WebLogic 12c 二三事
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了WebLogic 12c 二三事相关的知识,希望对你有一定的参考价值。
写在前面的话,在前人的基础上,重新实践了一遍,有些是截取了部分总结,有些是照搬,原文请注意蓝色超链。
-
安装篇
关于WebLogic的安装,之前通过图形化的安装方式,部署WebService以后,通过不带WSDL地址访问WebService路径,会有一个TEST选项。(稍后补图) 后来项目正式环境没有图形化界面,只能静默安装,结果就没有这个TEST的选项,也不知道是为什么,无从下手该怎么搜索这个问题。
无论是图形化界面还是静默安装INSTALL_TYPE都选择的是一样的,为什么会出现这样的问题?百思不得其解。
静默安装的配置文件 (参考地址)
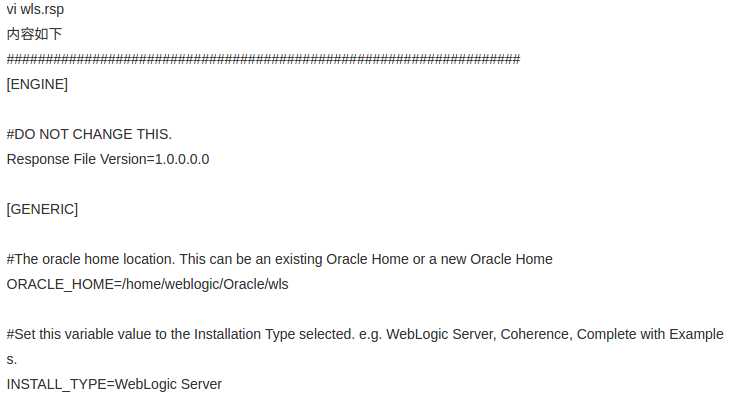
图形化安装
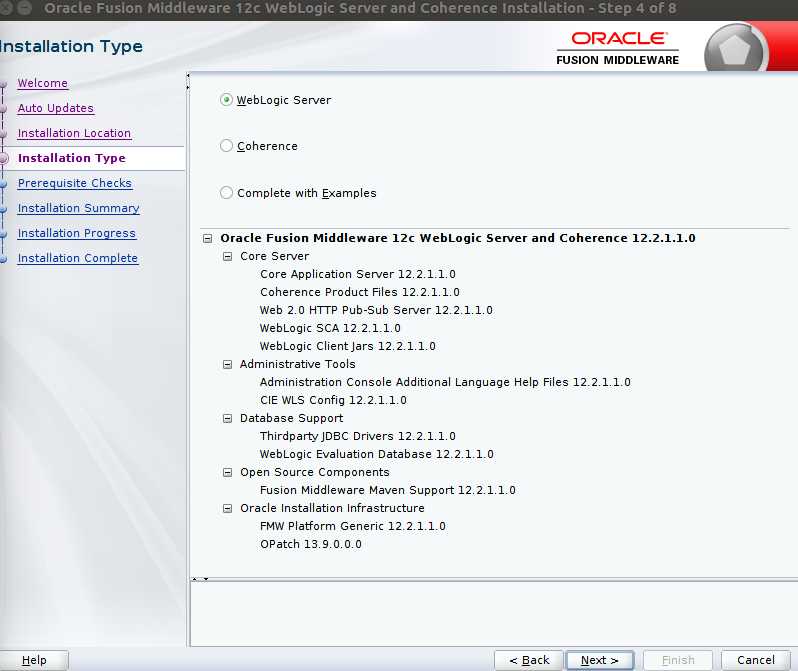
既然扯到静默安装,就多扯两句吧。静默安装后,再创建Domains 时有可能会出现如下状况。
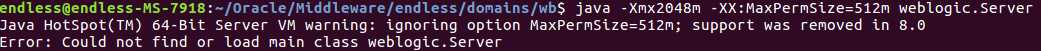
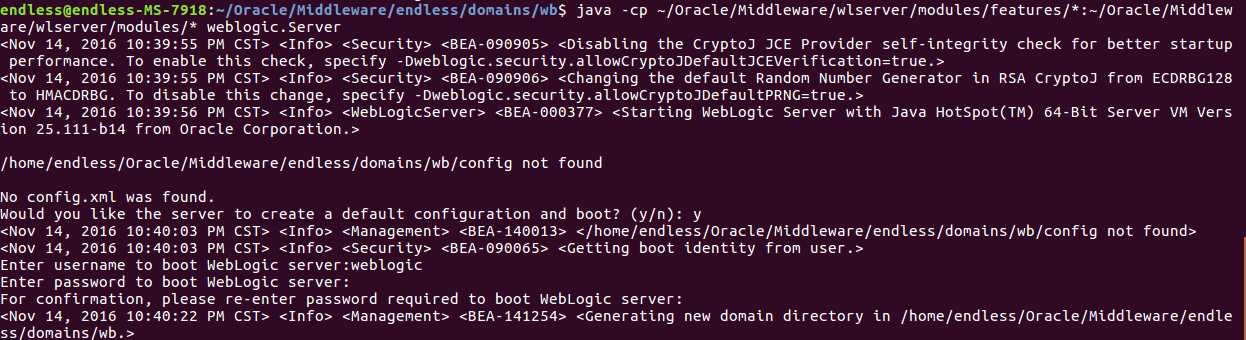
通过前人栽树,将路径补充完整。类似这样的命令解决此问题
java -cp /app/Oracle/Middleware/wlserver/modules/features/*:/app/Oracle/Middleware/wlserver/modules/* weblogic.Server
20161116 又偷懒了几天,不知道今天能否更新完,发现图片截取的太宽了,导致部分显示不全,原来模板这东西也需要与时俱进啊。
-
SSL证书
-
生成证书
项目快要上线了,来了一波第三方测试,被要求WebLogic启用SSL登录,并且需要修改控制台的默认登录路径。领导们肯定是不会在这上面花钱了,因为非必须嘛,只是为了通过测试,于是乎,度娘来帮忙,自制证书...
因为已经在Linux和HPXU上实验过,此处以Ubantu为例
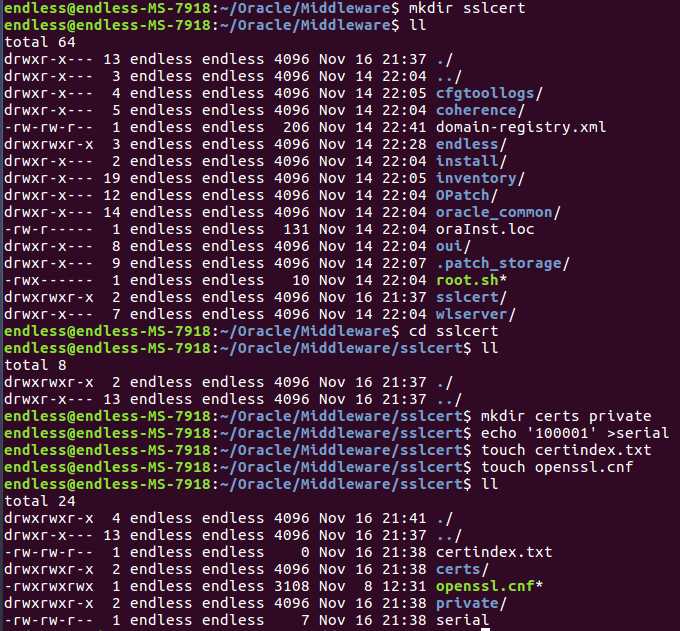
openssl.cnf文件内容(和原文的一样,我只是改了部分提示信息)

# # OpenSSL configuration file # # Working directory dir = . [ ca ] default_ca = CA_default [ CA_default ] serial = $dir/serial database = $dir/certindex.txt new_certs_dir = $dir/certs certificate = $dir/cacert.pem private_key = $dir/private/cakey.pem default_days = 365 default_md = sha1 preserve = no email_in_dn = no nameopt = default_ca certopt = default_ca policy = policy_match [ policy_match ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional [ req ] default_bits = 2048 # Size of keys default_keyfile = key.pem # name of generated keys default_md = sha1 # message digest algorithm string_mask = nombstr # permitted characters distinguished_name = req_distinguished_name req_extensions = v3_req [ req_distinguished_name ] # Variable name Prompt string #------------------------- ---------------------------------- 0.organizationName = Organization Name (company) organizationalUnitName = Organizational Unit Name (department, division) emailAddress = Email Address emailAddress_max = 40 localityName = Locality Name (city, district) stateOrProvinceName = State or Province Name (full name) countryName = Country Name (2 letter code) countryName_min = 2 countryName_max = 2 commonName = Common Name (hostname, IP, or your name) commonName_max = 64 # Default values for the above, for consistency and less typing. # Variable name Value #------------------------ ------------------------------ 0.organizationName_default = ENDLESS organizationalUnitName_default = EBILL emailAddress_default = [email protected] localityName_default = Shanghai stateOrProvinceName_default = Shanghai countryName_default = CN [ v3_ca ] basicConstraints = CA:TRUE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer:always [ v3_req ] basicConstraints = CA:FALSE subjectKeyIdentifier = hash [ my_v3_ext ] basicConstraints = CA:true [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional
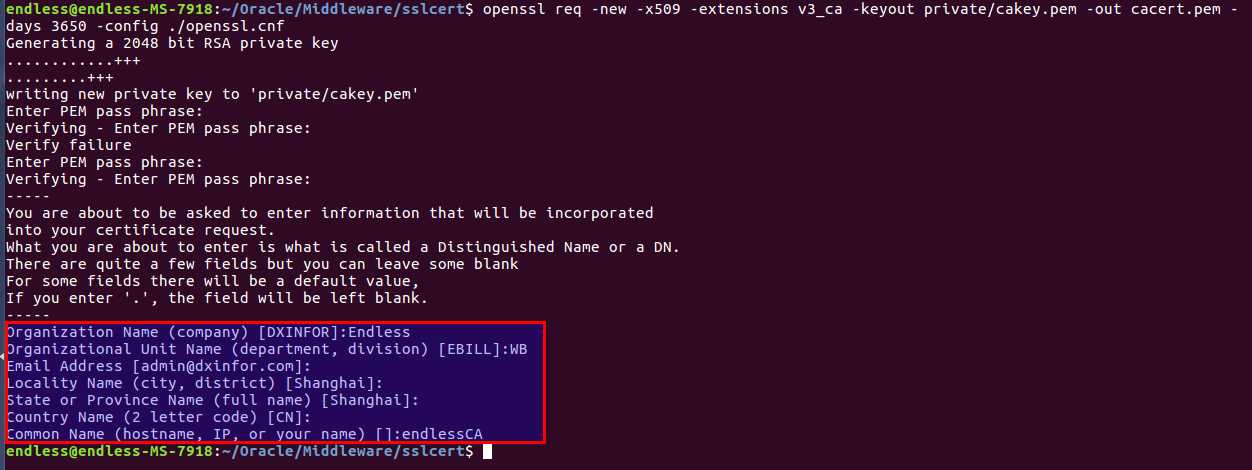
openssl req -new -x509 -extensions v3_ca -keyout private/cakey.pem -out cacert.pem -days 3650 -config ./openssl.cnf
此处的提示信息(红框部分)和前者文件openssl.cnf中的配置相关,有兴趣的可以自行研究。密码需要牢记,后面会用到。
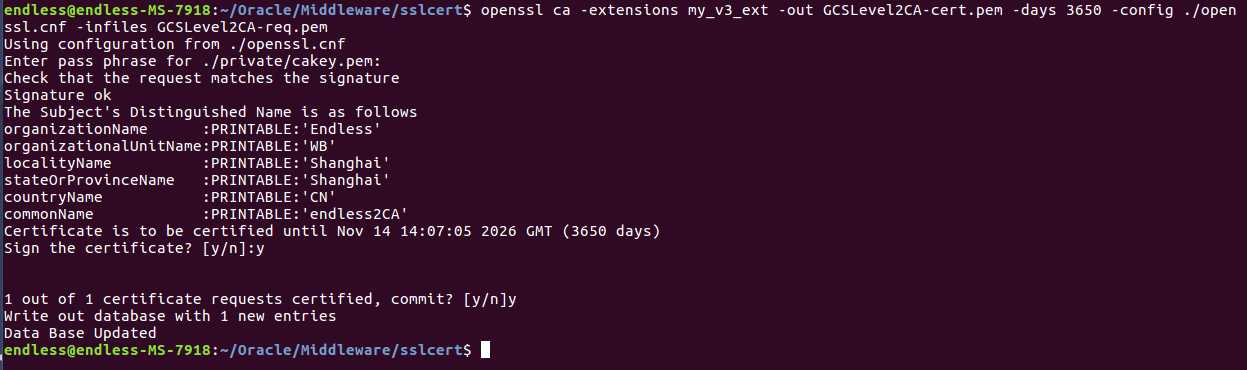
openssl req -new -nodes -out GCSLevel2CA-req.pem -keyout private/GCSLevel2CA-key.pem -pubkey -days 3650 -config ./openssl.cnf
和上图类似,只是最后Common Name需要与之前的区分,此处为二级证书。(endless2CA)
openssl ca -extensions my_v3_ext -out GCSLevel2CA-cert.pem -days 3650 -config ./openssl.cnf -infiles GCSLevel2CA-req.pem
确认之前的信息
一般填写本机IP,原文中填写的域名(未测试,应该是可以的),密码为第一步中输出的密码,文件名和key可以自定义,之前都是照着原作者Copy,这次尝试自定义文件名,但请注意前后对应。
keytool -genkey -dname "cn=127.0.0.1, ou=WB, o=Endless, c=CN" -keyalg RSA -keysize 2048 -alias wbkey -keypass 密码 -keystore wbkeystore.jks -storepass 密码 -validity 3650
keytool -certreq -alias wbkey -file wbkey-req.pem -keypass 密码 -storetype JKS -keystore wbkeystore.jks -storepass 密码
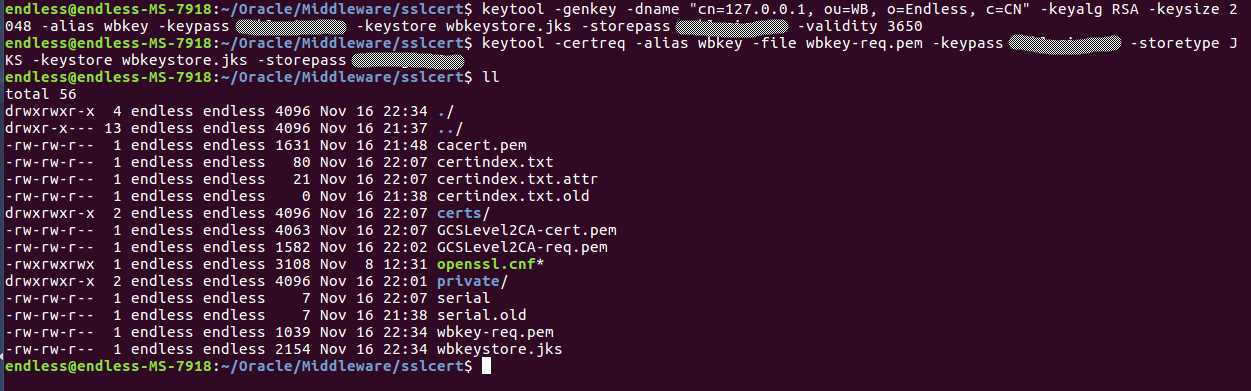
openssl ca -policy policy_anything -keyfile private/GCSLevel2CA-key.pem -cert GCSLevel2CA-cert.pem -days 3650 -config ./openssl.cnf -out wbkey.pem -infiles wbkey-req.pem
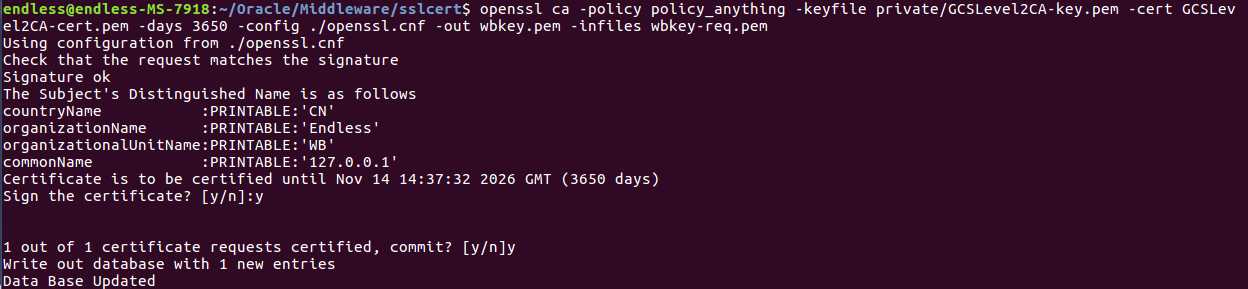
openssl crl2pkcs7 -nocrl -certfile wbkey.pem -certfile GCSLevel2CA-cert.pem -certfile cacert.pem -outform PEM -out wbkey.p7b
keytool -import -alias wbkey -file wbkey.p7b -keystore wbkeystore.jks
小插曲:自定义key以后的悲剧
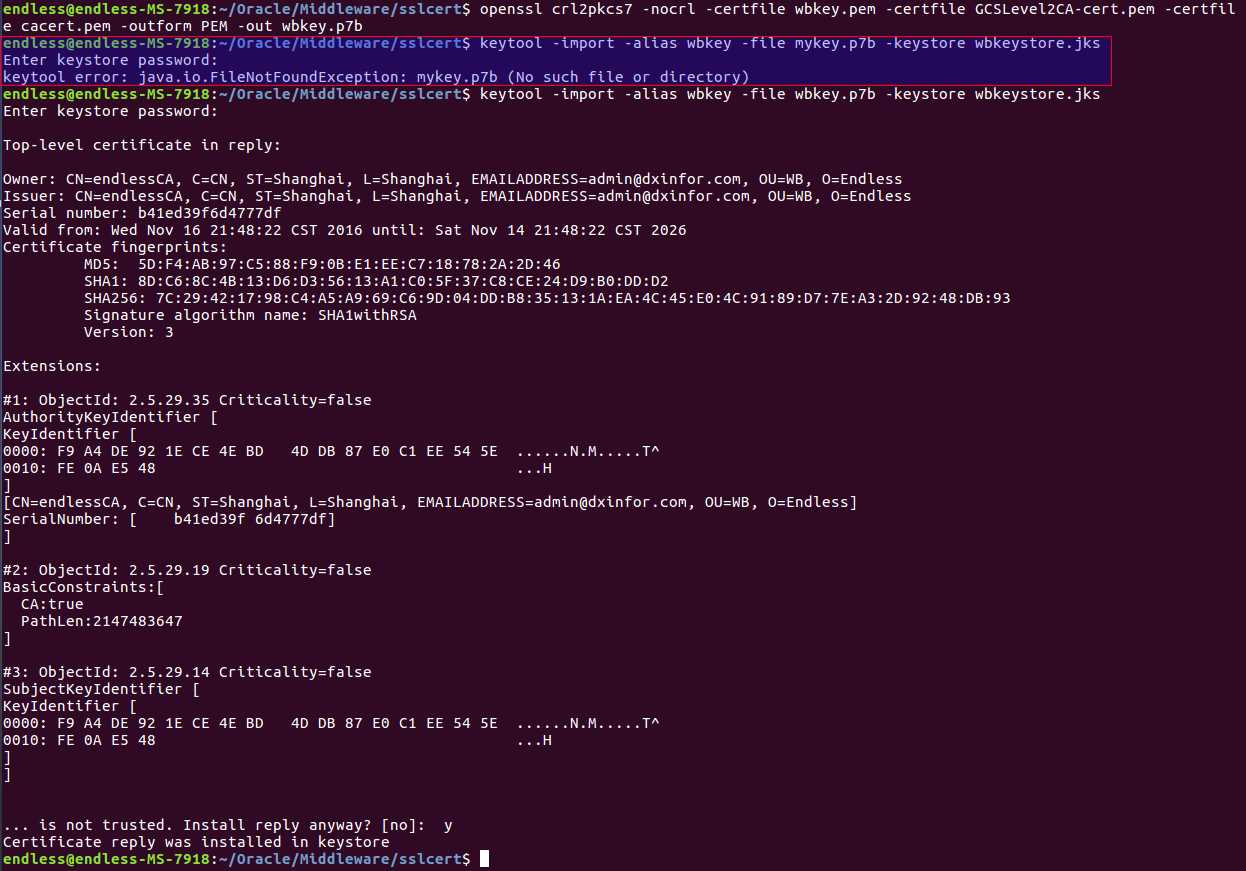
至此,证书算是自制完毕。检查之前输入的信息
keytool -list -keystore wbkeystore.jks -storepass 密码 -v

Keystore type: JKS Keystore provider: SUN Your keystore contains 1 entry Alias name: wbkey Creation date: Nov 16, 2016 Entry type: PrivateKeyEntry Certificate chain length: 3 Certificate[1]: Owner: CN=127.0.0.1, OU=WB, O=Endless, C=CN Issuer: CN=endless2CA, OU=WB, O=Endless, ST=Shanghai, C=CN Serial number: 100002 Valid from: Wed Nov 16 22:37:32 CST 2016 until: Sat Nov 14 22:37:32 CST 2026 Certificate fingerprints: MD5: 70:DB:F8:08:6B:23:B4:56:17:64:EF:04:D4:FF:29:13 SHA1: 27:12:91:C6:FD:8C:AC:9A:C1:27:8C:25:75:7D:09:8F:19:E9:CD:F4 SHA256: 03:4C:83:57:58:DF:0B:AF:C7:DC:0E:ED:66:37:83:E9:17:C0:C5:7C:D9:0F:5A:3F:0D:B7:B7:92:FC:F6:58:41 Signature algorithm name: SHA1withRSA Version: 1 Certificate[2]: Owner: CN=endless2CA, OU=WB, O=Endless, ST=Shanghai, C=CN Issuer: CN=endlessCA, C=CN, ST=Shanghai, L=Shanghai, [email protected], OU=WB, O=Endless Serial number: 100001 Valid from: Wed Nov 16 22:07:05 CST 2016 until: Sat Nov 14 22:07:05 CST 2026 Certificate fingerprints: MD5: 9D:39:81:C4:32:31:F0:24:84:E8:58:E5:5D:1A:AF:5F SHA1: F8:46:21:A7:69:1C:D6:59:CF:29:FF:1E:BC:89:B8:CF:BD:5E:FC:91 SHA256: 86:AB:F6:26:D5:B0:06:59:19:BD:C5:CA:49:39:BB:41:E6:32:D2:E4:0D:06:C6:E3:43:5F:17:97:8C:E1:5F:2A Signature algorithm name: SHA1withRSA Version: 3 Extensions: #1: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] Certificate[3]: Owner: CN=endlessCA, C=CN, ST=Shanghai, L=Shanghai, [email protected], OU=WB, O=Endless Issuer: CN=endlessCA, C=CN, ST=Shanghai, L=Shanghai, [email protected], OU=WB, O=Endless Serial number: b41ed39f6d4777df Valid from: Wed Nov 16 21:48:22 CST 2016 until: Sat Nov 14 21:48:22 CST 2026 Certificate fingerprints: MD5: 5D:F4:AB:97:C5:88:F9:0B:E1:EE:C7:18:78:2A:2D:46 SHA1: 8D:C6:8C:4B:13:D6:D3:56:13:A1:C0:5F:37:C8:CE:24:D9:B0:DD:D2 SHA256: 7C:29:42:17:98:C4:A5:A9:69:C6:9D:04:DD:B8:35:13:1A:EA:4C:45:E0:4C:91:89:D7:7E:A3:2D:92:48:DB:93 Signature algorithm name: SHA1withRSA Version: 3 Extensions: #1: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: F9 A4 DE 92 1E CE 4E BD 4D DB 87 E0 C1 EE 54 5E ......N.M.....T^ 0010: FE 0A E5 48 ...H ] [CN=endlessCA, C=CN, ST=Shanghai, L=Shanghai, [email protected], OU=WB, O=Endless] SerialNumber: [ b41ed39f 6d4777df] ] #2: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] #3: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: F9 A4 DE 92 1E CE 4E BD 4D DB 87 E0 C1 EE 54 5E ......N.M.....T^ 0010: FE 0A E5 48 ...H ] ] ******************************************* *******************************************
-
安装证书
登陆WebLogic,选择Environment->Servers->myserver
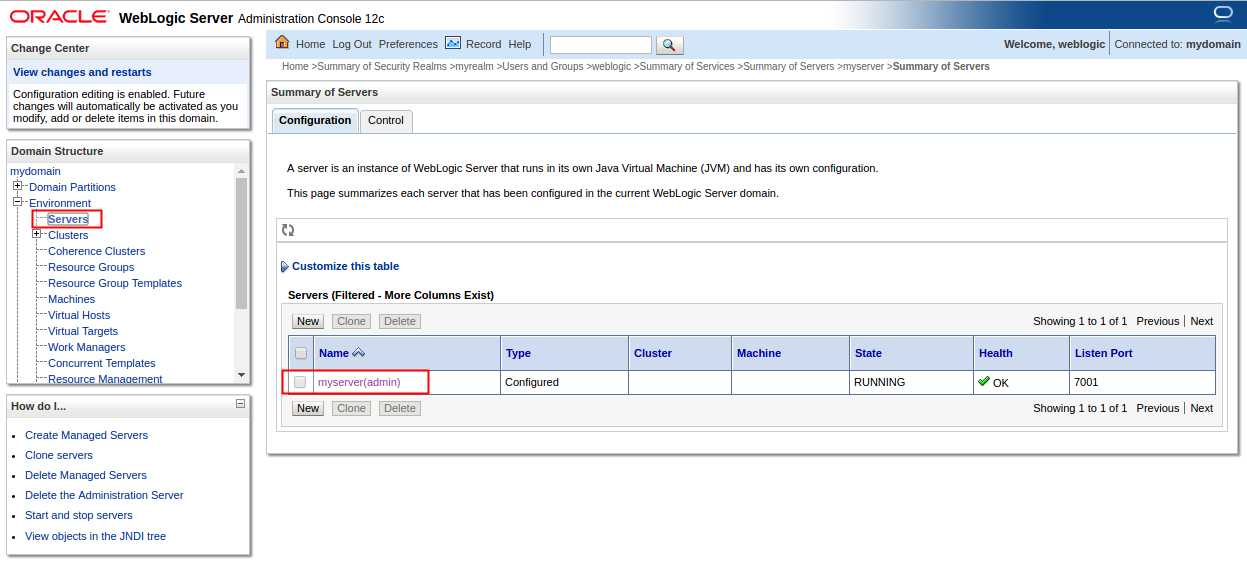
选择Keystores (密钥库)选项卡
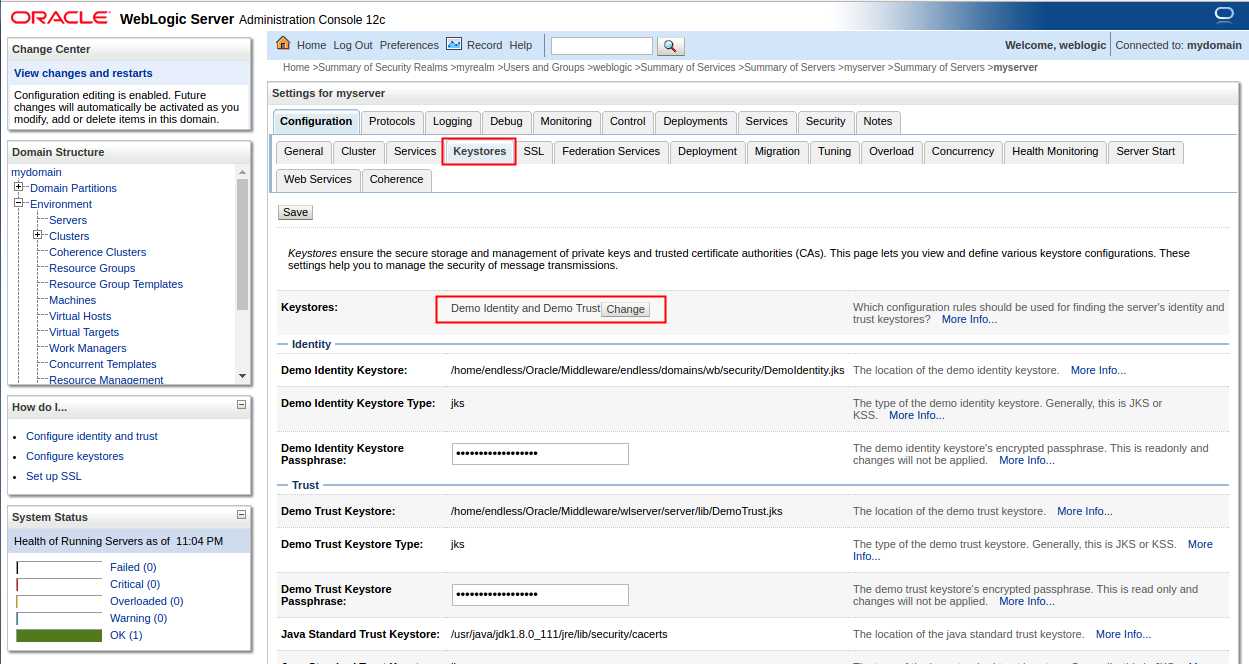
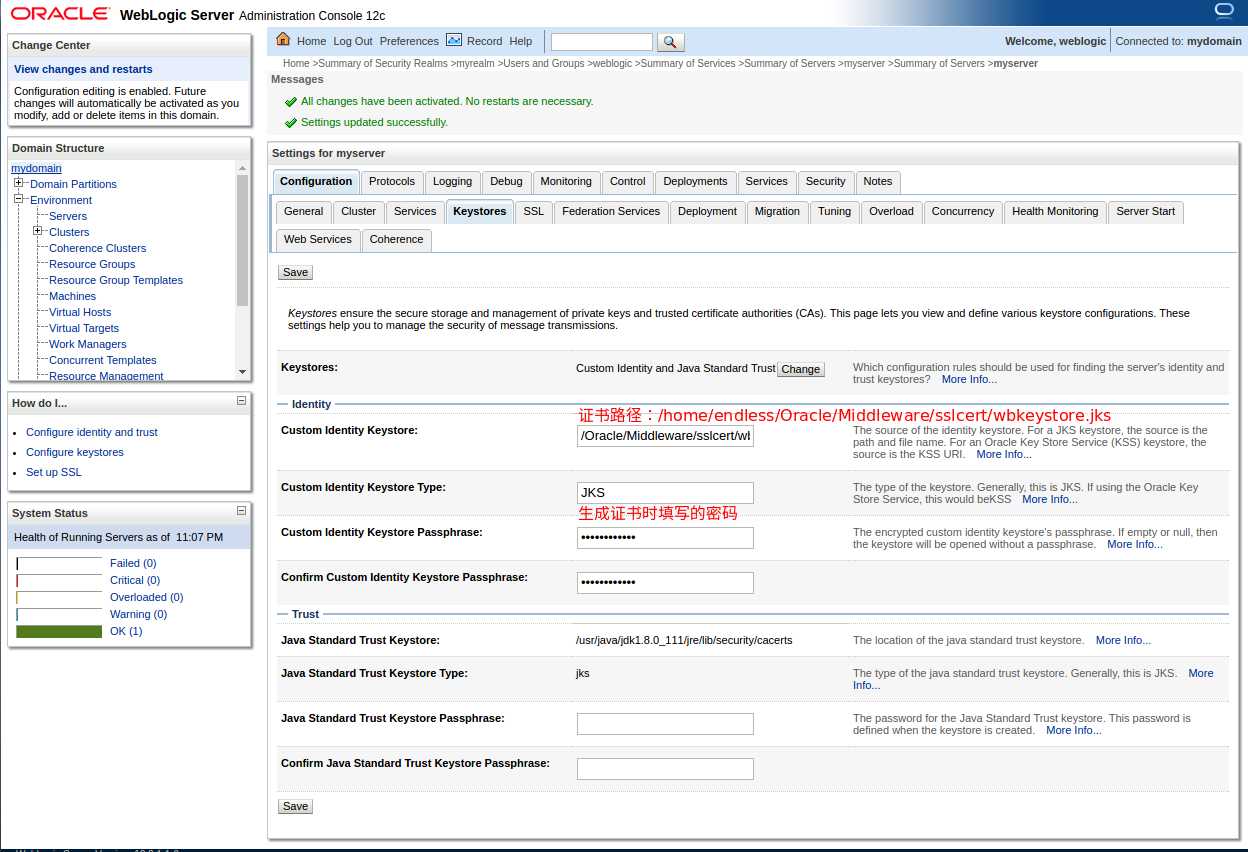
选择‘Custom Identity and Java Standard Trust’ (定制标识和Java标准信任)后点击保存,填空相应的信息再次点击保存。
选择SSL选项卡
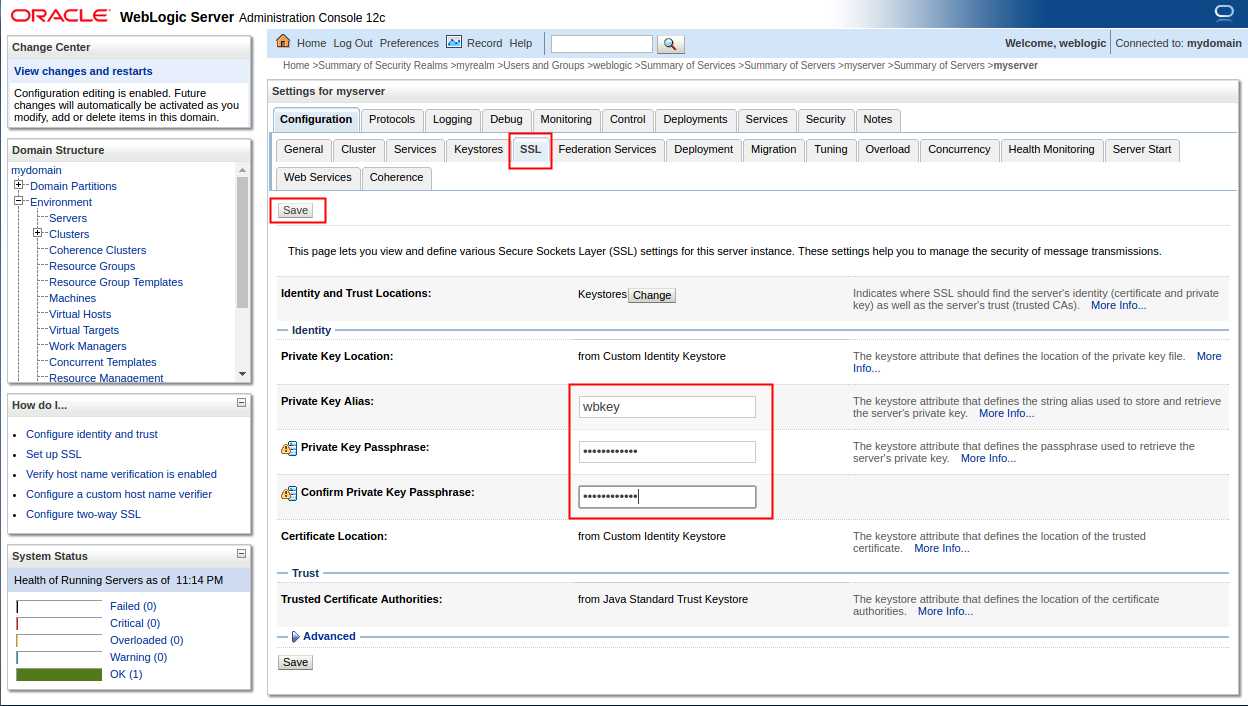
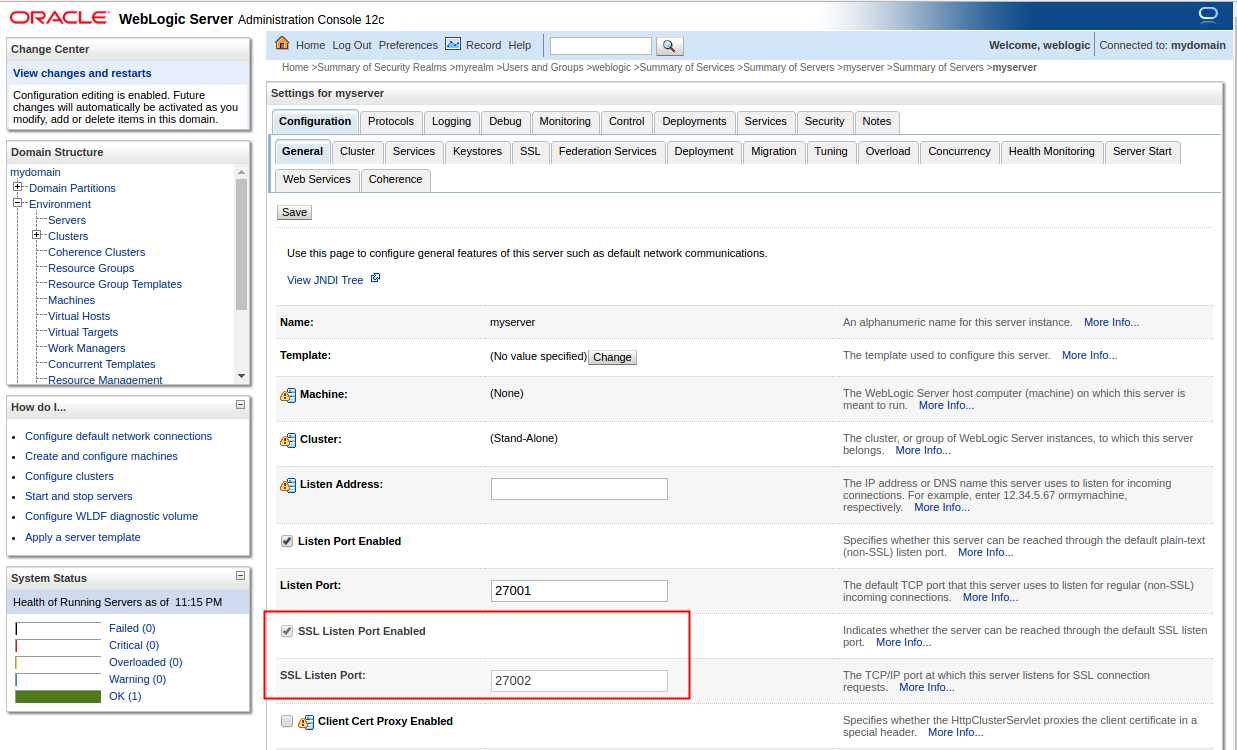
选择General (一般信息)选项卡,选中启用SSL监听端口,并指定端口后点击保存。
浏览器测试(IE中默认设置貌似是无法访问,会提示有风险,需要在高级设置中开启SSL、TLS)
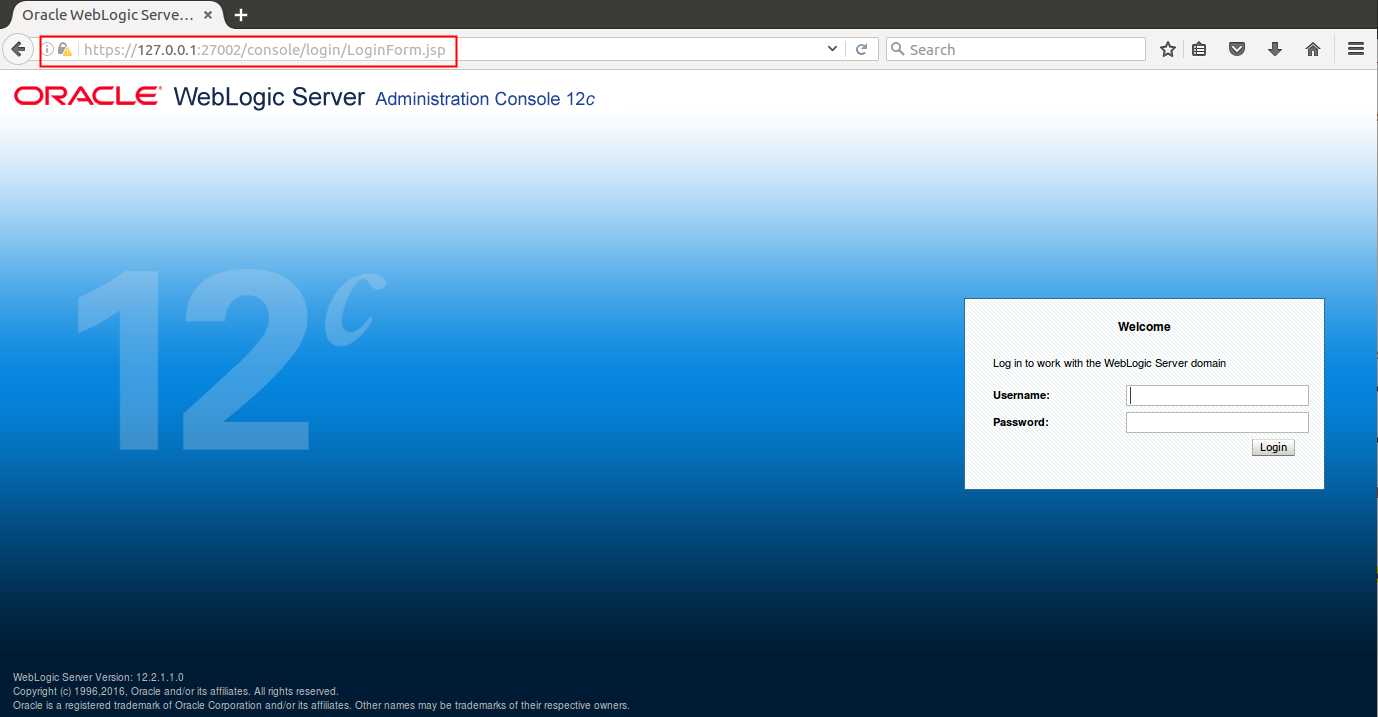
-
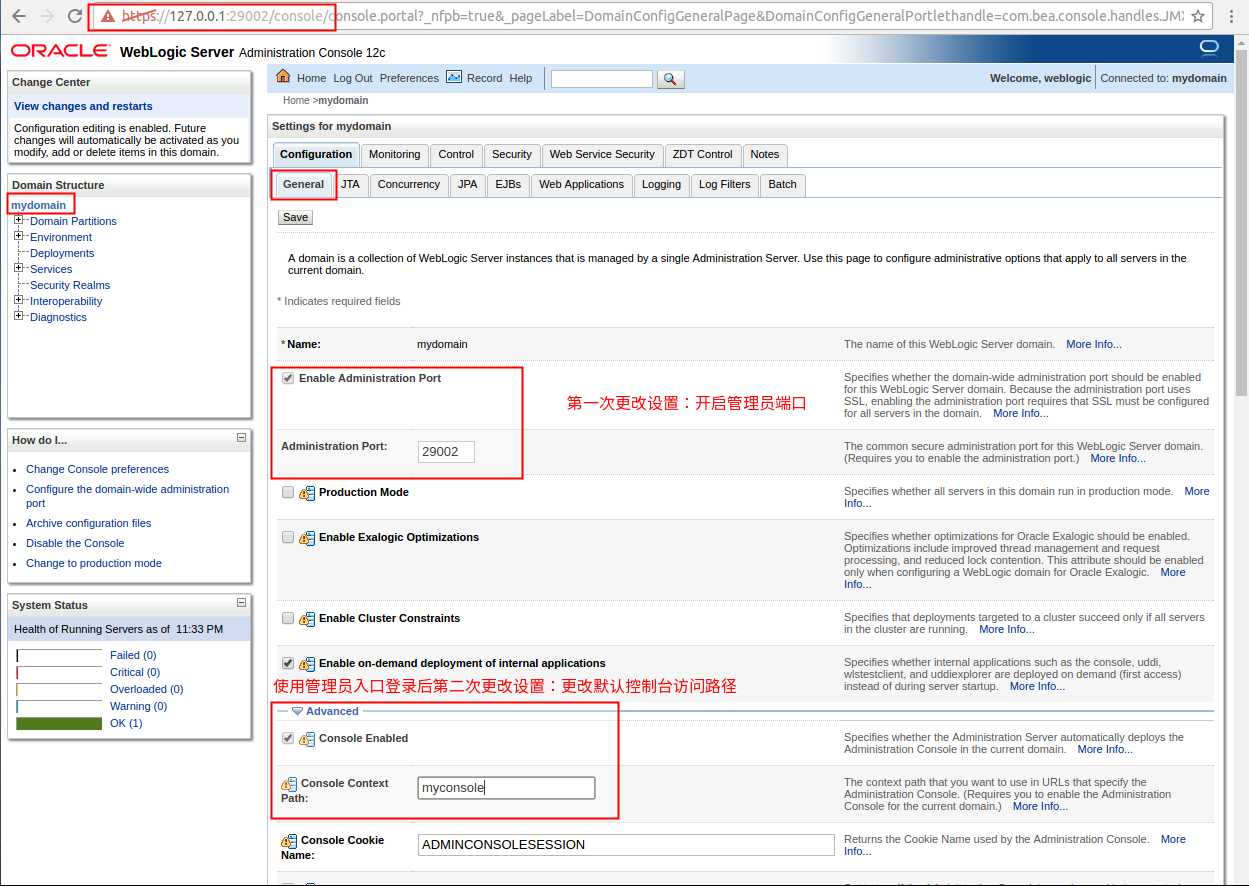
修改访问控制台默认路径
建议更改前备份自己的config.xml(位于../WebLogic_HOME/user_projects/domains/domain/config/config.xml)
先开启管理员入口,再次更改访问控制台的默认路径。
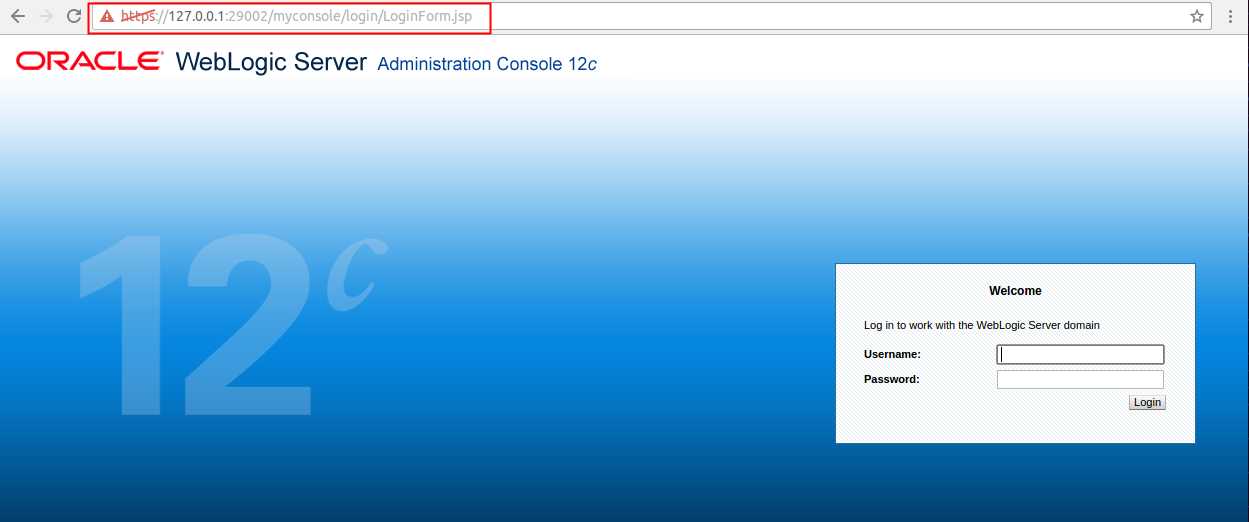
保存后重启WebLogic查看路径已改变
附上刚出炉的config.xml

<?xml version=‘1.0‘ encoding=‘UTF-8‘?> <domain xmlns="http://xmlns.oracle.com/weblogic/domain" xmlns:sec="http://xmlns.oracle.com/weblogic/security" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:wls="http://xmlns.oracle.com/weblogic/security/wls" xsi:schemaLocation="http://xmlns.oracle.com/weblogic/security/wls http://xmlns.oracle.com/weblogic/security/wls/1.0/wls.xsd http://xmlns.oracle.com/weblogic/domain http://xmlns.oracle.com/weblogic/1.0/domain.xsd http://xmlns.oracle.com/weblogic/security/xacml http://xmlns.oracle.com/weblogic/security/xacml/1.0/xacml.xsd http://xmlns.oracle.com/weblogic/security/providers/passwordvalidator http://xmlns.oracle.com/weblogic/security/providers/passwordvalidator/1.0/passwordvalidator.xsd http://xmlns.oracle.com/weblogic/security http://xmlns.oracle.com/weblogic/1.0/security.xsd"> <name>mydomain</name> <domain-version>12.2.1.1.0</domain-version> <security-configuration> <name>mydomain</name> <realm> <sec:authentication-provider xsi:type="wls:default-authenticatorType"> <sec:name>DefaultAuthenticator</sec:name> </sec:authentication-provider> <sec:authentication-provider xsi:type="wls:default-identity-asserterType"> <sec:name>DefaultIdentityAsserter</sec:name> <sec:active-type>AuthenticatedUser</sec:active-type> <sec:active-type>weblogic-jwt-token</sec:active-type> </sec:authentication-provider> <sec:role-mapper xmlns:xac="http://xmlns.oracle.com/weblogic/security/xacml" xsi:type="xac:xacml-role-mapperType"> <sec:name>XACMLRoleMapper</sec:name> </sec:role-mapper> <sec:authorizer xmlns:xac="http://xmlns.oracle.com/weblogic/security/xacml" xsi:type="xac:xacml-authorizerType"> <sec:name>XACMLAuthorizer</sec:name> </sec:authorizer> <sec:adjudicator xsi:type="wls:default-adjudicatorType"> <sec:name>DefaultAdjudicator</sec:name> </sec:adjudicator> <sec:credential-mapper xsi:type="wls:default-credential-mapperType"> <sec:name>DefaultCredentialMapper</sec:name> </sec:credential-mapper> <sec:cert-path-provider xsi:type="wls:web-logic-cert-path-providerType"> <sec:name>WebLogicCertPathProvider</sec:name> </sec:cert-path-provider> <sec:cert-path-builder>WebLogicCertPathProvider</sec:cert-path-builder> <sec:name>myrealm</sec:name> <sec:password-validator xmlns:pas="http://xmlns.oracle.com/weblogic/security/providers/passwordvalidator" xsi:type="pas:system-password-validatorType"> <sec:name>SystemPasswordValidator</sec:name> <pas:min-password-length>8</pas:min-password-length> <pas:min-numeric-or-special-characters>1</pas:min-numeric-or-special-characters> </sec:password-validator> </realm> <default-realm>myrealm</default-realm> <credential-encrypted>{AES}pL6ITnj4ocFHXlXUl7cd7Zh2lQfvtu2fflaNrEB4bo0g3D5V2juCjRo9RPtfsmaJl2BGQ1aGSMGodt/g1WorJck8EqSQ6GYUCZkxlGhl89A+sgUtHe52UoJ1Yp2VLG1Q</credential-encrypted> <node-manager-username>weblogic</node-manager-username> <node-manager-password-encrypted>{AES}fQbMdQ6HRyDs/42utRwPtXOBSe11CJWnCQpVOV34kKE=</node-manager-password-encrypted> </security-configuration> <deployment-configuration> <remote-deployer-ejb-enabled>false</remote-deployer-ejb-enabled> </deployment-configuration> <console-enabled>true</console-enabled> <console-context-path>myconsole</console-context-path> <console-extension-directory>console-ext</console-extension-directory> <server> <name>myserver</name> <ssl> <enabled>true</enabled> <listen-port>27001</listen-port> <server-private-key-alias>wbkey</server-private-key-alias> <server-private-key-pass-phrase-encrypted>{AES}i223ERrerDkKqujTpGmgRtcFnY28IcnmNY9Lpe9zov0=</server-private-key-pass-phrase-encrypted> </ssl> <listen-port>27002</listen-port> <listen-port-enabled>false</listen-port-enabled> <listen-address></listen-address> <java-compiler>javac</java-compiler> <client-cert-proxy-enabled>false</client-cert-proxy-enabled> <key-stores>CustomIdentityAndJavaStandardTrust</key-stores> <custom-identity-key-store-file-name>/home/endless/Oracle/Middleware/sslcert/wbkeystore.jks</custom-identity-key-store-file-name> <custom-identity-key-store-type>JKS</custom-identity-key-store-type> <custom-identity-key-store-pass-phrase-encrypted>{AES}wCJOf6UFj12nzj1ndBjzXMkFhos5gNSFyQzmIcMTpec=</custom-identity-key-store-pass-phrase-encrypted> <server-diagnostic-config> <wldf-diagnostic-volume>Low</wldf-diagnostic-volume> </server-diagnostic-config> </server> <production-mode-enabled>false</production-mode-enabled> <embedded-ldap> <name>mydomain</name> <credential-encrypted>{AES}a0TCOHCuYZsjo6s7wHbvJ6+qXmqbKOj6elt0WiFyKaxsiKbN7/q9MbHkz/YpbFdr</credential-encrypted> </embedded-ldap> <administration-port-enabled>true</administration-port-enabled> <administration-port>29002</administration-port> <exalogic-optimizations-enabled>false</exalogic-optimizations-enabled> <config-backup-enabled>false</config-backup-enabled> <configuration-version>12.2.1.1.0</configuration-version> <configuration-audit-type>none</configuration-audit-type> <cluster-constraints-enabled>false</cluster-constraints-enabled> <cdi-container> <implicit-bean-discovery-enabled>true</implicit-bean-discovery-enabled> </cdi-container> <jmx> <compatibility-m-bean-server-enabled>true</compatibility-m-bean-server-enabled> <management-ejb-enabled>true</management-ejb-enabled> <platform-m-bean-server-enabled>false</platform-m-bean-server-enabled> <invocation-timeout-seconds>0</invocation-timeout-seconds> <platform-m-bean-server-used>true</platform-m-bean-server-used> </jmx> <admin-server-name>myserver</admin-server-name> <administration-protocol>t3s</administration-protocol> <admin-console> <cookie-name>ADMINCONSOLESESSION</cookie-name> <protected-cookie-enabled>true</protected-cookie-enabled> <session-timeout>3600</session-timeout> <min-threads>101</min-threads> </admin-console> <internal-apps-deploy-on-demand-enabled>true</internal-apps-deploy-on-demand-enabled> <log-format-compatibility-enabled>false</log-format-compatibility-enabled> <restful-management-services> <enabled>true</enabled> </restful-management-services> <webservice-testpage> <enabled>false</enabled> </webservice-testpage> <partition-uri-space>/partitions</partition-uri-space> <diagnostic-context-compatibility-mode-enabled>true</diagnostic-context-compatibility-mode-enabled> <lifecycle-manager-config> <deployment-type>none</deployment-type> <out-of-band-enabled>false</out-of-band-enabled> </lifecycle-manager-config> <enable-ee-compliant-classloading-for-embedded-adapters>true</enable-ee-compliant-classloading-for-embedded-adapters> </domain>
以上是关于WebLogic 12c 二三事的主要内容,如果未能解决你的问题,请参考以下文章
