nginx ssl 更换问题
Posted wawahan
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了nginx ssl 更换问题相关的知识,希望对你有一定的参考价值。
公司之前使用的是免费startssl证书,听说ios 以后不信任这些免费的验证不严格的证书,公司果断购买了一个统配域名证书,其实不用貌似也没什么事,主要是提交app的时候得说明理由,被拒的可能性比较大。
在更换证书前想着保留原来免费的证书,然后使用新域名做测试。结果新域名使用了新证书,测试包老是不通过
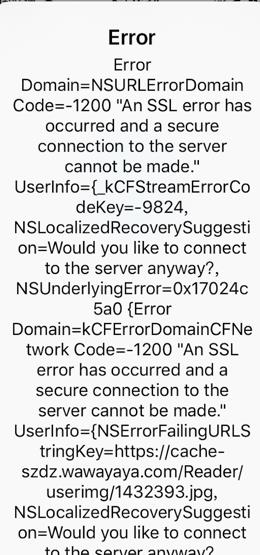
我就纳闷了~怎么就不成了,到网上搜索到的问题都是说使用的是TLS1 ,而IOS要求是TLS1.2 。但是修改nginx配置,又重新编译nginx升级openssl版本
server
{
listen 443 ssl;
include ex_ssl.conf;
server_name www.ex.com;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
....
}
ex_ssl.conf
ssl on; ssl_certificate /path/to/crt/ex.com.crt; ssl_certificate_key /path/to/crt/ex.com.key;
而且肯定的是crt 文件和 key都没有问题
试了很多方法后使用了一条命令,才发现蹊跷所在
还好这条命令救了命了!
openssl s_client -connect you.domain.com:443
这条命令可以查看你的证书内容
看到以后看到了,虽然我使用了新的域名,但是解析以后,nignx还是匹配到了老域名的server中。证书内容是苹果不信任的那个证书,也就是应该不支持TLS1.2,就算我配置了TLS1.2,还是走的TLS1

~ openssl s_client -connect new.domain.com:443 CONNECTED(00000003) depth=2 /C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE6\\xA0\\xB9\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 verify error:num=20:unable to get local issuer certificate verify return:0 --- Certificate chain 0 s:/CN=old.domain.com.cn i:/C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE5\\x85\\x8D\\xE8\\xB4\\xB9SSL\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 G2 1 s:/C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE5\\x85\\x8D\\xE8\\xB4\\xB9SSL\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 G2 i:/C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE6\\xA0\\xB9\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 2 s:/C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE6\\xA0\\xB9\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 i:/C=IL/O=StartCom Ltd./OU=Secure Digital Certificate Signing/CN=StartCom Certification Authority --- Server certificate -----BEGIN CERTIFICATE----- MIIE2jCCA8KgAwIBAgIQWIvbLAj1ZlJ0SiUTwM+HYTANBgkqhkiG9w0BAQsFADBP MQswCQYDVQQGEwJDTjEaMBgGA1UEChMRV29TaWduIENBIExpbWl0ZWQxJDAiBgNV BAMMG0NBIOayg+mAmuWFjei0uVNTTOivgeS5piBHMjAeFw0xNjA1MTAwNzQxMTRa Fw0xODA1MTAwNzQxMTRaMB4xHDAaBgNVBAMME3BheS5za3l4bGluay5jb20uY24w ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC5qPSW1whnRnJtLB2nfL6F 18O3/pb2hAf7TJTDR6iqKEj/TIuuQTg2JYG+yHQCJTSjUwjK4wFKjyNharFkGCru LmPVYDr/fL8Q0VBCj7ST8KwJ1u61/FcGuFxXkTAXXrRMTvf7EOPqaZBW/YzZm6ln P0VsmnthfAIW1m4vxesB12DLJIigOvSdGC8w+Blcb1zwP/TnH65/0GRoL2dC9iO/ y2E2eALfYxbhQXjegJHy6jam1L/hN8yKP9JRjxWkg4k7xmDRSDU36/9vBq5mGAy0 VrndXzPCVmgW00mbLcyr149f9Z4oMADHH8suUi/OtebEvLd62uOs5EG/WtMv1P2z AgMBAAGjggHhMIIB3TAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUH AwIGCCsGAQUFBwMBMAkGA1UdEwQCMAAwHQYDVR0OBBYEFHgm8Y6dMdKihXYvYUEz ZLlTvPXGMB8GA1UdIwQYMBaAFDDadIbzKJBWntcxMcK9Wc2TEjkdMH8GCCsGAQUF BwEBBHMwcTA1BggrBgEFBQcwAYYpaHR0cDovL29jc3AyLndvc2lnbi5jbi9jYTJn Mi9zZXJ2ZXIxL2ZyZWUwOAYIKwYBBQUHMAKGLGh0dHA6Ly9haWEyLndvc2lnbi5j bi9jYTJnMi5zZXJ2ZXIxLmZyZWUuY2VyMD4GA1UdHwQ3MDUwM6AxoC+GLWh0dHA6 Ly9jcmxzMi53b3NpZ24uY24vY2EyZzItc2VydmVyMS1mcmVlLmNybDBPBgNVHREE SDBGghNwYXkuc2t5eGxpbmsuY29tLmNughRzemR6LnNreXhsaW5rLmNvbS5jboIZ Y2FjaGVzemR6LnNreXhsaW5rLmNvbS5jbjBPBgNVHSAESDBGMAgGBmeBDAECATA6 BgsrBgEEAYKbUQEBAjArMCkGCCsGAQUFBwIBFh1odHRwOi8vd3d3Lndvc2lnbi5j b20vcG9saWN5LzANBgkqhkiG9w0BAQsFAAOCAQEAFRo81c/5Q3BKbSLyCxTOoYNh 2w2XlyPs3zaOJlOo/Cr9QACkOcqj2KBpOXfGBunLvMa9S5n9dzw3C3ltfPDI1hOZ XyJFsfv0JKk58Jbc6vKhS/JVcclTxQar5JM+9QoHkUPGMon69FzG9z16Ihbt/DxS TAlj/DC4p9c9Lw132HmMJONKs6o4+ipO/z9/zRi+EKCR8IOgEbzih7/50niBw++l oSZnbsCKotNwQVher4zfLAhdOPuMluW8kxTAj9+HFLK3sb9Bz+sRUdOpU9DuRzhx yYHO37HLuiZWNU/J4YkzJehyS52Dk+tBSOXz5yisIK92kIY8ila728qMpSilsQ== -----END CERTIFICATE----- subject=/CN=old.domain.com.cn issuer=/C=CN/O=WoSign CA Limited/CN=CA \\xE6\\xB2\\x83\\xE9\\x80\\x9A\\xE5\\x85\\x8D\\xE8\\xB4\\xB9SSL\\xE8\\xAF\\x81\\xE4\\xB9\\xA6 G2 --- No client certificate CA names sent --- SSL handshake has read 5000 bytes and written 328 bytes --- New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHA Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1 . <----------看这里 Cipher : DHE-RSA-AES256-SHA Session-ID: 692236B3DBEB590216BDFC115F4FF2B1AEBFB282D0205E25FE8E85078C72C64F Session-ID-ctx: Master-Key: 0A72976BDA8D92331C5873E49953C900C09AF680EF206522623D1424CC31A93D18964D771659AF9DA411188EF0D95C98 Key-Arg : None Start Time: 1482845223 Timeout : 300 (sec) Verify return code: 0 (ok) ---
好了,可以处理一下这个问题了。希望可以解决!
以上是关于nginx ssl 更换问题的主要内容,如果未能解决你的问题,请参考以下文章
