rootkit检测之检测hook——iat hookinline hookeat hookidt hookirp hookssdt
Posted 将者,智、信、仁、勇、严也。
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了rootkit检测之检测hook——iat hookinline hookeat hookidt hookirp hookssdt相关的知识,希望对你有一定的参考价值。






可以看到识别inline hook的关键。


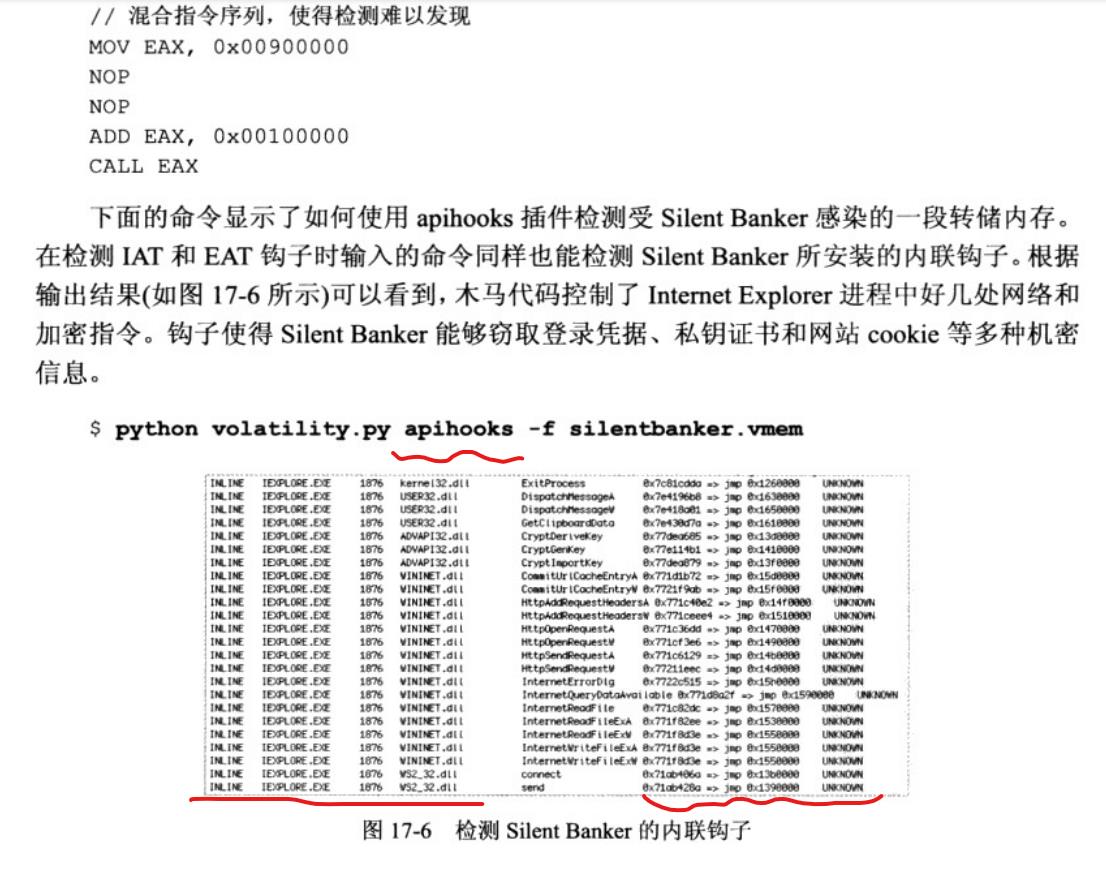
好了,我自己机器上实验下:先看下手册里介绍用法 https://downloads.volatilityfoundation.org/releases/2.4/CheatSheet_v2.4.pdf
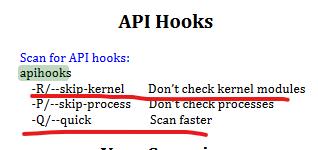
实际使用发现确实加上-R 和 -Q会快很多!输出的结果如下:
PS D:\\Application\\volatility3-stable\\moddmp_out> volatility26.exe -f D:\\book\\malwarecookbook-master\\malwarecookbook-master\\16\\6\\silentbanker.vmem\\silentbanker.vmem apihooks -R -Q >.\\hooks2.result.txt Volatility Foundation Volatility Framework 2.6 PS D:\\Application\\volatility3-stable\\moddmp_out> notepad .\\hooks2.result.txt PS D:\\Application\\volatility3-stable\\moddmp_out> volatility26 -f D:\\book\\malwarecookbook-master\\malwarecookbook-master\\17\\1\\zeus.vmem\\zeus.vmem apihooks -R -Q >hooks.result.txt Volatility Foundation Volatility Framework 2.6 PS D:\\Application\\volatility3-stable\\moddmp_out> notepad .\\hooks.result.txt
其中,zeus的hook结果:
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 676 (services.exe)
Victim module: ntdll.dll (0x7c900000 - 0x7c9b0000)
Function: ntdll.dll!NtCreateThread at 0x7c90d7d2
Hook address: 0x7e3b47
Hooking module: <unknown>
Disassembly(0):
0x7c90d7d2 e97063ed83 JMP 0x7e3b47
0x7c90d7d7 ba0003fe7f MOV EDX, 0x7ffe0300
0x7c90d7dc ff12 CALL DWORD [EDX]
0x7c90d7de c22000 RET 0x20
0x7c90d7e1 90 NOP
0x7c90d7e2 90 NOP
0x7c90d7e3 90 NOP
0x7c90d7e4 90 NOP
0x7c90d7e5 90 NOP
0x7c90d7e6 90 NOP
0x7c90d7e7 b8 DB 0xb8
0x7c90d7e8 36 DB 0x36
0x7c90d7e9 00 DB 0x0
Disassembly(1):
0x7e3b47 55 PUSH EBP
0x7e3b48 8bec MOV EBP, ESP
0x7e3b4a 83ec18 SUB ESP, 0x18
0x7e3b4d 53 PUSH EBX
0x7e3b4e 56 PUSH ESI
0x7e3b4f 57 PUSH EDI
0x7e3b50 8b7d14 MOV EDI, [EBP+0x14]
0x7e3b53 8d4514 LEA EAX, [EBP+0x14]
0x7e3b56 50 PUSH EAX
0x7e3b57 6a18 PUSH 0x18
0x7e3b59 8d45e8 LEA EAX, [EBP-0x18]
0x7e3b5c 50 PUSH EAX
0x7e3b5d 33f6 XOR ESI, ESI
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 676 (services.exe)
Victim module: ntdll.dll (0x7c900000 - 0x7c9b0000)
Function: ntdll.dll!NtQueryDirectoryFile at 0x7c90df5e
Hook address: 0x7e3ca5
Hooking module: <unknown>
Disassembly(0):
0x7c90df5e e9425ded83 JMP 0x7e3ca5
0x7c90df63 ba0003fe7f MOV EDX, 0x7ffe0300
0x7c90df68 ff12 CALL DWORD [EDX]
0x7c90df6a c22c00 RET 0x2c
0x7c90df6d 90 NOP
0x7c90df6e 90 NOP
0x7c90df6f 90 NOP
0x7c90df70 90 NOP
0x7c90df71 90 NOP
0x7c90df72 90 NOP
0x7c90df73 b8 DB 0xb8
0x7c90df74 92 XCHG EDX, EAX
0x7c90df75 00 DB 0x0
Disassembly(1):
0x7e3ca5 55 PUSH EBP ==》不在ntdll.dll (0x7c900000 - 0x7c9b0000)范围内 所以是恶意的!!!
0x7e3ca6 8bec MOV EBP, ESP
0x7e3ca8 e88bfeffff CALL 0x7e3b38
0x7e3cad ff7530 PUSH DWORD [EBP+0x30]
0x7e3cb0 ff752c PUSH DWORD [EBP+0x2c]
0x7e3cb3 ff7528 PUSH DWORD [EBP+0x28]
0x7e3cb6 ff7524 PUSH DWORD [EBP+0x24]
0x7e3cb9 ff7520 PUSH DWORD [EBP+0x20]
0x7e3cbc ff DB 0xff
。。。很多很多!!!
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: CRYPT32.dll (0x77a80000 - 0x77b14000)
Function: CRYPT32.dll!PFXImportCertStore at 0x77aef748
Hook address: 0x15d3692
Hooking module: <unknown>
Disassembly(0):
0x77aef748 e9453fae89 JMP 0x15d3692
0x77aef74d 83ec18 SUB ESP, 0x18
0x77aef750 53 PUSH EBX
0x77aef751 57 PUSH EDI
0x77aef752 33c0 XOR EAX, EAX
0x77aef754 8d7de8 LEA EDI, [EBP-0x18]
0x77aef757 33db XOR EBX, EBX
0x77aef759 f74510dcefffef TEST DWORD [EBP+0x10], 0xefffefdc
Disassembly(1):
0x15d3692 55 PUSH EBP
0x15d3693 8bec MOV EBP, ESP
0x15d3695 81ec80000000 SUB ESP, 0x80
0x15d369b 53 PUSH EBX
0x15d369c 56 PUSH ESI
0x15d369d e896040000 CALL 0x15d3b38
0x15d36a2 ff7510 PUSH DWORD [EBP+0x10]
0x15d36a5 8b7508 MOV ESI, [EBP+0x8]
0x15d36a8 ff DB 0xff
0x15d36a9 75 DB 0x75
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!HttpQueryInfoA at 0x771c8c6a
Hook address: 0x15e7477
Hooking module: <unknown>
Disassembly(0):
0x771c8c6a e908e8418a JMP 0x15e7477
0x771c8c6f 1c77 SBB AL, 0x77
0x771c8c71 e8fc89feff CALL 0x771b1672
0x771c8c76 33db XOR EBX, EBX
0x771c8c78 895ddc MOV [EBP-0x24], EBX
0x771c8c7b 895de4 MOV [EBP-0x1c], EBX
0x771c8c7e 39 DB 0x39
0x771c8c7f 1d DB 0x1d
0x771c8c80 50 PUSH EAX
0x771c8c81 98 CWDE
Disassembly(1):
0x15e7477 55 PUSH EBP
0x15e7478 8bec MOV EBP, ESP
0x15e747a 56 PUSH ESI
0x15e747b 57 PUSH EDI
0x15e747c bf6c275f01 MOV EDI, 0x15f276c
0x15e7481 57 PUSH EDI
0x15e7482 ff1574125d01 CALL DWORD [0x15d1274]
0x15e7488 8b7508 MOV ESI, [EBP+0x8]
0x15e748b e8 DB 0xe8
0x15e748c 67e5ff IN EAX, 0xff
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!HttpSendRequestA at 0x771c76b8
Hook address: 0x15e7366
Hooking module: <unknown>
Disassembly(0):
0x771c76b8 e9a9fc418a JMP 0x15e7366
0x771c76bd 6a13 PUSH 0x13
0x771c76bf 6a00 PUSH 0x0
0x771c76c1 ff7518 PUSH DWORD [EBP+0x18]
0x771c76c4 ff7514 PUSH DWORD [EBP+0x14]
0x771c76c7 ff7510 PUSH DWORD [EBP+0x10]
0x771c76ca ff750c PUSH DWORD [EBP+0xc]
0x771c76cd ff7508 PUSH DWORD [EBP+0x8]
Disassembly(1):
0x15e7366 55 PUSH EBP
0x15e7367 8bec MOV EBP, ESP
0x15e7369 e8cac7feff CALL 0x15d3b38
0x15e736e ff7510 PUSH DWORD [EBP+0x10]
0x15e7371 8b4518 MOV EAX, [EBP+0x18]
0x15e7374 ff750c PUSH DWORD [EBP+0xc]
0x15e7377 8b4d14 MOV ECX, [EBP+0x14]
0x15e737a ff7508 PUSH DWORD [EBP+0x8]
0x15e737d 6a DB 0x6a
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!HttpSendRequestExA at 0x7721190d
Hook address: 0x15e73ac
Hooking module: <unknown>
Disassembly(0):
0x7721190d e99a5a3d8a JMP 0x15e73ac
0x77211912 53 PUSH EBX
0x77211913 56 PUSH ESI
0x77211914 57 PUSH EDI
0x77211915 33db XOR EBX, EBX
0x77211917 33c0 XOR EAX, EAX
0x77211919 33c9 XOR ECX, ECX
0x7721191b 33d2 XOR EDX, EDX
0x7721191d 33ff XOR EDI, EDI
0x7721191f 395d10 CMP [EBP+0x10], EBX
0x77211922 7539 JNZ 0x7721195d
0x77211924 8b DB 0x8b
Disassembly(1):
0x15e73ac 55 PUSH EBP
0x15e73ad 8bec MOV EBP, ESP
0x15e73af 53 PUSH EBX
0x15e73b0 e883c7feff CALL 0x15d3b38
0x15e73b5 ff7518 PUSH DWORD [EBP+0x18]
0x15e73b8 8b450c MOV EAX, [EBP+0xc]
0x15e73bb ff7514 PUSH DWORD [EBP+0x14]
0x15e73be 8b5d08 MOV EBX, [EBP+0x8]
0x15e73c1 ff7510 PUSH DWORD [EBP+0x10]
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!HttpSendRequestExW at 0x771d53eb
Hook address: 0x15e7388
Hooking module: <unknown>
Disassembly(0):
0x771d53eb e9981f418a JMP 0x15e7388
0x771d53f0 83ec14 SUB ESP, 0x14
0x771d53f3 53 PUSH EBX
0x771d53f4 56 PUSH ESI
0x771d53f5 33c0 XOR EAX, EAX
0x771d53f7 57 PUSH EDI
0x771d53f8 33d2 XOR EDX, EDX
0x771d53fa 33db XOR EBX, EBX
0x771d53fc 33ff XOR EDI, EDI
0x771d53fe 33c9 XOR ECX, ECX
0x771d5400 395508 CMP [EBP+0x8], EDX
Disassembly(1):
0x15e7388 55 PUSH EBP
0x15e7389 8bec MOV EBP, ESP
0x15e738b 53 PUSH EBX
0x15e738c e8a7c7feff CALL 0x15d3b38
0x15e7391 ff7518 PUSH DWORD [EBP+0x18]
0x15e7394 8b450c MOV EAX, [EBP+0xc]
0x15e7397 ff7514 PUSH DWORD [EBP+0x14]
0x15e739a 8b5d08 MOV EBX, [EBP+0x8]
0x15e739d ff7510 PUSH DWORD [EBP+0x10]
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!HttpSendRequestW at 0x77211808
Hook address: 0x15e7344
Hooking module: <unknown>
Disassembly(0):
0x77211808 e9375b3d8a JMP 0x15e7344
0x7721180d 83ec14 SUB ESP, 0x14
0x77211810 53 PUSH EBX
0x77211811 33db XOR EBX, EBX
0x77211813 56 PUSH ESI
0x77211814 33f6 XOR ESI, ESI
0x77211816 33c0 XOR EAX, EAX
0x77211818 395d08 CMP [EBP+0x8], EBX
0x7721181b 57 PUSH EDI
0x7721181c 895df8 MOV [EBP-0x8], EBX
0x7721181f 89 DB 0x89
Disassembly(1):
0x15e7344 55 PUSH EBP
0x15e7345 8bec MOV EBP, ESP
0x15e7347 e8ecc7feff CALL 0x15d3b38
0x15e734c ff7510 PUSH DWORD [EBP+0x10]
0x15e734f 8b4518 MOV EAX, [EBP+0x18]
0x15e7352 ff750c PUSH DWORD [EBP+0xc]
0x15e7355 8b4d14 MOV ECX, [EBP+0x14]
0x15e7358 ff7508 PUSH DWORD [EBP+0x8]
0x15e735b 6a DB 0x6a
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!InternetCloseHandle at 0x771c61dc
Hook address: 0x15e7438
Hooking module: <unknown>
Disassembly(0):
0x771c61dc e95712428a JMP 0x15e7438
0x771c61e1 51 PUSH ECX
0x771c61e2 51 PUSH ECX
0x771c61e3 53 PUSH EBX
0x771c61e4 56 PUSH ESI
0x771c61e5 33db XOR EBX, EBX
0x771c61e7 33f6 XOR ESI, ESI
0x771c61e9 f60544a3237701 TEST BYTE [0x7723a344], 0x1
0x771c61f0 895dfc MOV [EBP-0x4], EBX
0x771c61f3 0f DB 0xf
Disassembly(1):
0x15e7438 53 PUSH EBX
0x15e7439 56 PUSH ESI
0x15e743a 57 PUSH EDI
0x15e743b e8f8c6feff CALL 0x15d3b38
0x15e7440 8b742410 MOV ESI, [ESP+0x10]
0x15e7444 56 PUSH ESI
0x15e7445 ff153c145d01 CALL DWORD [0x15d143c]
0x15e744b bf6c275f01 MOV EDI, 0x15f276c
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!InternetQueryDataAvailable at 0x771d325f
Hook address: 0x15e7415
Hooking module: <unknown>
Disassembly(0):
0x771d325f e9b141418a JMP 0x15e7415
0x771d3264 83ec10 SUB ESP, 0x10
0x771d3267 53 PUSH EBX
0x771d3268 33db XOR EBX, EBX
0x771d326a 391d50982377 CMP [0x77239850], EBX
0x771d3270 56 PUSH ESI
0x771d3271 57 PUSH EDI
0x771d3272 895dfc MOV [EBP-0x4], EBX
0x771d3275 c7 DB 0xc7
0x771d3276 45 INC EBP
Disassembly(1):
0x15e7415 e81ec7feff CALL 0x15d3b38
0x15e741a ff742410 PUSH DWORD [ESP+0x10]
0x15e741e ff742410 PUSH DWORD [ESP+0x10]
0x15e7422 ff742410 PUSH DWORD [ESP+0x10]
0x15e7426 6a00 PUSH 0x0
0x15e7428 6a00 PUSH 0x0
0x15e742a ff DB 0xff
0x15e742b 7424 JZ 0x15e7451
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!InternetReadFile at 0x771c9555
Hook address: 0x15e73d0
Hooking module: <unknown>
Disassembly(0):
0x771c9555 e976de418a JMP 0x15e73d0
0x771c955a 83ec24 SUB ESP, 0x24
0x771c955d 53 PUSH EBX
0x771c955e 33db XOR EBX, EBX
0x771c9560 391d50982377 CMP [0x77239850], EBX
0x771c9566 57 PUSH EDI
0x771c9567 895df4 MOV [EBP-0xc], EBX
0x771c956a 895df8 MOV [EBP-0x8], EBX
Disassembly(1):
0x15e73d0 e863c7feff CALL 0x15d3b38
0x15e73d5 33c0 XOR EAX, EAX
0x15e73d7 50 PUSH EAX
0x15e73d8 50 PUSH EAX
0x15e73d9 ff742418 PUSH DWORD [ESP+0x18]
0x15e73dd ff742418 PUSH DWORD [ESP+0x18]
0x15e73e1 ff742418 PUSH DWORD [ESP+0x18]
0x15e73e5 ff DB 0xff
0x15e73e6 7424 JZ 0x15e740c
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WININET.dll (0x771b0000 - 0x77256000)
Function: WININET.dll!InternetReadFileExA at 0x771f7e9a
Hook address: 0x15e73f2
Hooking module: <unknown>
Disassembly(0):
0x771f7e9a e953f53e8a JMP 0x15e73f2
0x771f7e9f 83ec20 SUB ESP, 0x20
0x771f7ea2 53 PUSH EBX
0x771f7ea3 56 PUSH ESI
0x771f7ea4 33c0 XOR EAX, EAX
0x771f7ea6 57 PUSH EDI
0x771f7ea7 33ff XOR EDI, EDI
0x771f7ea9 40 INC EAX
0x771f7eaa 393d50982377 CMP [0x77239850], EDI
0x771f7eb0 89 DB 0x89
0x771f7eb1 7d DB 0x7d
Disassembly(1):
0x15e73f2 e841c7feff CALL 0x15d3b38
0x15e73f7 ff742410 PUSH DWORD [ESP+0x10]
0x15e73fb ff742410 PUSH DWORD [ESP+0x10]
0x15e73ff 6a00 PUSH 0x0
0x15e7401 6a00 PUSH 0x0
0x15e7403 ff742418 PUSH DWORD [ESP+0x18]
0x15e7407 ff DB 0xff
0x15e7408 7424 JZ 0x15e742e
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WS2_32.dll (0x71ab0000 - 0x71ac7000)
Function: WS2_32.dll!WSASend at 0x71ab6233
Hook address: 0x15e112c
Hooking module: <unknown>
Disassembly(0):
0x71ab6233 e9f4aeb28f JMP 0x15e112c
0x71ab6238 51 PUSH ECX
0x71ab6239 51 PUSH ECX
0x71ab623a 813d2840ac714894ab71 CMP DWORD [0x71ac4028], 0x71ab9448
0x71ab6244 56 PUSH ESI
0x71ab6245 0f847f540000 JZ 0x71abb6ca
Disassembly(1):
0x15e112c 55 PUSH EBP
0x15e112d 8bec MOV EBP, ESP
0x15e112f 837d1000 CMP DWORD [EBP+0x10], 0x0
0x15e1133 56 PUSH ESI
0x15e1134 8b750c MOV ESI, [EBP+0xc]
0x15e1137 7615 JBE 0x15e114e
0x15e1139 57 PUSH EDI
0x15e113a 8b7d10 MOV EDI, [EBP+0x10]
0x15e113d ff36 PUSH DWORD [ESI]
0x15e113f 8b4604 MOV EAX, [ESI+0x4]
0x15e1142 ff DB 0xff
0x15e1143 75 DB 0x75
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WS2_32.dll (0x71ab0000 - 0x71ac7000)
Function: WS2_32.dll!closesocket at 0x71ab9639
Hook address: 0x15e10db
Hooking module: <unknown>
Disassembly(0):
0x71ab9639 e99d7ab28f JMP 0x15e10db
0x71ab963e 51 PUSH ECX
0x71ab963f 813d2840ac714894ab71 CMP DWORD [0x71ac4028], 0x71ab9448
0x71ab9649 56 PUSH ESI
0x71ab964a 0f84aef3ffff JZ 0x71ab89fe
0x71ab9650 e8 DB 0xe8
Disassembly(1):
0x15e10db 56 PUSH ESI
0x15e10dc bef4265f01 MOV ESI, 0x15f26f4
0x15e10e1 56 PUSH ESI
0x15e10e2 ff1574125d01 CALL DWORD [0x15d1274]
0x15e10e8 ff742408 PUSH DWORD [ESP+0x8]
0x15e10ec e859fcffff CALL 0x15e0d4a
0x15e10f1 85c0 TEST EAX, EAX
************************************************************************
Hook mode: Usermode
Hook type: Inline/Trampoline
Process: 1724 (explorer.exe)
Victim module: WS2_32.dll (0x71ab0000 - 0x71ac7000)
Function: WS2_32.dll!send at 0x71ab428a
Hook address: 0x15e110f
Hooking module: <unknown>
Disassembly(0):
0x71ab428a e980ceb28f JMP 0x15e110f
0x71ab428f 83ec10 SUB ESP, 0x10
0x71ab4292 56 PUSH ESI
0x71ab4293 57 PUSH EDI
0x71ab4294 33ff XOR EDI, EDI
0x71ab4296 813d2840ac714894ab71 CMP DWORD [0x71ac4028], 0x71ab9448
0x71ab42a0 0f DB 0xf
0x71ab42a1 84 DB 0x84
Disassembly(1):
0x15e110f 55 PUSH EBP
0x15e1110 8bec MOV EBP, ESP
0x15e1112 ff7510 PUSH DWORD [EBP+0x10]
0x15e1115 8b450c MOV EAX, [EBP+0xc]
0x15e1118 ff7508 PUSH DWORD [EBP+0x8]
0x15e111b e838fdffff CALL 0x15e0e58
0x15e1120 e8132affff CALL 0x15d3b38
0x15e1125 5d POP EBP
0x15e1126 ff DB 0xff
zeus这个恶意软件作者也是蛋疼,挂了那么多hook!!!不过iat和eat的hook,我看到两个恶意软件都没有体现。并且由于使用了vol26的版本,输出也和书中有很大的出入。
idt hook、irp hook、ssdt这几个比较少见,并且仅有ssdt作者提供了可以操作的vmem。可以参考原书,我就只是截图示意下volatility的用法:
IDT的见原书吧,这里不写了。
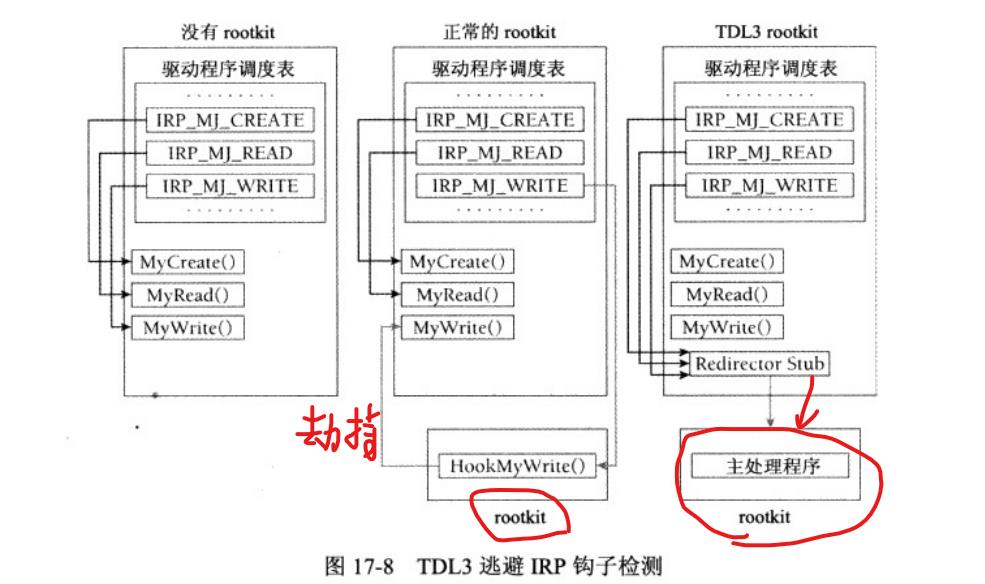
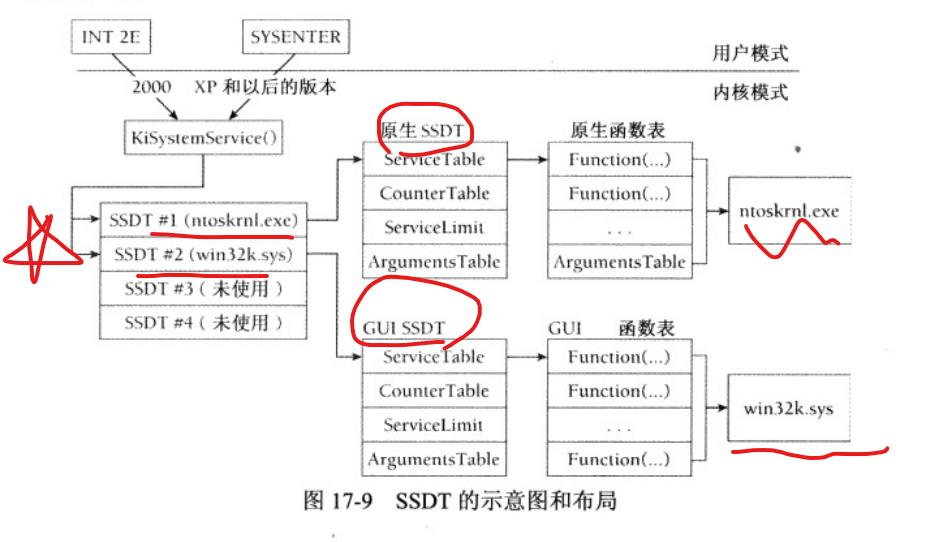

ssdt本质上也是劫持!!!
我本机的输出:
PS D:\\Application\\volatility3-stable\\moddmp_out> volatility26.exe -f "D:\\book\\malwarecookbook-master\\malwarecookbook-master\\17\\6\\be2.vmem\\be2.vmem" ssdt | grep -E -v "(ntoskrnl|win32k)" Volatility Foundation Volatility Framework 2.6 [x86] Gathering all referenced SSDTs from KTHREADs... Finding appropriate address space for tables... SSDT[0] at ff3aab90 with 284 entries Entry 0x0041: 0xff0d2487 (NtDeleteValueKey) owned by 00004A2A Entry 0x0047: 0xff0d216b (NtEnumerateKey) owned by 00004A2A Entry 0x0049: 0xff0d2267 (NtEnumerateValueKey) owned by 00004A2A Entry 0x0077: 0xff0d20c3 (NtOpenKey) owned by 00004A2A Entry 0x007a: 0xff0d1e93 (NtOpenProcess) owned by 00004A2A Entry 0x0080: 0xff0d1f0b (NtOpenThread) owned by 00004A2A Entry 0x0089: 0xff0d2617 (NtProtectVirtualMemory) owned by 00004A2A Entry 0x00ad: 0xff0d1da0 (NtQuerySystemInformation) owned by 00004A2A Entry 0x00ba: 0xff0d256b (NtReadVirtualMemory) owned by 00004A2A Entry 0x00d5: 0xff0d2070 (NtSetContextThread) owned by 00004A2A Entry 0x00f7: 0xff0d2397 (NtSetValueKey) owned by 00004A2A Entry 0x00fe: 0xff0d201d (NtSuspendThread) owned by 00004A2A Entry 0x0102: 0xff0d1fca (NtTerminateThread) owned by 00004A2A Entry 0x0115: 0xff0d25c1 (NtWriteVirtualMemory) owned by 00004A2A SSDT[0] at 80f162d0 with 284 entries Entry 0x0041: 0xff0d2487 (NtDeleteValueKey) owned by 00004A2A Entry 0x0047: 0xff0d216b (NtEnumerateKey) owned by 00004A2A Entry 0x0049: 0xff0d2267 (NtEnumerateValueKey) owned by 00004A2A Entry 0x0077: 0xff0d20c3 (NtOpenKey) owned by 00004A2A Entry 0x007a: 0xff0d1e93 (NtOpenProcess) owned by 00004A2A Entry 0x0080: 0xff0d1f0b (NtOpenThread) owned by 00004A2A Entry 0x0089: 0xff0d2617 (NtProtectVirtualMemory) owned by 00004A2A Entry 0x00ad: 0xff0d1da0 (NtQuerySystemInformation) owned by 00004A2A Entry 0x00ba: 0xff0d256b (NtReadVirtualMemory) owned by 00004A2A Entry 0x00d5: 0xff0d2070 (NtSetContextThread) owned by 00004A2A Entry 0x00f7: 0xff0d2397 (NtSetValueKey) owned by 00004A2A Entry 0x00fe: 0xff0d201d (NtSuspendThread) owned by 00004A2A Entry 0x0102: 0xff0d1fca (NtTerminateThread) owned by 00004A2A Entry 0x0115: 0xff0d25c1 (NtWriteVirtualMemory) owned by 00004A2A SSDT[0] at 80501030 with 284 entries SSDT[1] at bf997600 with 667 entries
不加过滤呢?输出就是一大篇的正常exe:
Entry 0x0024: 0x8060bb94 (NtCreateEventPair) owned by ntoskrnl.exe Entry 0x0025: 0x8056d14c (NtCreateFile) owned by ntoskrnl.exe Entry 0x0026: 0x8056b9de (NtCreateIoCompletion) owned by ntoskrnl.exe Entry 0x0027: 0x805ca126 (NtCreateJobObject) owned by ntoskrnl.exe Entry 0x0028: 0x805c9e5e (NtCreateJobSet) owned by ntoskrnl.exe Entry 0x0029: 0x80618bd2 (NtCreateKey) owned by ntoskrnl.exe Entry 0x002a: 0x8056d25a (NtCreateMailslotFile) owned by ntoskrnl.exe Entry 0x002b: 0x8060bf8c (NtCreateMutant) owned by ntoskrnl.exe Entry 0x002c: 0x8056d186 (NtCreateNamedPipeFile) owned by ntoskrnl.exe Entry 0x002d: 0x8059f8fa (NtCreatePagingFile) owned by ntoskrnl.exe Entry 0x002e: 0x80598f56 (NtCreatePort) owned by ntoskrnl.exe Entry 0x002f: 0x805c5ce8 (NtCreateProcess) owned by ntoskrnl.exe Entry 0x0030: 0x805c5c32 (NtCreateProcessEx) owned by ntoskrnl.exe Entry 0x0031: 0x8060c3ac (NtCreateProfile) owned by ntoskrnl.exe Entry 0x0032: 0x8059f23e (NtCreateSection) owned by ntoskrnl.exe Entry 0x0033: 0x80609936 (NtCreateSemaphore) owned by ntoskrnl.exe Entry 0x0034: 0x805b9410 (NtCreateSymbolicLinkObject) owned by ntoskrnl.exe Entry 0x0035: 0x805c5ad0 (NtCreateThread) owned by ntoskrnl.exe Entry 0x0036: 0x8060b85c (NtCreateTimer) owned by ntoskrnl.exe Entry 0x0037: 0x805edc98 (NtCreateToken) owned by ntoskrnl.exe Entry 0x0038: 0x80598f7a (NtCreateWaitablePort) owned by ntoskrnl.exe Entry 0x0039: 0x80637ac4 (NtDebugActiveProcess) owned by ntoskrnl.exe Entry 0x003a: 0x80637c14 (NtDebugContinue) owned by ntoskrnl.exe Entry 0x003b: 0x8060b26e (NtDelayExecution) owned by ntoskrnl.exe Entry 0x003c: 0x8060aa90 (NtDeleteAtom) owned by ntoskrnl.exe Entry 0x003d: 0x805bce0e (NtDeleteBootEntry) owned by ntoskrnl.exe Entry 0x003e: 0x8056ad2c (NtDeleteFile) owned by ntoskrnl.exe 。。。。
一点一滴,成材之基! Linux后门Trojan Horse检测工具
目录:(一)Trojan Horse后门工具了解
(二)rootkit后门检测工具chkrootkit
(三)rootkit后门检测工具RKHunter
(一)Trojan Horse后门工具了解
(1.1)rootkit是Linux平台下最常见的一种Trojan Horse后门工具,它主要通过替换系统文件来达到attack和隐蔽的目的,这种Trojan Horse比普通Trojan Horse后门更加危险和隐蔽,普通的监测工具和检查手段很难发现这种Trojan Horse。rootkit的 accuse能力极强,对系统的危害很大,它通过一套工具来建立后门和隐藏行迹,从而让 accuse者保住权限,以使它在任何时候都可以使用root权限登录到系统。
(1.2)rootkit主要有两种类型:文件级别和内核级别,下面分别进行简单介绍。
(1.2.1)文件级别的rootkit一般是通过程序漏洞或者系统漏洞进入系统后,通过修改系统的重要文件来达到隐藏自己的目的。在系统遭受rootkit的 accuse后,合法的文件被Trojan Horse程序替代,变成了外壳程序,而其内部是隐藏着的后门程序。通常容易被rootkit替换的系统程序有login、ls、ps、ifconfig、du、find、netstat等,其中login程序是最经常被替换的,因为当访问Linux时,无论是通过本地登录还是远程登录,/bin/login程序都会运行,系统将通过/bin/login来收集并核对用户的账号和密码,而rootkit就是利用这个程序的特点,使用一个带有权限后门密码的/bin/login来替换系统的/bin/login,这样accuse者通过输入设定好的密码就能轻松进入系统。此时,即使系统管理员修改root密码或者清除root密码,accuse者还是一样能通过root用户登录系统。accuse者通常在进入Linux系统后,会进行一系列的accuse动作,最常见的是安装嗅探器收集本机或者网络中其他服务器的重要数据。在默认情况下,Linux中也有一些文件系统会监控这些工具动作,例如ifconfig命令,所以,accuse者为了避免被发现,会想方设法替换其他文件系统,常见的就是ls、ps、ifconfig、du、find、netstat等。如果这些文件都被替换,那么在系统层面就很难发现rootkit已经在系统中运行了。这就是文件级别的rootkit,对系统危害很大,目前最有效的防御方法是定期对系统重要文件的完整性进行检查,如果发现文件被修改或者被替换,那么很可能系统已经遭受了rootkit的attack。检查文件完整性的工具很多,常见的有Tripwire、aide等,可以通过这些工具定期检查文件系统的完整性,以检测系统是否被rootkit的attack。
(1.2.2)内核级rootkit是比文件级rootkit更高级的一种attack方式,它可以使accuse者获得对系统底层的完全控制权,此时accuse者可以修改系统内核,进而截获运行程序向内核提交的命令,并将其重定向到attack者所选择的程序并运行此程序,也就是说,当用户要运行程序A时,被attack者修改过的内核会假装执行A程序,而实际上却执行了程序B。内核级rootkit主要依附在内核上,它并不对系统文件做任何修改,因此一般的监测工具很难检测到它的存在,这样一旦系统内核被植入rootkit,accuse者就可以对系统为所欲为而不被发现。目前对于内核级的rootkit还没有很好的防御工具,因此,做好系统安全防范就非常重要,将系统维持在最小权限内工作,只要accuse者不能获取root权限,就无法在内核中植入rootkit。
(二)rootkit后门检测工具chkrootkit
(2.1)chkrootkit是一个Linux系统下查找并检测rootkit后门的工具,chkrootkit没有包含在官方的CentOS源中,因此要采取手动编译的方法来安装,不过这种安装方法更加安全,chkrootkit的使用比较简单,直接执行chkrootkit命令即可自动开始检测系统。
(2.2)在vms001主机上首先安装gcc、gcc-c++、make等软件,接着安装Development Tools工具软件,并进入到/usr/local/src/目录中解压缩chkrootkit软件。
# yum install gcc gcc-c++ make -y
# yum groupinstall Development Tools -y
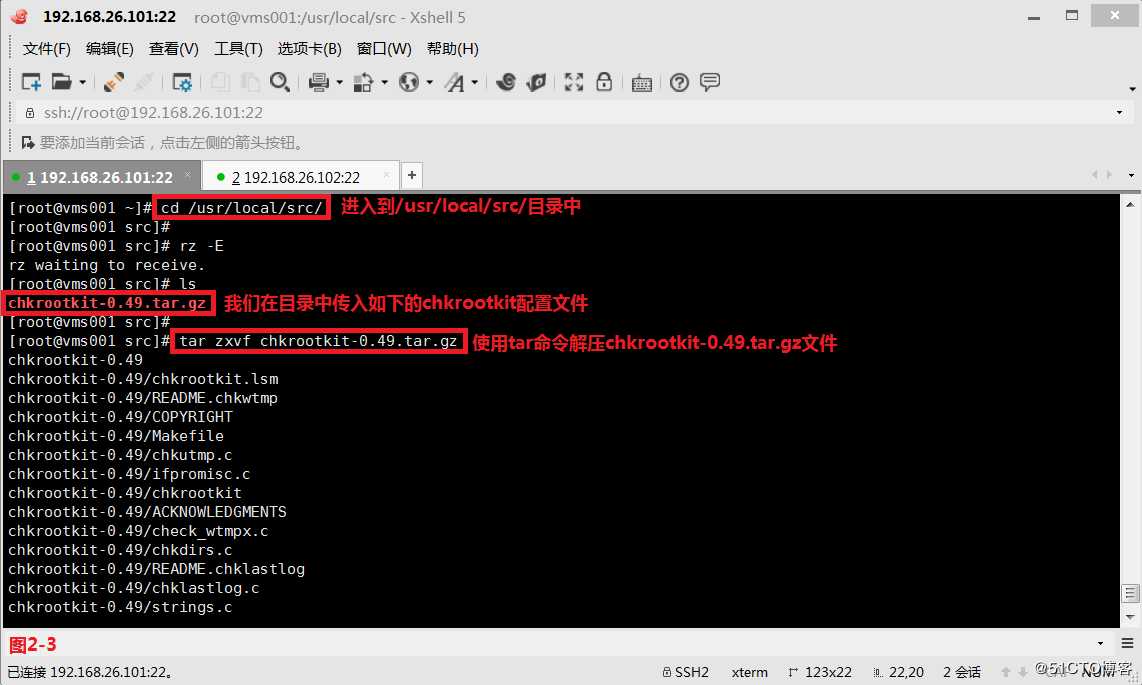
# cd /usr/local/src/---进入到/usr/local/src/目录中
# tar zxvf chkrootkit-0.49.tar.gz---在目录中解压chkrootkit软件包
(2.3)接着我们进入到chkrootkit-0.49/目录中,并执行make命令安装软件。
# make sense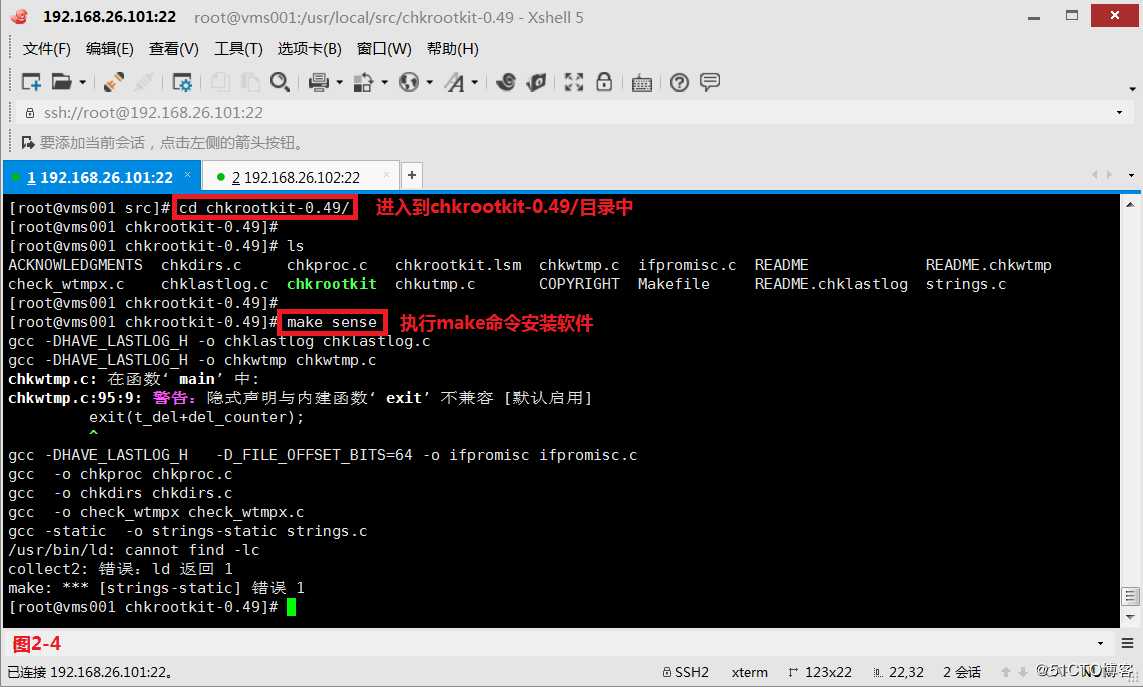
(2.4)我们在系统中运行chkrootkit命令,一旦有INFECTED,说明可能被植入了rootkit
# ./chkrootkit | grep INFECTED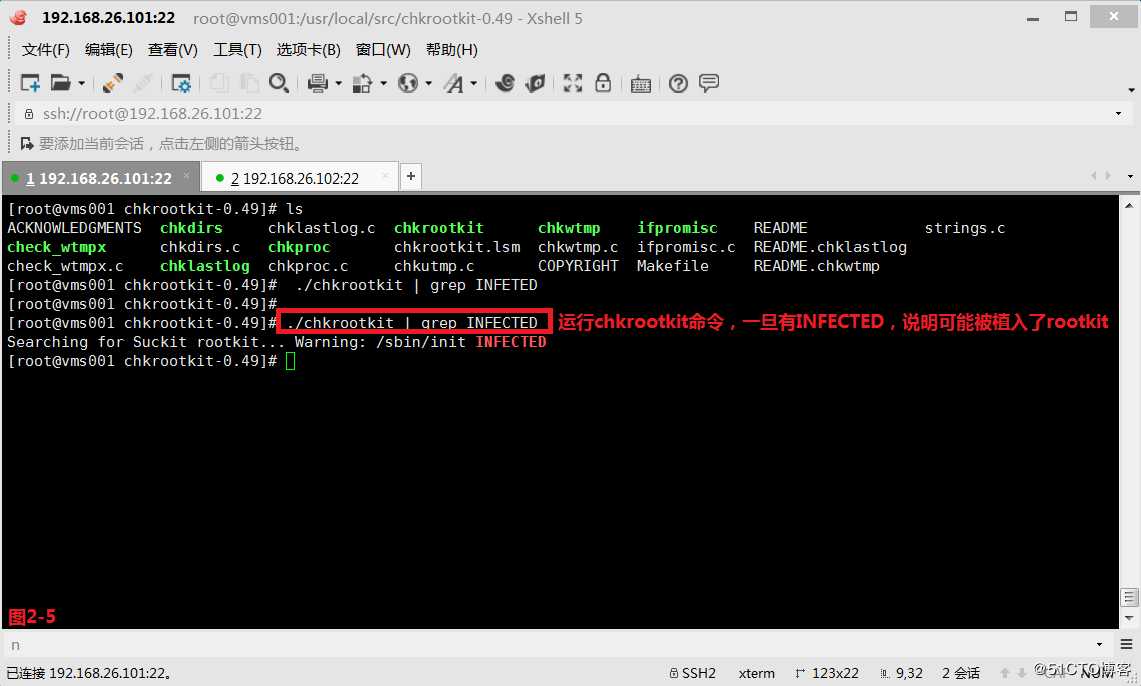
(2.5)我们直接执行chkrootkit可执行文件,从输出可以看出,此系统的常用执行命令并没有感染rootkit的Trojan Horse,不过对于系统来说最安全而有效的方法就是备份数据重新安装系统。
# ./chkrootkit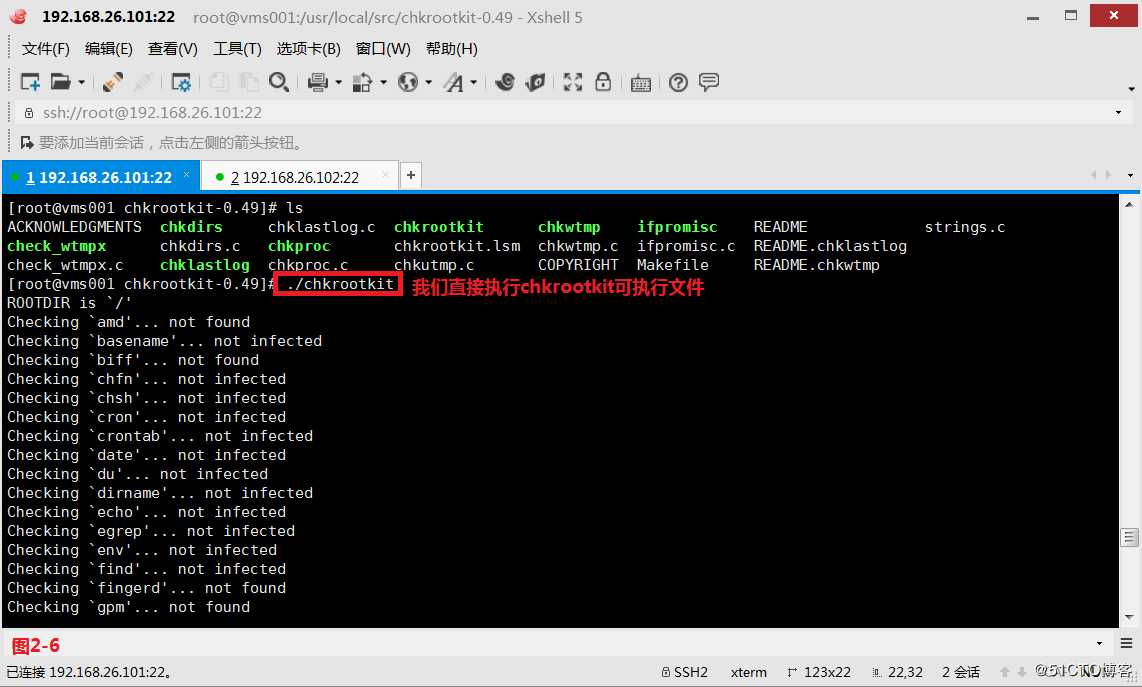
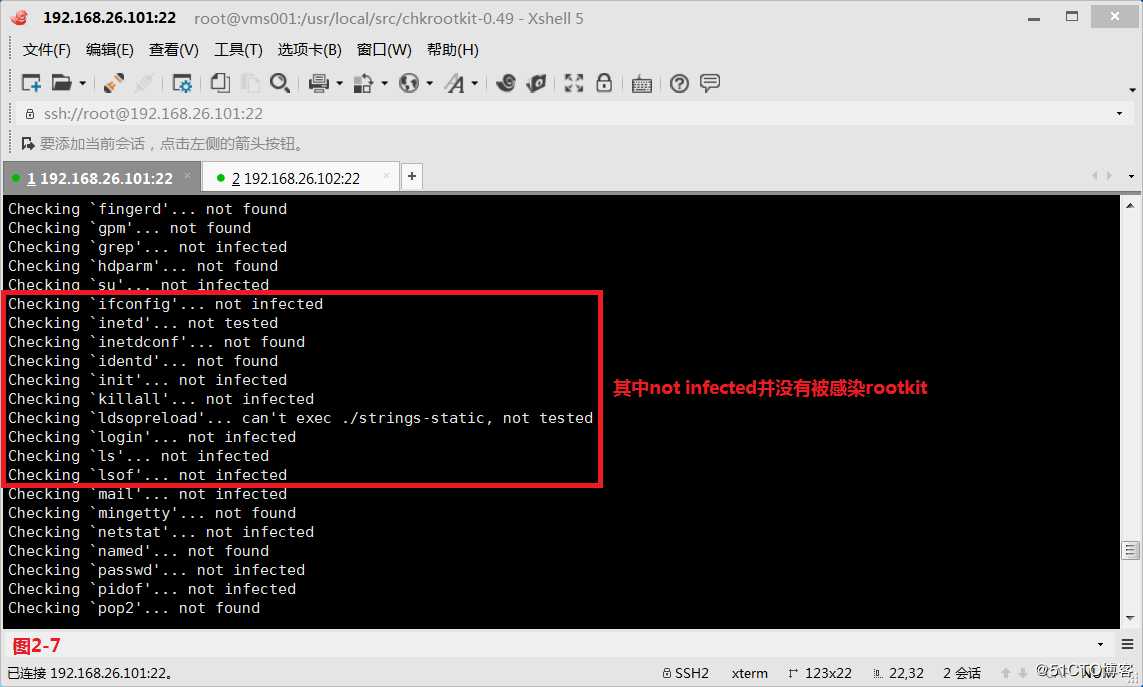
(2.6)chkrootkit在检查rootkit的过程中使用了部分系统命令,因此,如果服务器被hacker attacks,那么依赖的系统命令可能也已经被attack者替换,此时chkrootkit的监测结果将变得完全不可信。为了避免chkrootkit的这个问题,可以在服务器对外开放前,事先将chkrootkit使用的系统命令进行备份,在需要的时候使用备份的原始系统命令让chkrootkit对rootkit进行检测。
(三)rootkit后门检测工具RKHunter
(3.1)RKHunter是一款专业的检测系统是否感染rootkit的工具,它通过执行一系列的脚本来确认服务器是否已经感染rootkit。在官方的资料中,RKHunter主要执行下面一系列的测试:①MD5校验测试,检测任何文件是否改动;②检测rootkit使用的二进制和系统工具文件;③检测特洛伊Trojan Horse程序的特征码;④检测大多常用程序的文件异常属性;⑤执行一些系统相关的测试,因为RKHunter可支持多个系统平台;⑥扫描任何混杂模式下的接口和后门程序常用的端口;⑦检测如/etc/rc.d/目录下的所有配置文件、日志文件、任何异常的隐藏文件等等,例如在检测/dev/.udev和/etc/.pwd.lock文件时候,系统被警告;⑧对一些使用常用端口的应用程序进行版本测试,如:Apache Web Server,Postfix等;⑨检测网络。
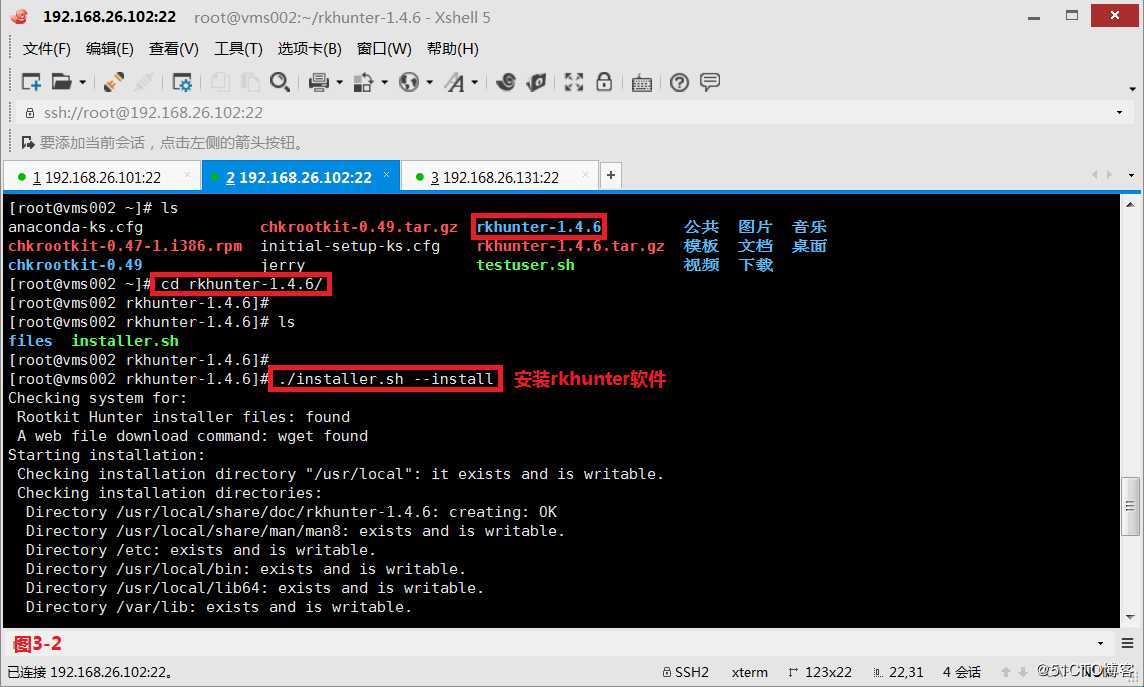
(3.2)首先我们安装RKHunter软件,先将rkhunter软件包解压缩,然后进入到rkhunter-1.4.6/目录中安装rkhunter软件。
# tar zxvf rkhunter-1.4.6.tar.gz---解压缩rkhunter软件包
# cd rkhunter-1.4.6/---进入到rkhunter-1.4.6/目录中
# ./installer.sh --install---安装rkhunter软件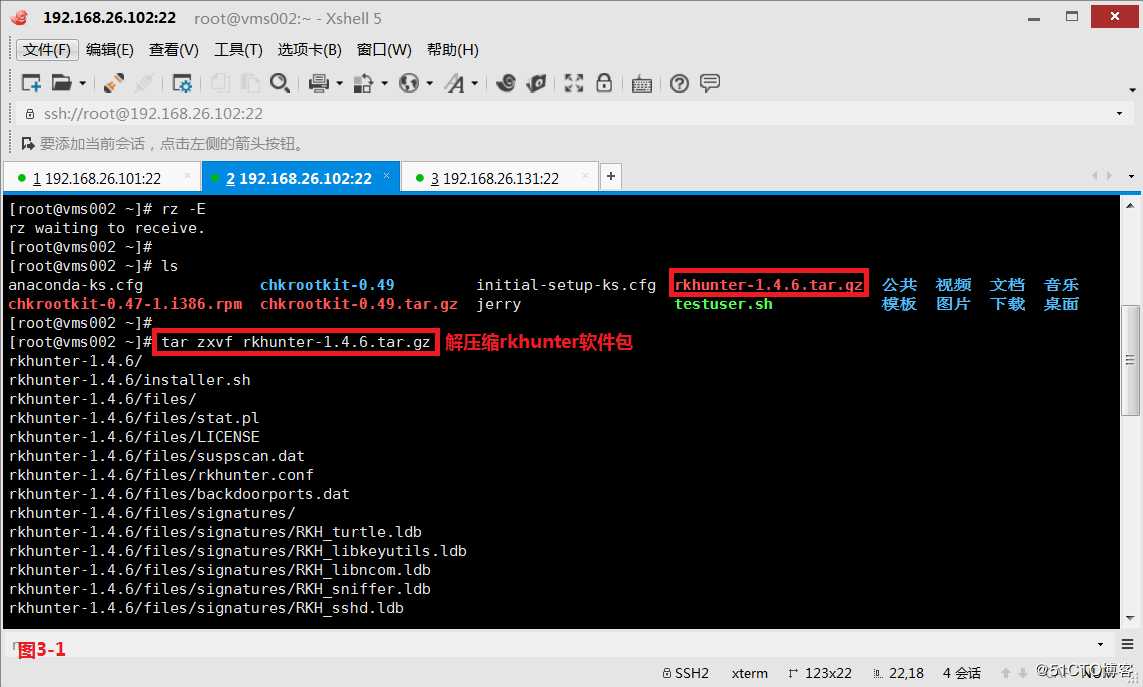
(3.3)接着为基本系统程序建立校对样本,建议系统安装完成后就建立,并可以查看系统生成的校对样本。
# rkhunter --propupd---为基本系统程序建立校对样本
# ls /var/lib/rkhunter/db/rkhunter.dat---查看系统生成的校对样本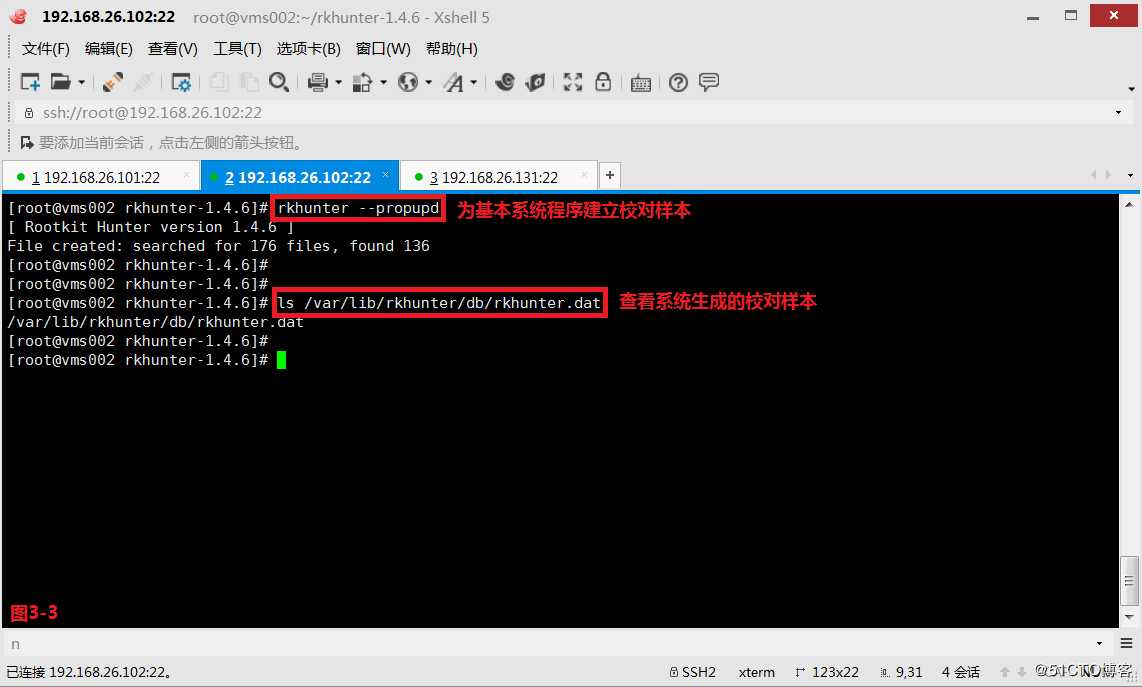
(3.4)接着我们执行检测命令
# rkhunter --check---执行检测命令
第一部分:检测系统命令,主要检测系统的二进制文件,这些文件最容易被rootkit进行accuse;[OK]表示正常,[Warning]表示由异常,[Not found]未找到。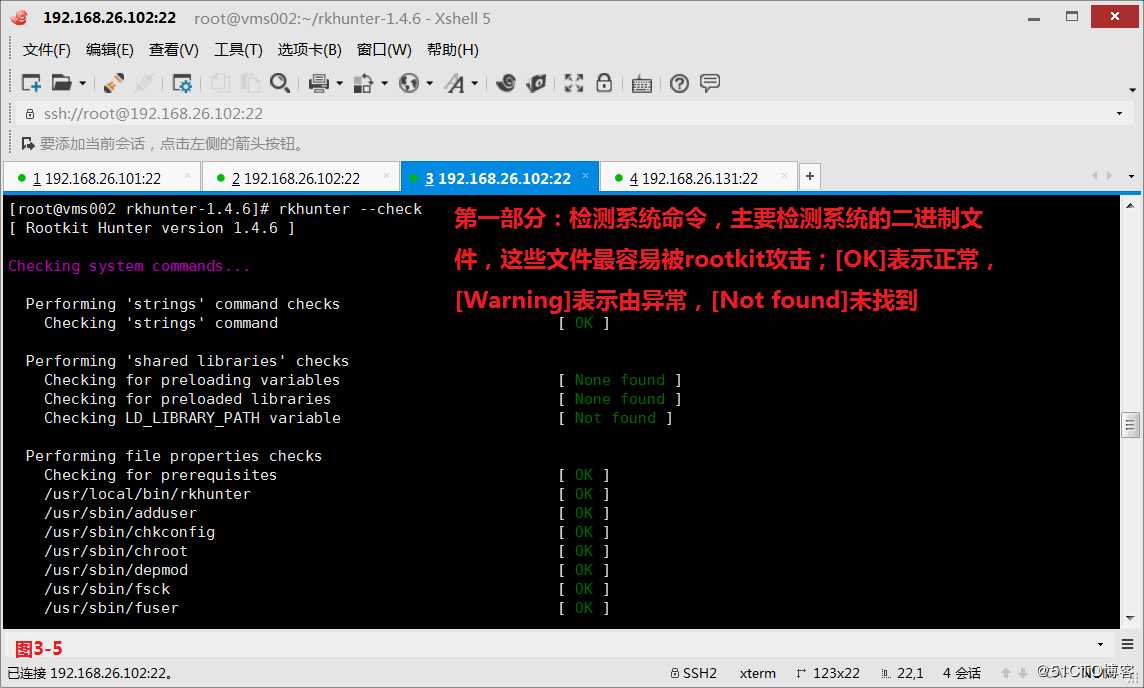
第二部分:检测rootkit,主要检测常见的rootkit程序;[Not found]表示未感染。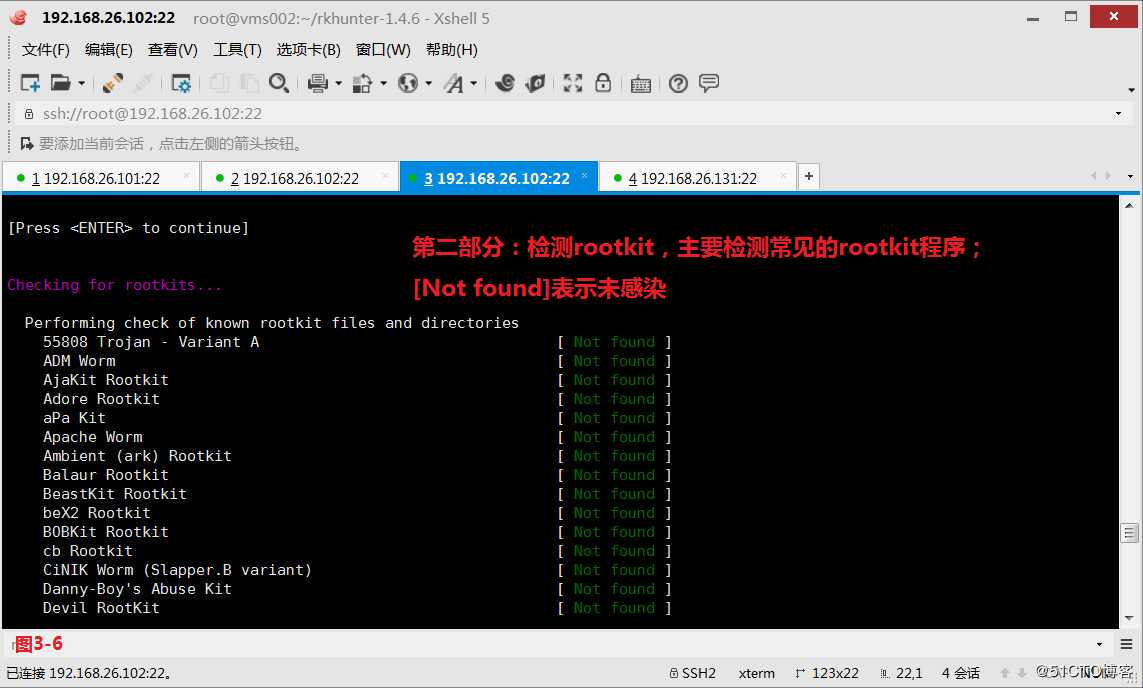
第三部分:特殊或附加检测:对rootkit文件或目录检测、对恶意软件检测、对指定内核检测等。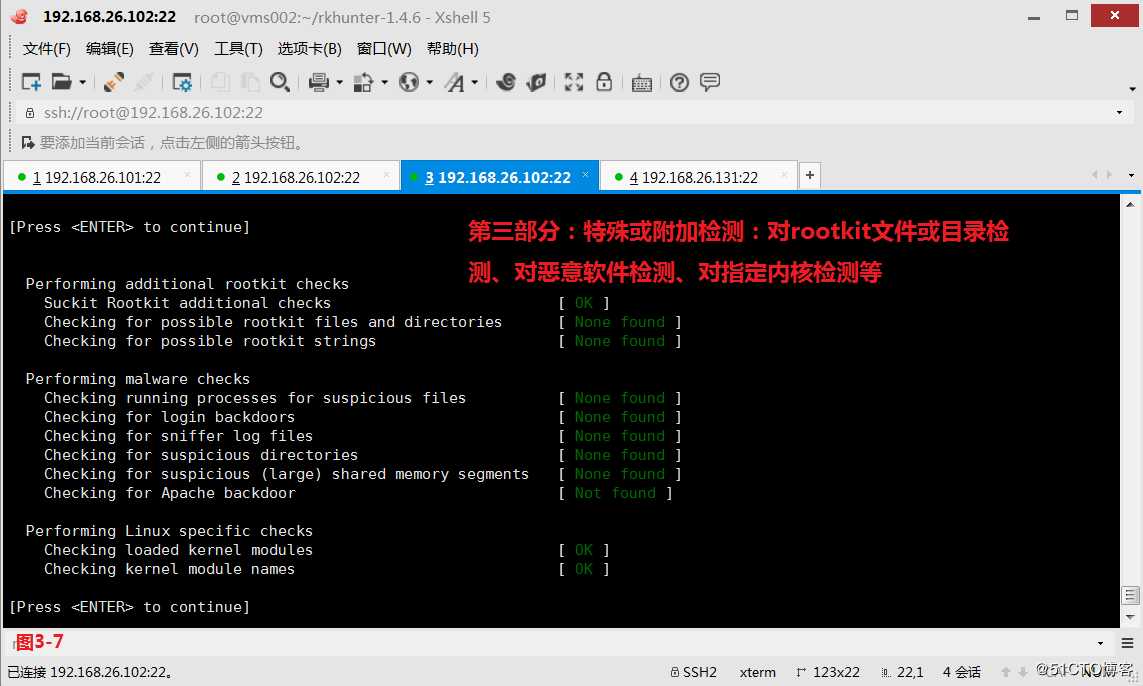
第四部分:检测网络、系统端口、系统启动文件、系统用户和组配置、ssh配置、文件系统等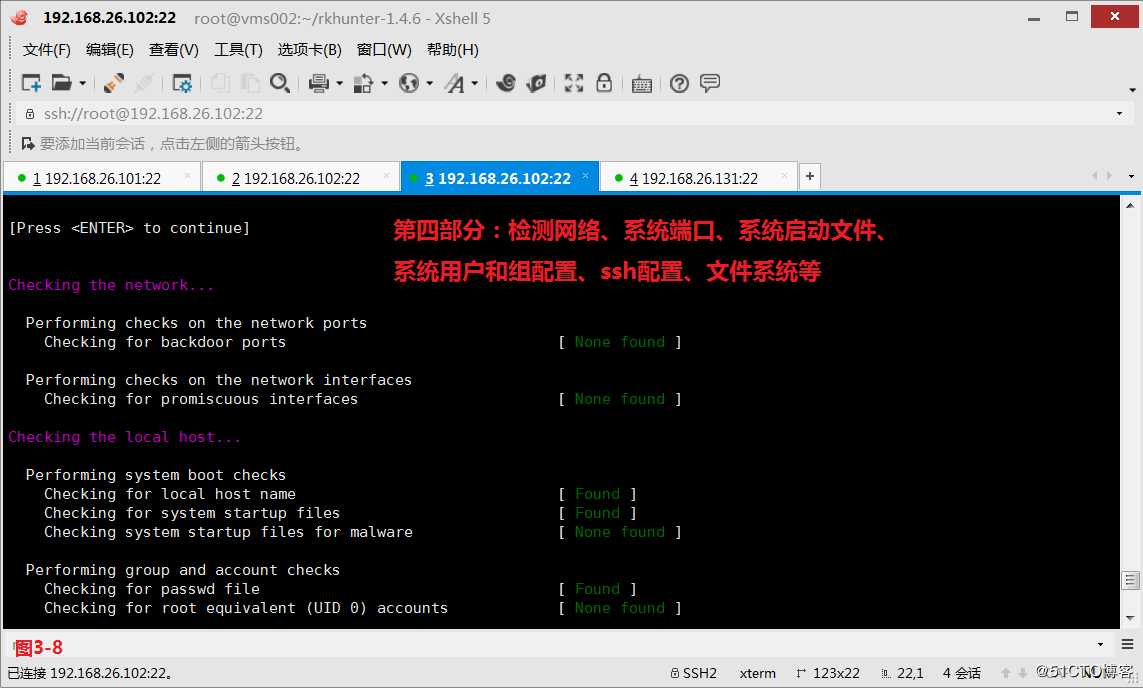
第五部分:应用程序版本检测
第六部分:总结服务器目前的安全状态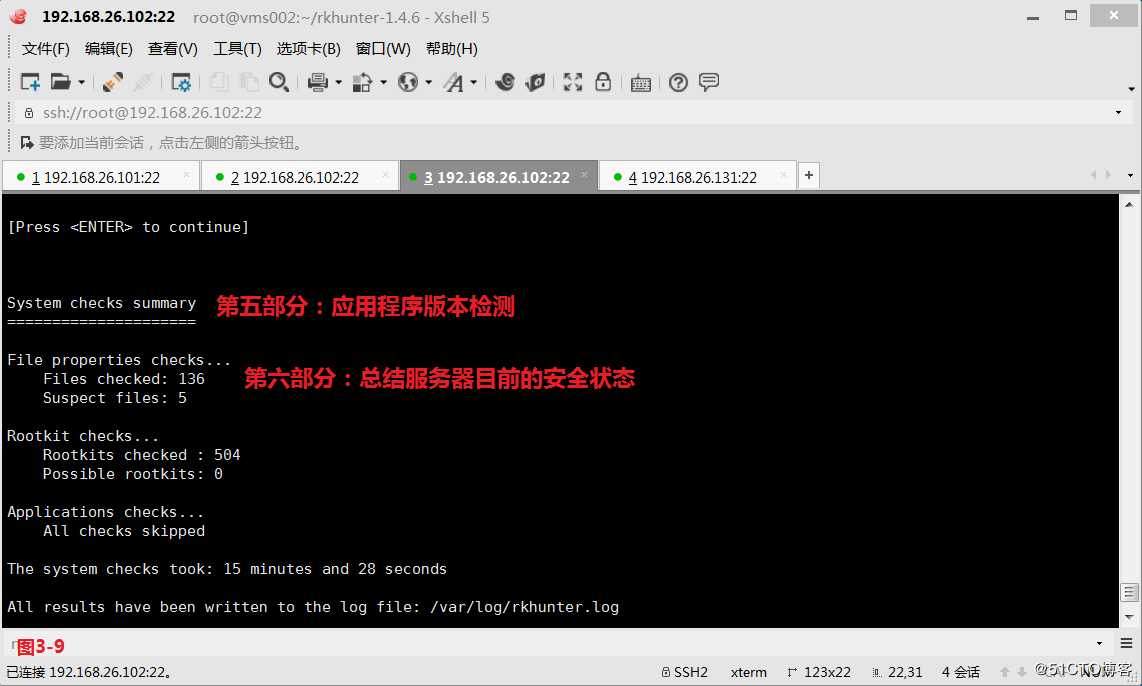
(3.5)在Linux终端使用rkhunter来检测,最大的好处在于每项的检测结果都有不同的颜色显示,如果是绿色的表示没有问题,如果是红色的,那就要引起关注了。另外,在执行检测的过程中,在每个部分检测完成后,需要以Enter键来继续。如果要让程序自动执行,可以执行如下命令:
# rkhunter --check --skip-keypress---如果我们不想每个部分都以Enter来继续,想要让程序自动持续执行可以加上--skip-keypress参数
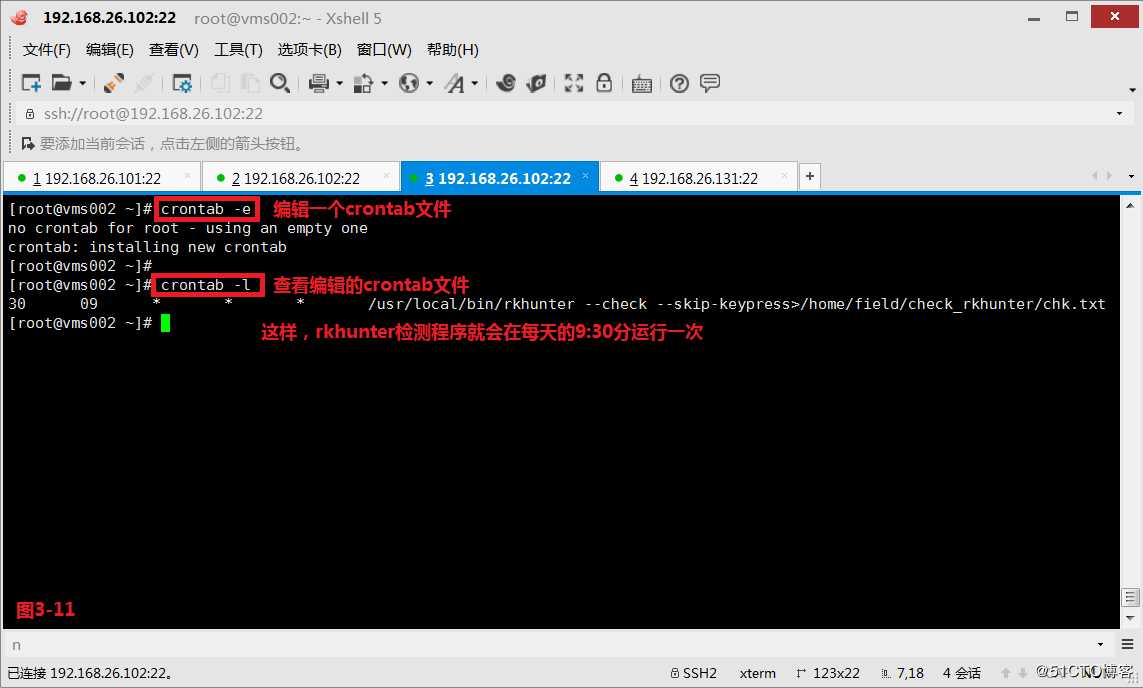
(3.6)如果想让检测程序每天定时运行,那么可以制定计划任务。我们设定计划任务在每天9:30执行,会执行一次rkhunter命令并且自动执行Enter键,并将结果输出到/home/field/check_rkhunter/chk.txt文件中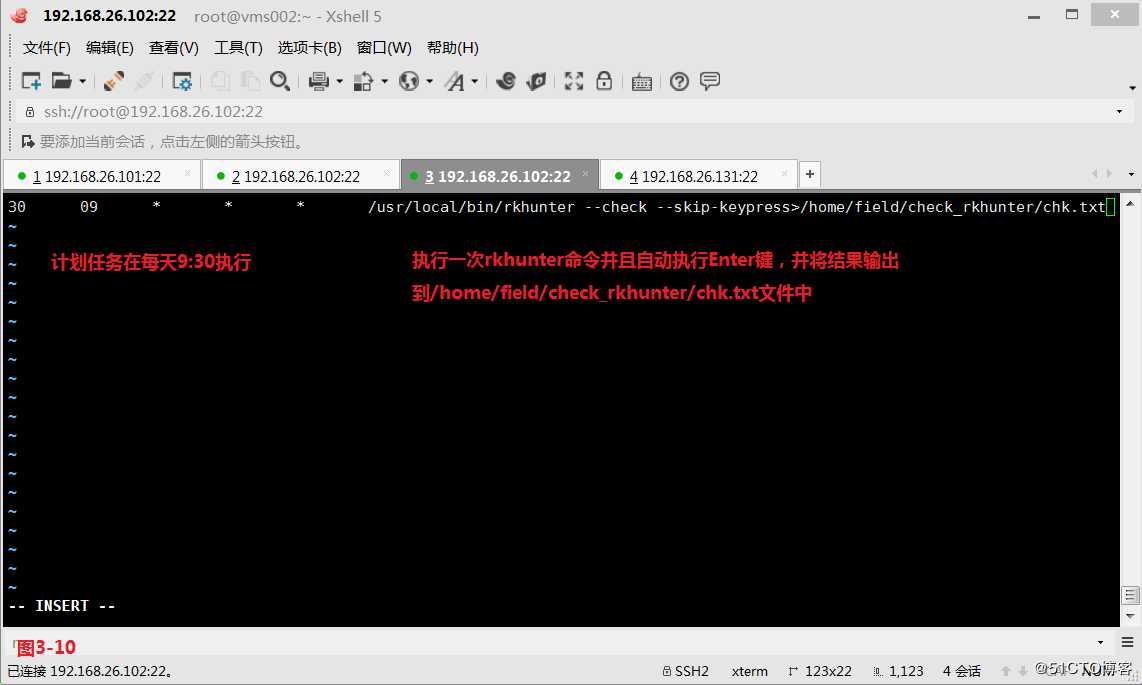
—————— 本文至此结束,感谢阅读 ——————
以上是关于rootkit检测之检测hook——iat hookinline hookeat hookidt hookirp hookssdt的主要内容,如果未能解决你的问题,请参考以下文章