计算机英语讲课笔记02
Posted howard2005
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了计算机英语讲课笔记02相关的知识,希望对你有一定的参考价值。
文章目录
- I. The Result of Sign-in
- II. Arithmetic Operations
- III. Big Data
- IV. Security
- V. How to Memorize Words Effectively?
- VI. After-class Reading Materials
I. The Result of Sign-in
- At the beginning of the class, I will do the sign-in to make sure whether everybody is here (present).
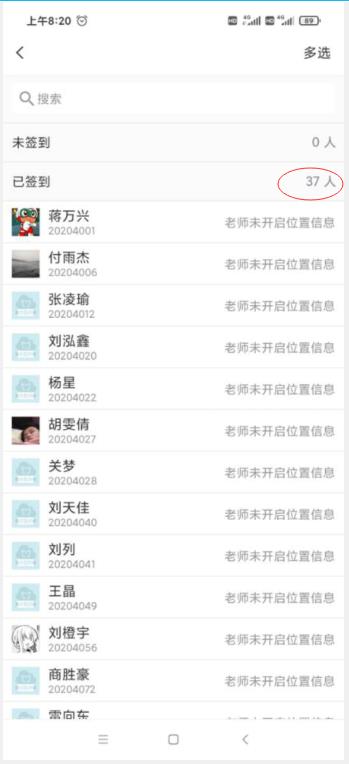
- This time, let’s take a look at the result of the sign-in.
- There are
thirty-ninestudents in our class, but onlythirty-sevenstudents have joined my cloud class. - Thirty-seven students have signed in this time. Another two students joined our cloud class just now.
II. Arithmetic Operations
1. Addition
add (v.) ⟹ \\Longrightarrow ⟹ addition (n.) ⟹ \\Longrightarrow ⟹ additional (adj.)
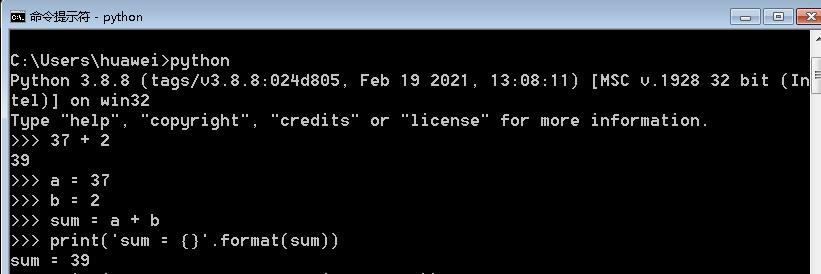
How to say 37 + 2 = 39 in English?
- Daily English: If you
addtwotothirty-seven, you will get thirty-nine. - Math English: Thirty-seven
plustwoequalsthirty-nine. - Use Python to do the addition
2. Subtraction
subtract (v.) ⟹ \\Longrightarrow ⟹ subtraction (n.)
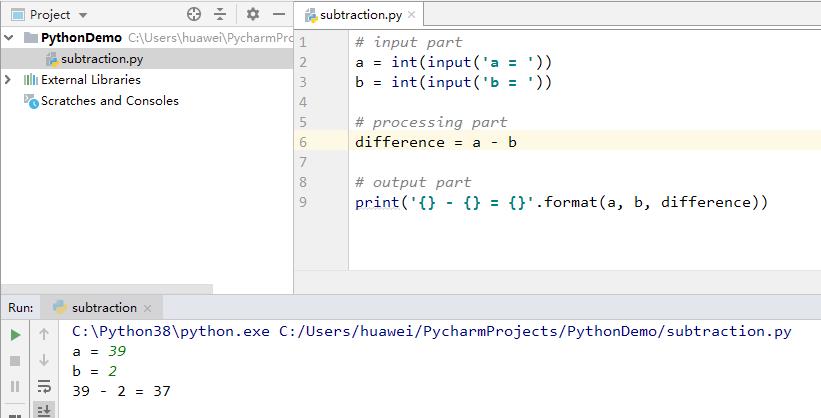
How to say 39 - 2 = 37 in English?
- Daily English: If you
subtracttwofromthirty-seven, you will get thirty-seven. - Math English: Thirty-nine
minustwoequalsthirty-seven. - Use a Python program to do the subtraction
- Life ⟹ \\Longrightarrow ⟹ Math ⟹ \\Longrightarrow ⟹ Computer (Program → \\rightarrow → Software)
3. Multiplication
multiply (v.)
⟹
\\Longrightarrow
⟹ multiplication (n.)
multiply (v.)
⟹
\\Longrightarrow
⟹ multiple (adj.)
single
⟹
\\Longrightarrow
⟹ double
⟹
\\Longrightarrow
⟹ multiple
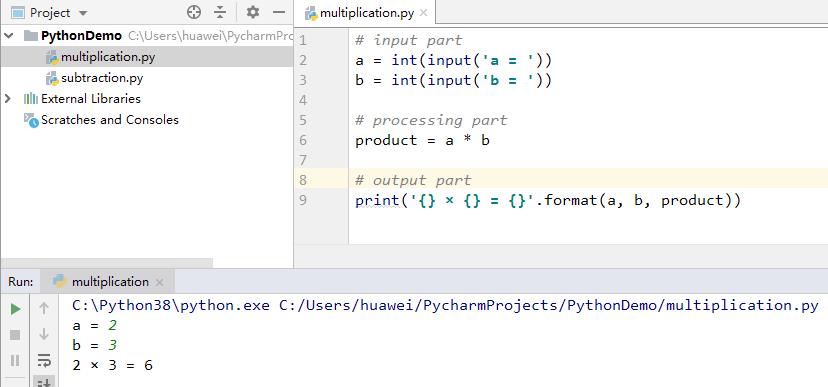
How to say 2 × 3 = 6 in English?
- Daily English: If you
multiplytwobythree, you will get six. - Math English: Two
timesthreeequalssix. - Use a Python program to do the multiplication
4. Division
divide (v.) ⟹ \\Longrightarrow ⟹ division (n.)
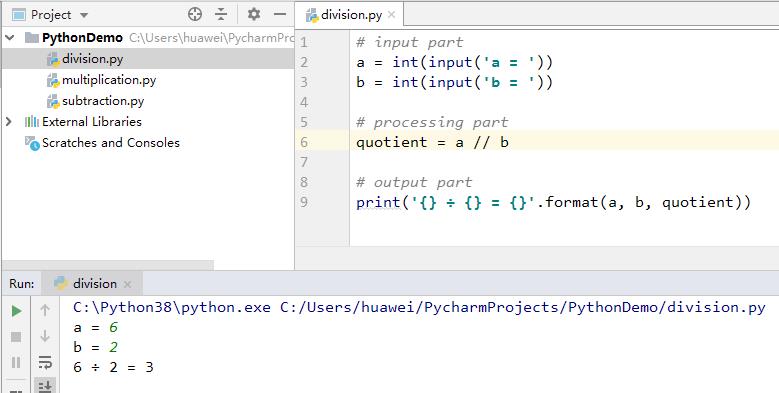
How to say 6 ÷ 2 = 3 in English?
- Daily English: If you
dividesixbytwo, you will get three. - Math English: Six
divided bytwoequalstwo. - Use a Python program to do the division
III. Big Data
Now we are living in an era of big data.
大数据学习笔记:Hadoop生态系统 (Hadoop Ecosystem)
- Structured Data (SQL DataBase) ⟹ \\Longrightarrow ⟹ mysql, Oracle, SQL Server, DB2 …
- Non-Structured Data ⟹ \\Longrightarrow ⟹ NoSQL (Redis, HBase, MongoDB, …), Text, Picture, Photo, Video, Sound…
Four Types of Keys in Tables
- Primary Key - id (identity)
- Candidate Key
- Unique Key
- Regular Key
IV. Security
1. Three Levels of Security
- Data Security ⟹ \\Longrightarrow ⟹ Software Security ⟹ \\Longrightarrow ⟹ Network Security
- Personal Security ⟹ \\Longrightarrow ⟹ Social Security ⟹ \\Longrightarrow ⟹ National Security
2. Two Technologies for Security
- Authentication 认证 - membership(成员)
- Authorization 授权 - authority (权限)
V. How to Memorize Words Effectively?
1. Master Word Formation
The most important method for word formation is derivation. 派生是最重要的一种构词法。
Prefix + Root + Suffix
- Nation – national - international - internationalize – internationalization (i18n)
2. Memorize Words Syllable by Syllable
We’d better memorize words syllable by syllable, not letter by letter.

3. Learn Words in Sentences or Articles
- In the sentences or articles we can really learn how to use the words properly. If your really want to enlarge your vocabulary, the best way is not reciting new words but doing extensive reading in various fields, especially reading the materials in which you have real interest.
VI. After-class Reading Materials
Computer Security
The process of ensuring confidentiality, integrity, and availability of computers, their programs, hardware devices, and data. Lack of security results from a failure of one of these three properties. The lack of confidentiality is unauthorized disclosure of data or unauthorized access to a computing system or a program. A failure of integrity results from unauthorized modification of data or damage to a computing system or program. A lack of availability of computing resources results in what is called denial of service.
An act or event that has the potential to cause a failure of computer security is called a threat. Some threats are effectively deflected by countermeasures called controls. Kinds of controls are physical, administrative, logical, cryptographic, legal, and ethical. Threats that are not countered by controls are called vulnerabilities.
1. Encryption
Encryption is a very effective technique for preserving the secrecy of computer data, and in some cases it can also be employed to ensure integrity and availability. An encrypted message is converted to a form presumed unrecognizable to unauthorized individuals. The principal advantage of encryption is that it renders interception useless. See Cryptography
2. Access Control
Computer security implies that access be limited to authorized users. Therefore, techniques are required to control access and to securely identify users. Access controls are typically logical controls designed into the hardware and software of a computing system. Identification is accomplished both under program control and by using physical controls.
Typically, access within a computing system is limited by an access control matrix administered by the operating system or a processing program. All users are represented as subjects by programs executing on behalf of the users; the resources, called the objects of a computing system, consist of files, programs, devices, and other items to which users’ accesses are to be controlled. The matrix specifies for each subject the objects that can be accessed and the kinds of access that are allowed.
Access control as described above relates to individual permissions. Typically, such access is called discretionary access control because the control is applied at the discretion of the object’s owner or someone else with permission. With a second type of access control, called mandatory access control, each object in the system is assigned a sensitivity level, which is a rating of how serious would be the consequences if the object were lost, modified, or disclosed, and each subject is assigned a level of trust.
Access control is not necessarily as direct as just described. Unauthorized access can occur through a covert channel. One process can signal something to another by opening and closing files, creating records, causing a device to be busy, or changing the size of an object. All of these are acceptable actions, and so their use for covert communication is essentially impossible to detect, let alone prevent.
3. Security of Programs
Computer programs are the first line of defense in computer security, since programs provide logical controls. Programs, however, are subject to error, which can affect computer security.
A computer program is correct if it meets the requirements for which it was designed. A program is complete if it meets all requirements. Finally, a program is exact if it performs only those operations specified by requirements.
Simple programmer errors are the cause of most program failures. Fortunately, the quality of software produced under rigorous design and production standards is likely to be quite high. However, a programmer who intends to create a faulty program can do so, in spite of development controls. See Software engineering
A salami attack is a method in which an accounting program reduces some accounts by a small amount, while increasing one other account by the sum of the amounts subtracted. The amount reduced is expected to be insignificant; yet, the net amount summed over all accounts is much larger.
Some programs have intentional trapdoors, additional undocumented entry points. If these trapdoors remain in operational systems, they can be used illicitly by the programmer or discovered accidentally by others.
A Trojan horse is an intentional program error by which a program performs some function in addition to its advertised use. For example, a program that ostensibly produces a formatted listing of stored files may write copies of those files on a second device to which a malicious programmer has access.
A program virus is a particular type of Trojan horse that is self-replicating. In addition to performing some illicit act, the program creates a copy of itself which it then embeds in other, innocent programs. Each time the innocent program is run, the attached virus code is activated as well; the virus can then replicate and spread itself to other, uninfected programs. Trojan horses and viruses can cause serious harm to computing resources, and there is no known feasible countermeasure to halt or even detect their presence.
4. Security of Operating Systems
Operating systems are the heart of computer security enforcement. They perform most access control mediation, most identification and authentication, and most assurance of data and program integrity and continuity of service.
Operating systems structured specifically for security are built in a kernelized manner, embodying the reference monitor concept. A kernelized operating system is designed in layers. The innermost layer provides direct access to the hardware facilities of the computing system and exports very primitive abstract objects to the next layer. Each successive layer builds more complex objects and exports them to the next layer. The reference monitor is effectively a gate between subjects and objects. See Operating system
5. Security of Databases
Integrity is a much more encompassing issue for databases than for general applications programs, because of the shared nature of the data. Integrity has many interpretations, such as assurance that data are not inadvertently overwritten, lost, or scrambled; that data are changed only by authorized individuals; that when authorized individuals change data, they do so correctly; that if several people access data at a time, their uses will not conflict; and that if data are somehow damaged, they can be recovered.
Database systems are especially prone to inference and aggregation. Through inference, a user may be able to derive a sensitive or prohibited piece of information by deduction from nonsensitive results without accessing the sensitive information itself. Aggregation is the ability of two or more separate data items to be more (or less) sensitive together than separately. Various statistical methods make it very difficult to prevent inference, and aggregation is also extremely difficult to prevent, since users can access great volumes of data from a database over long periods of time and then correlate the data independently.
6. Security of Networks
As computing needs expand, users interconnect computers. Network connectivity, however, increases the security risks in computing. Whereas users of one machine are protected by some physical controls, with network access, a user can easily be thousands of miles from the actual computer. Furthermore, message routing may involve many intermediate machines, called hosts, each of which is a possible point where the message can be modified or deleted, or a new message fabricated. A serious threat is the possibility of one machine’s impersonating another on a network in order to be able to intercept communications passing through the impersonated machine.
The principal method for improving security of communications within a network is encryption. Messages can be encrypted link or end-to-end. With link encryption, the message is decrypted at each intermediate host and reencrypted before being transmitted to the next host. End-to-end encryption is applied by the originator of a message and removed only by the ultimate recipient.
To benefit from sharing access to computing systems that are not all located together, organizations have established virtual private networks (VPNs). These networks approach the security of a private network at costs closer to those of shared public resources. The primary security technique used is encryption.
The Internet, or any similar public network, is subject to threats to its availability, integrity, and confidentiality. A complicating feature is that there is effectively no control on transmissions over the Internet. Consequently, a system connected to the Internet is exposed to any malicious attack that any other Internet user wants to launch.
7. Security Perimeter
A security perimeter is a logical boundary surrounding all resources that are controlled and protected. The protected resources are called a domain (or enclave or protected subnetwork). There may be overlapping domains of varying protection, so that the most sensitive resources are in the innermost domain, which is the best protected. Protecting the security perimeter may be physical controls, identification and authentication, encryption, and other forms of access control. Two controls that relate especially to the security perimeter are network vulnerability scanning and firewalls.
A network vulnerability scan is the process of determining the connectivity of the subnetwork within a security perimeter, and then testing the strength of protection at all the access points to the subnetwork. With a network domain, if a forgotten access point is not secured, its weakness can undermine the protection of the rest of the domain. A network scanner maps the connectivity of a domain, typically by probing from outside the domain, to determine what resources are visible from the outside. Once all outside connections are identified, each is tested with a range of attacks to determine the vulnerabilities to which it is susceptible and from which it needs to be better protected.
A firewall is a host that fuctions as a secured gateway between a protected enclave and the outside. The firewall controls all traffic according to a predefined access policy. For example, many firewalls are configured to allow unhindered communication outbound (from the protected domain to a destination outside the domain) but to allow only certain kinds of inbound communication. A firewall can be a separate computer, or firewall functionality can be built into the communications switch connecting the enclave to the external network.
8. Intrusion Detection
It is most effective to eliminate vulnerabilities, but if that is not possible, it is then desirable to recognize that an attack is occuring or has occured, and take action to prevent future attacks or limit the damage from the current one. Intrusion detection can be either anomaly detection, which seeks to identify an attack by behavior that is out of the norm, or misuse detection, to identify an attack by its attempted effect on sensitive resources. Intrusion detection systems monitor a computing system in order to warn of an attack that is imminent, is under way, or has occurred.
以上是关于计算机英语讲课笔记02的主要内容,如果未能解决你的问题,请参考以下文章