods -n kube-system --as test
yes
六.总结
本文介绍了Kubernetes(k8s)访问控制之一的用户认证。并重点介绍了base auth认证,token认证,kubeconfig认证。提供了相关代码示例。通过本文的介绍,读者可以更好地理解Kubernetes的访问控制机制,并学会如何在Kubernetes中实现用户认证。
以上是关于Kubernetes(k8s)访问控制:身份认证的主要内容,如果未能解决你的问题,请参考以下文章