Security ❀ JavaScript Attacks 前端攻击
Posted 无糖可乐没有灵魂
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Security ❀ JavaScript Attacks 前端攻击相关的知识,希望对你有一定的参考价值。
文章目录
javascript Attacks 前端攻击
JavaScript是一种基于对象和事件驱动的、并具有安全性能的脚本语言。是一种解释型语言(代码不需要进行预编译)。通常JavaScript脚本是通过嵌入在html中来实现自身的功能的;若是涉及到Cookie、Session等记录用户信息的脚本,应该通过外部引入方式,并且不能暴露文件路径,控制好文件访问权限,若被攻击者获取到重要脚本代码,则能伪造其他合法用户进行伪造。
1 Low Level
源码:
<?php
$page[ 'body' ] .= <<<EOF
<script>
/*
MD5 code from here
https://github.com/blueimp/JavaScript-MD5
*/
!function(n)"use strict";function t(n,t)var r=(65535&n)+(65535&t);return(n>>16)+(t>>16)+(r>>16)<<16|65535&rfunction r(n,t)return n<<t|n>>>32-tfunction e(n,e,o,u,c,f)return t(r(t(t(e,n),t(u,f)),c),o)function o(n,t,r,o,u,c,f)return e(t&r|~t&o,n,t,u,c,f)function u(n,t,r,o,u,c,f)return e(t&o|r&~o,n,t,u,c,f)function c(n,t,r,o,u,c,f)return e(t^r^o,n,t,u,c,f)function f(n,t,r,o,u,c,f)return e(r^(t|~o),n,t,u,c,f)function i(n,r)n[r>>5]|=128<<r%32,n[14+(r+64>>>9<<4)]=r;var e,i,a,d,h,l=1732584193,g=-271733879,v=-1732584194,m=271733878;for(e=0;e<n.length;e+=16)i=l,a=g,d=v,h=m,g=f(g=f(g=f(g=f(g=c(g=c(g=c(g=c(g=u(g=u(g=u(g=u(g=o(g=o(g=o(g=o(g,v=o(v,m=o(m,l=o(l,g,v,m,n[e],7,-680876936),g,v,n[e+1],12,-389564586),l,g,n[e+2],17,606105819),m,l,n[e+3],22,-1044525330),v=o(v,m=o(m,l=o(l,g,v,m,n[e+4],7,-176418897),g,v,n[e+5],12,1200080426),l,g,n[e+6],17,-1473231341),m,l,n[e+7],22,-45705983),v=o(v,m=o(m,l=o(l,g,v,m,n[e+8],7,1770035416),g,v,n[e+9],12,-1958414417),l,g,n[e+10],17,-42063),m,l,n[e+11],22,-1990404162),v=o(v,m=o(m,l=o(l,g,v,m,n[e+12],7,1804603682),g,v,n[e+13],12,-40341101),l,g,n[e+14],17,-1502002290),m,l,n[e+15],22,1236535329),v=u(v,m=u(m,l=u(l,g,v,m,n[e+1],5,-165796510),g,v,n[e+6],9,-1069501632),l,g,n[e+11],14,643717713),m,l,n[e],20,-373897302),v=u(v,m=u(m,l=u(l,g,v,m,n[e+5],5,-701558691),g,v,n[e+10],9,38016083),l,g,n[e+15],14,-660478335),m,l,n[e+4],20,-405537848),v=u(v,m=u(m,l=u(l,g,v,m,n[e+9],5,568446438),g,v,n[e+14],9,-1019803690),l,g,n[e+3],14,-187363961),m,l,n[e+8],20,1163531501),v=u(v,m=u(m,l=u(l,g,v,m,n[e+13],5,-1444681467),g,v,n[e+2],9,-51403784),l,g,n[e+7],14,1735328473),m,l,n[e+12],20,-1926607734),v=c(v,m=c(m,l=c(l,g,v,m,n[e+5],4,-378558),g,v,n[e+8],11,-2022574463),l,g,n[e+11],16,1839030562),m,l,n[e+14],23,-35309556),v=c(v,m=c(m,l=c(l,g,v,m,n[e+1],4,-1530992060),g,v,n[e+4],11,1272893353),l,g,n[e+7],16,-155497632),m,l,n[e+10],23,-1094730640),v=c(v,m=c(m,l=c(l,g,v,m,n[e+13],4,681279174),g,v,n[e],11,-358537222),l,g,n[e+3],16,-722521979),m,l,n[e+6],23,76029189),v=c(v,m=c(m,l=c(l,g,v,m,n[e+9],4,-640364487),g,v,n[e+12],11,-421815835),l,g,n[e+15],16,530742520),m,l,n[e+2],23,-995338651),v=f(v,m=f(m,l=f(l,g,v,m,n[e],6,-198630844),g,v,n[e+7],10,1126891415),l,g,n[e+14],15,-1416354905),m,l,n[e+5],21,-57434055),v=f(v,m=f(m,l=f(l,g,v,m,n[e+12],6,1700485571),g,v,n[e+3],10,-1894986606),l,g,n[e+10],15,-1051523),m,l,n[e+1],21,-2054922799),v=f(v,m=f(m,l=f(l,g,v,m,n[e+8],6,1873313359),g,v,n[e+15],10,-30611744),l,g,n[e+6],15,-1560198380),m,l,n[e+13],21,1309151649),v=f(v,m=f(m,l=f(l,g,v,m,n[e+4],6,-145523070),g,v,n[e+11],10,-1120210379),l,g,n[e+2],15,718787259),m,l,n[e+9],21,-343485551),l=t(l,i),g=t(g,a),v=t(v,d),m=t(m,h);return[l,g,v,m]function a(n)var t,r="",e=32*n.length;for(t=0;t<e;t+=8)r+=String.fromCharCode(n[t>>5]>>>t%32&255);return rfunction d(n)var t,r=[];for(r[(n.length>>2)-1]=void 0,t=0;t<r.length;t+=1)r[t]=0;var e=8*n.length;for(t=0;t<e;t+=8)r[t>>5]|=(255&n.charCodeAt(t/8))<<t%32;return rfunction h(n)return a(i(d(n),8*n.length))function l(n,t)var r,e,o=d(n),u=[],c=[];for(u[15]=c[15]=void 0,o.length>16&&(o=i(o,8*n.length)),r=0;r<16;r+=1)u[r]=909522486^o[r],c[r]=1549556828^o[r];return e=i(u.concat(d(t)),512+8*t.length),a(i(c.concat(e),640))function g(n)var t,r,e="";for(r=0;r<n.length;r+=1)t=n.charCodeAt(r),e+="0123456789abcdef".charAt(t>>>4&15)+"0123456789abcdef".charAt(15&t);return efunction v(n)return unescape(encodeURIComponent(n))function m(n)return h(v(n))function p(n)return g(m(n))function s(n,t)return l(v(n),v(t))function C(n,t)return g(s(n,t))function A(n,t,r)return t?r?s(t,n):C(t,n):r?m(n):p(n)"function"==typeof define&&define.amd?define(function()return A):"object"==typeof module&&module.exports?module.exports=A:n.md5=A(this);
function rot13(inp)
return inp.replace(/[a-zA-Z]/g,function(c)return String.fromCharCode((c<="Z"?90:122)>=(c=c.charCodeAt(0)+13)?c:c-26););
# 生成一个token与phrase值互相匹配即可,且token为phrase值经md5(rot13(phrase))获得
function generate_token()
var phrase = document.getElementById("phrase").value;
document.getElementById("token").value = md5(rot13(phrase));
generate_token();
</script>
EOF;
?>
因此只要将phrase值经md5(rot13(phrase))获得token即可,攻击案例success:38581812b435834ebf84ebcc2c6424d6。

获取到token后,使用burp进行抓包重组参数后发送即可完成攻击。

web页面效果如下:

2 Medium Level
源码:
<?php
$page[ 'body' ] .= '<script src="' . DVWA_WEB_PAGE_TO_ROOT . 'vulnerabilities/javascript/source/medium.js"></script>';
?>
medium.js代码:
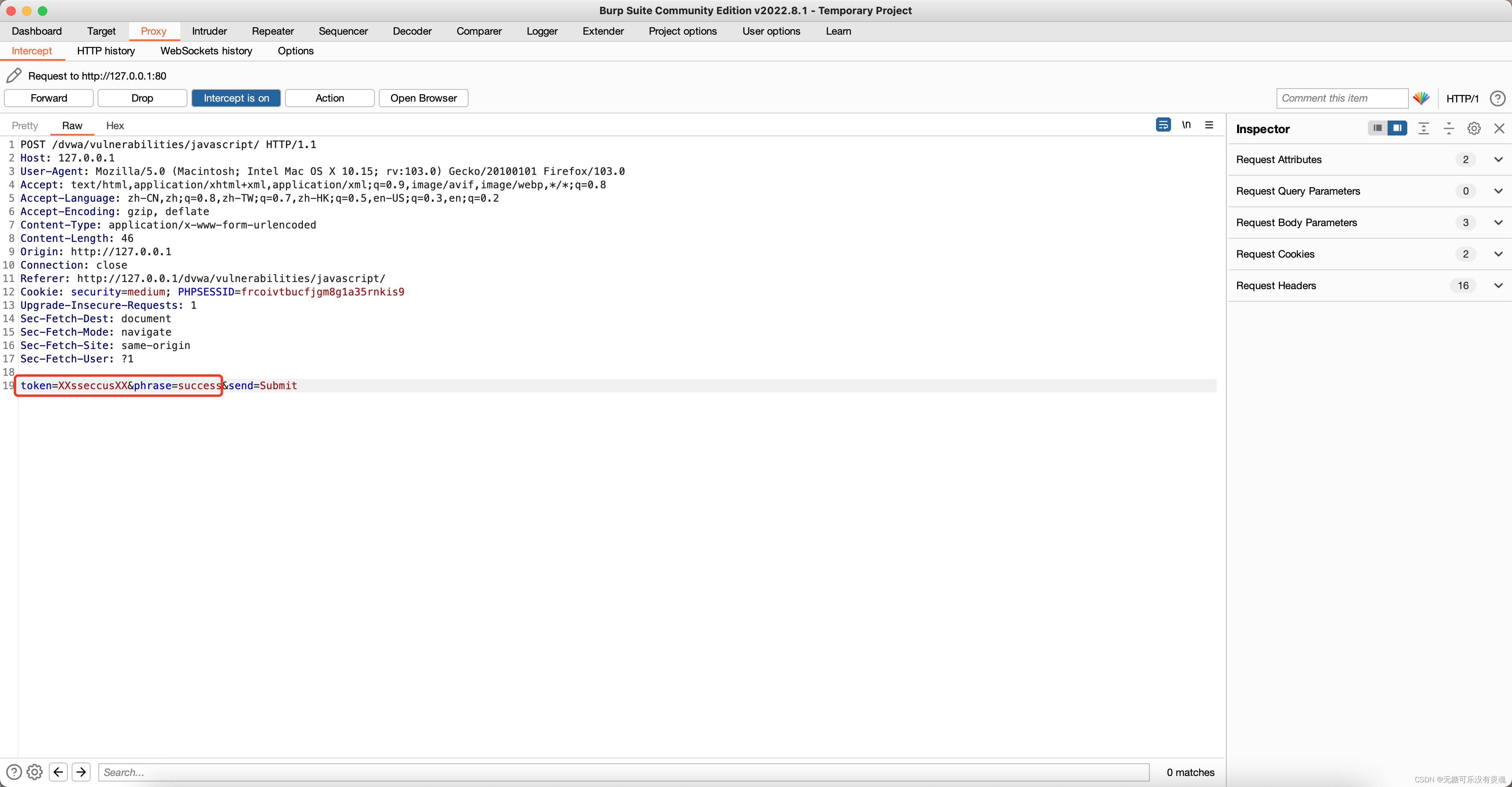
function do_something(e)for(var t="",n=e.length-1;n>=0;n--)t+=e[n];return tsetTimeout(function()
do_elsesomething("XX"),300);function do_elsesomething(e)document.getElementById("token").value=do_something(e+document.getElementById("phrase").value+"XX")
// 将phrase进行反转,并前后添加XX构成token
burp抓包如下:

修改token与phrase的值后进行转发,触发攻击。
web页面效果如下:

3 High Level
源码:
<?php
$page[ 'body' ] .= '<script src="' . DVWA_WEB_PAGE_TO_ROOT . 'vulnerabilities/javascript/source/high.js"></script>';
?>
high.js代码:
var a=['fromCharCode','toString','replace','BeJ','\\x5cw+','Lyg','SuR','(w()\\x273M\\x203L\\x27;q\\x201l=\\x273K\\x203I\\x203J\\x20T\\x27;q\\x201R=1c\\x202I===\\x271n\\x27;q\\x20Y=1R?2I:;p(Y.3N)1R=1Oq\\x202L=!1R&&1c\\x202M===\\x271n\\x27;q\\x202o=!Y.2S&&1c\\x202d===\\x271n\\x27&&2d.2Q&&2d.2Q.3S;p(2o)Y=3Rz\\x20p(2L)Y=2Mq\\x202G=!Y.3Q&&1c\\x202g===\\x271n\\x27&&2g.X;q\\x202s=1c\\x202l===\\x27w\\x27&&2l.3P;q\\x201y=!Y.3H&&1c\\x20Z!==\\x272T\\x27;q\\x20m=\\x273G\\x27.3z(\\x27\\x27);q\\x202w=[-3y,3x,3v,3w];q\\x20U=[24,16,8,0];q\\x20K=[3A,3B,3F,3E,3D,3C,3T,3U,4d,4c,4b,49,4a,4e,4f,4j,4i,4h,3u,48,47,3Z,3Y,3X,3V,3W,40,41,46,45,43,42,4k,3f,38,36,39,37,34,33,2Y,31,2Z,35,3t,3n,3m,3l,3o,3p,3s,3r,3q,3k,3j,3d,3a,3c,3b,3e,3h,3g,3i,4g];q\\x201E=[\\x271e\\x27,\\x2727\\x27,\\x271G\\x27,\\x272R\\x27];q\\x20l=[];p(Y.2S||!1z.1K)1z.1K=w(1x)A\\x204C.Q.2U.1I(1x)===\\x27[1n\\x201z]\\x27p(1y&&(Y.50||!Z.1N))Z.1N=w(1x)A\\x201c\\x201x===\\x271n\\x27&&1x.1w&&1x.1w.1J===Zq\\x202m=w(1X,x)A\\x20w(s)A\\x20O\\x20N(x,1d).S(s)[1X]();q\\x202a=w(x)q\\x20P=2m(\\x271e\\x27,x);p(2o)P=2P(P,x)P.1T=w()A\\x20O\\x20N(x);P.S=w(s)A\\x20P.1T().S(s);1g(q\\x20i=0;i<1E.W;++i)q\\x20T=1E[i];P[T]=2m(T,x)A\\x20P;q\\x202P=w(P,x)q\\x201S=2O(\\x222N(\\x271S\\x27)\\x22);q\\x201Y=2O(\\x222N(\\x271w\\x27).1Y\\x22);q\\x202n=x?\\x271H\\x27:\\x271q\\x27;q\\x202z=w(s)p(1c\\x20s===\\x272p\\x27)A\\x201S.2x(2n).S(s,\\x274S\\x27).1G(\\x271e\\x27)zp(s===2q||s===2T)1u\\x20O\\x201t(1l)z\\x20p(s.1J===Z)s=O\\x202r(s)p(1z.1K(s)||Z.1N(s)||s.1J===1Y)A\\x201S.2x(2n).S(O\\x201Y(s)).1G(\\x271e\\x27)zA\\x20P(s);A\\x202z;q\\x202k=w(1X,x)A\\x20w(G,s)A\\x20O\\x201P(G,x,1d).S(s)[1X]();q\\x202f=w(x)q\\x20P=2k(\\x271e\\x27,x);P.1T=w(G)A\\x20O\\x201P(G,x);P.S=w(G,s)A\\x20P.1T(G).S(s);1g(q\\x20i=0;i<1E.W;++i)q\\x20T=1E[i];P[T]=2k(T,x)A\\x20P;w\\x20N(x,1v)p(1v)l[0]=l[16]=l[1]=l[2]=l[3]=l[4]=l[5]=l[6]=l[7]=l[8]=l[9]=l[10]=l[11]=l[12]=l[13]=l[14]=l[15]=0;k.l=lzk.l=[0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0]p(x)k.C=4I;k.B=4H;k.E=4l;k.F=4U;k.J=4J;k.I=4K;k.H=4L;k.D=4Tzk.C=4X;k.B=4W;k.E=4Y;k.F=4Z;k.J=4V;k.I=4O;k.H=4F;k.D=4sk.1C=k.1A=k.L=k.2i=0;k.1U=k.1L=1O;k.2j=1d;k.x=xN.Q.S=w(s)p(k.1U)Aq\\x202h,T=1c\\x20s;p(T!==\\x272p\\x27)p(T===\\x271n\\x27)p(s===2q)1u\\x20O\\x201t(1l)z\\x20p(1y&&s.1J===Z)s=O\\x202r(s)z\\x20p(!1z.1K(s))p(!1y||!Z.1N(s))1u\\x20O\\x201t(1l)z1u\\x20O\\x201t(1l)2h=1dq\\x20r,M=0,i,W=s.W,l=k.l;4t(M<W)p(k.1L)k.1L=1O;l[0]=k.1C;l[16]=l[1]=l[2]=l[3]=l[4]=l[5]=l[6]=l[7]=l[8]=l[9]=l[10]=l[11]=l[12]=l[13]=l[14]=l[15]=0p(2h)1g(i=k.1A;M<W&&i<1k;++M)l[i>>2]|=s[M]<<U[i++&3]z1g(i=k.1A;M<W&&i<1k;++M)r=s.1Q(M);p(r<R)l[i>>2]|=r<<U[i++&3]z\\x20p(r<2v)l[i>>2]|=(2t|(r>>6))<<U[i++&3];l[i>>2]|=(R|(r&V))<<U[i++&3]z\\x20p(r<2A||r>=2E)l[i>>2]|=(2D|(r>>12))<<U[i++&3];l[i>>2]|=(R|((r>>6)&V))<<U[i++&3];l[i>>2]|=(R|(r&V))<<U[i++&3]zr=2C+(((r&23)<<10)|(s.1Q(++M)&23));l[i>>2]|=(2X|(r>>18))<<U[i++&3];l[i>>2]|=(R|((r>>12)&V))<<U[i++&3];l[i>>2]|=(R|((r>>6)&V))<<U[i++&3];l[i>>2]|=(R|(r&V))<<U[i++&3]k.2u=i;k.L+=i-k.1A;p(i>=1k)k.1C=l[16];k.1A=i-1k;k.1W();k.1L=1dzk.1A=ip(k.L>4r)k.2i+=k.L/2H<<0;k.L=k.L%2HA\\x20k;N.Q.1s=w()p(k.1U)Ak.1U=1d;q\\x20l=k.l,i=k.2u;l[16]=k.1C;l[i>>2]|=2w[i&3];k.1C=l[16];p(i>=4q)p(!k.1L)k.1W()l[0]=k.1C;l[16]=l[1]=l[2]=l[3]=l[4]=l[5]=l[6]=l[7]=l[8]=l[9]=l[10]=l[11]=l[12]=l[13]=l[14]=l[15]=0l[14]=k.2i<<3|k.L>>>29;l[15]=k.L<<3;k.1W();N.Q.1W=w()q\\x20a=k.C,b=k.B,c=k.E,d=k.F,e=k.J,f=k.I,g=k.H,h=k.D,l=k.l,j,1a,1b,1j,v,1f,1h,1B,1Z,1V,1D;1g(j=16;j<1k;++j)v=l[j-15];1a=((v>>>7)|(v<<25))^((v>>>18)|(v<<14))^(v>>>3);v=l[j-2];1b=((v>>>17)|(v<<15))^((v>>>19)|(v<<13))^(v>>>10);l[j]=l[j-16]+1a+l[j-7]+1b<<01D=b&c;1g(j=0;j<1k;j+=4)p(k.2j)p(k.x)1B=4m;v=l[0]-4n;h=v-4o<<0;d=v+4p<<0z1B=4v;v=l[0]-4w;h=v-4G<<0;d=v+4D<<0k.2j=1Oz1a=((a>>>2)|(a<<30))^((a>>>13)|(a<<19))^((a>>>22)|(a<<10));1b=((e>>>6)|(e<<26))^((e>>>11)|(e<<21))^((e>>>25)|(e<<7));1B=a&b;1j=1B^(a&c)^1D;1h=(e&f)^(~e&g);v=h+1b+1h+K[j]+l[j];1f=1a+1j;h=d+v<<0;d=v+1f<<01a=((d>>>2)|(d<<30))^((d>>>13)|(d<<19))^((d>>>22)|(d<<10));1b=((h>>>6)|(h<<26))^((h>>>11)|(h<<21))^((h>>>25)|(h<<7));1Z=d&a;1j=1Z^(d&b)^1B;1h=(h&e)^(~h&f);v=g+1b+1h+K[j+1]+l[j+1];1f=1a+1j;g=c+v<<0;c=v+1f<<0;1a=((c>>>2)|(c<<30))^((c>>>13)|(c<<19))^((c>>>22)|(c<<10));1b=((g>>>6)|(g<<26))^((g>>>11)|(g<<21))^((g>>>25)|(g<<7));1V=c&d;1j=1V^(c&a)^1Z;1h=(g&h)^(~g&e);v=f+1b+1h+K[j+2]+l[j+2];1f=1a+1j;f=b+v<<0;b=v+1f<<0;1a=((b>>>2)|(b<<30))^((b>>>13)|(b<<19))^((b>>>22)|(b<<10));1b=((f>>>6)|(f<<26))^((f>>>11)|(f<<21))^((f>>>25)|(f<<7));1D=b&c;1j=1D^(b&d)^1V;1h=(f&g)^(~f&h);v=e+1b+1h+K[j+3]+l[j+3];1f=1a+1j;e=a+v<<0;a=v+1f<<0k.C=k.C+a<<0;k.B=k.B+b<<0;k.E=k.E+c<<0;k.F=k.F+d<<0;k.J=k.J+e<<0;k.I=k.I+f<<0;k.H=k.H+g<<0;k.D=k.D+h<<0;N.Q.1e=w()k.1s();q\\x20C=k.C,B=k.B,E=k.E,F=k.F,J=k.J,I=k.I,H=k.H,D=k.D;q\\x201e=m[(C>>28)&o]+m[(C>>24)&o]+m[(C>>20)&o]+m[(C>>16)&o]+m[(C>>12)&o]+m[(C>>8)&o]+m[(C>>4)&o]+m[C&o]+m[(B>>28)&o]+m[(B>>24)&o]+m[(B>>20)&o]+m[(B>>16)&o]+m[(B>>12)&o]+m[(B>>8)&o]+m[(B>>4)&o]+m[B&o]+m[(E>>28)&o]+m[(E>>24)&o]+m[(E>>20)&o]+m[(E>>16)&o]+m[(E>>12)&o]+m[(E>>8)&o]+m[(E>>4)&o]+m[E&o]+m[(F>>28)&o]+m[(F>>24)&o]+m[(F>>20)&o]+m[(F>>16)&o]+m[(F>>12)&o]+m[(F>>8)&o]+m[(F>>4)&o]+m[F&o]+m[(J>>28)&o]+m[(J>>24)&o]+m[(J>>20)&o]+m[(J>>16)&o]+m[(J>>12)&o]+m[(J>>8)&o]+m[(J>>4)&o]+m[J&o]+m[(I>>28)&o]+m[(I>>24)&o]+m[(I>>20)&o]+m[(I>>16)&o]+m[(I>>12)&o]+m[(I>>8)&o]+m[(I>>4)&o]+m[I&o]+m[(H>>28)&o]+m[(H>>24)&o]+m[(H>>20)&o]+m[(H>>16)&o]+m[(H>>12)&o]+m[(H>>8)&o]+m[(H>>4)&o]+m[H&o];p(!k.x)1e+=m[(D>>28)&o]+m[(D>>24)&o]+m[(D>>20)&o]+m[(D>>16)&o]+m[(D>>12)&o]+m[(D>>8)&o]+m[(D>>4)&o]+m[D&o]A\\x201e;N.Q.2U=N.Q.1e;N.Q.1G=w()k.1s();q\\x20C=k.C,B=k.B,E=k.E,F=k.F,J=k.J,I=k.I,H=k.H,D=k.D;q\\x202b=[(C>>24)&u,(C>>16)&u,(C>>8)&u,C&u,(B>>24)&u,(B>>16)&u,(B>>8)&u,B&u,(E>>24)&u,(E>>16)&u,(E>>8)&u,E&u,(F>>24)&u,(F>>16)&u,(F>>8)&u,F&u,(J>>24)&u,(J>>16)&u,(J>>8)&u,J&u,(I>>24)&u,(I>>16)&u,(I>>8)&u,I&u,(H>>24)&u,(H>>16)&u,(H>>8)&u,H&u];p(!k.x)2b.4A((D>>24)&u,(D>>16)&u,(D>>8)&u,D&u)A\\x202b;N.Q.27=N.Q.1G;N.Q.2R=w()k.1s();q\\x201w=O\\x20Z(k.x?28:32);q\\x201i=O\\x204x(1w);1i.1p(0,k.C);1i.1p(4,k.B);1i.1p(8,k.E);1i.1p(12,k.F);1i.1p(16,k.J);1i.1p(20,k.I);1i.1p(24,k.H);p(!k.x)1i.1p(28,k.D)A\\x201w;w\\x201P(G,x,1v)q\\x20i,T=1c\\x20G;p(T===\\x272p\\x27)q\\x20L=[],W=G.W,M=0,r;1g(i=0;i<W;++i)r=G.1Q(i);p(r<R)L[M++]=rz\\x20p(r<2v)L[M++]=(2t|(r>>6));L[M++]=(R|(r&V))z\\x20p(r<2A||r>=2E)L[M++]=(2D|(r>>12));L[M++]=(R|((r>>6)&V));L[M++]=(R|(r&V))zr=2C+(((r&23)<<10)|(G.1Q(++i)&23));L[M++]=(2X|(r>>18));L[M++]=(R|((r>>12)&V));L[M++]=(R|((r>>6)&V));L[M++]=(R|(r&V))G=Lzp(T===\\x271n\\x27)p(G===2q)1u\\x20O\\x201t(1l)z\\x20p(1y&&G.1J===Z)G=O\\x202r(G)z\\x20p(!1z.1K(G))p(!1y||!Z.1N(G))1u\\x20O\\x201t(1l)z1u\\x20O\\x201t(1l)p(G.W>1k)G=(O\\x20N(x,1d)).S(G).27()q\\x201F=[],2e=[];1g(i=0;i<1k;++i)q\\x20b=G[i]||0;1F[i]=4z^b;2e[i]=4y^bN.1I(k,x,1v);k.S(2e);k.1F=1F;k.2c=1d;k.1v=1v1P.Q=O\\x20N();1P.Q.1s=w()N.Q.1s.1I(k);p(k.2c)k.2c=1O;q\\x202W=k.27();N.1I(k,k.x,k.1v);k.S(k.1F);k.S(2W);N.Q.1s.1I(k);q\\x20X=2a();X.1q=X;X.1H=2a(1d);X.1q.2V=2f();X.1H.2V=2f(1d);p(2G)2g.X=XzY.1q=X.1q;Y.1H=X.1H;p(2s)2l(w()A\\x20X))();w\\x202y(e)1g(q\\x20t=\\x22\\x22,n=e.W-1;n>=0;n--)t+=e[n];A\\x20tw\\x202J(t,y=\\x224B\\x22)1m.1o(\\x221M\\x22).1r=1q(1m.1o(\\x221M\\x22).1r+y)w\\x202B(e=\\x224E\\x22)1m.1o(\\x221M\\x22).1r=1q(e+1m.1o(\\x221M\\x22).1r)w\\x202K(a,b)1m.1o(\\x221M\\x22).1r=2y(1m.1o(\\x222F\\x22).1r)1m.1o(\\x222F\\x22).1r=\\x22\\x22;4u(w()2B(\\x224M\\x22),4N);1m.1o(\\x224P\\x22).4Q(\\x224R\\x22,2J);2K(\\x223O\\x22,44);','||||||||||||||||||||this|blocks|HEX_CHARS||0x0F|if|var|code|message||0xFF|t1|function|is224||else|return|h1|h0|h7|h2|h3|key|h6|h5|h4||bytes|index|Sha256|new|method|prototype|0x80|update|type|SHIFT|0x3f|length|exports|root|ArrayBuffer|||||||||||s0|s1|typeof|true|hex|t2|for|ch|dataView|maj|64|ERROR|document|object|getElementById|setUint32|sha256|value|finalize|Error|throw|sharedMemory|buffer|obj|ARRAY_BUFFER|Array|start|ab|block|bc|OUTPUT_TYPES|oKeyPad|digest|sha224|call|constructor|isArray|hashed|token|isView|false|HmacSha256|charCodeAt|WINDOW|crypto|create|finalized|cd|hash|outputType|Buffer|da||||0x3ff||||array|||createMethod|arr|inner|process|iKeyPad|createHmacMethod|module|notString|hBytes|first|createHmacOutputMethod|define|createOutputMethod|algorithm|NODE_JS|string|null|Uint8Array|AMD|0xc0|lastByteIndex|0x800|EXTRA|createHash|do_something|nodeMethod|0xd800|token_part_2|0x10000|0xe0|0xe000|phrase|COMMON_JS|4294967296|window|token_part_3|token_part_1|WEB_WORKER|self|require|eval|nodeWrap|versions|arrayBuffer|JS_SHA256_NO_NODE_JS|undefined|toString|hmac|innerHash|0xf0|0xa2bfe8a1|0xc24b8b70||0xa81a664b||0x92722c85|0x81c2c92e|0xc76c51a3|0x53380d13|0x766a0abb|0x4d2c6dfc|0x650a7354|0x748f82ee|0x84c87814|0x78a5636f|0x682e6ff3|0x8cc70208|0x2e1b2138|0xa4506ceb|0x90befffa|0xbef9a3f7|0x5b9cca4f|0x4ed8aa4a|0x106aa070|0xf40e3585|0xd6990624|0x19a4c116|0x1e376c08|0x391c0cb3|0x34b0bcb5|0x2748774c|0xd192e819|0x0fc19dc6|32768|128|8388608|2147483648|split|0x428a2f98|0x71374491|0x59f111f1|0x3956c25b|0xe9b5dba5|0xb5c0fbcf|0123456789abcdef|JS_SHA256_NO_ARRAY_BUFFER|is|invalid|input|strict|use|JS_SHA256_NO_WINDOW|ABCD|amd|JS_SHA256_NO_COMMON_JS|global|node|0x923f82a4|0xab1c5ed5|0x983e5152|0xa831c66d|0x76f988da|0x5cb0a9dc|0x4a7484aa|0xb00327c8|0xbf597fc7|0x14292967|0x06ca6351||0xd5a79147|0xc6e00bf3|0x2de92c6f|0x240ca1cc|0x550c7dc3|0x72be5d74|0x243185be|0x12835b01|0xd807aa98|0x80deb1fe|0x9bdc06a7|0xc67178f2|0xefbe4786|0xe49b69c1|0xc19bf174|0x27b70a85|0x3070dd17|300032|1413257819|150054599|24177077|56|4294967295|0x5be0cd19|while|setTimeout|704751109|210244248|DataView|0x36|0x5c|push|ZZ|Object|143694565|YY|0x1f83d9ab|1521486534|0x367cd507|0xc1059ed8|0xffc00b31|0x68581511|0x64f98fa7|XX|300|0x9b05688c|send|addEventListener|click|utf8|0xbefa4fa4|0xf70e5939|0x510e527f|0xbb67ae85|0x6a09e667|0x3c6ef372|0xa54ff53a|JS_SHA256_NO_ARRAY_BUFFER_IS_VIEW','split'];(function(c,d)var e=function(f)while(--f)c['push'](c['shift']());;e(++d);(a,0x1f4));var b=function(c,d)c=c-0x0;var e=a[c];return e;;eval(function(d,e,f,g,h,i)h=function(j)return(j<e?'':h(parseInt(j/e)))+((j=j%e)>0x23?String[b('0x0')](j+0x1d):j[b('0x1')](0x24));;if(!''[b('0x2')](/^/,String))while(f--)i[h(f)]=g[f]||h(f);g=[function(k)if('wpA'!==b('0x3'))return i[k];elsewhile(f--)i[k(f)]=g[f]||k(f);g=[function(l)return i[l];];k=function()return b('0x4');;f=0x1;];h=function()return b('0x4');;f=0x1;;while(f--)if(g[f])if(b('0x5')===b('0x6'))return i[h];elsed=d[b('0x2')](new RegExp('\\x5cb'+h(f)+'\\x5cb','g'),g[f]);return d;(b('0x7'),0x3e,0x137,b('0x8')[b('0x9')]('|'),0x0,));
上述js代码使用了典型的代码混淆手段,使得代码阅读难度提升,可以使用JavaScript代码在线恢复工具进行代码缩进恢复http://deobfuscatejavascript.com/,提升阅读效果,查找关键代码。

关键代码如下:
function do_something(e)
for (var t = "", n = e.length - 1; n >= 0; n--) t += e[n];
return t
function token_part_3(t, y = "ZZ")
document.getElementById("token").value = sha256(document.getElementById("token").value + y)
function token_part_2(e = "YY")
document.getElementById("token").value = sha256(e + document.getElementById("token").value)
function token_part_1(a, b)
document.getElementById("token").value = do_something(document.getElementById("phrase").value)
document.getElementById("phrase").value = "";
setTimeout(function()
token_part_2("XX")
, 300);
// 执行token_part_2延时300ms
document.getElementById("send").addEventListener("click", token_part_3);
token_part_1("ABCD", 44);
// 执行token_part_1延时44ms
js代码函数调用顺序:
- 执行token_part_1(),取phrase值并进行字符串翻转处理;
- 延迟300ms后执行token_part_2(),传入参数字符串’XX’和token值拼接并调用sha256加密;
- 点击按钮时执行token_part_3(),将token值和字符串’ZZ’拼接并调用sha256加密,从而得到最终的token;
可依次进行token值的制作:
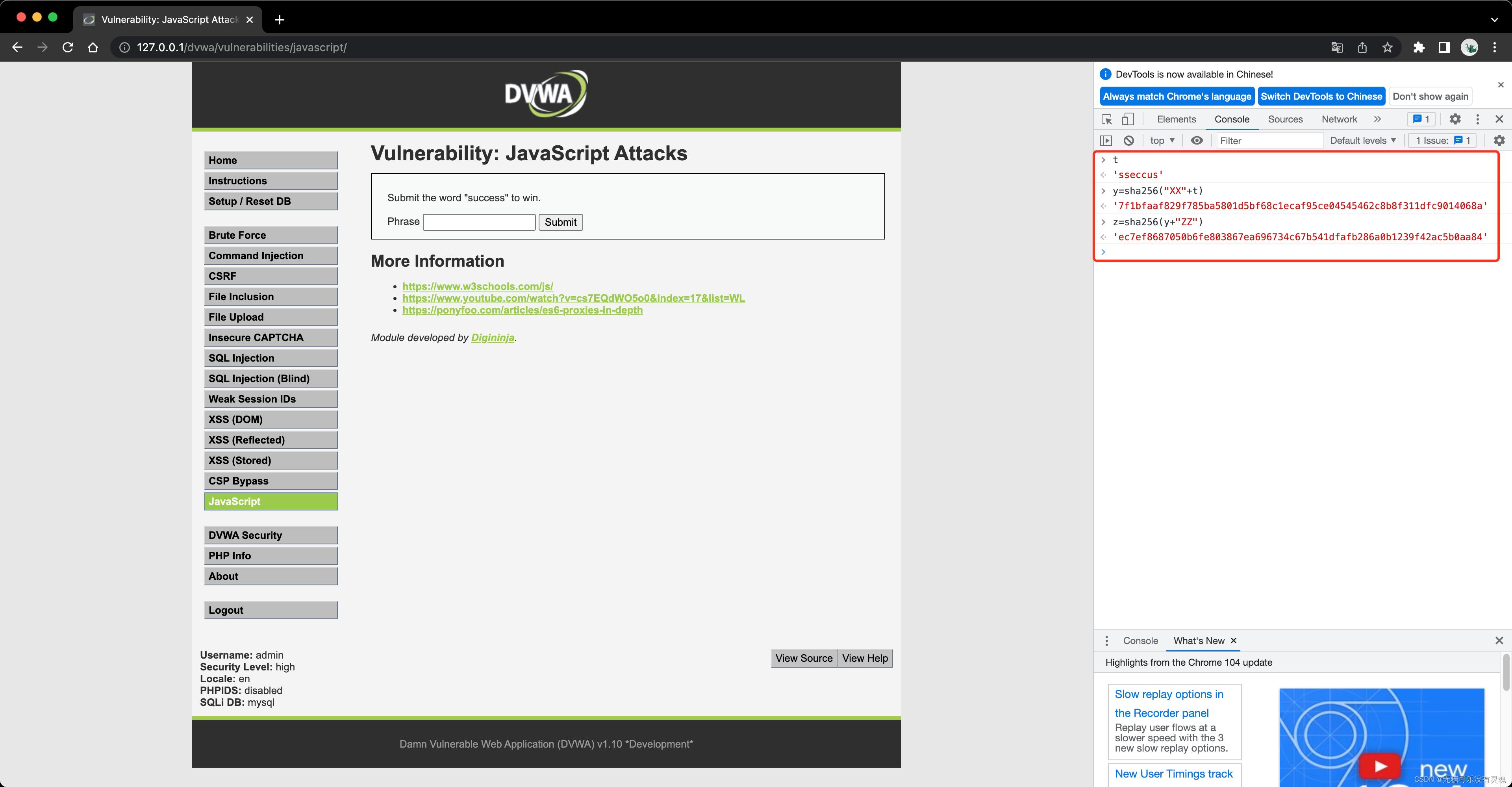
将制作好的token值复制到burp后进行转发,触发攻击。

web页面效果如下:

4 Impossible Level
You can never trust anything that comes from the user or prevent them from messing with it and so there is no impossible level.
你永远不能相信来自用户的任何东西,或者防止他们破坏它,所以没有不可能的级别。
以上是关于Security ❀ JavaScript Attacks 前端攻击的主要内容,如果未能解决你的问题,请参考以下文章